信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 1-16.doi: 10.3969/j.issn.1671-1122.2023.08.001
基于机器学习的模糊测试研究综述
王鹃1,2( ), 张冲1,2, 龚家新1,2, 李俊娥1,2
), 张冲1,2, 龚家新1,2, 李俊娥1,2
- 1.武汉大学国家网络安全学院,武汉 430072
2.武汉大学空天信息安全与可信计算教育部重点实验室,武汉 430072
-
收稿日期:2022-12-16出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:王鹃 E-mail:jwang@whu.edu.cn -
作者简介:王鹃(1976—),女,湖北,教授,博士,CCF高级会员,主要研究方向为系统和软件安全、可信计算、人工智能应用、云计算、物联网安全|张冲(1997—),男,河南,硕士研究生,主要研究方向为人工智能、漏洞挖掘|龚家新(1999—),男,安徽,硕士研究生,主要研究方向为软件安全、漏洞挖掘|李俊娥(1966—),女,湖北,教授,博士,CCF会员,主要研究方向为软件体系结构和网络安全 -
基金资助:国家自然科学基金(61872430);国家重点研发计划(2020AAA0107700);国家电网有限公司科技项目(520940210009)
Review of Fuzzing Based on Machine Learning
WANG Juan1,2( ), ZHANG Chong1,2, GONG Jiaxin1,2, LI Jun’e1,2
), ZHANG Chong1,2, GONG Jiaxin1,2, LI Jun’e1,2
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2022-12-16Online:2023-08-10Published:2023-08-08 -
Contact:WANG Juan E-mail:jwang@whu.edu.cn
摘要:
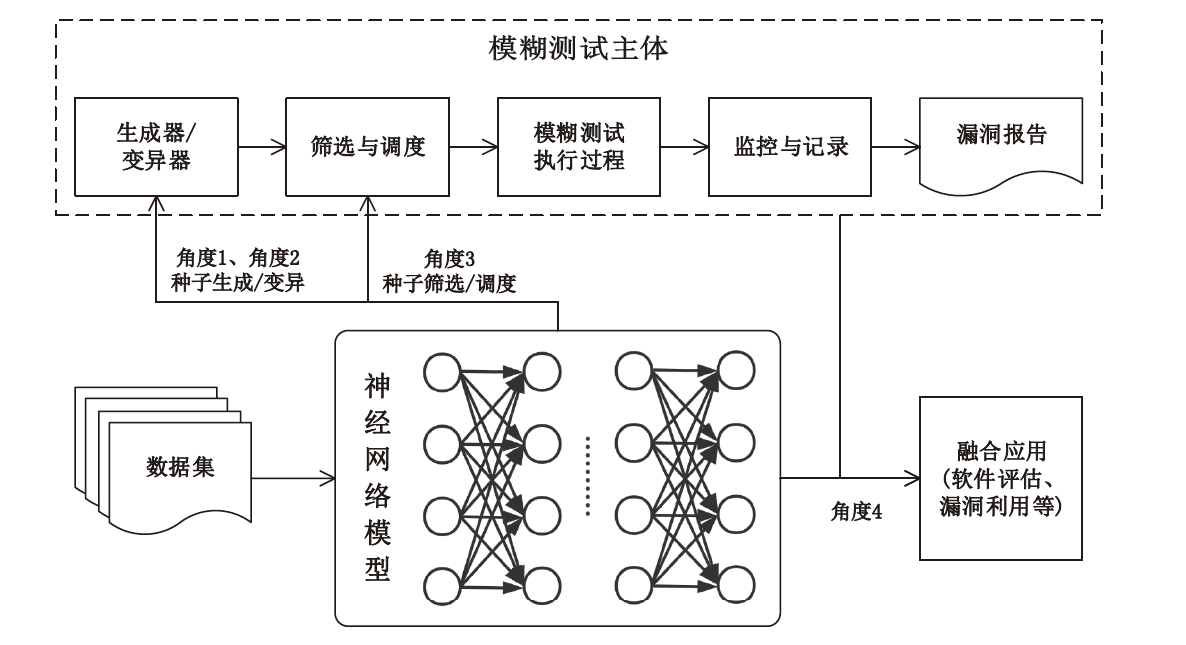
模糊测试是当今比较流行的漏洞挖掘技术之一。传统的模糊测试往往需要大量人工参与,测试周期较长且测试效果依赖于专家经验。近年来,机器学习应用广泛,这为软件安全测试技术注入了新活力。一些研究工作使用机器学习技术对模糊测试过程进行优化和改进,弥补了传统模糊测试技术的诸多缺陷。文章对基于机器学习的模糊测试技术进行了全面分析。首先,总结了常见的漏洞挖掘方法、模糊测试过程与分类以及传统模糊测试技术的不足;然后,从模糊测试的测试用例生成、变异、筛选和调度等角度入手,着重介绍了机器学习方法在模糊测试技术中的应用研究,并结合机器学习和模糊测试实现其他功能的研究工作;最后,基于现有的工作分析总结了目前研究的局限性和面临的挑战,并对该领域未来的发展方向进行了展望。
中图分类号:
引用本文
王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16.
