信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 17-31.doi: 10.3969/j.issn.1671-1122.2023.08.002
SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计
- 1.南京邮电大学计算机学院,南京 210023
2.江苏省联创软件研究院,南京 210003
-
收稿日期:2023-06-25出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:张伟 E-mail:zhangw@njupt.edu.cn -
作者简介:张伟(1973—),男,江苏,教授,博士,CCF会员,主要研究方向为网络信息安全、恶意代码分析、社会网络分析|李子轩(1998—),男,河北,硕士研究生,主要研究方向为网络安全|徐晓瑀(1983—),男,江苏,工程师,主要研究方向为云计算|黄海平(1981—),男,福建,教授,博士,CCF会员,主要研究方向为物联网技术、网络安全、数据隐私保护技术 -
基金资助:国家重点研发计划(2019YFB2101700)
SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter
ZHANG Wei1( ), LI Zixuan1, XU Xiaoyu2, HUANG Haiping1
), LI Zixuan1, XU Xiaoyu2, HUANG Haiping1
- 1. School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. Jiangsu Lianchuang Software Research Institute, Nanjing 210003, China
-
Received:2023-06-25Online:2023-08-10Published:2023-08-08 -
Contact:ZHANG Wei E-mail:zhangw@njupt.edu.cn
摘要:
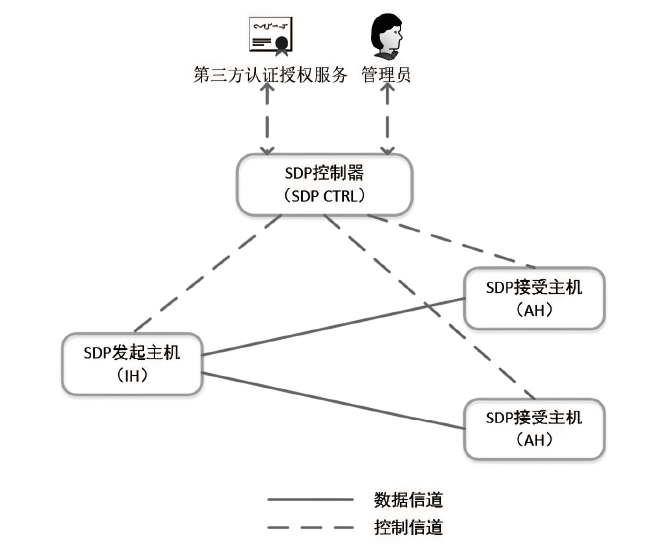
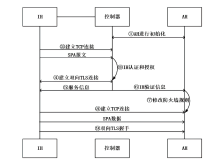
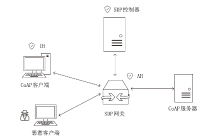
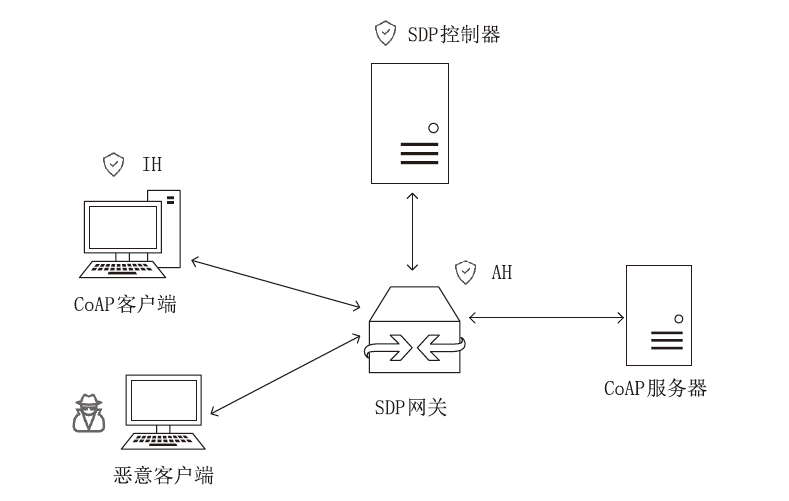
