信息网络安全 ›› 2025, Vol. 25 ›› Issue (2): 295-305.doi: 10.3969/j.issn.1671-1122.2025.02.010
基于探测间隔变化的OpenFlow交换机超时嗅探方法
杨致远1,2,3,4, 崔允贺1,2,3,4( ), 陈意1,2,3,4, 郭春1,2,3,4
), 陈意1,2,3,4, 郭春1,2,3,4
- 1.贵州大学计算机科学与技术学院,贵阳 550025
2.公共大数据国家重点实验室,贵阳 550025
3.文本计算与认知智能教育部工程研究中心,贵阳 550025
4.贵州省软件工程与信息安全特色重点实验室,贵阳 550025
-
收稿日期:2024-11-05出版日期:2025-02-10发布日期:2025-03-07 -
通讯作者:崔允贺 E-mail:yhcui@gzu.edu.cn -
作者简介:杨致远(2000—),男,甘肃,硕士研究生,主要研究方向为软件定义网络、网络与信息安全|崔允贺(1987—),男,山东,副教授,博士,CCF高级会员,主要研究方向为软件定义网络、边缘计算和云计算|陈意(1991—),男,贵州,副教授,博士,主要研究方向为多媒体安全及人工智能安全|郭春(1986—),男,贵州,教授,博士,CCF高级会员,主要研究方向为恶意软件分析、入侵检测和数据挖掘 -
基金资助:贵州省科技重大专项(黔科合重大专项字[2024]003);贵州省高等学校大数据安全与网络安全创新团队资助项目(黔教技[2023]052号)
OpenFlow Switch Timeout Sniffing Method Based on Detection Interval Changes
YANG Zhiyuan1,2,3,4, CUI Yunhe1,2,3,4( ), CHEN Yi1,2,3,4, GUO Chun1,2,3,4
), CHEN Yi1,2,3,4, GUO Chun1,2,3,4
- 1. College of Computer Science and Technology, Guizhou University, Guiyang 550025, China
2. State Key Laboratory of Public Big Data, Guiyang 550025, China
3. Engineering Research Center of Text Computing & Cognitive Intelligence, Ministry of Education, Guiyang 550025, China
4. Key Laboratory of Software Engineering and Information Security in Guizhou Province, Guiyang 550025, China
-
Received:2024-11-05Online:2025-02-10Published:2025-03-07
摘要:
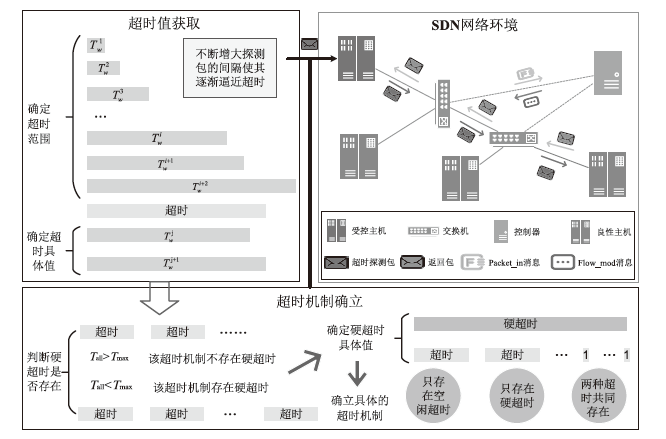
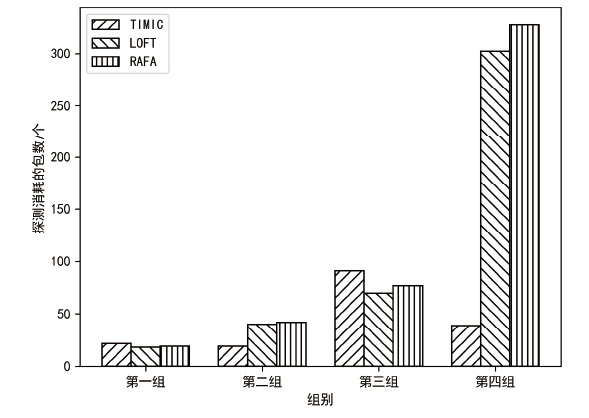
软件定义网络(SDN)通过分离控制平面和数据平面实现了网络的集中化、可编程化和灵活化。但这种架构也使SDN面临新的攻击威胁,针对SDN交换机的超时嗅探是其面临的主要安全威胁之一。现有的超时嗅探方法忽略了超时的最大值、探测包的生成时间以及超时之间的关系对于探测超时的影响,导致出现探测失败、超时类型识别错误和超时值探测精度低的问题。为解决上述问题,文章提出一种基于探测间隔变化的OpenFlow交换机流表项超时机制嗅探方法—TIMIC。该方法先通过调整探测包的发送间隔获得超时值,再通过该超时值判断具体的超时机制及更精确的超时值。实验结果表明,TIMIC在不同的超时机制下都能成功探测超时类型和超时值,且探测出的超时值能够保持较小的探测误差。在通用的超时设置下,TIMIC发送的超时探测包更少,探测成本更低。
中图分类号:
引用本文
杨致远, 崔允贺, 陈意, 郭春. 基于探测间隔变化的OpenFlow交换机超时嗅探方法[J]. 信息网络安全, 2025, 25(2): 295-305.
