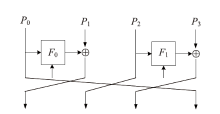
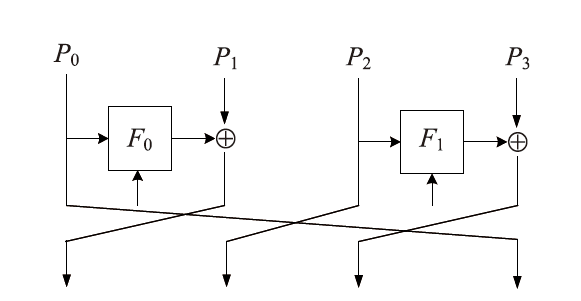
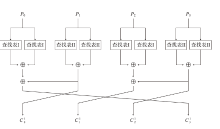
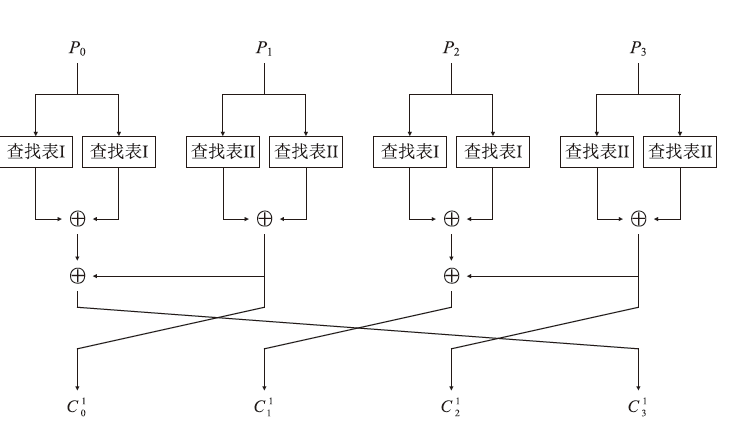
信息网络安全 ›› 2023, Vol. 23 ›› Issue (6): 66-73.doi: 10.3969/j.issn.1671-1122.2023.06.007
基于白盒CLEFIA实现的软件防篡改方案
- 1.西安电子科技大学通信工程学院,西安 710071
2.河南省网络密码技术重点实验室,郑州 100190
3.西安邮电大学网络空间安全学院,西安 710121
-
收稿日期:2023-02-09出版日期:2023-06-10发布日期:2023-06-20 -
通讯作者:陈杰jchen@mail.xidian.edu.cn -
作者简介:罗一诺(1998—),女,河北,硕士研究生,主要研究方向为白盒密码设计与安全性分析|姚思(1995—),男,辽宁,硕士研究生,主要研究方向为白盒密码设计与安全性分析|陈杰(1979—),女,湖南,副教授,博士,主要研究方向为密码协议、密码算法设计与分析、白盒密码设计与安全性分析|董晓丽(1982—),女,山西,讲师,博士,主要研究方向为分组密码算法设计与分析、安全协议设计 -
基金资助:“十三五”国家密码发展基金(MMJJ20180219);陕西省自然科学基础研究计划基金(2021JM-126);河南省网络密码技术重点实验室研究课题(LNCT2022-A08);陕西省重点研发计划(2023-YBGY-015)
Software Tamper Resistance Scheme Based on White-Box CLEFIA Implementation
LUO Yinuo1, YAO Si1, CHEN Jie1,2( ), DONG Xiaoli3
), DONG Xiaoli3
- 1. School of Telecommunications Engineering, Xidian University, Xi’an 710071, China
2. Henan Key Laboratory of Network Cryptography Technology, Zhengzhou 100190, China
3. School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2023-02-09Online:2023-06-10Published:2023-06-20
摘要:
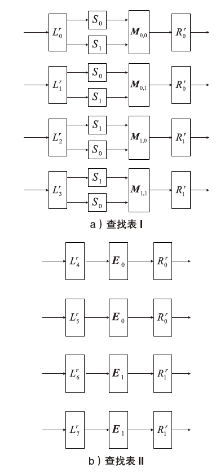
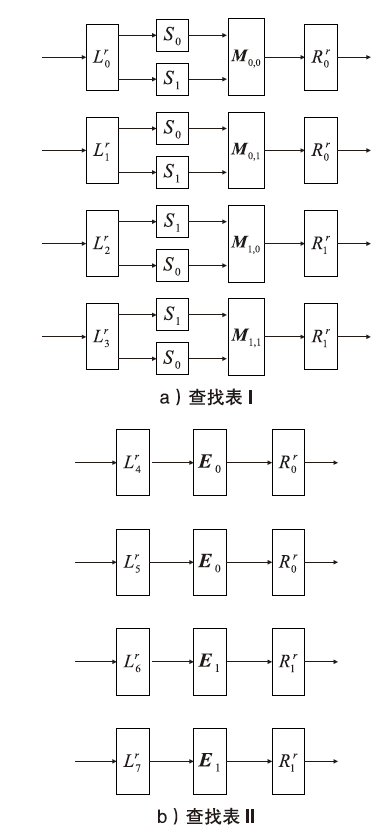
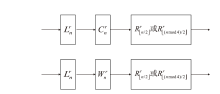
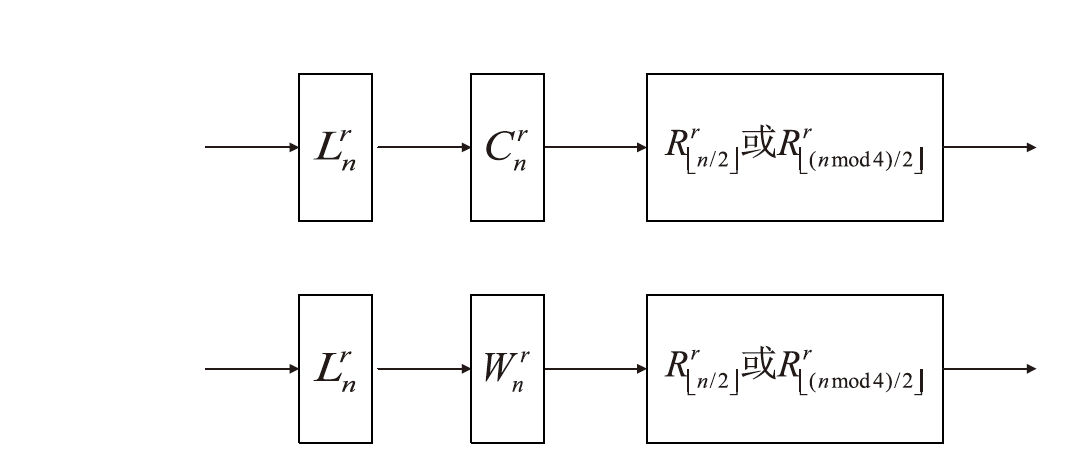
2002年,CHOW等人根据数字版权管理(Digital Rights Management,DRM)应用场景定义了白盒攻击环境的概念,并将其模型化为一种极端的攻击模型,即白盒模型。白盒模型颠覆了以往攻击模型中对攻击者能力的诸多限制,从软件保护角度考虑,攻击者被认为拥有对目标软件及其执行的完全控制权。因此,在白盒模型中,数字版权管理系统中的设备,如智能卡、机顶盒等都存在被攻击者篡改的可能。文章基于CLEFIA算法的白盒实现方案,为数字版权管理系统提供一种软件防篡改方案。该方案将软件的二进制代码文件所解释的查找表隐藏在CLEFIA算法的白盒实现方案的查找表集合中,使软件的防篡改安全性与CLEFIA算法的白盒实现方案的加解密正确性结合在一起。一旦软件发生篡改,CLEFIA算法的白盒实现方案的加解密结果将产生错误。CLEFIA算法白盒实现方案的明密文对也将发生变化,而攻击者很难对其进行修复。
中图分类号:
引用本文
罗一诺, 姚思, 陈杰, 董晓丽. 基于白盒CLEFIA实现的软件防篡改方案[J]. 信息网络安全, 2023, 23(6): 66-73.
LUO Yinuo, YAO Si, CHEN Jie, DONG Xiaoli. Software Tamper Resistance Scheme Based on White-Box CLEFIA Implementation[J]. Netinfo Security, 2023, 23(6): 66-73.
| [1] | CHOW S, EISEN P, JOHNSON H, et al. White-Box Cryptography and an AES Implementation[C]// SAC. Proceedings of International Workshop on Selected Areas in Cryptography. Berlin:Springer, 2002: 250-270. |