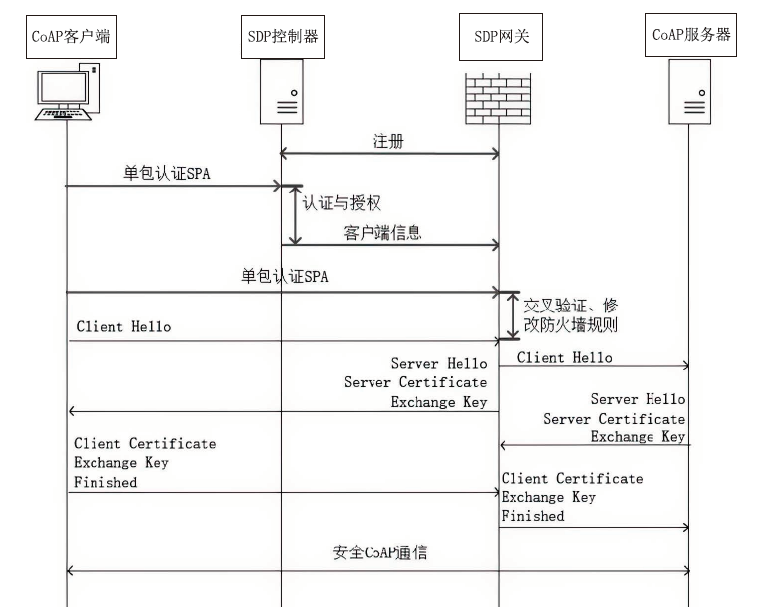
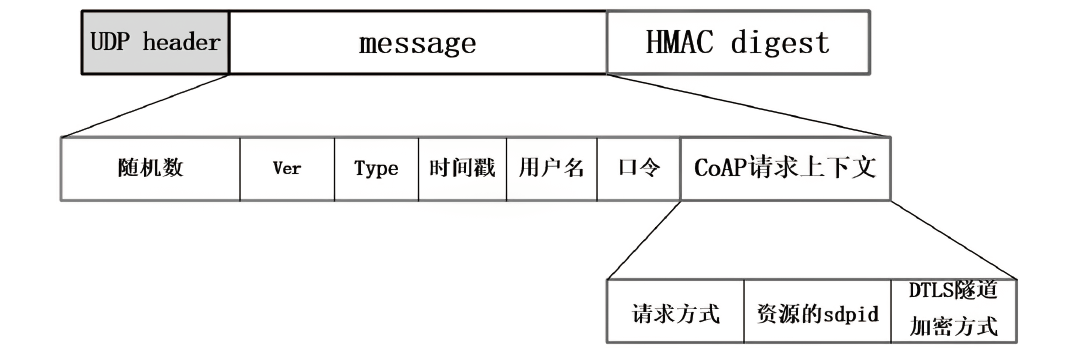
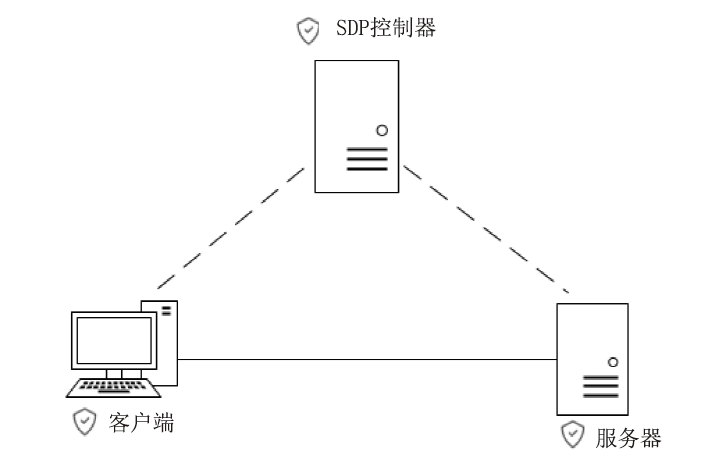
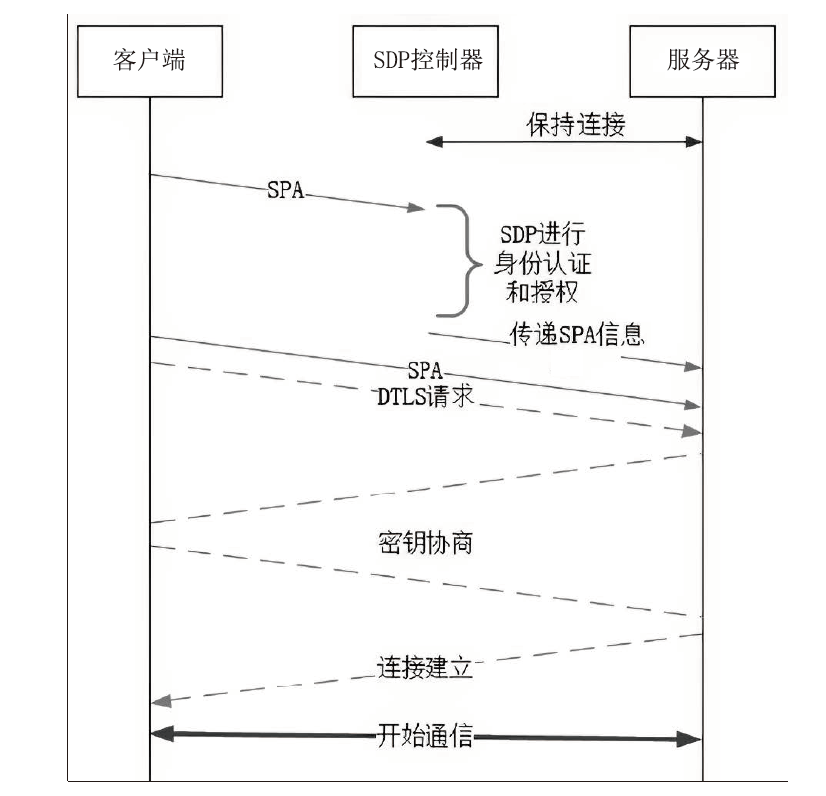
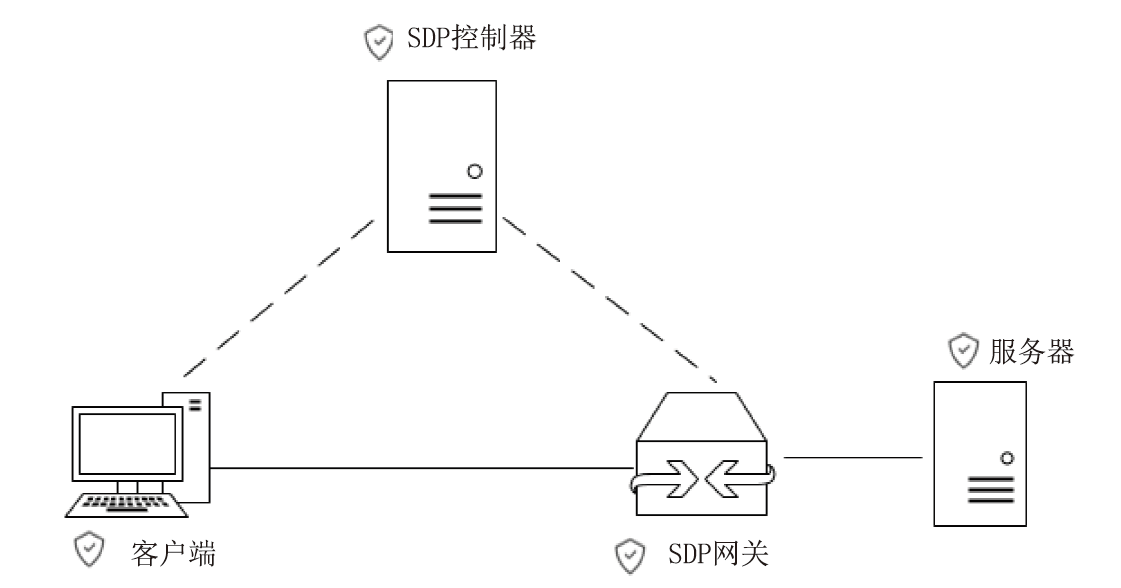
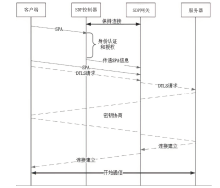
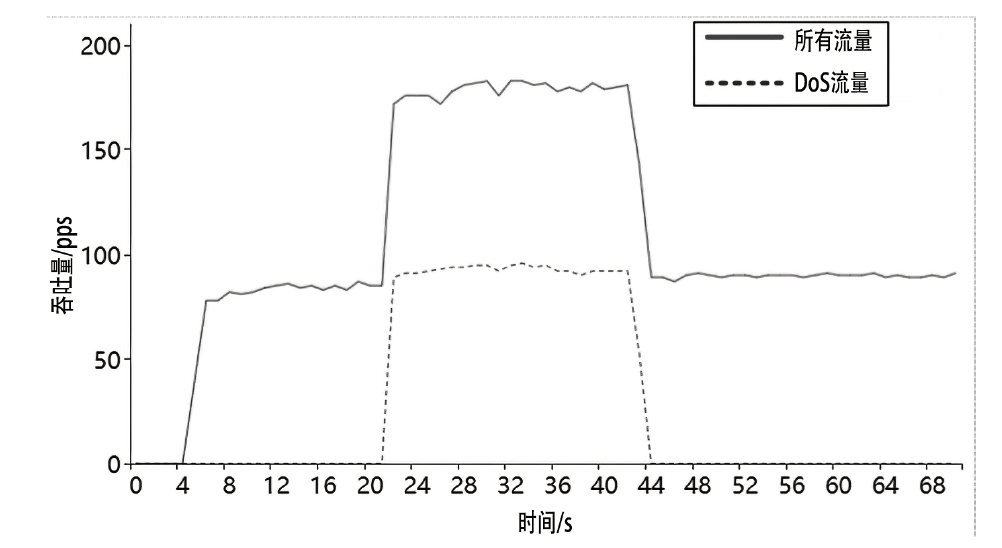
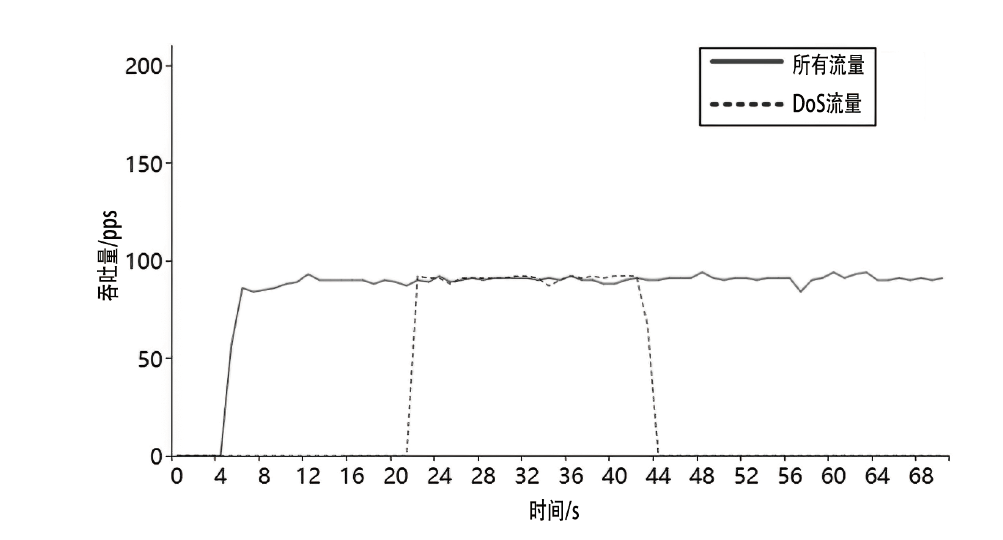
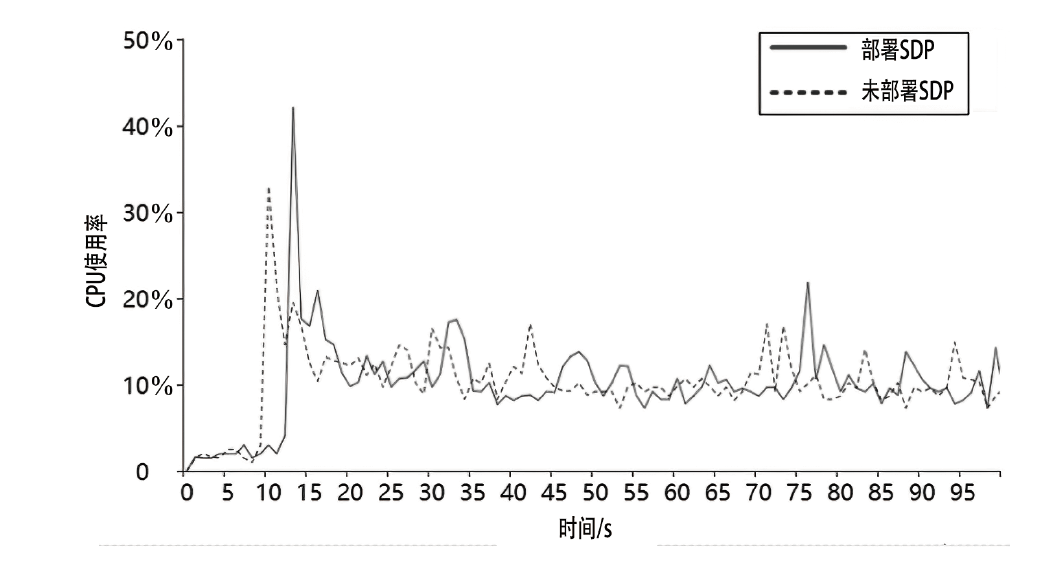
