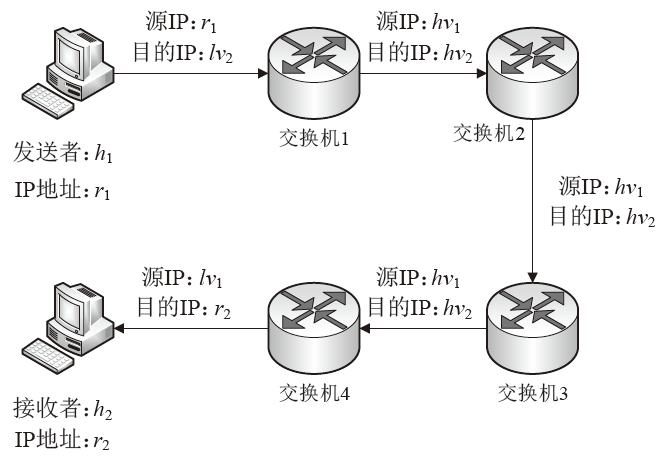
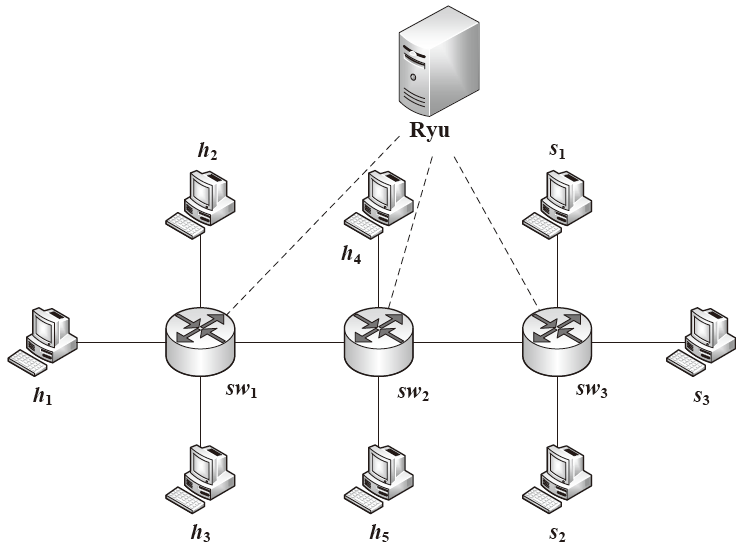
信息网络安全 ›› 2021, Vol. 21 ›› Issue (2): 24-33.doi: 10.3969/j.issn.1671-1122.2021.02.004
基于双重地址跳变的移动目标防御方法
- 1.信息工程大学密码工程学院,郑州 450001
2.郑州大学软件学院,郑州 450001
-
收稿日期:2020-11-02出版日期:2021-02-10发布日期:2021-02-23 -
通讯作者:谭晶磊 E-mail:nxutjl@126.com -
作者简介:李朝阳(1996—),男,河南,硕士研究生,主要研究方向为网络信息安全、移动目标防御|谭晶磊(1994—),男,山东,博士研究生,主要研究方向为网络信息安全、移动目标防御、安全博弈决策|胡瑞钦(1995—),男,湖北,硕士研究生,主要研究方向为网络信息安全、移动目标防御|张红旗(1962—),男,河北,教授,博士,主要研究方向为网络信息安全、移动目标防御、等级保护和信息安全管理 -
基金资助:国家自然科学基金(61902427);国家重点研发计划(2016YFF0204002);国家重点研发计划(2016YFF0204003);郑州市科技领军人才项目(131PLJRC644)
