信息网络安全 ›› 2025, Vol. 25 ›› Issue (7): 1053-1062.doi: 10.3969/j.issn.1671-1122.2025.07.005
基于库函数动态替换的物联网设备固件仿真方案
张光华1,2,3, 常继友2,3, 陈放2,3, 毛伯敏4, 王鹤1, 张建燕2,3( )
)
- 1.西安电子科技大学网络与信息安全学院,西安 710071
2.河北科技大学信息科学与工程学院,石家庄 050018
3.河北省智能物联网技术创新中心,石家庄 050018
4.西北工业大学太仓长三角研究院,太仓 215400
-
收稿日期:2024-06-03出版日期:2025-07-10发布日期:2025-08-07 -
通讯作者:张建燕 E-mail:1179602456@qq.com -
作者简介:张光华(1979—),男,河北,教授,博士,CCF会员,主要研究方向为网络与信息安全|常继友(1999—),男,河南,硕士研究生,主要研究方向为物联网安全、嵌入式设备仿真|陈放(2000—),男,河北,硕士研究生,主要研究方向为物联网安全、漏洞检测|毛伯敏(1989—),男,湖北,教授,博士,主要研究方向为空天地一体化网络、卫星物联网、车联网和边缘计算|王鹤(1987—),女,河南,讲师,博士,主要研究方向为应用密码和量子密码协议|张建燕(1982—),女,河北,助理研究员,硕士,主要研究方向为数字通信 -
基金资助:国家自然科学基金(62072239);国家自然科学基金(62372236);苏州姑苏创新创业领军人才计划-青年创新领军人才项目(ZXL2022458)
Firmware Simulation Scheme of IoT Devices Based on Dynamic Substitution of Library Functions
ZHANG Guanghua1,2,3, CHANG Jiyou2,3, CHEN Fang2,3, MAO Bomin4, WANG He1, ZHANG Jianyan2,3( )
)
- 1. School of Cyber Engineering, Xidian University, Xi’an 710071, China
2. School of Information Science and Engineering, Hebei University of Science and Technology, Shijiazhuang 050018, China
3. Hebei Intelligent Internet of Things Technology Innovation Center, Shijiazhuang 050018, China
4. Yangtze River Delta Research Institute of Northwestern Polytechnical University, Taicang 215400, China
-
Received:2024-06-03Online:2025-07-10Published:2025-08-07 -
Contact:ZHANG Jianyan E-mail:1179602456@qq.com
摘要:
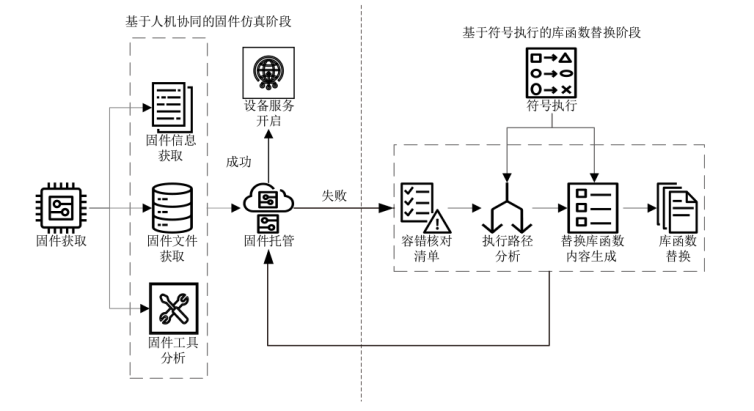
物联网设备资源有限,导致传统的漏洞检测技术难以有效应用。固件仿真技术为解决这一问题提供了可能,但现有方案存在硬件依赖性强、运行成本高和可移植性差等问题。针对这些问题,文章提出一种基于库函数动态替换的物联网设备固件仿真方案。首先,设计了基于人机协同的固件仿真方法,通过固件分析和固件托管构建仿真环境,并在固件文件获取过程中引入专家经验。然后,提出一种基于符号执行的库函数替换技术,通过提取上一阶段的关键信息,利用符号执行技术进行分析并指导库函数生成,最终通过将库函数编译为动态链接库完成库函数替换。实验结果表明,相较于FIRMADYNE,文章所提方案的仿真速度平均提升了80.50%,优化后的符号执行运行速度约为优化前的两倍。同时,通过漏洞复现和漏洞挖掘技术进行验证,实验结果表明,该方案的仿真保真度能够满足漏洞检测和漏洞挖掘的需求。
中图分类号:
引用本文
张光华, 常继友, 陈放, 毛伯敏, 王鹤, 张建燕. 基于库函数动态替换的物联网设备固件仿真方案[J]. 信息网络安全, 2025, 25(7): 1053-1062.
