信息网络安全 ›› 2023, Vol. 23 ›› Issue (9): 95-107.doi: 10.3969/j.issn.1671-1122.2023.09.009
基于动态默克尔哈希树的跨链数据一致性验证模型
- 南京航空航天大学计算机科学与技术学院,南京 211106
-
收稿日期:2023-06-27出版日期:2023-09-10发布日期:2023-09-18 -
通讯作者:张玉书 E-mail:yushu@nuaa.edu.cn -
作者简介:赵佳豪(1998—),男,安徽,硕士研究生,主要研究方向为区块链与密码学|蒋佳佳(1997—),女,山东,博士研究生,主要研究方向为区块链与密码学|张玉书(1987—),男,江苏,教授,博士,CCF会员,主要研究方向为多媒体安全与人工智能、区块链与物联网安全、云计算与大数据安全 -
基金资助:国家重点研发计划(2020YFB1005500);南京航空航天大学科研与实践创新计划(xcxjh20221616)
Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree
ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu( )
)
- College of Computer Science and Technology, Nanjing University of Aeronautics and Astronautics, Nanjing 211106, China
-
Received:2023-06-27Online:2023-09-10Published:2023-09-18 -
Contact:ZHANG Yushu E-mail:yushu@nuaa.edu.cn
摘要:
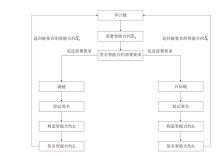
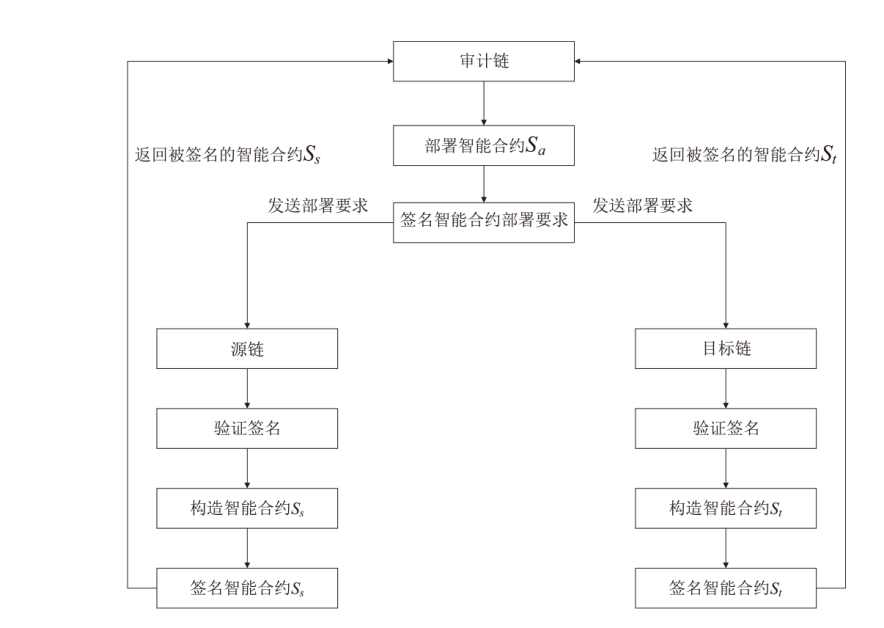
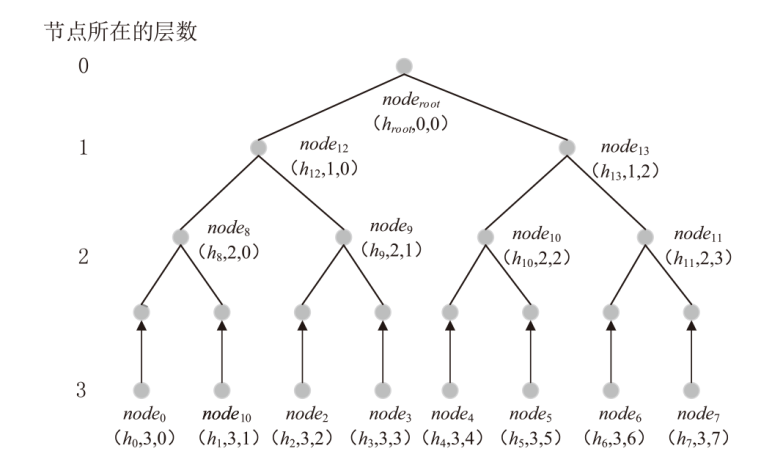
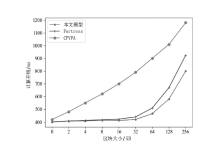
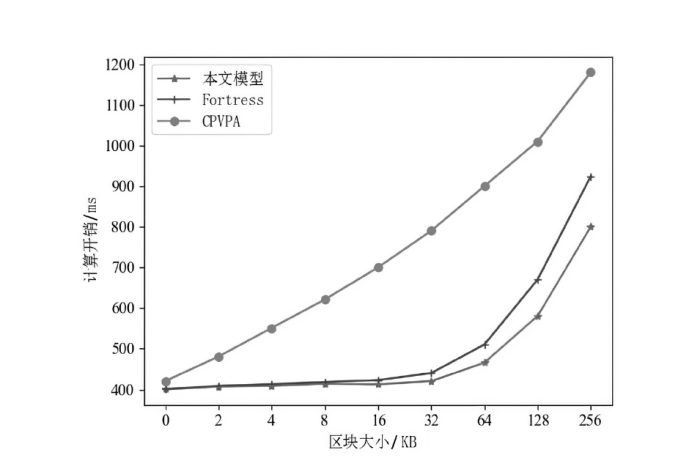
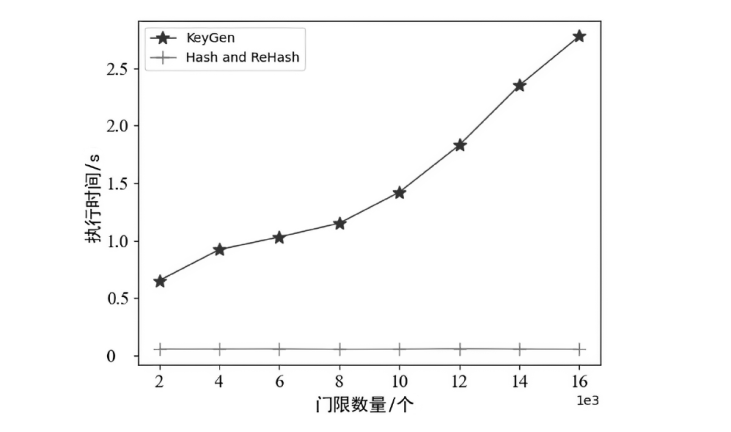
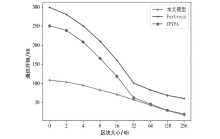
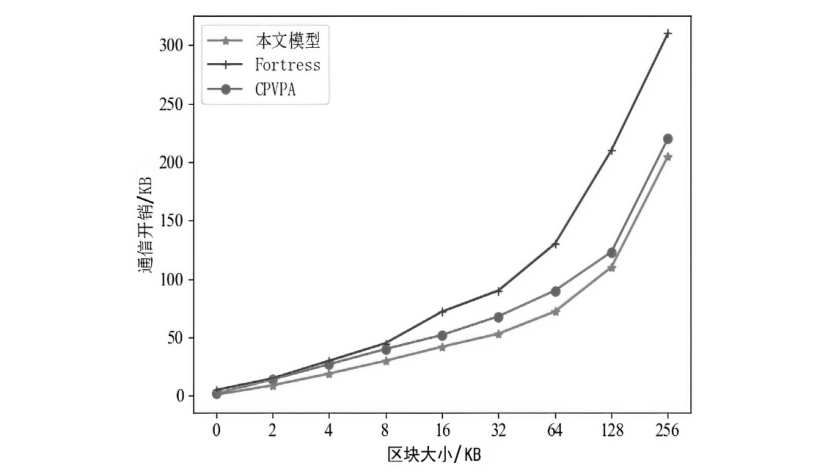
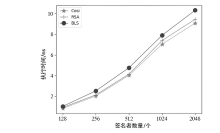
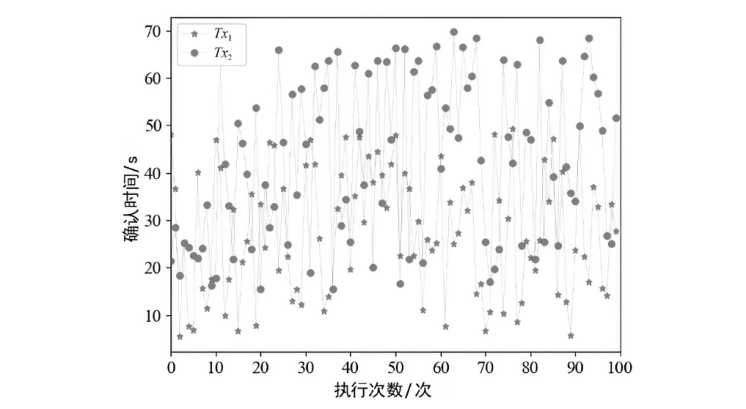
