信息网络安全 ›› 2023, Vol. 23 ›› Issue (9): 108-117.doi: 10.3969/j.issn.1671-1122.2023.09.010
基于HotStuff改进的多主节点共识算法
- 1.西安电子科技大学计算机科学与技术学院,西安 710068
2.北京电子科技学院网络空间安全系,北京 100070
-
收稿日期:2023-02-21出版日期:2023-09-10发布日期:2023-09-18 -
通讯作者:公鹏飞 E-mail:970903247@qq.com -
作者简介:公鹏飞(1997—),男,山东,硕士研究生,主要研究方向为区块链共识算法|谢四江(1971—),男,湖北,正高级工程师,硕士,主要研究方向为密码系统、量子保密和通信网络安全体系|程安东(1998—),男,山西,硕士研究生,主要研究方向为量子安全和区块链 -
基金资助:广东省重点研发计划(2020B03030100001)
The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff
GONG Pengfei1( ), XIE Sijiang1,2, CHENG Andong2
), XIE Sijiang1,2, CHENG Andong2
- 1. College of Computer Science and Technology, Xi’an University of Electronic Technology, Xi’an 710068, China
2. Department of Cyberspace Security, Beijing Electronic Science and Technology Institute, Beijing 100070, China
-
Received:2023-02-21Online:2023-09-10Published:2023-09-18 -
Contact:GONG Pengfei E-mail:970903247@qq.com
摘要:
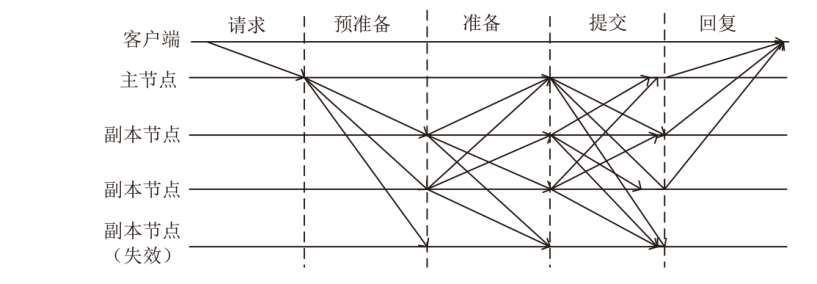
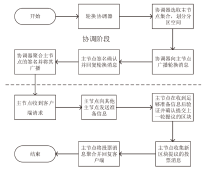
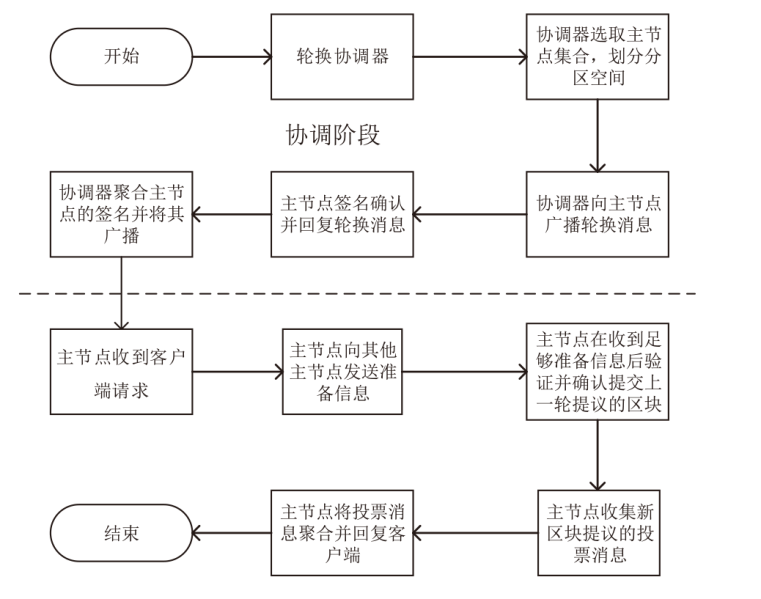
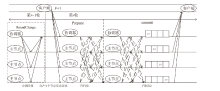
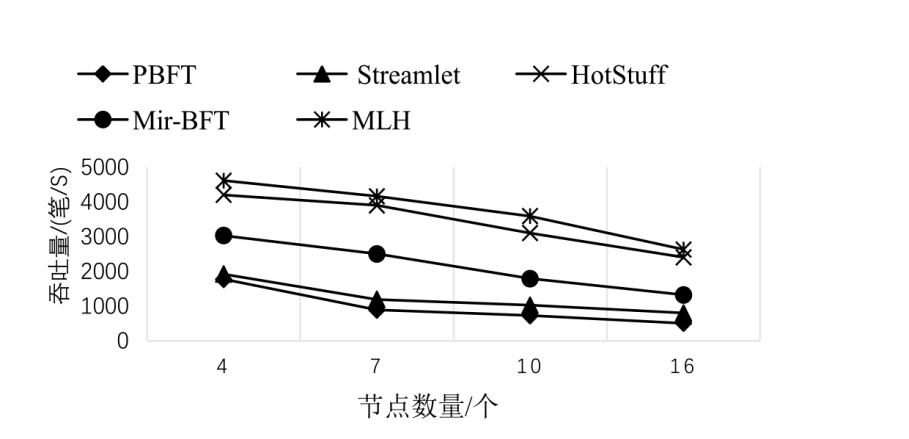
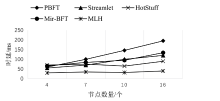
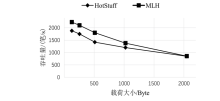
针对区块链中拜占庭容错(Byzantine Fault Tolerance,BFT)类共识算法存在的性能瓶颈问题,文章提出一种基于HotStuff改进的多主节点共识算法,即MLH (Multi Leader HotStuff)共识算法。该算法引入了不在关键路径上的协调阶段,结合轮次内收集投票、跨轮次提交区块等机制,令多个节点同时成为主节点,使算法可以并行提交区块,提升了算法的计算效率。另外,通过结合门限签名与聚合签名降低了分区内的通信复杂度,使MLH算法在连续视图切换的情况下仍保持线性通信复杂度不变。实验结果表明,MLH算法在时延和吞吐量方面都有较好的表现。
中图分类号:
引用本文
公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117.
GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff[J]. Netinfo Security, 2023, 23(9): 108-117.
| [1] |
LAMPORT L, SHOSTAK R, PEASE M. The Byzantine Generals Problem[J]. ACM Transactions on Programming Languages and Systems, 2019, 4(3): 382-401.
doi: 10.1145/357172.357176 URL |
| [2] | CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance[C]// ACM. The Third Symposium on Operating Systems Design and Implementation. New York: ACM, 1999: 173-186. |
| [3] | BUCHMAN E, KWON J, MILOSEVIC Z. The Latest Gossip on BFT Consensus[EB/OL]. (2018-07-13)[2023-01-13]. https://arxiv.org/abs/1807.04938. |
| [4] | YIN Maofan, MALKHI D, REITER M K, et al. HotStuff: BFT Consensus with Linearity and Responsiveness[C]// ACM. The 2019 ACM Symposium on Principles of Distributed Computing. New York: ACM, 2019: 347-356. |
| [5] | CHAN B Y, SHI E. Streamlet: Textbook Streamlined Blockchains[C]// ACM. The 2nd ACM Conference on Advances in Financial Technologies. New York: ACM, 2020: 1-11. |
