信息网络安全 ›› 2023, Vol. 23 ›› Issue (9): 118-128.doi: 10.3969/j.issn.1671-1122.2023.09.011
基于中国剩余定理秘密共享的切换认证协议
- 重庆邮电大学通信与信息工程学院,重庆 400065
-
收稿日期:2023-06-15出版日期:2023-09-10发布日期:2023-09-18 -
通讯作者:戴玉 E-mail:s210131030@stu.cqupt.edu.cn -
作者简介:戴玉(1998—),女,重庆,硕士研究生,主要研究方向为车联网身份认证|周非(1977—),男,湖北,教授,博士,主要研究方向为网络信息安全、信息与信号处理|薛丹(1998—),女,重庆,硕士研究生,主要研究方向为车联网隐私保护 -
基金资助:国家自然科学基金(62271096)
Handover Authentication Protocol Based on Chinese Remainder Theorem Secret Sharing
- School of Communication and Information Engineering, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2023-06-15Online:2023-09-10Published:2023-09-18 -
Contact:DAI Yu E-mail:s210131030@stu.cqupt.edu.cn
摘要:
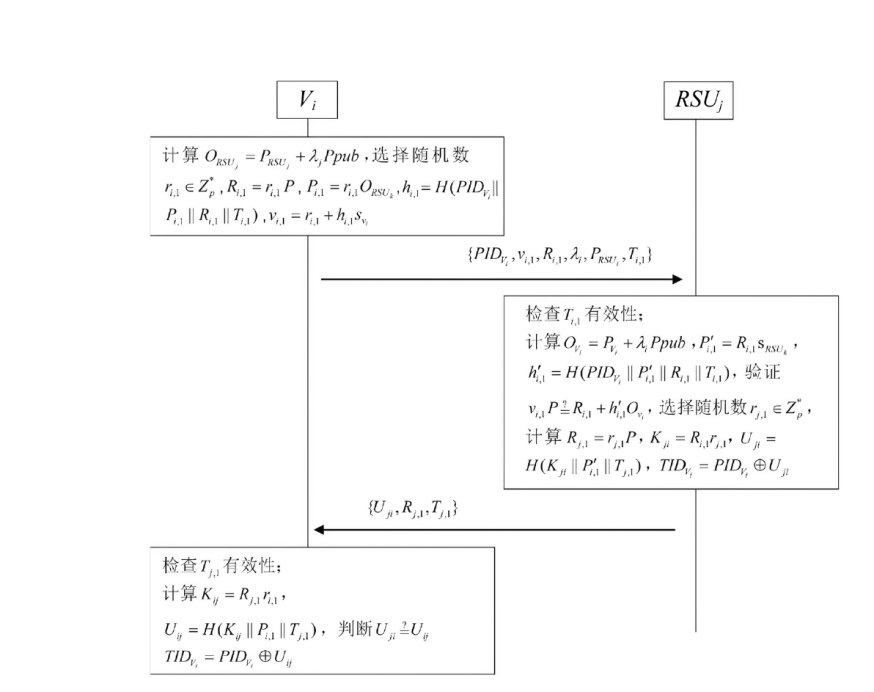