目前,区块链由于其高度的去中心化以及不可篡改的特性被广泛应用于不同领域,文章以解决区块链在应用过程中的链间数据交互一致性无法保证以及不支持数据动态更新的问题为研究目标,设计了一种去中心化的数据一致性审计模型,该模型采用跨链技术来实现异构区块链之间数据的安全可信共享,利用去中心化的变色龙哈希函数构建动态的默克尔哈希树以实现数据的动态更新操作,引入审计链对源链和目标链之间的数据交互进行监管,并利用Cosi多重签名算法来保证数据传输过程中的一致性。经过理论分析和实验验证,结果表明,该模型采用的Cosi算法在时间开销和可扩展性方面与目前主流多重签名算法相比具有较大优势。此外,本文模型在时间开销和通信开销方面与常见的审计模型相比有较大优势,能够以较小的成本完成相同的审计任务,并且可以达到99%的数据审计一致性保证概率。
中图分类号:
引用本文
赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107.
ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree[J]. Netinfo Security, 2023, 23(9): 95-107.
| [1] | CHEN Jing, YAO Shixiong, YUAN Quan, et al. Certchain: Public and Efficient Certificate Audit Based on Blockchain for TLS Connections[C]// IEEE. 37th IEEE Conference on Computer Communications. New York: IEEE, 2018: 2060-2068. |
| [2] |
KUBILAY M Y, KIRAZ M S, MANTAR H A. CertLedger: A New PKI Model with Certificate Transparency Based on Blockchain[J]. Computers & Security, 2019, 85(2): 333-352.
doi: 10.1016/j.cose.2019.05.013 URL |
| [3] | CAI Chengjun, ZHENG Yifeng, DU Yuefeng, et al. Towards Private, Robust, and Verifiable Crowdsensing Systems via Public Blockchains[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(4): 1893-1907. |
| [4] |
AUJLA G S, JINDAL A. A Decoupled Blockchain Approach for Edge-Envisioned IoT-Based Healthcare Monitoring[J]. IEEE Journal on Selected Areas in Communications, 2020, 39(2): 491-499.