Moving Target Defense Method Based on Double Address Hopping
LI Zhaoyang1,2, TAN Jinglei1( ), HU Ruiqin1, ZHANG Hongqi1
), HU Ruiqin1, ZHANG Hongqi1
- 1. Department of Cryptogram Engineering, Information Engineering University, Zhengzhou 450001, China
2. Software College, Zhengzhou University, Zhengzhou 450001, China
-
Received:2020-11-02Online:2021-02-10Published:2021-02-23 -
Contact:TAN Jinglei E-mail:nxutjl@126.com
摘要:
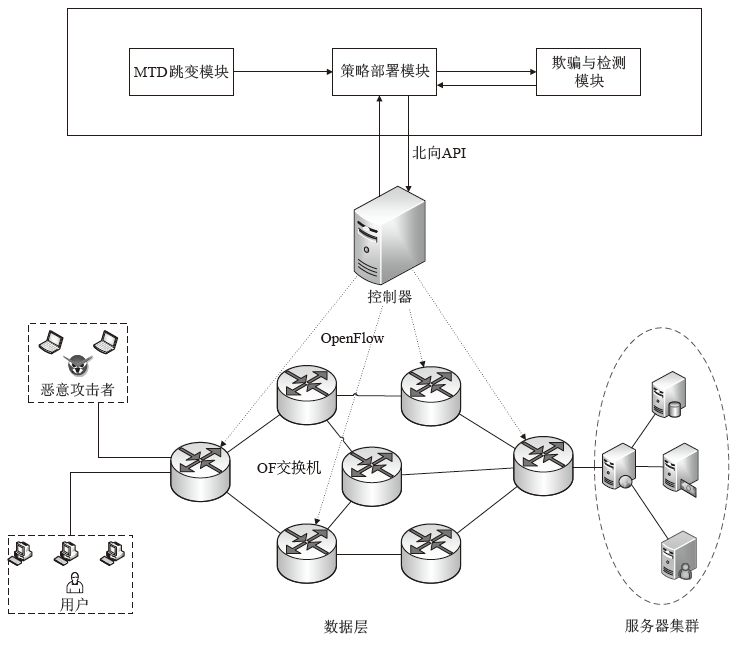
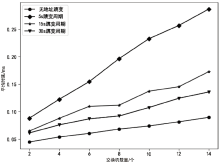
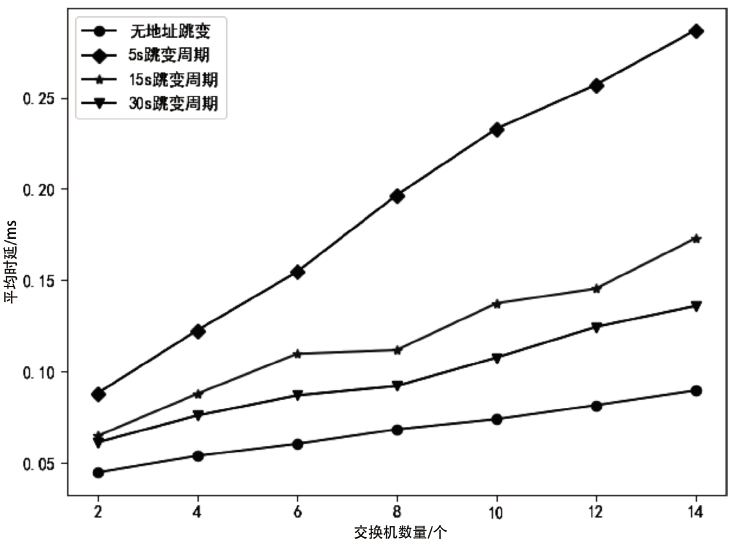
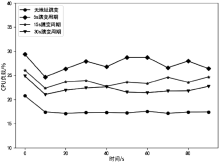