| [6] | JALALZAI M M, NIU Jianyu, FENG Chen, et al. Fast-Hotstuff: A Fast and Resilient Hotstuff Protocol[EB/OL]. (2020-10-22)[2023-01-13]. https://arxiv.org/abs/2010.11454. |
| [7] | GUETA G G, ABRAHAM I, GROSSMAN S, et al. SBFT: A Scalable and Decentralized Trust Infrastructure[C]// IEEE. 2019 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York: IEEE, 2019: 568-580. |
| [8] | BUCHMAN E. Tendermint: Byzantine Fault Tolerance in the Age of Blockchains[D]. Guelph: University of Guelph, 2016. |
| [9] | BUTERIN V, GRIFFITH V. Casper the Friendly Finality Gadget[EB/OL]. (2017-10-25)[2023-01-13]. https://arxiv.org/abs/1710.09437. |
| [10] | SHI E. Streamlined Blockchains: A Simple and Elegant Approach (A Tutorial and Survey)[C]// Springer. ASIACRYPT 2019: 25th International Conference on the Theory and Application of Cryptology and Information Security. Berlin: Springer, 2019: 3-17. |
| [11] | ZHANG Baochen, KONG Lanju, LI Qingzhong, et al. EB-BFT: An Elastic Batched BFT Consensus Protocol in Blockchain[J]. Future Generation Computer Systems, 2023(139): 267-279. |
| [12] | LIU Yuan, AI Zhengpeng, TIAN Mengmeng, et al. DSBFT: A Delegation Based Scalable Byzantine False Tolerance Consensus Mechanism[C]// Springer. International Conference on Algorithms and Architectures for Parallel Processing (ICA3PP 2020). Berlin: Springer, 2020: 426-440. |
| [13] | ABSPOEL M, ATTEMA T, RAMBAUD M. Malicious Security Comes for Free in Consensus with Leaders[C]// ACM. The 2021 ACM Symposium on Principles of Distributed Computing(PODC’21). New York: ACM, 2020: 195-198. |
| [14] | GELASHVILI R, KOKORIS-KOGIAS L, SONNINO A, et al. Jolteon and Ditto: Network-Adaptive Efficient Consensus with Asynchronous Fallback[C]// Springer. Financial Cryptography and Data Security:26th International Conference. Berlin: Springer, 2022: 296-315. |
| [15] | GIRIDHARAN N, HOWARD H, ABRAHAM I, et al. No-Commit Proofs: Defeating Livelock in BFT[EB/OL]. (2021-09-28)[2023-01-13]. https://eprint.iacr.org/2021/1308.pdf. |
| [16] | ALQAHTANI S, DEMIRBAS M. Bottlenecks in Blockchain Consensus Protocols[C]// IEEE. 2021 IEEE International Conference on Omni-Layer Intelligent Systems (COINS). New York: IEEE, 2021: 1-8. |
| [17] | GAI Fangyu, FARAHBAKHSH A, NIU Jianyu, et al. Dissecting the Performance of Chained-BFT[C]// IEEE. 2021 IEEE 41st International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2021: 595-606. |
| [18] | AILIJIANG A, CHARAPKO A, DEMIRBAS M. Dissecting the Performance of Strongly-Consistent Replication Protocols[C]// ACM. The 2019 International Conference on Management of Data. New York: ACM, 2019: 1696-1710. |