doi: 10.1109/JSAC.49 URL |
| [5] | PAN Chen, LIU Zhiqiang, LIU Zhen, et al. Research on Scalability of Blockchain Technology: Problems and Methods[J]. Journal of Computer Research and Development, 2018, 55(10): 2099-2110. |
| 潘晨, 刘志强, 刘振, 等. 区块链可扩展性研究:问题与方法[J]. 计算机研究与发展, 2018, 55(10): 2099-2110. | |
| [6] | BACK A, CORALLO M, DASHJR L, et al. Enabling Blockchain Innovations with Pegged Sidechains[J]. Open Science Review, 2014, 72(3): 201-224. |
| [7] | WOOD G. Polkadot: Vision for a Heterogeneous Multi-Chain Framework[J]. White Paper, 2016, 21: 2327-4662. |
| [8] | ZHANG Shitong, QIN Bo, ZHENG Haibin. Research on the Protocol of Multiple Cross-Chains Based on the Hash Lock[J]. Cyberspace Security, 2018, 9(11): 57-62, 67. |
| 张诗童, 秦波, 郑海彬. 基于哈希锁定的多方跨链协议研究[J]. 网络空间安全, 2018, 9(11): 57-62,67. | |
| [9] | ATZEI N, BARTOLETTI M, CIMOLI T. A Survey of Attacks on Ethereum Smart Contracts (SoK)[C]// Springer. 4th International Conference on Principles of Security and Trust. Berlin: Springer, 2017: 164-186. |
| [10] |
SHEN Jian, SHEN Jun, CHEN Xiaofeng, et al. An Efficient Public Auditing Protocol with Novel Dynamic Structure for Cloud Data[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(10): 2402-2415.