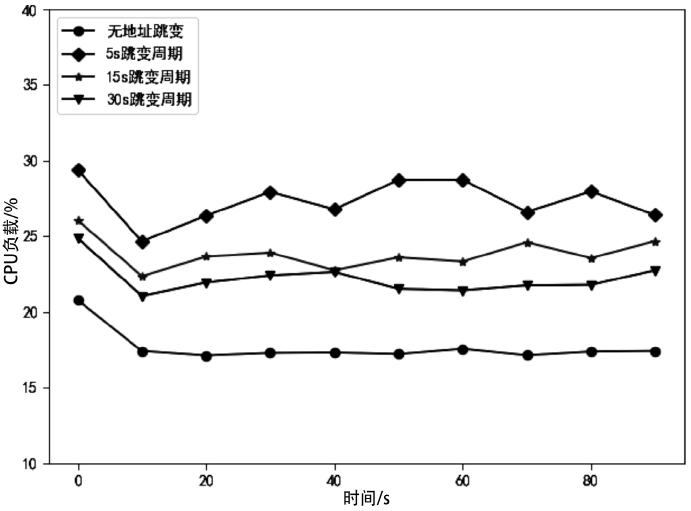
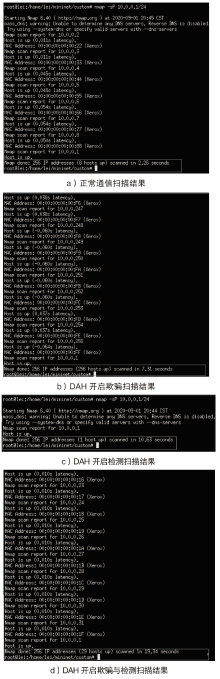
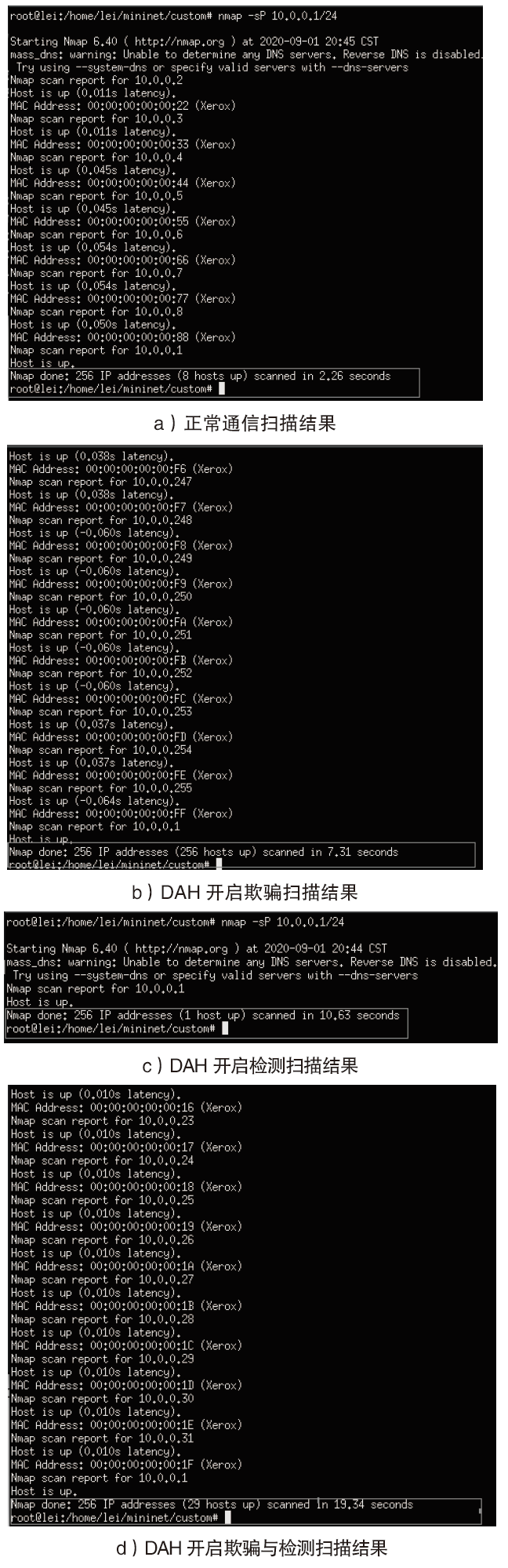
网络系统的确定性和静态性使得防御处在被动之中,移动目标防御作为一种改变攻守态势的防御理念被提出。针对嗅探和扫描攻击,文章提出一种基于双重地址跳变的移动目标防御方法——DAH。通过双重虚拟地址跳变频率分级,有效解决通信服务质量和跳变频率之间的矛盾,利用低频虚拟地址跳变保证网络可用性,利用高频虚拟地址跳变抵御嗅探攻击。通过检测主机异常通信行为构造欺骗数据包,以实现迷惑并阻断扫描攻击的效果。测试实验表明,DAH既可以保证网络的正常通信时延和CPU负载,又可以有效抵御嗅探和扫描攻击。
中图分类号:
引用本文
李朝阳, 谭晶磊, 胡瑞钦, 张红旗. 基于双重地址跳变的移动目标防御方法[J]. 信息网络安全, 2021, 21(2): 24-33.
LI Zhaoyang, TAN Jinglei, HU Ruiqin, ZHANG Hongqi. Moving Target Defense Method Based on Double Address Hopping[J]. Netinfo Security, 2021, 21(2): 24-33.