| [2] | WANG Chaokun, FU Junning, WANG Jianmin, et al. Survey of Software Tamper Proofing Technique[J]. Journal of Computer Research and Development, 2011, 48(6): 923-933. |
| 王朝坤, 付军宁, 王建民, 等. 软件防篡改技术综述[J]. 计算机研究与发展, 2011, 48(6): 923-933. | |
| [3] | WANG Ping, KANG S K, KIM K. Tamper Resistant Software Through Dynamic Integrity Checking[EB/OL]. (2005-01-28)[2023-01-30]. https://www.researchgate.net/publication/266246195. |
| [4] | COLLBERG C, THOMBORSON C, LOW D. A Taxonomy of Obfuscating Transformations[R]. New Zealand: Department of Computer Science, University of Auckland, TR148, 1997. |
| [5] | SUN Zongyao. Software Tamper-Proofing Technology Based on Hash Function[D]. Changchun: Jilin University, 2009. |
| 孙宗姚. 基于Hash函数的软件防篡改技术[D]. 长春: 吉林大学, 2009. | |
| [6] | MICHIELS W, GORISSEN P. Mechanism for Software Tamper Resistance: An Application of White-Box Cryptography[C]// SIGSAC. Proceedings of ACM Workshop on Digital Rights Management. Berlin:Springer, 2007: 82-89. |
| [7] | LU Zhixu. The Research of Software Tamper Resistance Based on White-Box Cryptography[D]. Shanghai: Shanghai Jiao Tong University, 2012. |
| 卢致旭. 基于白盒加密算法的软件防篡改技术研究[D]. 上海: 上海交通大学, 2012. | |
| [8] | XIAO Yaying, LAI Xuejia. A Secure Implementation of White-Box AES[C]// ICCSA. Proceedings of International Conference on Computer Science and its Applications. New York: IEEE, 2009: 1-6. |
| [9] | LIN Tingting, ZHONG Yixin, LAI Xuejia, et al. Software Tamper Resistance Based on White-Box SMS4 Implementation[C]// ISCI. Proceedings of International Conference on Smart City and Informatization. Berlin:Springer, 2019: 486-495. |
| [10] | XIAO Yaying, LAI Xuejia. White-Box Cryptography and White-Box Implementation of SMS4 Algorithm[C]// CACR. Proceedings of ChinaCrypt 2009. Beijing: Science and Technology of China Press, 2009: 24-34. |
| 肖雅莹, 来学嘉. 白盒密码及SMS4算法的白盒实现[C]// 中国密码学会.中国密码学会2009年会. 北京: 中国科学出版, 2009: 24-34. | |
| [11] | DE MULDER Y, ROELSE P, PRENEEL B. Cryptanalysis of the Xiao-Lai White-Box AES Implementation[C]// SAC. Proceedings of International Workshop on Selected Areas in Cryptography:19th International Conference, SAC 2012. Berlin:Springer, 2013: 34-49. |
| [12] |
LIN Tingting, LAI Xuejia. Efficient Attack to White-Box SMS4 Implementation[J]. Journal of Software, 2013, 24(9): 2238-2249.