WANG Juan, ZHANG Chong, GONG Jiaxin, LI Jun’e. Review of Fuzzing Based on Machine Learning[J]. Netinfo Security, 2023, 23(8): 1-16.
表1
测试用例生成工作中的机器学习应用
| 已有工作 | 发表时间 | 测试目标类型 | 模型输入 | 学习模型 | 模型功能 | |
|---|---|---|---|---|---|---|
| 文件 解析 | 文献[ | 2017 | PDF文件解析工具 | 文件字符流 | Char-RNN | 生成PDF 文件 |
| 文献[ | 2021 | 文件解析工具 | RNN(LSTM) | 学习文件结构并生成新文件 | ||
| 文献[ | 2018 | Web 浏览器 | One-hot 编码向量 | LSTM/GRU | 生成HTML文件 | |
| 文献[ | 2018 | 文件解析工具 | 文件文本 | Seq2Seq | 生成多种格式的文件 | |
| 文献[ | 2019 | PDF文件解析工具 | 指令序列 | RNN | 生成PDF页面指令流 | |
| 文献[ | 2019 | PDF文件解析工具 | PDF文件 | RNN、Seq2Seq | 生成PDF 文件 | |
| 协议 解析 | 文献[ | 2018 | 专有网络协议 | 网络数据包 | LSTM、Seq2Seq | 生成网络协议数据包 |
| 文献[ | 2019 | 网络协议 | 网络数据包 | Seq2seq-attention | 解析协议 规范 | |
| 文献[ | 2020 | Modbus TCP | Modbus TCP网络层数据包 | RNN | 学习协议数据单元的 语义 | |
| 文献[ | 2019 | 工业协议 解析工具 | 协议数据包 | Seq2Seq、LSTM | 生成虚假可信的协议 消息 | |
| 文献[ | 2018 | GAN(LSTM/CNN) | ||||
| 代码 解析 | 文献[ | 2018 | 编译器 | 程序代码 | LSTM | 推断代码 结构 |
| 文献[ | 2019 | C编译器 | C源程序 | Seq2Seq | 生成C 代码 | |
| 文献[ | 2020 | JavaScript 引擎 | AST序列 | LSTM | 生成JavaScript 程序 | |
| 文献[ | 2021 | JS源代码中单词的统计向量 | GPT-2 | |||
| 其他 | 文献[ | 2017 | 移动应用程序 | 自定义的行为模型向量表示 | RNN、Word2Vec | 生成上下文相关文本 |
| 文献[ | 2019 | GUI上下文的向量表示 | LSTM | 生成GUI行为输入 | ||
| 文献[ | 2019 | CPS | — | LSTM/SVR | 指导生成CPS测试 用例 | |
表2
测试用例变异工作中的机器学习应用
| 已有 工作 | 发表 时间 | 测试目标类型 | 模型输入 | 学习模型 | 模型功能 |
|---|---|---|---|---|---|
| 文献[ | 2017 | 文件解析工具 | 文件字节 序列 | Seq2Seq、LSTM | 预测种子 变异位置 |
| 文献[ | 2019 | 二进制程序 | 待测程序输入和输出 测试输入 字节序列 | NN | 近似模拟目标程序的逻辑分支,指导模糊器的种子突变 |
| 文献[ | 2020 | MTNN | |||
| 文献[ | 2022 | NN | |||
| 文献[ | 2018 | 二进制程序 | 测试程序的输入 | MAB | 预测变异算子概率分布 |
| 文献[ | 2018 | 二进制程序 | 文件字节 序列 | DQN | 优化变异选择策略 |
| 文献[ | 2018 | — | 包含状态、操作和奖励信息的向量 | Q-Learning | 指导生成高回报的输入 |
| 文献[ | 2022 | — | 测试程序的输入 | UCB1-Tuned | 预测Havoc堆叠次数和变异算子 |
表3
测试用例筛选和调度工作中的机器学习应用
| 已有工作 | 发表时间 | 模型输入 | 学习模型 | 模型功能 | |
|---|---|---|---|---|---|
| 种子 调度 | 文献[ | 2020 | 函数ACFG | Bi-LSTM | 预测代码块的脆弱性 |
| 文献[ | 2020 | 函数ACFG | 图嵌入 网络 | 预测脆弱性代码位置 | |
| 文献[ | 2019 | 指令字节码组成的执行路径 | LSTM | 预测路径脆弱性 | |
| 文献[ | 2020 | 种子特征向量 和对应标签 | 有监督 机器学习 | 预测测试用例的 模糊测试效果 | |