ZHANG Guanghua, CHANG Jiyou, CHEN Fang, MAO Bomin, WANG He, ZHANG Jianyan. Firmware Simulation Scheme of IoT Devices Based on Dynamic Substitution of Library Functions[J]. Netinfo Security, 2025, 25(7): 1053-1062.
表2
数据集产品固件仿真时间
| 设备型号 | FIRMADYNE/s | RLEmu/s | 提升幅度 |
|---|---|---|---|
| AC15 | 72.0644 | 8.2368 | 88.57% |
| DIR-600 | 66.7150 | 9.8483 | 85.24% |
| DIR-859 | 81.0538 | 10.6115 | 86.91% |
| DIR-823G | 67.1768 | 8.5844 | 87.22% |
| DIR-619L | 69.3207 | 8.2919 | 88.04% |
| RV160 | 135.1891 | 87.3373 | 35.40% |
| HG532 | 68.5444 | 6.6619 | 90.28% |
| R9000 | 97.1509 | 16.4884 | 83.03% |
| R6400 | 100.3214 | 11.5311 | 88.51% |
| T310 | 78.9124 | 22.2200 | 71.84% |
| 平均 | 83.6448 | 18.9811 | 80.50% |
表5
后续仿真时间
| 设备型号 | 初次仿真/s | 后续仿真/s | 提升幅度 |
|---|---|---|---|
| AC15 | 8.2368 | 5.1482 | 37.50% |
| DIR-600 | 9.8483 | 8.6387 | 12.28% |
| DIR-859 | 10.6115 | 8.1962 | 22.76% |
| DIR-823G | 8.5844 | 6.3457 | 26.08% |
| DIR-619L | 8.2919 | 3.9558 | 52.29% |
| RV160 | 87.3373 | 78.3328 | 10.31% |
| HG532 | 6.6619 | 2.9420 | 55.84% |
| R9000 | 16.4884 | 11.6889 | 29.11% |
| R6400 | 11.5311 | 10.7336 | 6.92% |
| T310 | 22.2200 | 18.0240 | 18.88% |
| 平均 | 18.9811 | 15.4005 | 27.20% |
| [1] | KUANG Boyu, FU Anmin, GAO Yansong, et al. FeSA: Automatic Federated Swarm Attestation on Dynamic Large-Scale IoT Devices[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(4): 2954-2969. |
| [2] | ARTENSTEIN N. Broadpwn: Remotely Compromising Android and iOS via a Bug in Broadcom’s Wi-Fi Chipsets[EB/OL]. (2017-07-27) [2024-05-29]. https://blog.exodusintel.com/2017/07/26/broadpwn/. |
| [3] | MARGOLIS J, OH T T, JADHAV S, et al. An In-Depth Analysis of the Mirai Botnet[C]// IEEE. 2017 International Conference on Software Security and Assurance (ICSSA). New York: IEEE, 2017: 6-12. |
| [4] | ZHANG Hao, SHEN Shandian, LIU Peng, et al. Review of Firmware Emulators in Embedded Devices[J]. Journal of Computer Research and Development, 2023, 60(10): 2255-2270. |
| 张浩, 申珊靛, 刘鹏, 等. 嵌入式设备固件仿真器综述[J]. 计算机研究与发展, 2023, 60(10): 2255-2270. | |
| [5] | FENG Xiaotao, ZHU Xiaogang, HAN Qinglong, et al. Detecting Vulnerability on IoT Device Firmware: A Survey[J]. IEEE/CAA Journal of Automatica Sinica, 2022, 10(1): 25-41. |
| [6] | YU Yingchao, CHEN Zuoning, GAN Shuitao, et al. Research on the Technologies of Security Analysis Technologies on the Embedded Device Firmware[J]. Chinese Journal of Computers, 2021, 44(5): 859-881. |
| 于颖超, 陈左宁, 甘水滔, 等. 嵌入式设备固件安全分析技术研究[J]. 计算机学报, 2021, 44(5): 859-881. | |