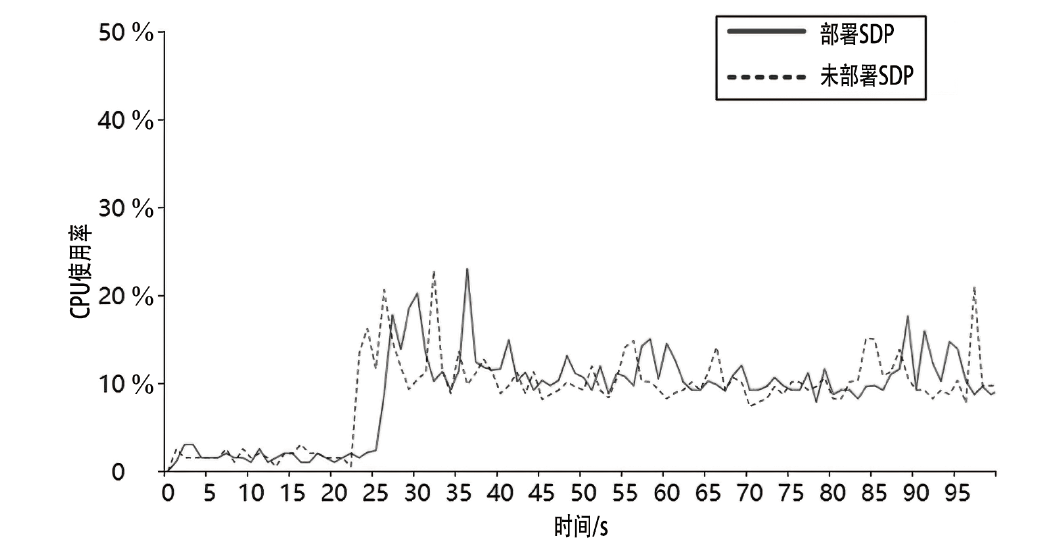
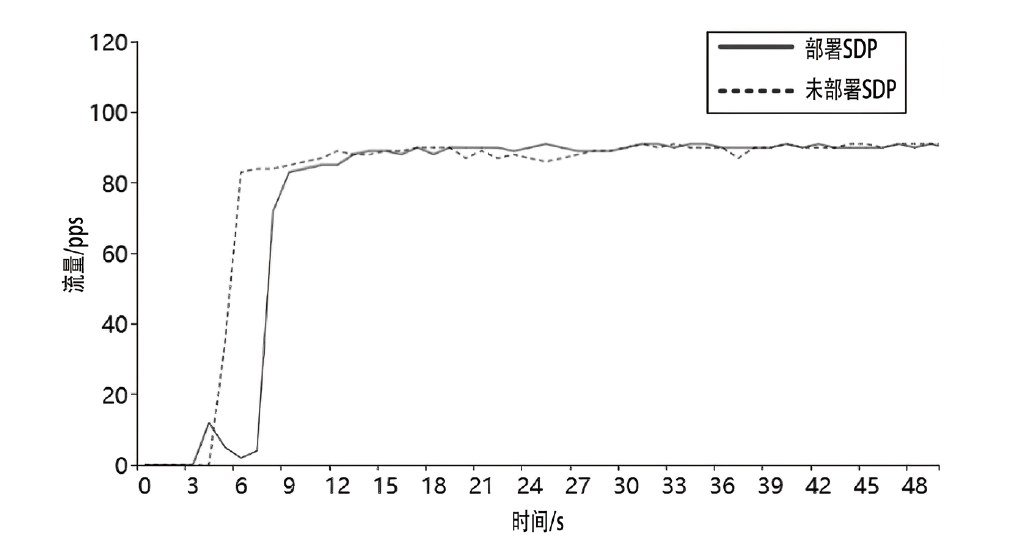
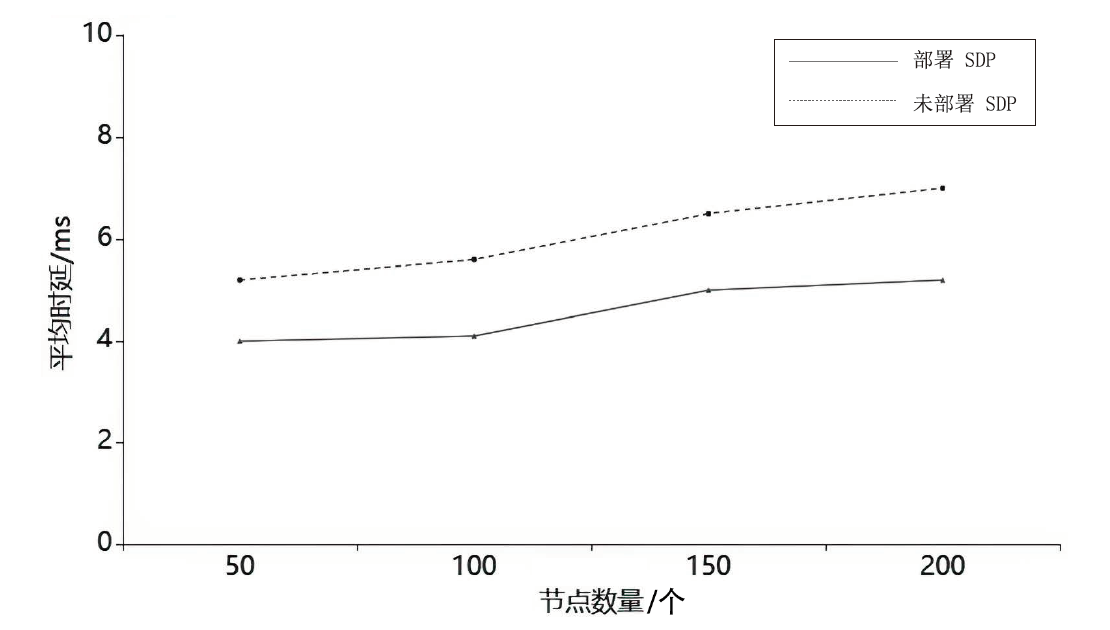
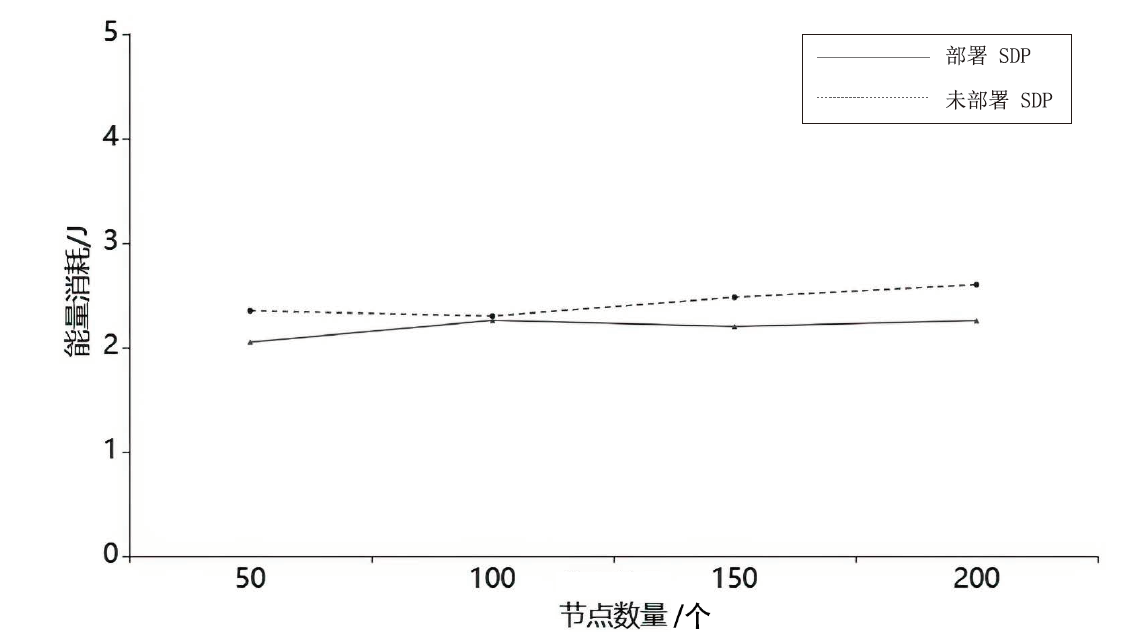
约束应用协议(CoAP)作为一种新兴的物联网协议,虽然考虑了安全设计,但依然不能满足新的安全需求。文章提出了一个基于软件定义边界(SDP)的安全增强CoAP通信框架(SDP-CoAP),利用单包认证(SPA)技术,客户端将认证信息、数据包传输层安全性协议(DTLS)的隧道加密方式和CoAP请求方式等信息添加到握手过程的第一个数据包中,并发送给SDP控制器,实现先认证后通信。对于通过认证的访问请求,从环境、行为等多个维度实时评估访问的可信度,结合客户端不同的请求方式,实现多维动态访问授权。文章还对SDP-CoAP架构的具体部署方式进行分析,设计了一种综合安全性能、能量消耗和处理延迟的部署方式。实验结果表明,SDP-CoAP的客户端-网关部署方式在没有引入明显能源消耗和网络延迟的情况下可以有效增强CoAP网络的安全性。
中图分类号:
引用本文
张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31.
ZHANG Wei, LI Zixuan, XU Xiaoyu, HUANG Haiping. SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter[J]. Netinfo Security, 2023, 23(8): 17-31.