使用本文
表2
嗅探攻击监听终端IP地址信息结果
| 终端 | 真实IP 地址 | 所收集到的终端IP地址 | ||||
|---|---|---|---|---|---|---|
| 正常通信 | DAH开启5 s后 | DAH开启10 s后 | …… | DAH开启50 s后 | ||
| h1 h2 h3 h4 h5 s1 s2 s3 | 10.0.0.1 10.0.0.2 10.0.0.3 10.0.0.4 10.0.0.5 10.0.0.6 10.0.0.7 10.0.0.8 | 10.0.0.1 10.0.0.2 10.0.0.3 10.0.0.4 10.0.0.5 10.0.0.6 10.0.0.7 10.0.0.8 | 10.0.0.70 10.0.0.138 10.0.0.61 10.0.0.117 10.0.0.249 10.0.0.97 10.0.0.227 10.0.0.97 | 10.0.0.245 10.0.0.214 10.0.0.170 10.0.0.28 10.0.0.38 10.0.0.234 10.0.0.196 10.0.0.109 | …… …… …… …… …… …… …… …… | 10.0.0.213 10.0.0.113 10.0.0.77 10.0.0.27 10.0.0.154 10.0.0.157 10.0.0.170 10.0.0.139 |
| [1] | CAI Guilin, WANG Baosheng, WANG Tianzuo, et al. Research and Development of Moving Target Defense Technology[J]. Journal of Computer Research and Development, 2016,53(5): 968-987. |
| 蔡桂林, 王宝生, 王天佐, 等. 移动目标防御技术研究进展[J]. 计算机研究与发展, 2016,53(5): 968-987. | |
| [2] | STEVENS C. Assembling Cybersecurity: The Politics and Materiality of Technical Malware Reports and the Case of Stuxnet[J]. Contemporary Security Policy, 2020,41(1): 129-152. |
| [3] | ADAMS C. Learning the Lessons of WannaCry[J]. Computer Fraud & Security, 2018,2018(9): 6-9. |
| [4] | SHARMA D P, ENOCH S Y, CHO J H, et al. Dynamic Security Metrics for Software-defined Network-based Moving Target Defense[EB/OL]. https://www.researchgate.net/publication/343979066_Dynamic_Security_Metrics_for_Software-Defined_Network-based_Moving_Target_Defense, 2020-09-20. |
| [5] | TAN Jinglei, ZHANG Hengwei, ZHANG Hongqi, et al. Optimal Timing Selection Approach to Moving Target Defense: A FlipIt Attack-Defense Game Model[J]. Security and Communication Networks, 2020,2020(1): 1-12. |
| [6] | CHO J H, SHARMA D P, ALAVIZADEH H, et al. Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense[EB/OL]. https://www.researchgate.net/publication/335908328_Toward_Proactive_Adaptive_Defense_A_Survey_on_Moving_Target_Defense, 2020-09-20. |
| [7] | AYDEGER A, SAPUTRO N, AKKAYA K. A Moving Target Defense and Network Forensics Framework for ISP Networks Using SDN and NFV[J]. Future Generation Computer Systems, 2019,94(5): 496-509. |
| [8] | ZHOU Yuyang, CHENG Guang, GUO Chunsheng, et al. A Survey on Attack Surface Dynamic Transfer Technology Based on Moving Target Defense[J]. Journal of Software, 2018,29(9): 2799-2820. |
| 周余阳, 程光, 郭春生, 等. 移动目标防御的攻击面动态转移技术研究综述[J]. 软件学报, 2018,29(9): 2799-2820. | |
| [9] | CARROLL T E, CROUSE M, FULP E W, et al. Analysis of Network Address Shuffling as a Moving Target Defense[C]//IEEE. IEEE International Conference on Communications, June 10-14, 2014, Sydney, NSW, Australia. NJ: IEEE, 2014: 701-706. |
| [10] | ZHANG Chaokun, CUI Yong, TANG Heyi, et al. State-of-the-Art Survey on Software-defined Networking (SDN)[J]. Journal of Software, 2015,26(1): 62-81. |
| 张朝昆, 崔勇, 唐翯祎, 等. 软件定义网络(SDN)研究进展[J]. 软件学报, 2015,26(1): 62-81. | |
| [11] | ZUO Qingyun, CHEN Ming, ZHAO Guangsong, et al. Research on SDN Technology Based on OpenFlow[J]. Journal of Software, 2013,24(5): 1078-1097. |
| 左青云, 陈鸣, 赵广松, 等. 基于OpenFlow的SDN技术研究[J]. 软件学报, 2013,24(5): 1078-1097. | |
| [12] | KEWLEY D, FINK R, LOWRY J, et al. Dynamic Approaches to Thwart Adversary Intelligence Gathering[C]//IEEE. DARPA Information Survivability Conference Exposition II, DISCEX 2001, June 12-14, 2001, Anaheim, CA, USA. NJ: IEEE, 2001: 176-185. |