YANG Zhiyuan, CUI Yunhe, CHEN Yi, GUO Chun. OpenFlow Switch Timeout Sniffing Method Based on Detection Interval Changes[J]. Netinfo Security, 2025, 25(2): 295-305.
表4
时延为200 ms时超时探测结果对比
| 组别 | 超时类别 | 设置时长/s | TIMIC | LOFT | RAFA |
|---|---|---|---|---|---|
| 第一组 | 空闲超时 | 10 | 9.00 s(10.00%) | 8.63 s(13.70%) | 3.05 s(69.50%) |
| 硬超时 | 11 | 9.55 s(13.18%) | 9.51 s(13.55%) | 11.92 s(8.36%) | |
| 第二组 | 空闲超时 | 10 | 9.00 s(10.00%) | 9.54 s(4.60%) | 4.42 s(55.80%) |
| 硬超时 | 30 | 29.36 s(2.13%) | 28.52 s(4.93%) | 30.95 s(3.17%) | |
| 第三组 | 空闲超时 | 60 | 59.00 s(1.67%) | 0 s(100%)/ 探测错误 | 6.38 s(89.37%) |
| 硬超时 | 61 | 59.61 s(2.28%) | 59.13 s(3.07%) | 62.69 s(2.77%) | |
| 第四组 | 空闲超时 | 60 | 59.00 s(1.67%) | 58.78 s(2.03%) | 13.62 s(77.30%) |
| 硬超时 | 300 | 299.13 s(0.29%) | 298.94 s(0.35%) | 301.53 s(0.51%) |
表5
时延为100 ms时超时探测结果对比
| 组别 | 超时类别 | 设置时长/s | TIMIC | LOFT | RAFA |
|---|---|---|---|---|---|
| 第一组 | 空闲超时 | 10 | 10.00 s(0%) | 9.42 s(5.80%) | 2.90 s(71.00%) |
| 硬超时 | 11 | 11.63 s(5.73%) | 10.56 s(4.00%) | 11.24 s(2.18%) | |
| 第二组 | 空闲超时 | 10 | 10.00 s(0%) | 9.87 s(1.30%) | 4.42 s(55.80%) |
| 硬超时 | 30 | 29.21 s(2.63%) | 29.60 s(1.33%) | 31.25 s(4.17%) | |
| 第三组 | 空闲超时 | 60 | 60.00 s(0%) | 0 s(100%)/ 探测错误 | 6.20 s(89.67%) |
| 硬超时 | 61 | 61.68 s(1.11%) | 60.20 s(1.31%) | 61.90 s(1.48%) | |
| 第四组 | 空闲超时 | 60 | 60.00 s(0.00%) | 58.97 s(1.72%) | 13.39 s(77.68%) |
| 硬超时 | 300 | 300.08 s(0.03%) | 299.90 s(0.03%) | 300.57 s(0.19%) |
表6
时延为0 ms时超时探测结果对比
| 组别 | 超时类别 | 设置时长/s | TIMIC | LOFT | RAFA |
|---|---|---|---|---|---|
| 第一组 | 空闲超时 | 10 | 10.00 s(0%) | 10.09 s(0.90%) | 2.63 s(73.70%) |
| 硬超时 | 11 | 11.60 s(5.45%) | 11.45 s(4.09%) | 12.44 s(13.09%) | |
| 第二组 | 空闲超时 | 10 | 10.00 s(0.00%) | 10.15 s(1.50%) | 4.17 s(58.30%) |
| 硬超时 | 30 | 30.78 s(2.60%) | 30.48 s(1.60%) | 31.54 s(5.13%) | |
| 第三组 | 空闲超时 | 60 | 60.00 s(0%) | 59.29 s(1.18%) | 5.97 s(90.05%) |
| 硬超时 | 61 | 61.68 s(1.11%) | 61.24 s(0.39%) | 62.45 s(2.38%) | |
| 第四组 | 空闲超时 | 60 | 60.00 s(0%) | 60.14 s(0.23%) | 13.19 s(78.02%) |
| 硬超时 | 300 | 300.09 s(0.03%) | 299.89 s(0.04%) | 300.84 s(0.28%) |
表7
时延为200 ms时超时探测结果对比
| 组别 | 超时类别 | 设置 时长/s | TIMIC | LOFT | RAFA |
|---|---|---|---|---|---|
| 第一组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 2.90 s(探测错误) |
| 硬超时 | 10 | 9.00 s(10.00%) | 8.44 s(15.60%) | 10.90 s(9.00%) | |
| 第二组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 4.52 s(探测错误) |
| 硬超时 | 30 | 29.00 s(3.33%) | 28.51 s (4.97%) | 30.99 s(3.30%) | |
| 第三组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 6.06 s(探测错误) |
| 硬超时 | 60 | 59.00 s(1.67%) | 58.08 s (3.20%) | 60.67 s(1.12%) | |