| 文献[ | 2021 | 种子集合 | UCB1 | 实现多级覆盖度的 分层调度 | |
| 文献[ | 2021 | 任务集合和 种子集合 | MAB | 进行种子选择 | |
| 测试用例筛选 | 文献[ | 2018 | AST | PCFG、Markov | 辅助进化算法中的适应度函数计算 |
| 文献[ | 2020 | HPC事件集 | MLP | 预测输入是否能触发异常 | |
| 文献[ | 2017 | AFL生成测试用例和执行结果 | DL | 分析变异得到的测试用例是否会到达新状态 | |
| 文献[ | 2018 | AFL生成的测试用例 | NN | 分析不同类型软件的变异模式 | |
| 文献[ | 2019 | 包含状态、操作和奖励信息的 向量 | NN | 指导生成高回报的输入 | |
| 文献[ | 2020 | 待测程序输入 和可访问性 | CNN | 预测测试用例的 目标可达性 | |
| [1] |
SUN Hongyu, HE Yuan, WANG Jice, et al. Application of Artificial Intelligence Technology in the Field of Security Vulnerability[J]. Journal on Communications, 2018, 39(8): 1-17.
doi: 10.11959/j.issn.1000-436x.2018137 |
|
孙鸿宇, 何远, 王基策, 等. 人工智能技术在安全漏洞领域的应用[J]. 通信学报, 2018, 39(8): 1-17.
doi: 10.11959/j.issn.1000-436x.2018137 |
|
| [2] | GU Mianxue, SUN Hongyu, HAN Dan, et al. Software Security Vulnerability Mining Based on Deep Learning[J]. Journal of Computer Research and Development, 2021, 58(10): 2140-2162. |
| 顾绵雪, 孙鸿宇, 韩丹, 等. 基于深度学习的软件安全漏洞挖掘[J]. 计算机研究与发展, 2021, 58(10): 2140-2162. | |
| [3] |
LECUN Y, BENGIO Y, HINTON G. Deep Learning[J]. Nature, 2015, 521(7553): 436-444.
doi: 10.1038/nature14539 |
| [4] |
DENG Li, YU Dong. Deep Learning: Methods and Applications[J]. Foundations and Trends in Signal Processing, 2014, 7(4): 197-387.
doi: 10.1561/2000000039 URL |
| [5] | SAAVEDRA G J, RODHOUSE K N, DUNLAVY D M, et al. A Review of Machine Learning Applications in Fuzzing[EB/OL]. (2019-08-04)[2022-10-07]. https://arxiv.org/pdf/1906.11133.pdf. |
| [6] | WANG Yan, JIA Peng, LIU Luping, et al. A Systematic Review of Fuzzing Based on Machine Learning Techniques[EB/OL]. (2020-08-18)[2022-10-07]. https://arxiv.org/abs/1908.01262. |
| [7] | ZOU Quanchen, ZHANG Tao, WU Runpu, et al. From Automation to Intelligence: Survey of Research on Vulnerability Discovery Techniques[J]. Journal of Tsinghua University (Science and Technology), 2018, 58(12): 1079-1094. |
| 邹权臣, 张涛, 吴润浦, 等. 从自动化到智能化:软件漏洞挖掘技术进展[J]. 清华大学学报(自然科学版), 2018, 58(12): 1079-1094. | |
| [8] |
MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44.