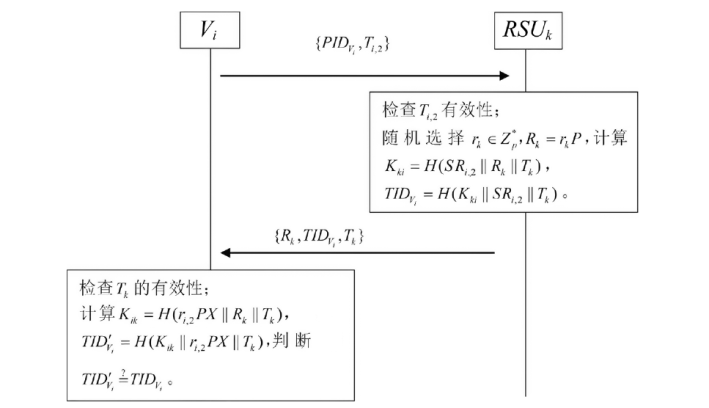
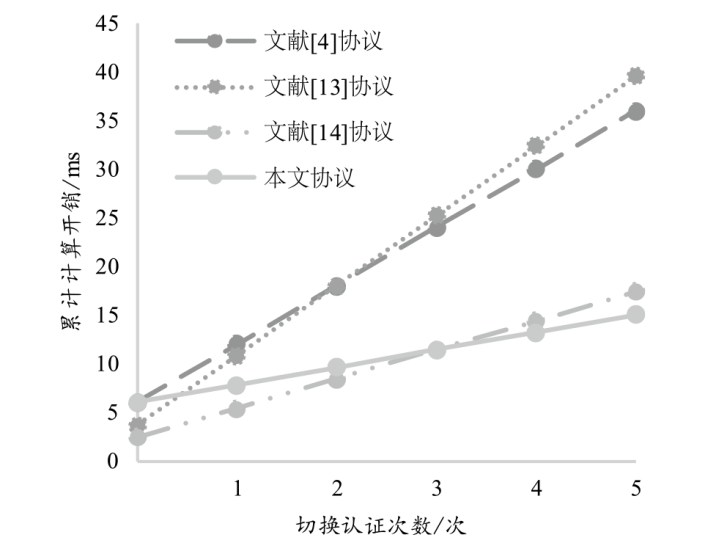
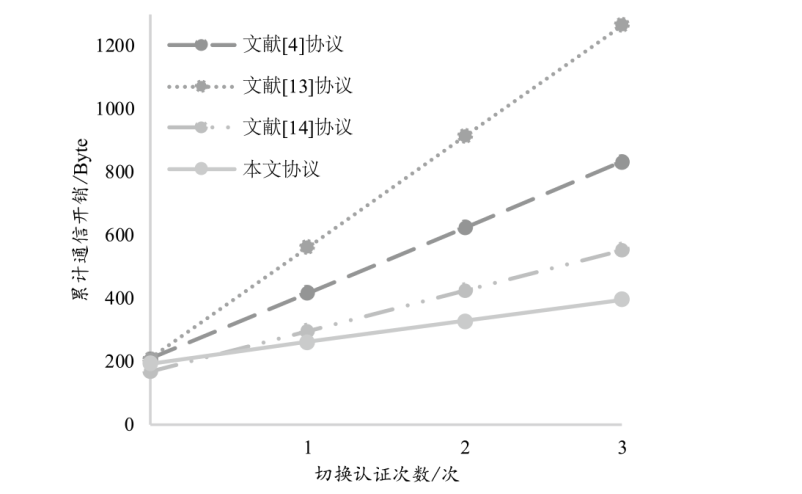
随着智能汽车行业的发展,车联网安全的应用意义与发展前景备受关注,而身份认证是车联网安全的第一道大门。目前关于车联网身份认证协议的研究重点大多放在车联网中两种实体间的首次认证与批量认证过程,对实体间切换认证过程的协议关注不足,并且现有切换认证协议大多基于区块链进行设计。针对上述情况,文章运用椭圆曲线加密和中国剩余定理秘密共享的技术,在不使用区块链技术的情况下提出了一个基于中国剩余定理秘密共享的车对路切换认证协议,实现了车辆与路边单元双向的初始化认证和切换认证,提高了车辆在路边单元组中切换认证的认证效率。文章首先通过理论推导证明了该协议的正确性,然后利用随机预言机模型证明了该协议的语义安全性,最后对该协议的安全性、计算开销和通信开销三方面进行性能分析,并与其他协议的性能进行对比。结果表明,随着切换认证次数的增加,该协议的累计计算开销和累计通信开销相较于其他协议增长更慢,对资源的消耗更低。
中图分类号:
引用本文
戴玉, 周非, 薛丹. 基于中国剩余定理秘密共享的切换认证协议[J]. 信息网络安全, 2023, 23(9): 118-128.
DAI Yu, ZHOU Fei, XUE Dan. Handover Authentication Protocol Based on Chinese Remainder Theorem Secret Sharing[J]. Netinfo Security, 2023, 23(9): 118-128.