| [13] | ANTONATOS S, AKRITIDIS P, MARKATOS E P, et al. Defending against Hitlist Worms Using Network Address Space Randomization[C]//ACM. The 2005 ACM Workshop on Rapid Malcode, November 11, 2005, Fairfax, Virginia, USA. New York: ACM, 2005: 30-40. |
| [14] | AL-SHAER E, DUAN Qi, JAFARIAN J H. Random Host Mutation for Moving Target Defense[M]//Springer. Security and Privacy in Communication Networks. Heidelberg: Springer, 2013: 310-327. |
| [15] | SHARMA D P, KIM D S, YOON S, et al. FRVM: Flexible Random Virtual IP Multiplexing in Software-defined Networks[C]//IEEE. 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), August 1-3, 2018, New York, NY, USA. NJ: IEEE, 2018: 579-587. |
| [16] | JAFARIAN J H, AL-SHAER E, DUAN Qi. Openflow Random Host Mutation: Transparent Moving Target Defense Using Software Defined Networking[C]//ACM. The First Workshop on Hot Topics in Software Defined Networks, August 13, 2012, New York, NY, USA. New York: ACM, 2012: 127-132. |
| [17] | NOMAN H M, JASIM M N. POX Controller and Open Flow Performance Evaluation in Software Defined Networks (SDN) Using Mininet Emulator[EB/OL]. https://www.researchgate.net/publication/343586922_POX_Controller_and_Open_Flow_Performance_Evaluation_in_Software_Defined_Networks_SDN_Using_Mininet_Emulator, 2020-09-20. |
| [18] | CHASIB S A, KHADIM A. Software Defined Network for Data Center Using Open Flow Protocol[J]. International Journal of Scientific Engineering and Technology, 2016,5(12): 537-541. |
| [19] | LEI Cheng, MA Duohe, ZHANG Hongqi, et al. Network Moving Target Defense Technique Based on Optimal Forwarding Path Migration[J]. Journal on Communications, 2017,38(3): 133-143. |
| 雷程, 马多贺, 张红旗, 等. 基于最优路径跳变的网络移动目标防御技术[J]. 通信学报, 2017,38(3): 133-143. | |
| [20] | ZHOU Zan, KUANG Xiaohui, SUN Limin, et al. Endogenous Security Defense against Deductive Attack: When Artificial Intelligence Meets Active Defense for Online Service[J]. IEEE Communications Magazine, 2020,58(6): 58-64. |
| [1] | 王鹃, 杨泓远, 樊成阳. 一种基于多阶段攻击响应的SDN动态蜜罐[J]. 信息网络安全, 2021, 21(1): 27-40. |
| [2] | 张涛, 芦斌, 李玎, 何康. 一种基于软件定义网络的主机指纹抗探测模型[J]. 信息网络安全, 2020, 20(7): 42-52. |
| [3] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [4] | 王健, 王语杰, 韩磊. 基于突变模型的SDN环境中DDoS攻击检测方法[J]. 信息网络安全, 2020, 20(5): 11-20. |
| [5] | 周亚球, 任勇毛, 李琢, 周旭. 基于SDN的科学DMZ研究与实现[J]. 信息网络安全, 2019, 19(9): 134-138. |
| [6] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [7] | 石悦, 李相龙, 戴方芳. 一种基于属性基加密的增强型软件定义网络安全框架[J]. 信息网络安全, 2018, 18(1): 15-22. |
| [8] | 李剑锋, 刘渊, 张浩, 王晓锋. 面向IaaS云平台的路由转发优化研究与实现[J]. 信息网络安全, 2017, 17(9): 10-15. |
| [9] | 徐洋, 陈燚, 何锐, 谢晓尧. SDN中DDoS检测及多层防御方法研究[J]. 信息网络安全, 2017, 17(12): 22-28. |
| [10] | 齐宇. SDN安全研究[J]. 信息网络安全, 2016, 16(9): 69-72. |
| [11] | 陈颖聪, 陈广清, 陈智明, 万能. 面向智能电网SDN的二进制代码分析漏洞扫描方法研究[J]. 信息网络安全, 2016, 16(7): 35-39. |
| [12] | 蒋宽, 杨鹏. 基于数据包回溯的软件定义网络中的故障排除[J]. 信息网络安全, 2016, 16(3): 71-76. |
| [13] | 武泽慧, 魏强. 基于OwnShip-Proof模型的软件定义网络控制器集群故障安全恢复方法[J]. 信息网络安全, 2016, 16(12): 13-18. |
| [14] | 王刚. 一种基于SDN技术的多区域安全云计算架构研究[J]. 信息网络安全, 2015, 15(9): 20-24. |
| [15] | 周益周, 王斌, 谢小权. 云环境下软件定义入侵检测系统设计[J]. 信息网络安全, 2015, 15(9): 191-195. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 435
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 587
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||