| 第四组 | 空闲超时 | 0 | 0 s(0%) | 98.10 s (探测错误) | 7.92 s (探测错误) |
| 硬超时 | 100 | 99.00 s(1.00%) | 99.26 s(0.74%) | 100.72 s(0.72%) |
表8
时延为100 ms时超时探测结果对比
| 组别 | 超时类别 | 设置 时长/s | TIMIC | LOFT | RAFA |
|---|---|---|---|---|---|
| 第一组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 2.63 s(探测错误) |
| 硬超时 | 10 | 10.00 s(0%) | 9.50 s(5.00%) | 12.44 s(24.4%) | |
| 第二组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 4.17 s(探测错误) |
| 硬超时 | 30 | 30.00 s(0%) | 29.57 s (1.43%) | 31.54 s(5.13%) | |
| 第三组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 5.97 s(探测错误) |
| 硬超时 | 60 | 60.00 s(0%) | 60.23 s (0.38%) | 62.45 s(4.08%) | |
| 第四组 | 空闲超时 | 0 | 0 s(0%) | 99.14 s (探测错误) | 13.19 s (探测错误) |
| 硬超时 | 100 | 100.00 s(0%) | 100.34 s(0.34%) | 100.84 s(0.84%) |
表9
时延为0 ms时超时探测结果对比
| 组别 | 超时类别 | 设置 时长/s | TIMIC | LOFT | RAFA |
|---|---|---|---|---|---|
| 第一组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 2.63 s(探测错误) |
| 硬超时 | 10 | 10.00 s(0%) | 9.50 s(5.00%) | 12.44 s(24.4%) | |
| 第二组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 4.17 s(探测错误) |
| 硬超时 | 30 | 30.00 s(0%) | 29.57 s(1.43%) | 31.54 s(5.13%) | |
| 第三组 | 空闲超时 | 0 | 0 s(0%) | 0 s(0%) | 5.97 s(探测错误) |
| 硬超时 | 60 | 60.00 s(0%) | 60.25 s(0.42%) | 62.45 s(4.08%) | |
| 第四组 | 空闲超时 | 0 | 0 s(0%) | 99.18 s (探测错误) | 13.19 s (探测错误) |
| 硬超时 | 100 | 100.00 s(0%) | 100.38 s(0.38%) | 100.84 s(0.84%) |
表10
时延为200 ms时超时探测结果对比
| 组别 | 超时类别 | 设置时长/s | TIMIC | LOFT |
|---|---|---|---|---|
| 第一组 | 空闲超时 | 10 | 9.00 s(10.00%) | 7.83 s(21.70%) |
| 硬超时 | 0 | 0 s(0%) | 0 s(0%) | |
| 第二组 | 空闲超时 | 30 | 29.00 s(3.33%) | 29.36 s(2.13%) |
| 硬超时 | 0 | 0 s(0%) | 0 s(0%) | |
| 第三组 | 空闲超时 | 60 | 59.00 s(1.67%) | 58.71 s(2.15%) |
| 硬超时 | 0 | 0 s(0%) | 0 s(0%) | |
| 第四组 | 空闲超时 | 100 | 99.00 s(1.00%) | 97.85 s(2.15%) |
| 硬超时 | 0 | 0 s(0%) | 0 s(0%) |
| [1] | CUI Yunhe, QIAN Qing, GUO Chun, et al. Towards DDoS Detection Mechanisms in Software-Defined Networking[EB/OL]. (2021-07-10)[2024-09-10]. https://www.sciencedirect.com/science/article/abs/pii/S1084804521001703?via%3Dihub. |
| [2] | YAO Xianxian, XIA Hongbin, LIU Yuan. Detection and Mitigation of DDoS Based on Attention Mechanism in SDN Environment[EB/OL]. (2024-05-31)[2024-09-10]. https://kns.cnki.net/kcms/detail/21.1106.TP.20240530.1039.008.html. |
| 姚纤纤, 夏鸿斌, 刘渊. SDN环境中基于注意力机制的DDoS检测和缓解[EB/OL]. (2024-05-31)[2024-09-10]. https://kns.cnki.net/kcms/detail/21.1106.TP.20240530.1039.008.html. | |
| [3] | LEI Yuxia. Research on DDoS Anomaly Attack Detection Technology Based on SDN Architecture[J]. Shanxi Electronic Technology, 2024(3): 120-123. |