doi: 10.1145/96267.96279 URL |
| [9] | AMINI P. Fuzzing: Brute Force Vulnerability Discovery[M]. Boston: Addison Wesley Publishing Company, 2007. |
| [10] | CHA S K, WOO M, BRUMLEY D. Program-Adaptive Mutational Fuzzing[C]//IEEE. 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 725-741. |
| [11] | HOSCHELE M, ZELLER A. Mining Input Grammars from Dynamic Taints[C]//IEEE. 2016 31st IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2016: 720-725. |
| [12] | KAKSONEN R, LAAKSO M, TAKANEN A. Software Security Assessment Through Specification Mutations and Fault Injection[C]//Springer. Communications and Multimedia Security Issues of the New Century. Berlin: Springer, 2001: 173-183. |
| [13] | GODEFROID P, LEVIN M Y, MOLNAR D. Automated Whitebox Fuzz Testing[C]//IEEE. Proceedings of Network and Distributed Systems Security (NDSS) 2008. New York: IEEE, 2008: 151-166. |
| [14] | CADAR C, DUNBAR D, ENGLER D R. Klee:Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs[C]//ACM. Proceedings of the 8th USENIX Conference on Operating Systems Design and Implementation. New York: ACM, 2008: 209-224. |
| [15] | SEN K, AGHA G. CUTE and jCUTE: Concolic Unit Testing and Explicit Path Model-Checking Tools[C]//Springer. International Conference on Computer Aided Verification. Berlin: Springer, 2006: 419-423. |
| [16] | GODEFROID P. Random Testing for Security:Blackbox vs Whitebox Fuzzing[C]//IEEE. Proceedings of the 2nd International Workshop on Random Testing: Co-Located with the 22nd IEEE/ACM International Conference on Automated Software Engineering (ASE 2007). New York: IEEE, 2007: 1-10. |
| [17] |
LI Jun, ZHAO Bodong, ZHANG Chao. Fuzzing: A Survey[J]. Cybersecurity, 2018, 1(1): 1-13.
doi: 10.1186/s42400-018-0005-8 |
| [18] | GODEFROID P, KIEZUN A, LEVIN M Y. Grammar-Based Whitebox Fuzzing[C]//ACM. Proceedings of the 29th ACM SIGPLAN Conference on Programming Language Design and Implementation. New York: ACM, 2008: 206-215. |
| [19] | NILIZADEH S, NOLLER Y, PASAREANU C S. DifFuzz:Differential Fuzzing for Side-Channel Analysis[C]//IEEE. 2019 IEEE/ACM 41st International Conference on Software Engineering (ICSE). New York: IEEE, 2019: 176-187. |
| [20] | WANG Junjie, CHEN Bihuan, WEI Lei, et al. Superion:Grammar-Aware Greybox Fuzzing[C]//IEEE. 2019 IEEE/ACM 41st International Conference on Software Engineering (ICSE). New York: IEEE, 2019: 724-735. |
| [21] | MICHAL Z. 2017 American Fuzzy Lop[EB/OL]. (2017-03-12)[2022-10-07]. http://lcamtuf.coredump.cx/afl. |
| [22] | BÖHME M, PHAM V T, NGUYEN M D, et al. Directed Greybox Fuzzing[C]//ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344. |
| [23] | CHEN Hongxu, XUE Yinxing, LI Yuekang, et al. Hawkeye:Towards a Desired Directed Grey-Box Fuzzer[C]//ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 2095-2108. |
| [24] | REN Zezhong, ZHENG Han, ZHANG Jiayuan, et al. A Review of Fuzzing Techniques[J]. Journal of Computer Research and Development, 2021, 58(5): 944-963. |
| 任泽众, 郑晗, 张嘉元, 等. 模糊测试技术综述[J]. 计算机研究与发展, 2021, 58(5): 944-963. | |
| [25] |
ZHANG Xiong, LI Zhoujun. Survey of Fuzz Testing Technology[J]. Computer Science, 2016, 43(5): 1-8, 26.
doi: 10.11896/j.issn.1002-137X.2016.05.001 |
|
张雄, 李舟军. 模糊测试技术研究综述[J]. 计算机科学, 2016, 43 (5): 1-8, 26.
doi: 10.11896/j.issn.1002-137X.2016.05.001 |
|
| [26] | GODEFROID P, PELEG H, SINGH R. Learn&Fuzz:Machine Learning for Input Fuzzing[C]//IEEE. 2017 32nd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2017: 50-59. |
| [27] |
NASRABADI M Z, PARSA S, KALAEE A. Format-Aware Learn&Fuzz: Deep Test Data Generation for Efficient Fuzzing[J]. Neural Computing and Applications, 2021, 33(5): 1497-1513.