doi: 10.1109/TIFS.2017.2705620 URL |
| [11] | HE Kun, CHEN Jing, YUAN Quan, et al. Dynamic Group-Oriented Provable Data Possession in the Cloud[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(3): 1394-1408. |
| [12] | PATIL J, CHAUDHARI S. Privacy Preserving and Dynamic Audit Service for Secure Cloud Storage[C]// IEEE. 7th International Conference on Smart City and Emerging Technology (ICSCET). New York: IEEE, 2018: 1-6. |
| [13] | ZHANG Yushu, JIANG Jiajia, DONG Xuewen, et al. BeDCV: Blockchain-Enabled Decentralized Consistency Verification for Cross-Chain Calculation[J]. IEEE Transactions on Cloud Computing, 2022, 28(2): 1-12. |
| [14] |
JIANG Jiajia, ZHANG Yushu, ZHU Youwen, et al. DCIV: Decentralized Cross-Chain Data Integrity Verification with Blockchain[J]. Journal of King Saud University-Computer and Information Sciences, 2022, 34(10): 7988-7999.
doi: 10.1016/j.jksuci.2022.07.015 URL |
| [15] |
JIA Meng, CHEN Jing, HE Kun, et al. Redactable Blockchain from Decentralized Chameleon Hash Functions[J]. IEEE Transactions on Information Forensics and Security, 2022, 17(6): 2771-2783.
doi: 10.1109/TIFS.2022.3192716 URL |
| [16] | SYTA E, TAMAS I, VISHER D, et al. Keeping Authorities "Honest or Bust" with Decentralized Witness Cosigning[C]// IEEE. 37th IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2016: 526-545. |
| [17] | LI Dawei, LIU Jianwei, TANG Zongxun, et al. AgentChain: A Decentralized Cross-Chain Exchange System[C]// IEEE. 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2019: 491-498. |
| [18] | TSAI W T, BLOWER R, ZHU Yan, et al. A System View of Financial Blockchains[C]// IEEE. 10th IEEE Symposium on Service-Oriented System Engineering. New York: IEEE, 2016: 450-457. |
| [19] | HE Yunhua, ZHANG Cui, WU Bin, et al. Cross-Chain Trusted Service Quality Computing Scheme for Multi-Chain Model-Based 5G Network Slicing SLA[J]. IEEE Internet of Things Journal, 2021, 14(10): 12126-12139. |
| [20] | ATENIESE G, PIETRO D R, MANCINI L V, et al. Scalable and Efficient Provable Data Possession[C]// ACM. 4th International Conference on Security and Privacy in Communication Netowrks. New York: ACM, 2008: 1-10. |
| [21] |
TIAN Hui, CHEN Yuxiang, CHANG C C, et al. Dynamic-Hash-Table Based Public Auditing for Secure Cloud Storage[J]. IEEE Transactions on Services Computing, 2015, 10(5): 701-714.
doi: 10.1109/TSC.2015.2512589 URL |
| [22] | ERWAY C C, KUPCU A, PAPAMANTHOU C, et al. Dynamic Provable Data Possession[J]. ACM Transactions on Information and System Security (TISSEC), 2015, 17(4): 1-29. |
| [23] |
WANG Cong, WANG Qian, REN Kui, et al. Toward Secure and Dependable Storage Services in Cloud Computing[J]. IEEE Transactions on Services Computing, 2012, 5(2): 220-232.
doi: 10.1109/TSC.2011.24 URL |
| [24] | CAMENISCH J, DERLER D, KRENN S, et al. Chameleon-Hashes with Ephemeral Trapdoors[C]// Springer. Public Key Cryptography. Berlin:Springer, 2017: 152-182. |
| [25] | BELLARE M, NEVEN G. Multi-Signatures in the Plain Public-Key Model and a General Forking Lemma[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 390-399. |
| [26] | LYNN B. The Pairing-Based Cryptography (PBC) Library[EB/OL]. (2010-06-05)[2023-06-10]. http://crypto.stanford.edu/pbc/. |
| [1] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [2] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [3] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [4] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [5] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [6] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [7] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [8] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [9] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [10] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [11] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [12] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [13] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [14] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [15] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||