| [7] | TANASACHE F D, SORELLA M, BONOMI S, et al. Building an Emulation Environment for Cyber Security Analyses of Complex Networked Systems[EB/OL]. (2018-10-23) [2024-05-29]. https://doi.org/10.48550/arXiv.1810.09752. |
| [8] | WRIGHT C, MOEGLEIN W A, BAGCHI S, et al. Challenges in Firmware Re-Hosting, Emulation, and Analysis[J]. ACM Computing Surveys (CSUR), 2022, 54(1): 1-36. |
| [9] | SCHWARTZ E J, AVGERINOS T, BRUMLEY D. All You Ever Wanted to Know about Dynamic Taint Analysis and Forward Symbolic Execution (But Might Have Been Afraid to Ask)[C]// IEEE. 2010 IEEE Symposium on Security and Privacy. New York: IEEE, 2010: 317-331. |
| [10] | FASANO A, BALLO T, MUENCH M, et al. SoK: Enabling Security Analyses of Embedded Systems via Rehosting[C]// ACM. The 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 687-701. |
| [11] | ZADDACH J, BRUNO L, FRANCILLON A, et al. Avatar: A Framework to Support Dynamic Security Analysis of Embedded Systems’ Firmwares[C]// IEEE. 2014 Network and Distributed System Security Symposium. New York: IEEE, 2014: 1-16. |
| [12] | KAMMERSTETTER M, PLATZER C, KASTNER W. Prospect: Peripheral Proxying Supported Embedded Code Testing[C]// ACM. The 9th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2014: 329-340. |
| [13] | BELLARD F. QEMU, a Fast and Portable Dynamic Translator[C]// USENIX. The Annual Conference on USENIX Annual Technical Conference. Berkley: USENIX, 2005: 41-46. |
| [14] | CHEN D D, EGELE M, WOO M, et al. Towards Automated Dynamic Analysis for Linux-Based Embedded Firmware[C]// IEEE. 2016 Network and Distributed System Security Symposium. New York: IEEE, 2016: 1-16. |
| [15] | KIM M, KIM D, KIM E, et al. FirmAE: Towards Large-Scale Emulation of IoT Firmware for Dynamic Analysis[C]// ACM. Annual Computer Security Applications Conference. New York: ACM, 2020: 733-745. |
| [16] | GUSTAFSON E, MUENCH M, SPENSKY C, et al. Toward the Analysis of Embedded Firmware through Automated Re-Hosting[C]// USENIX. 22nd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2019). Berkley: USENIX, 2019: 135-150. |
| [17] | FENG Bo, MERA A, LU Long. {P2IM}: Scalable and Hardware-Independent Firmware Testing via Automatic Peripheral Interface Modeling[C]// USENIX. 29th USENIX Security Symposium. Berkley: USENIX, 2020: 1237-1254. |
| [18] | CLEMENTS A A, GUSTAFSON E, SCHARNOWSKI T, et al. {HALucinator}: Firmware Re-Hosting through Abstraction Layer Emulation[C]// USENIX. 29th USENIX Security Symposium. Berkley: USENIX, 2020: 1201-1218. |