doi: 10.1007/s00521-020-05039-7 |
| [28] | SABLOTNY M, JENSEN B S, JOHNSON C W. Recurrent Neural Networks for Fuzz Testing Web Browsers[C]//Springer. Information Security and Cryptology-ICISC 2018. Berlin: Springer, 2019: 354-370. |
| [29] | PADURARU C, MELEMCIUC M C. An Automatic Test Data Generation Tool Using Machine Learning[EB/OL]. (2018-10-16)[2022-10-07]. https://pdfs.semanticscholar.org/82bd/ef8522578768ffa161a255eb9ce68b99e371.pdf. |
| [30] | JITSUNARI Y, ARAHORI Y. Coverage-Guided Learning-Assisted Grammar-Based Fuzzing[C]//IEEE. 2019 IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW). New York: IEEE, 2019: 275-280. |
| [31] | CHENG Liang, ZHANG Yang, ZHANG Yi, et al. Optimizing Seed Inputs in Fuzzing with Machine Learning[C]//IEEE. 2019 IEEE/ACM 41st International Conference on Software Engineering:Companion Proceedings (ICSE-Companion). New York: IEEE, 2019: 244-245. |
| [32] | FAN Rong, CHANG Yaoyao. Machine Learning for Black-Box Fuzzing of Network Protocols[C]//Springer. Information and Communications Security-ICICS 2017. Berlin: Springer, 2018: 621-632. |
| [33] | GAO Zicong, DONG Weiyu, CHANG Rui, et al. The Stacked Seq2Seq-Attention Model for Protocol Fuzzing[C]//IEEE. 2019 IEEE 7th International Conference on Computer Science and Network Technology (ICCSNT). New York: IEEE, 2019: 126-130. |
| [34] |
LAI Yingxu, GAO Huijuan, LIU Jing. Vulnerability Mining Method for the Modbus TCP Using an Anti-Sample Fuzzer[J]. Sensors, 2020, 20(7): 20-40.
doi: 10.3390/s20010020 URL |
| [35] | ZHAO Hui, LI Zhihui, WEI Hansheng, et al. SeqFuzzer:An Industrial Protocol Fuzzing Framework from a Deep Learning Perspective[C]//IEEE. 2019 12th IEEE Conference on Software Testing, Validation and Verification (ICST). New York: IEEE, 2019: 59-67. |
| [36] | HU Zhicheng, SHI Jianqi, HUANG Yanhong, et al. GANFuzz:A GAN-Based Industrial Network Protocol Fuzzing Framework[C]//ACM. Proceedings of the 15th ACM International Conference on Computing Frontiers. New York: ACM, 2018: 138-145. |
| [37] | CUMMINS C, PETOUMENOS P, MURRAY A, et al. Compiler Fuzzing Through Deep Learning[C]//ACM. Proceedings of the 27th ACM SIGSOFT International Symposium on Software Testing and Analysis. New York: ACM, 2018: 95-105. |
| [38] | LIU Xiao, LI Xiaoting, PRAJAPATI R, et al. DeepFuzz:Automatic Generation of Syntax Valid C Programs for Fuzz Testing[C]//ACM. Proceedings of the AAAI Conference on Artificial Intelligence. New York: ACM, 2019: 1044-1051. |
| [39] | LEE S, HAN H S, CHA S K, et al. Montage:A Neural Network Language Model-Guided Javascript Engine Fuzzer[C]//USENIX. 29th USENIX Security Symposium. Berkley: USENIX, 2020: 2613-2630. |
| [40] | YE Guixin, TANG Zhanyong, TAN S H, et al. Automated Conformance Testing for Javascript Engines via Deep Compiler Fuzzing[C]//ACM. Proceedings of the 42nd ACM SIGPLAN International Conference on Programming Language Design and Implementation. New York: ACM, 2021: 435-450. |
| [41] | LIU Peng, ZHANG Xiangyu, PISTOIA M, et al. Automatic Text Input Generation for Mobile Testing[C]//IEEE. 2017 IEEE/ACM 39th International Conference on Software Engineering (ICSE). New York: IEEE, 2017: 643-653. |
| [42] | LI Yuanchun, YANG Ziyue, GUO Yao, et al. Humanoid:A Deep Learning-Based Approach to Automated Black-Box Android App Testing[C]//IEEE. 2019 34th IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2019: 1070-1073. |