doi: 10.3724/SP.J.1001.2013.04356 URL |
| 林婷婷, 来学嘉. 对白盒SMS4实现的一种有效攻击[J]. 软件学报, 2013, 24(9): 2238-2249. | |
| [13] | YAO Si, CHEN Jie, GONG Yating, et al. A New Method for White-Box Implementation of CLEFIA Algorithm[J]. Journal of Xidian University, 2020, 47(5): 150-158. |
| 姚思, 陈杰, 宫雅婷, 等. CLEFIA算法的一种新型白盒实现[J]. 西安电子科技大学学报, 2020, 47(5): 150-158. | |
| [14] | SHIRAI T, SHIBUTANI K, AKISHITA T, et al. The 128-bit Blockcipher CLEFIA (Extended Abstract)[C]// FSE. Proceedings of International Workshop on Fast Software Encryption. Berlin:Springer, 2007: 181-195. |
| [15] | SU Shuai, DONG Hang, FU Ge, et al. A White-Box CLEFIA Implementation for Mobile Devices[C]// CSC. Proceedings of Communications Security Conference. New York: IEEE, 2014: 1-8. |
| [16] | GONG Yating. Security Analysis and Improvement of White-Box CLEFIA Algorithm[D]. Xi'an: Xidian University, 2019. |
| 宫雅婷. 白盒CLEFIA算法的安全性分析与改进[D]. 西安: 西安电子科技大学, 2019. | |
| [17] | MICHIELS W, GORISSEN P, HOLLMANN H D L. Cryptanalysis of a Generic Class of White-Box Implementations[C]// SAC. Proceedings of International Workshop on Selected Areas in Cryptography. Berlin:Springer, 2008: 414-428. |
| [1] | 黄杰, 何城鋆. 基于软件定义边界的服务保护方案[J]. 信息网络安全, 2023, 23(6): 1-10. |
| [2] | 孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6): 104-110. |
| [3] | 王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6): 11-21. |
| [4] | 谢盈, 曾竹, 胡巍, 丁旭阳. 一种虚假数据注入攻击检测与补偿方法[J]. 信息网络安全, 2023, 23(6): 22-33. |
| [5] | 杨宇光, 卢嘉煜. 一种基于星型簇态的动态的分级的量子秘密共享协议[J]. 信息网络安全, 2023, 23(6): 34-42. |
| [6] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [7] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [8] | 蒋曾辉, 曾维军, 陈璞, 武士涛. 面向调制识别的对抗样本研究综述[J]. 信息网络安全, 2023, 23(6): 74-90. |
| [9] | 吴尚远, 申国伟, 郭春, 陈意. 威胁情报驱动的动态威胁狩猎方法[J]. 信息网络安全, 2023, 23(6): 91-103. |
| [10] | 赵俊, 任怡, 李宝, 谭郁松. 混源操作系统供应链安全风险评估方法研究[J]. 信息网络安全, 2023, 23(5): 50-61. |
| [11] | 裴蓓, 张水海, 吕春利. 用于云存储的主动秘密共享方案[J]. 信息网络安全, 2023, 23(5): 95-104. |
| [12] | 陈梓彤, 贾鹏, 刘嘉勇. 基于Siamese架构的恶意软件隐藏函数识别方法[J]. 信息网络安全, 2023, 23(5): 62-75. |
| [13] | 秦宝东, ,陈从正, ,何俊杰, 郑东. 基于可验证秘密共享的多关键词可搜索加密方案[J]. 信息网络安全, 2023, 23(5): 32-40. |
| [14] | 毛红晶, 程驭坤, 胡红钢. 基于未知故障模型的多重持续故障分析[J]. 信息网络安全, 2023, 23(5): 41-49. |
| [15] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||