| [19] | LI Wenqiang, GUAN Le, LIN Jingqiang, et al. From Library Portability to Para-Rehosting: Natively Executing Microcontroller Software on Commodity Hardware[EB/OL]. (2021-07-04) [2024-05-29]. https://arxiv.org/abs/2107.12867. |
| [20] | ZHOU Wei, ZHANG Lan, GUAN Le, et al. What Your Firmware Tells You is Not How You Should Emulate It: A Specification-Guided Approach for Firmware Emulation[C]// ACM. The 2022 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 3269-3283. |
| [21] | CAO Chen, GUAN Le, MING Jiang, et al. Device-Agnostic Firmware Execution is Possible: A Concolic Execution Approach for Peripheral Emulation[C]// ACM. Annual Computer Security Applications Conference. New York: ACM, 2020: 746-759. |
| [22] | ZHOU Wei, GUAN Le, LIU Peng, et al. Automatic Firmware Emulation through Invalidity-Guided Knowledge Inference[C]// USENIX. 30th USENIX Security Symposium. Berkley: USENIX, 2021: 2007-2024. |
| [23] | SHOSHITAISHVILI Y, WANG Ruoyu, SALLS C, et al. SOK: (State of ) The Art of War: Offensive Techniques in Binary Analysis[C]// IEEE. 2016 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2016: 138-157. |
| [24] | SCHARNOWSKI T, BARS N, SCHLOEGEL M, et al. Fuzzware: Using Precise {MMIO} Modeling for Effective Firmware Fuzzing[C]// USENIX. 31st USENIX Security Symposium. Berkley: USENIX, 2022: 1239-1256. |
| [1] | 王梅, 杨潇然, 李增鹏. 简洁低交互的物联网设备认证协议研究[J]. 信息网络安全, 2025, 25(7): 1032-1043. |
| [2] | 邓东上, 王伟业, 张卫东, 吴宣够. 基于模型特征方向的分层个性化联邦学习框架[J]. 信息网络安全, 2025, 25(6): 889-897. |
| [3] | 李强, 沈援海, 王锦泽, 黄晏瑜, 孙建国. 一种面向工业物联网环境的离线—在线签名方案[J]. 信息网络安全, 2025, 25(3): 392-402. |
| [4] | 王鹃, 张勃显, 张志杰, 谢海宁, 付金涛, 王洋. 基于模糊测试的Java反序列化漏洞挖掘[J]. 信息网络安全, 2025, 25(1): 1-12. |
| [5] | 袁征, 张跃飞, 冯笑, 乔雅馨. 基于PUF的电力物联网智能终端认证协议[J]. 信息网络安全, 2025, 25(1): 13-26. |
| [6] | 张学旺, 陈思宇, 罗欣悦, 雷志滔, 谢昊飞. 面向云辅助工业物联网的高效可搜索属性基加密方案[J]. 信息网络安全, 2024, 24(9): 1352-1363. |
| [7] | 邢长友, 王梓澎, 张国敏, 丁科. 基于预训练Transformers的物联网设备识别方法[J]. 信息网络安全, 2024, 24(8): 1277-1290. |
| [8] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [9] | 李志华, 陈亮, 卢徐霖, 方朝晖, 钱军浩. 面向物联网Mirai僵尸网络的轻量级检测方法[J]. 信息网络安全, 2024, 24(5): 667-681. |
| [10] | 杨杰超, 胡汉平, 帅燕, 邓宇昕. 基于时变互耦合双混沌系统的轻量级序列密码[J]. 信息网络安全, 2024, 24(3): 385-397. |
| [11] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [12] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [13] | 王鹃, 龚家新, 蔺子卿, 张晓娟. 多维深度导向的Java Web模糊测试方法[J]. 信息网络安全, 2024, 24(2): 282-292. |
| [14] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [15] | 张展鹏, 王鹃, 张冲, 王杰, 胡宇义. 基于图同构网络的高效Web模糊测试技术研究[J]. 信息网络安全, 2024, 24(10): 1544-1552. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||