| [43] | CHEN Yuqi, POSKITT C M, SUN Jun, et al. Learning-Guided Network Fuzzing for Testing Cyber-Physical System Defences[C]//IEEE. 2019 34th IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2019: 962-973. |
| [44] | RAJPAL M, BLUM W, SINGH R. Not All Bytes are Equal: Neural Byte Sieve for Fuzzing[EB/OL]. (2017-11-10)[2022-10-07]. https://arxiv.org/abs/1711.04596. |
| [45] | SHE Dongdong, PEI Kexin, EPSTEIN D, et al. Neuzz:Efficient Fuzzing with Neural Program Smoothing[C]//IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 803-817. |
| [46] | SHE Dongdong, RAHUL K, YAN Lu, et al. MTFuzz:Fuzzing with a Multi-Task Neural Network[C]//ACM. Proceedings of the 28th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering (ESEC/FSE 2020). New York: ACM, 2020: 737-749. |
| [47] | WU Mingyuan, JIANG Ling, XIANG Jiahong, et al. Evaluating and Improving Neural Program-Smoothing-Based Fuzzing[C]//IEEE. 2022 IEEE/ACM 44th International Conference on Software Engineering (ICSE). New York: IEEE, 2022: 847-858. |
| [48] | KARAMCHETI S, MANN G, ROSENBERG D. Adaptive Grey-Box Fuzz-Testing with Thompson Sampling[C]//ACM. Proceedings of the 11th ACM Workshop on Artificial Intelligence and Security. New York: ACM, 2018: 37-47. |
| [49] | DROZD W, MICHAEL D W. FuzzerGym: A Competitive Framework for Fuzzing and Learning[EB/OL]. (2018-07-19)[2022-10-07]. https://arxiv.org/abs/1807.07490. |
| [50] | BOTTINGER K, GODEFROID P, SINGH R. Deep Reinforcement Fuzzing[C]//IEEE. 2018 IEEE Security and Privacy Workshops (SPW). New York: IEEE, 2018: 116-122. |
| [51] | WU Mingyuan, JIANG Ling, XIANG Jiahong, et al. One Fuzzing Strategy to Rule Them All[C]//IEEE. 2022 IEEE/ACM 44th International Conference on Software Engineering (ICSE). New York: IEEE, 2022: 1634-1645. |
| [52] | ZHAO Yuyue, LI Yangyang, YANG Tengfei, et al. Suzzer: A Vulnerability-Guided Fuzzer Based on Deep Learning[C]//Springer. Information Security and Cryptology:15th International Conference. Berlin: Springer, 2020: 134-153. |
| [53] |
LI Yuwei, JI Shouling, LYU Chenyang, et al. V-Fuzz: Vulnerability Prediction-Assisted Evolutionary Fuzzing for Binary Programs[J]. IEEE Transactions on Cybernetics, 2020, 52(5): 3745-3756.
doi: 10.1109/TCYB.2020.3013675 URL |
| [54] | WANG Yunchao, WU Zehui, WEI Qiang, et al. NeuFuzz: Efficient Fuzzing with Deep Neural Network[J]. IEEE Access, 2019(7): 36340-36352. |
| [55] | CHEN Yaohui, AHMADI M, FARKHANI R M, et al. MEUZZ:Smart Seed Scheduling for Hybrid Fuzzing[C]//USENIX. 23rd International Symposium on Research in Attacks, Intrusions and Defenses ({RAID} 2020). Berkley: USENIX, 2020: 77-92. |
| [56] | WANG Jinghan, SONG Chengyu, YIN Heng. Reinforcement Learning-Based Hierarchical Seed Scheduling for Greybox Fuzzing[EB/OL]. (2021-01-01)[2022-10-07]. https://escholarship.org/uc/item/44p2v1gd. |
| [57] | WANG Daimeng, ZHANG Zheng, ZHANG Hang, et al. SyzVegas:Beating Kernel Fuzzing Odds with Reinforcement Learning[C]//USENIX. 30th USENIX Security Symposium. Berkley: USENIX, 2021: 2741-2758. |
| [58] | SUN Xiaoshan, FU Yu, DONG Yun, et al. Improving Fitness Function for Language Fuzzing with PCFG Model[C]//IEEE. 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC). New York: IEEE, 2018: 655-660. |