| [19] | YANG Yin. LinBFT: Linear-Communication Byzantine Fault Tolerance for Public Blockchains[EB/OL]. (2018-07-05)[2023-01-13]. https://arxiv.org/abs/1807.01829v1. |
| [20] | STATHAKOPOULOU C, DAVID T, VUKOLIC M. Mir-BFT: High-Throughput BFT for Blockchains[EB/OL]. (2019-06-13)[2023-01-13]. https://arxiv.org/abs/1906.05552. |
| [21] | AVARIKIOTI Z, HEIMBACH L, SCHMID R, et al. FnF-BFT: Exploring Performance Limits of BFT Protocols[EB/OL]. (2020-09-04)[2023-01-13]. https://arxiv.org/abs/2009.02235. |
| [22] | GUPTA S, HELLINGS J, SADOGHI M. RCC: Resilient Concurrent Consensus for High-Throughput Secure Transaction Processing[C]// IEEE. 2021 IEEE 37th International Conference on Data Engineering (ICDE). New York: IEEE, 2021: 1392-1403. |
| [23] | BARCELONA C S. Mencius: Building Efficient Replicated State Machines for WANs[C]// USENIX. 8th USENIX Symposium on Operating Systems Design and Implementation (OSDI 08). Berlin: USENIX, 2008: 369-384. |
| [24] | BONEH D, LYNN B, SHACHAM H. Short Signatures from the Weil Pairing[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security (ASIACRYPT 2001). Berlin: Springer, 2001: 514-532. |
| [25] | CACHIN C, SHOUP V. Random Oracles in Constantinople: Practical Asynchronous Byzantine Agreement Using[C]// ACM. The 19th ACM Symposium on Principles of Distributed Computing. New York: ACM, 2000: 1-26. |
| [26] | SHOUP V. Practical Threshold Signatures[C]// Springer. EUROCRYPT 2000:International Conference on the Theory and Application of Cryptographic Techniques Bruges. Berlin:Springer, 2000: 207-220. |
| [27] | KAKLAMANIS I, YANG Lei, ALIZADEH M. Coded Broadcast for Scalable Leader-Based BFT Consensus[C]// ACM. 2022 ACM SIGSAC Conference on Computer and Communications Security(CCS’22). New York: ACM, 2022: 3375-3377. |
| [1] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [2] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| [3] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [4] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [5] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [6] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [7] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [8] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [9] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [10] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [11] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [12] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [13] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [14] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [15] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||