表4
实验设备配置
| 设备 | 安装的软件 | 配置 |
|---|---|---|
| VM1 (SDP Controller) | - Linux CentOS7 - SDPcontroller module | - 1 Processor - 2 GB RAM - 2 NICs |
| VM2 (SDP Gateway) | - Linux Ubuntu 20.04 - Californium CoAP Server - SDPgateway module | - 2 Processor - 4 GB RAM - 2 NICs |
| VM3 (Normal Client) | - Linux Ubuntu 20.04 - Californium CoAP Client - IH module | - 2 Processor - 2 GB RAM - 2 NICs |
| VM4 (Malicious Client) | - Linux Ubuntu 20.04 - Californium CoAP Client | - 2 Processor - 4 GB RAM - 2 NICs |
| VM5 (CoAP Server) | - Linux Ubuntu 20.04 - Californium CoAP Server | - 2 Processor - 2 GB RAM - 2 NICs |
| [1] |
SHAFIQUE K, KHAWAJA B A, SABIR F, et al. Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios[J]. IEEE Access, 2020, 8: 23022-23040.
doi: 10.1109/Access.6287639 URL |
| [2] | Ministry of Industry and Information Technology. Economic Operation of the Communications Industry from January to May 2023[EB/OL]. (2023-06-21)[2023-06-25]. https://wap.miit.gov.cn/gxsj/tjfx/txy/art/2023/art_a62ac3d2646541fba9e6a5e3a20534c1.html. |
| 中华人民共和国工业与信息化部. 2023年1-5月份通信业经济运行情况[EB/OL]. (2023-06-21)[2023-06-25]. https://wap.miit.gov.cn/gxsj/tjfx/txy/art/2023/art_a62ac3d2646541fba9e6a5e3a20534c1.html. | |
| [3] |
BORMANN C, CASTELLANI A P, SHELBY Z. Coap: An Application Protocol for Billions of Tiny Internet Nodes[J]. IEEE Internet Computing, 2012, 16(2): 62-67.
doi: 10.1109/MIC.2012.29 URL |
| [4] | KARAGIANNIS V, CHATZIMISIOS P, VAZQUEZ-GALLEGO F, et al. A Survey on Application Layer Protocols for the Internet of Things[J]. Transaction on IoT and Cloud Computing, 2015, 3(1): 11-17 |
| [5] | HAN J, HA M, KIM D. Practical Security Analysis for the Constrained Node Networks:Focusing on the DTLS Protocol[C]//IEEE. 2015 5th International Conference on the Internet of Things (IoT). New York: IEEE, 2015: 22-29. |
| [6] | CAMPBELL M. Beyond Zero Trust: Trust is a Vulnerability[J]. Computer, 2020, 53(10): 110-113. |
| [7] | PALMO Y, TANIMOTO S, SATO H, et al. A Consideration of Scalability for Software Defined Perimeter Based on the Zero-Trust Model[C]//IEEE. 2021 10th International Congress on Advanced Applied Informatics (IIAI-AAI). New York: IEEE, 2021: 717-724. |
| [8] | Internet Engineering Task Force. Datagram Transport Layer Security[EB/OL]. [2023-05-20]. https://www.rfc-editor.org/rfc/rfc6347. |
| [9] | ARVIND S, NARAYANAN V A. An Overview of Security in CoAP:Attack and Analysis[C]//IEEE. 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS). New York: IEEE, 2019: 655-660. |
| [10] | LERCHE C, HARTKE K, KOVATSCH M. Industry Adoption of the Internet of Things:A Constrained Application Protocol Survey[C]//IEEE. Proceedings of 2012 IEEE 17th International Conference on Emerging Technologies & Factory Automation (ETFA 2012). New York: IEEE, 2012: 1-6. |
| [11] | CAPOSSELE A, CERVO V, DECICCO G, et al. Security as a CoAP Resource:An Optimized DTLS Implementation for the IoT[C]//IEEE. 2015 IEEE International Conference on Communications (ICC). New York: IEEE, 2015: 549-554. |
| [12] | NAVAS R E, BOUDER H L, CUPPENS N, et al. Do not Trust Your Neighbors! A Small IoT Platform Illustrating a Man-in-the-Middle Attack[C]//Springer. International Conference on Ad-Hoc Networks and Wireless. Berlin: Springer, 2018: 120-125. |
| [13] |
MOUBAYED A, REFAEY A, SHAMI A. Software-Defined Perimeter (SDP): State of the Art Secure Solution for Modern Networks[J]. IEEE Network, 2019, 33(5): 226-233.
doi: 10.1109/MNET.65 URL |
| [14] | HAROON A, AKRAM S, SHAH M A, et al. E-Lithe:A Lightweight Secure DTLS for IoT[C]//IEEE. 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall). New York: IEEE, 2017: 1-5. |
| [15] | KAJWADKAR S, JAIN V K. A Novel Algorithm for DoS and DDoS Attack Detection in Internet of Things[C]//IEEE. 2018 Conference on Information and Communication Technology (CICT). New York: IEEE, 2018: 1-4. |
| [16] | DEY S, HOSSAIN A. Session-Key Establishment and Authentication in a Smart Home Network Using Public Key Cryptography[J]. IEEE Sensors Letters, 2019, 3(4): 1-4. |
| [17] |
MAJUMDER S, RAY S, SADHUKHAN D, et al. ECC-CoAP: Elliptic Curve Cryptography Based Constraint Application Protocol for Internet of Things[J]. Wireless Personal Communications, 2021, 116(3): 1867-1896.