| [59] | SANJEEV D, KEDRIAN J, JAN W, et al. A Flexible Framework for Expediting Bug Finding by Leveraging Past (Mis-)Behavior to Discover New Bugs[C]//ACM. Annual Computer Security Applications Conference (ACSAC’20). New York: ACM, 2020: 345-359. |
| [60] | GONG Weiwei, ZHANG Gen, ZHOU Xu. Learn to Accelerate Identifying New Test Cases in Fuzzing[C]//Springer. International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage. Berlin: Springer, 2017: 298-307. |
| [61] | JOFFE L. Machine Learning Augmented Fuzzing[C]//IEEE. 2018 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW). New York: IEEE, 2018: 178-183. |
| [62] | JOFFE L, CLARK D. Directing a Search Towards Execution Properties with a Learned Fitness Function[C]//IEEE. 2019 12th IEEE Conference on Software Testing, Validation and Verification (ICST). New York: IEEE, 2019: 206-216. |
| [63] | ZONG Peiyuan, LYU Tao, WANG Dawei, et al. Fuzzguard:Filtering out Unreachable Inputs in Directed Grey-Box Fuzzing Through Deep Learning[C]//USENIX. 29th USENIX Security Symposium. Berkley: USENIX, 2020: 2255-2269. |
| [64] | MING Liang, ZHAO Gang, HUANG Minhuan, et al. Remote Protocol Vulnerability Discovery for Intelligent Transportation Systems (ITS)[C]//IEEE. 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC). New York: IEEE, 2018: 923-929. |
| [65] | TRIPATHI S, GRIECO G, RAWAT S. Exniffer:Learning to Prioritize Crashes by Assessing the Exploitability from Memory Dump[C]//IEEE. 2017 24th Asia-Pacific Software Engineering Conference (APSEC). New York: IEEE, 2017: 239-248. |
| [66] | ZHANG Li, THING V. Assisting Vulnerability Detection by Prioritizing Crashes with Incremental Learning[C]//IEEE. TENCON 2018 IEEE Region 10 Conference. New York: IEEE, 2018: 2080-2085. |
| [67] | YAN Guanhua, LU Junchen, SHU Zhan, et al. Exploitmeter:Combining Fuzzing with Machine Learning for Automated Evaluation of Software Exploitability[C]//IEEE. 2017 IEEE Symposium on Privacy-Aware Computing (PAC). New York: IEEE, 2017: 164-175. |
| [68] | YOU Wei, ZONG Peiyuan, CHEN Kai, et al. Semfuzz:Semantics-Based Automatic Generation of Proof-of-Concept Exploits[C]//ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2139-2154. |
| [1] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [2] | 钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108. |
| [3] | 许春根, 薛少康, 徐磊, 张盼. 基于安全两方计算的高效神经网络推理协议[J]. 信息网络安全, 2023, 23(7): 22-30. |
| [4] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [5] | 胡智杰, 陈兴蜀, 袁道华, 郑涛. 基于改进随机森林的Android广告应用静态检测方法[J]. 信息网络安全, 2023, 23(2): 85-95. |
| [6] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| [7] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [8] | 王鹃, 王蕴茹, 翁斌, 龚家新. 机器学习在x86二进制反汇编中的应用研究综述[J]. 信息网络安全, 2022, 22(6): 9-25. |
| [9] | 牛艺诺, 张逸飞, 高能, 马存庆. 融合时序和逻辑关系的日志异常检测系统设计[J]. 信息网络安全, 2022, 22(11): 1-6. |
| [10] | 段晓毅, 李邮, 令狐韫行, 胡荣磊. 基于RF算法的侧信道攻击方法研究[J]. 信息网络安全, 2022, 22(1): 19-26. |
| [11] | 郭春, 蔡文艳, 申国伟, 周雪梅. 基于关键载荷截取的SQL注入攻击检测方法[J]. 信息网络安全, 2021, 21(7): 43-53. |
| [12] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [13] | 马骁, 蔡满春, 芦天亮. 基于CNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2021, 21(10): 69-75. |
| [14] | 徐瑜, 周游, 林璐, 张聪. 无监督机器学习在游戏反欺诈领域的应用研究[J]. 信息网络安全, 2020, 20(9): 32-36. |
| [15] | 杜笑宇, 叶何, 文伟平. 基于字节码搜索的Java反序列化漏洞调用链挖掘方法[J]. 信息网络安全, 2020, 20(7): 19-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||