| 雷宇霞. 基于SDN架构的DDoS异常攻击检测技术研究[J]. 山西电子技术, 2024(3): 120-123. | |
| [4] | ZHANG Junrong. Analysis of Software Defined Network (SDN) Technology[J]. Digital Communication World, 2024(6): 115-117. |
| 张俊茸. 软件定义网络(SDN)技术分析[J]. 数字通信世界, 2024(6): 115-117. | |
| [5] |
WANG Dongbin, WU Dongzhe, ZHI Hui, et al. Preventing Flow Table Overflow against Denial of Service Attack in Software Defined Network[J]. Journal on Communications, 2023, 44(2): 1-11
doi: 10.11959/j.issn.1000-436x.2023036 |
|
王东滨, 吴东哲, 智慧, 等. 软件定义网络抗拒绝服务攻击的流表溢出防护[J]. 通信学报, 2023, 44(2): 1-11.
doi: 10.11959/j.issn.1000-436x.2023036 |
|
| [6] | RAN Longyan, CUI Yunhe, GUO Chun, et al. Defending Saturation Attacks on SDN Controller: A Confusable Instance Analysis-Based Algorithm[EB/OL]. (2022-06-17)[2024-09-10]. https://www.sciencedirect.com/science/article/abs/pii/S1389128622002298?via%3Dihub. |
| [7] | LI Jishuai, TU Tengfei, LI Yongsheng, et al. DoSGuard: Mitigating Denial-of-Service Attacks in Software-Defined Networks[EB/OL]. (2021-01-29)[2024-09-10]. https://pubmed.ncbi.nlm.nih.gov/35161800/. |
| [8] | CONTI M, GANGWAL A, GAUR M S. A Comprehensive and Effective Mechanism for DDoS Detection in SDN[C]// IEEE. 2017 IEEE 13th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob). New York: IEEE, 2017: 1-8. |
| [9] | WANG Zhi, ZHANG Hao, GU Jianjun. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN[J]. Netinfo Security, 2023, 23(10): 1-7. |
| 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. | |
| [10] | XU Jianfeng, ZHANG Fangtao, XU Zhen, et al. Field Manipulation Attacks Based on Sniffing Techniques[J]. Journal of Electronics & Information Technology, 2020, 42(10): 2342-2349. |
| 徐建峰, 张方韬, 徐震, 等. 基于嗅探技术的字段操纵攻击研究[J]. 电子与信息学报, 2020, 42(10): 2342-2349. | |
| [11] | PATWARDHAN A, JAYARAMA D, LIMAYE N, et al. SDN Security: Information Disclosure and Flow Table Overflow Attacks[C]// IEEE. 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6. |
| [12] | YIĞIT B, GÜR G, ALAGÖZ F, et al. Network Fingerprinting via Timing Attacks and Defense in Software Defined Networks[EB/OL]. (2023-06-02)[2024-09-10]. https://www.sciencedirect.com/science/article/abs/pii/S1389128623002955?via%3Dihub. |
| [13] | CAO Jiahao, XU Mingwei, LI Qi, et al. The LOFT Attack: Overflowing SDN Flow Tables at a Low Rate[J]. IEEE/ACM Transactions on Networking, 2023, 31(3): 1416-1431. |
| [14] |
CHEN Xingshu, HUA Qiang, WANG Yitong, et al. Research on Low-Rate DDoS Attack of SDN Network in Cloud Environment[J]. Journal on Communications, 2019, 40(6): 210-222.