doi: 10.1007/s11277-020-07769-2 |
| [18] | SARAIVA D A F, LEITHARDT V R Q, DEPAULA D, et al. Prisec: Comparison of Symmetric Key Algorithms for IoT Devices[EB/OL]. [2023-06-21]. https://www.mdpi.com/1424-8220/19/19/4312. |
| [19] | HALABI D, HAMDAN S, ALMAJALI S. Enhance the Security in Smart Home Applications Based on IoT-CoAP Protocol[C]//IEEE. 2018 Sixth International Conference on Digital Information, Networking, and Wireless Communications (DINWC). New York: IEEE, 2018: 81-85. |
| [20] | PANDYA H B, CHAMPANERIA T A. Enhancement of Security in IoTSyS Framework[C]//Springer. Proceedings of International Conference on Communication and Networks. Berlin: Springer, 2017: 31-43. |
| [21] |
DE HOZ DIEGO J D, SALDANA J, FERNÁNDEZ-NAVAJAS J, et al. Decoupling Security from Applications in CoAP-Based IoT Devices[J]. IEEE Internet of Things Journal, 2019, 7(1): 467-476.
doi: 10.1109/JIoT.6488907 URL |
| [22] |
KUMAR P M, GANDHI U D. Enhanced DTLS with CoAP-Based Authentication Scheme for the Internet of Things in Healthcare Application[J]. The Journal of Supercomputing, 2020, 76(6): 3963-3983.
doi: 10.1007/s11227-017-2169-5 |
| [23] |
SINGH J, REFAEY A, KOILPILLAI J. Adoption of the Software-Defined Perimeter (SDP) Architecture for Infrastructure as a Service[J]. Canadian Journal of Electrical and Computer Engineering, 2020, 43(4): 357-363.
doi: 10.1109/CJECE.2020.3005316 URL |
| [24] |
SALLAM A, REFAEY A, SHAMI A. On the Security of SDN: A Completed Secure and Scalable Framework Using the Software-Defined Perimeter[J]. IEEE Access, 2019, 7: 146577-146587.
doi: 10.1109/Access.6287639 URL |
| [25] | SINGH J, REFAEY A, SHAMI A. Multilevel Security Framework for NFV Based on Software Defined Perimeter[J]. IEEE Network, 2020, 34(5): 114-119. |
| [26] |
SINGH J, BELLO Y, HUSSEIN A R, et al. Hierarchical Security Paradigm for IoT Multiaccess Edge Computing[J]. IEEE Internet of Things Journal, 2020, 8(7): 5794-5805.
doi: 10.1109/JIOT.2020.3033265 URL |
| [27] |
REFAEY A, SALLAM A, SHAMI A. On IoT Applications: A Proposed SDP Framework for MQTT[J]. Electronics Letters, 2019, 55(22): 1201-1203.
doi: 10.1049/el.2019.2334 |
| [28] | SALLAM A, REFAEY A, SHAMI A. Securing Smart Home Networks with Software-Defined Perimeter[C]//IEEE. 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC). New York: IEEE, 2019: 1989-1993. |
| [1] | 黄杰, 何城鋆. 基于软件定义边界的服务保护方案[J]. 信息网络安全, 2023, 23(6): 1-10. |
| [2] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [3] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [4] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| [5] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [6] | 赵洪, 李姗, 左珮良, 魏占祯. 基于强化学习的物联网安全资源分配方法[J]. 信息网络安全, 2022, 22(6): 44-52. |
| [7] | 郭宝霞, 王佳慧, 马利民, 张伟. 基于零信任的敏感数据动态访问控制模型研究[J]. 信息网络安全, 2022, 22(6): 86-93. |
| [8] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [9] | 韩俐, 宋吉祥, 孙士民. SD-IoT中基于设备地址的移动目标防御机制研究[J]. 信息网络安全, 2022, 22(11): 36-46. |
| [10] | 李桐, 任帅, 王刚, 孟庆宇. 基于变色龙认证树的云边端协同流式数据完整性验证模型[J]. 信息网络安全, 2022, 22(1): 37-45. |
| [11] | 陈庆港, 杜彦辉, 韩奕, 刘翔宇. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. |
| [12] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [13] | 李群, 董佳涵, 关志涛, 王超. 一种基于聚类分类的物联网恶意攻击检测方法[J]. 信息网络安全, 2021, 21(8): 82-90. |
| [14] | 刘忻, 杨浩睿, 郭振斌, 王家寅. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7): 1-9. |
| [15] | 刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||