表4
计算开销对比
| 协议 | 初始化认证/ms | 切换认证/ms | |||
|---|---|---|---|---|---|
| Vi | RSUj | Vi | RSUj | RSUk | |
| 文献[ | 5TEsm+5TH= 2.9985 | 5TEsm+4TH= 2.9984 | 5TEsm+5TH= 2.9985 | 0 | 5TEsm+4TH= 2.9984 |
| 文献[ 协议 | 3TEsm+6TH= 1.7994 | 3TEsm+6TH= 1.7994 | 3TEsm+6TH= 1.7994 | 3TEsm+4TH= 1.7992 | 6TEsm+11TH= 3.5987 |
| 文献[ | 3TEsm+11TH= 1.7999 | TEsm+9TH= 0.6005 | 6TH=0.0006 | 0 | 4TEsm+TEap+ 12TH=2.9984 |
| 本文 协议 | 4TEsm+TEap+2TH= 2.4009 | 6TEsm+2TEap+ 2TH=3.6024 | TEsm+2TH= 0.5998 | 0 | 2TEsm+TH= 1.1993 |
| [1] | DUREJA A, SANGWAN S. A Review: Efficient Transportation—Future Aspects of IoV[J]. Evolving Technologies for Computing, Communication and Smart World, 2020, 694: 97-108. |
| [2] |
FAROOQ S M, HUSSAIN S M S, USTUN T S. A Survey of Authentication Techniques in Vehicular Ad-hoc Networks[J]. IEEE Intelligent Transportation Systems Magazine, 2020, 13(2): 39-52.
doi: 10.1109/MITS.2020.2985024 URL |
| [3] |
ZHANG Jing, CUI Jie, ZHONG Hong, et al. PA-CRT: Chinese Remainder Theorem Based Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-hoc Networks[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(2): 722-735.
doi: 10.1109/TDSC.8858 URL |
| [4] | XIE Qi, DING Zixuan, ZHENG Panpan. Provably Secure and Anonymous V2I and V2V Authentication Protocol for VANETs[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(7): 1-10. |
| [5] |
KUMAR P, OM H. Secure and Efficient Cache-Based Authentication Scheme for Vehicular Ad-Hoc Networks[J]. Wireless Networks, 2022, 28(7): 2821-2836.
doi: 10.1007/s11276-022-03003-y |
| [6] |
YANG Anjia, WENG Jian, YANG Kan, et al. Delegating Authentication to Edge: A Decentralized Authentication Architecture for Vehicular Networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 23(2): 1284-1298.
doi: 10.1109/TITS.2020.3024000 URL |
| [7] | SCOTT M. On the Efficient Implementation of Pairing-Based Protocols[C]// Springer. Cryptography and Coding:13th IMA International Conference. Berlin: Springer, 2011: 296-308. |
| [8] |
SHAH K, CHADOTRA S, TANWAR S, et al. Blockchain for IoV in 6G Environment: Review Solutions and Challenges[J]. Cluster Computing, 2022, 25(3): 1927-1955.
doi: 10.1007/s10586-021-03492-0 |
| [9] |
ANG L M, SENG K P, IJEMARU G K, et al. Deployment of IoV for Smart Cities: Applications, Architecture, and Challenges[J]. IEEE Access, 2018, 7: 6473-6492.
doi: 10.1109/ACCESS.2018.2887076 URL |
| [10] | KUMAR A, DAS D. EIoVChain: Towards Authentication and Secure Communication Based Blockchain for Internet of Vehicles (IoV)[C]// IEEE. 2021 IEEE International Conference on Blockchain. New York: IEEE, 2021: 47-54. |
| [11] | ZENG Ping, CHEN Zhijuan, MA Yingjie, et al. Blockchain-Based Privacy-Preserving Certificateless Authentication Scheme for Internet of Vehicles[J]. Application Research of Computers, 2021, 38(10): 2919-2925. |
| 曾萍, 陈志娟, 马英杰, 等. 基于区块链的IoV隐私保护认证方案设计[J]. 计算机应用研究, 2021, 38(10): 2919-2925. | |
| [12] |
HE Daojing, CHAN S, GUIZANI M. Handover Authentication for Mobile Networks: Security and Efficiency Aspects[J]. IEEE Network, 2015, 29(3): 96-103.