doi: 10.11959/j.issn.1000-436x.2019120 |
|
陈兴蜀, 滑强, 王毅桐, 等. 云环境下SDN网络低速率DDoS攻击的研究[J]. 通信学报, 2019, 40(6): 210-222.
doi: 10.11959/j.issn.1000-436x.2019120 |
|
| [15] | AZZOUNI A, BRAHAM O, TRANG N T M, et al. Fingerprinting OpenFlow Controllers: The First Step to Attack an SDN Control Plane[C]// IEEE. 2016 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2016: 1-6. |
| [16] | LENG Junyuan, ZHOU Yadong, ZHANG Junjie, et al. An Inference Attack Model for Flow Table Capacity and Usage: Exploiting the Vulnerability of Flow Table Overflow in Software-Defined Network[EB/OL]. (2015-04-13)[2024-09-10]. https://arxiv.org/abs/1504.03095v1. |
| [17] | BENSON T, AKELLA A, MALTZ D A, et al. Network Traffic Characteristics of Data Centers in the Wild[C]// ACM. Proceedings of the 10th ACM SIGCOMM Conference on Internet Measurement. New York: ACM, 2010: 267-280. |
| [1] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [2] | 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. |
| [3] | 于俊清, 李自尊, 吴驰, 赵贻竹. 面向软件定义网络的两级DDoS攻击检测与防御[J]. 信息网络安全, 2022, 22(1): 1-8. |
| [4] | 范广宇, 王兴伟, 贾杰, 黄敏. SDN应用平面与控制平面安全交互方法[J]. 信息网络安全, 2021, 21(6): 70-79. |
| [5] | 李朝阳, 谭晶磊, 胡瑞钦, 张红旗. 基于双重地址跳变的移动目标防御方法[J]. 信息网络安全, 2021, 21(2): 24-33. |
| [6] | 王鹃, 杨泓远, 樊成阳. 一种基于多阶段攻击响应的SDN动态蜜罐[J]. 信息网络安全, 2021, 21(1): 27-40. |
| [7] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [8] | 王健, 王语杰, 韩磊. 基于突变模型的SDN环境中DDoS攻击检测方法[J]. 信息网络安全, 2020, 20(5): 11-20. |
| [9] | 周亚球, 任勇毛, 李琢, 周旭. 基于SDN的科学DMZ研究与实现[J]. 信息网络安全, 2019, 19(9): 134-138. |
| [10] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [11] | 石悦, 李相龙, 戴方芳. 一种基于属性基加密的增强型软件定义网络安全框架[J]. 信息网络安全, 2018, 18(1): 15-22. |
| [12] | 李剑锋, 刘渊, 张浩, 王晓锋. 面向IaaS云平台的路由转发优化研究与实现[J]. 信息网络安全, 2017, 17(9): 10-15. |
| [13] | 徐洋, 陈燚, 何锐, 谢晓尧. SDN中DDoS检测及多层防御方法研究[J]. 信息网络安全, 2017, 17(12): 22-28. |
| [14] | 齐宇. SDN安全研究[J]. 信息网络安全, 2016, 16(9): 69-72. |
| [15] | 陈颖聪, 陈广清, 陈智明, 万能. 面向智能电网SDN的二进制代码分析漏洞扫描方法研究[J]. 信息网络安全, 2016, 16(7): 35-39. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||