doi: 10.1109/MNET.2015.7113232 URL |
| [13] | DWIVEDI S K, AMIN R, VOLLALA S, et al. B-HAS: Blockchain-Assisted Efficient Handover Authentication and Secure Communication Protocol in VANETs[J]. IEEE Transactions on Network Science and Engineering, 2023, 23: 1-14. |
| [14] |
SON S, LEE J, PARK Y, et al. Design of Blockchain-Based Lightweight V2I Handover Authentication Protocol for VANET[J]. IEEE Transactions on Network Science and Engineering, 2022, 9(3): 1346-1358.
doi: 10.1109/TNSE.2022.3142287 URL |
| [15] |
NIRANJANAMURTHY M, NITHYA B N, JAGANNATHA S. Analysis of Blockchain Technology: Pros, Cons and SWOT[J]. Cluster Computing, 2019, 22: 14743-14757.
doi: 10.1007/s10586-018-2387-5 |
| [16] | CHEN Zewen, ZHANG Longjun, WANG Yumin, et al. A Group Signature Scheme Based on Chinese Remainder Theorem[J]. Acta Electronica Sinica, 2004, 32(7): 1062-1065. |
| 陈泽文, 张龙军, 王育民, 等. 一种基于中国剩余定理的群签名方案[J]. 电子学报, 2004, 32(7): 1062-1065. | |
| [17] | PANG Liaojun, PEI Qingqi, LI Huixian, et al. Secret Sharing Technology and Its Applications[M]. Beijing: Post & Telecom Press, 2017. |
| 庞辽军, 裴庆祺, 李慧贤, 等. 秘密共享技术及其应用[M]. 北京: 人民邮电出版社, 2017. | |
| [18] |
COPPERSMITH D. Cryptography[J]. IBM Journal of Research and Development, 1987, 31(2): 244-248.
doi: 10.1147/JRD.1987.5390134 URL |
| [19] |
KOBLITZ N, MENEZES A J. The Random Oracle Model: A Twenty-Year Retrospective[J]. Designs, Codes and Cryptography, 2015, 77: 587-610.
doi: 10.1007/s10623-015-0094-2 URL |
| [20] |
ALIMORADI R, ARKIAN H R, RAZAVIAN S M J, et al. Scalar Multiplication in Elliptic Curve Libraries[J]. Journal of Discrete Mathematical Sciences and Cryptography, 2021, 24(3): 657-666.
doi: 10.1080/09720529.2017.1378411 URL |
| [1] | 曹越, 吕臣臣, 孙娅苹, 张宇昂. 面向车联网环境的异常行为检测机制研究综述[J]. 信息网络安全, 2023, 23(4): 10-19. |
| [2] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [3] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [4] | 郎为民, 王雪丽, 张汉, 裴云祥. 一种基于秘密共享算法的安全数据去重方案[J]. 信息网络安全, 2020, 20(11): 43-50. |
| [5] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [6] | 吴志红, 赵建宁, 朱元, 陆科. 国密算法和国际密码算法在车载单片机上应用的对比研究[J]. 信息网络安全, 2019, 19(8): 68-75. |
| [7] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [8] | 王永建, 张健, 程少豫, 铁小辉. 面向云计算的同态加密改进设计[J]. 信息网络安全, 2017, 17(3): 21-26. |
| [9] | 袁超, 张浩, Gulliver Thomas Aaron. 车联网中协作车--车通信系统在N-Rayleigh信道下ASEP性能分析[J]. 信息网络安全, 2016, 16(3): 40-46. |
| [10] | 徐凌伟, 张浩, 王景景, 吴春雷. 车联网中车—车通信系统在n-Rayleigh信道下的性能分析[J]. 信息网络安全, 2014, 14(12): 65-70. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||