信息网络安全 ›› 2023, Vol. 23 ›› Issue (6): 55-65.doi: 10.3969/j.issn.1671-1122.2023.06.006
一种基于Intel SGX的信息中心网络隐私保护方案
- 1.中国科学技术大学先进技术研究院,合肥 230031
2.中国科学技术大学网络空间安全学院,合肥 230022
-
收稿日期:2023-03-30出版日期:2023-06-10发布日期:2023-06-20 -
通讯作者:张驰chizhang@ustc.edu.cn -
作者简介:唐雨(1998—),男,辽宁,硕士研究生,主要研究方向为可信硬件、计算机技术|张驰(1977—),男,湖北,副教授,博士,主要研究方向为无线网络、网络安全、区块链技术 -
基金资助:国家自然科学基金重点项目(U19B2023);国家重点研发计划(2018YFB0804201)
A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX
- 1. Institute of Advanced Technology, University of Science and Technology of China, Hefei 230031, China
2. School of Cyber Science and Technology, University of Science and Technology of China, Hefei 230022, China
-
Received:2023-03-30Online:2023-06-10Published:2023-06-20
摘要:
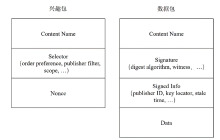
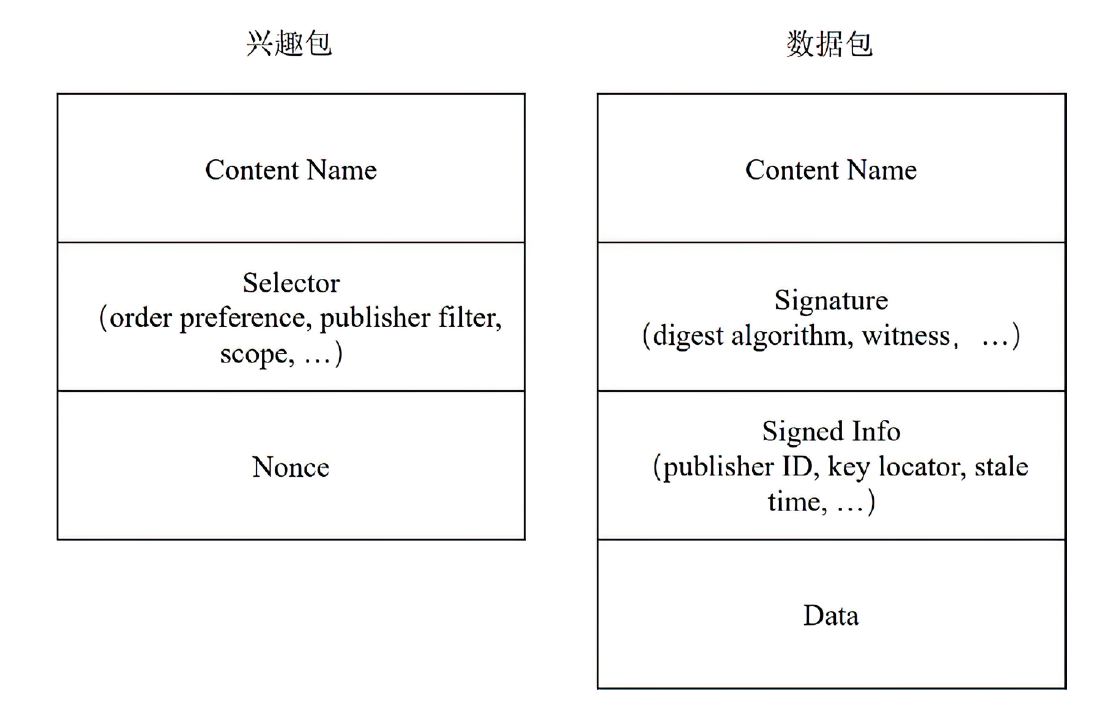
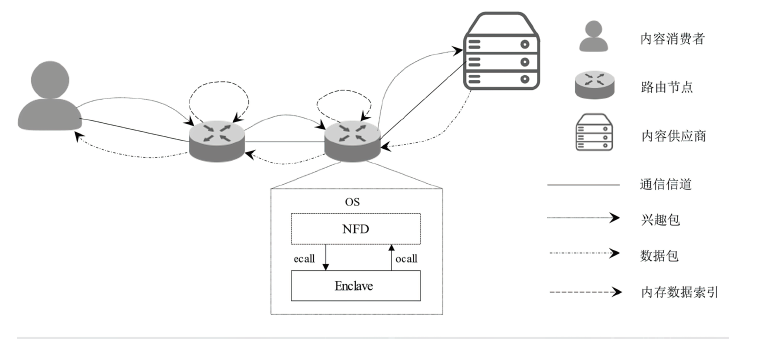
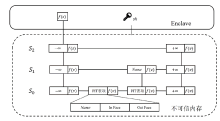
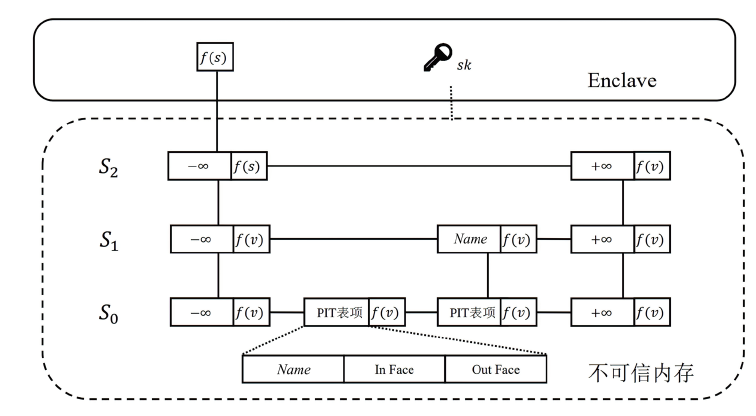
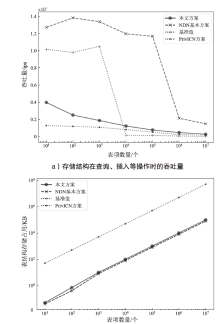
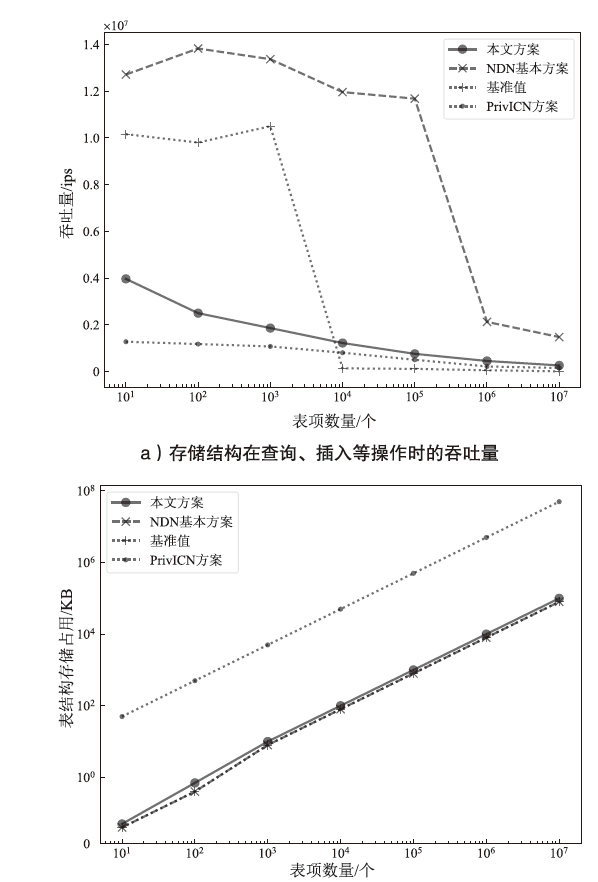
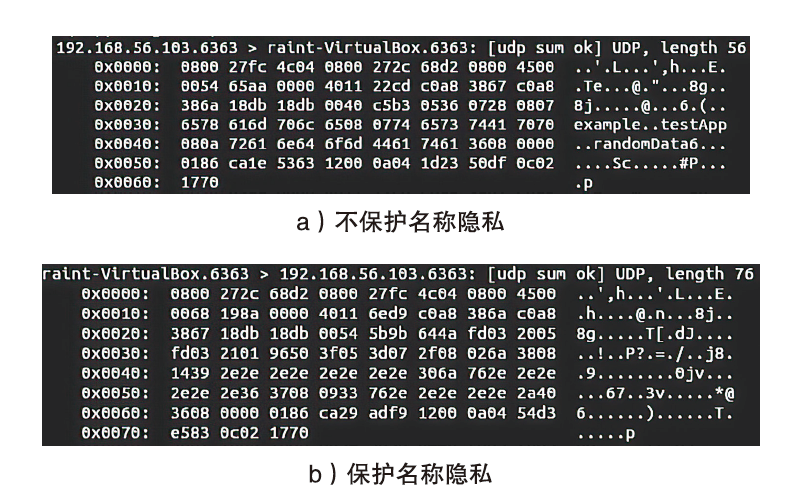
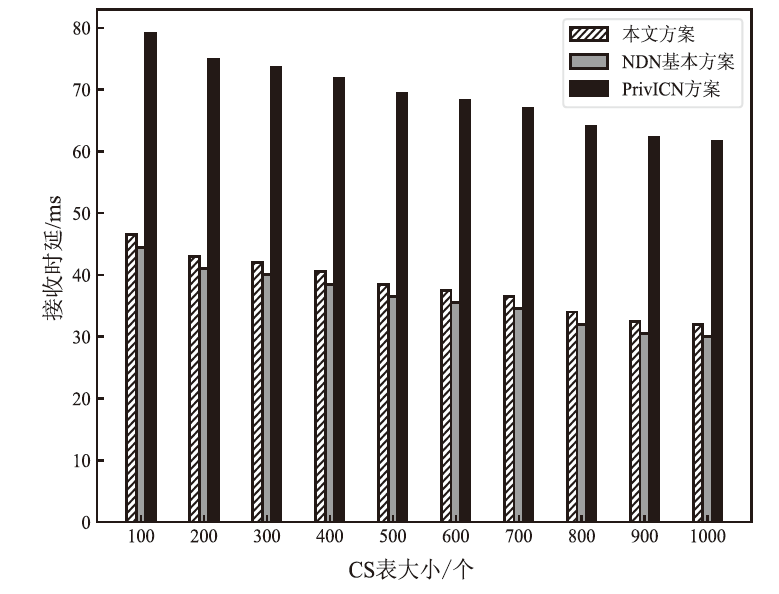
信息中心网络作为一种新型的网络架构,能够最大化利用网络带宽,实现快速、可靠、可扩展的内容交互服务。但是,由于信息中心网络的路由节点需要承担包括数据存储、名称检索等功能,其软硬件架构相对于传统网络而言也更复杂,这导致网络基础设施的安全性更加脆弱。文章提出一种基于可信执行环境的信息中心网络隐私保护方案,使用跳表实现网络主要内存数据的存储,并利用Intel SGX提供的可信执行环境保证存储在不可信内存数据的机密性和完整性,之后在此基础上提出一种保护网络内容包名称隐私的转发方案。实验结果表明,该方案在提供更高安全性的同时,其网络平均接收时延仅比NDN基本方案高10%左右。
中图分类号:
引用本文
唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65.
TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX[J]. Netinfo Security, 2023, 23(6): 55-65.
| [1] | GHODSI A, SHENKER S, KOPONEN T, et al. Information-Centric Networking: Seeing the Forest for the Trees[C]// ACM.Proceedings of the 10th ACM Workshop on Hot Topics in Networks. New York: ACM, 2011: 1-6. |
| [2] | FURDEK M, WOSINSKA L, GOŚCIEŃ R, et al. An Overview of Security Challenges in Communication Networks[C]// IEEE. 2016 8th International Workshop on Resilient Networks Design and Modeling (RNDM). New York:IEEE, 2016: 43-50. |
| [3] | AHLGREN B, DANNEWITZ C, IMBRENDA C, et al. A Survey of Information-Centric Networking[J]. IEEE Communications Magazine, 2012, 50(7): 26-36. |
| [4] | BERTINO E, NABEEL M. Securing Named Data Networks: Challenges and the Way Forward[C]// ACM. Proceedings of the 23nd ACM on Symposium on Access Control Models and Technologies. New York: ACM, 2018: 51-59. |
| [5] | BARDHI E, CONTI M, LAZZERETTI R, et al. Security and Privacy of IP-ICN Coexistence: A Comprehensive Survey[EB/OL]. (2022-09-06)[2023-03-20]. https://arxiv.org/abs/2209.02835. |
| [6] | JACOBSON V, SMETTERS D K, THORNTON J D, et al. Networking Named Content[J]. Communications of the ACM, 2012, 55(1): 117-124. |
| [7] | GRAMPP F T, MORRIS R H. The Unix System: Unix Operating System Security[J]. AT&T Bell Laboratories Technical Journal, 1984, 63(8): 1649-1672. |
| [8] |
FOTIOU N, POLYZOS G C. Name-Based Security for Information-Centric Networking Architectures[J]. Future Internet, 2019, 11(11): 1-13.
doi: 10.3390/fi11010001 URL |
| [9] | WU Danye, XU Zhiwei, CHEN Bo, et al. What if Routers are Malicious? Mitigating Content Poisoning Attack in NDN[C]// IEEE. IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York:IEEE, 2016: 481-488. |
| [10] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2016-01-31)[2023-03-20]. https://ia.cr/2016/086. |
| [11] | ZHANG Zhiyi, WON S Y, ZHANG Lixia. Investigating the Design Space for Name Confidentiality in Named Data Networking[C]// IEEE. MILCOM 2021-2021 IEEE Military Communications Conference (MILCOM). New York:IEEE, 2021: 570-576. |
| [12] |
CHAABANE A, DE CRISTOFARO E, KAAFAR M A, et al. Privacy in Content-Oriented Networking: Threats and Countermeasures[J]. ACM SIGCOMM Computer Communication Review, 2013, 43(3): 25-33.
doi: 10.1145/2500098.2500102 URL |
| [13] |
BRODER A, MITZENMACHER M. Network Applications of Bloom Filters: A Survey[J]. Internet Mathematics, 2004, 1(4): 485-509.
doi: 10.1080/15427951.2004.10129096 URL |
| [14] |
BERNARDINI C, MARCHAL S, ASGHAR M R, et al. PrivICN: Privacy-Preserving Content Retrieval in Information-Centric Networking[J]. Computer Networks, 2019, 149: 13-28.
doi: 10.1016/j.comnet.2018.11.012 URL |
| [15] |
GUO Xian, CHEN Cheng, ZHANG Majiang, et al. Privacy-Aware Transmission Scheme Based on Homomorphic Proxy Re-Encryption for NDN[J]. International Journal of Security and Networks, 2018, 13(1): 58-70.
doi: 10.1504/IJSN.2018.090646 URL |
| [16] | BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Berlin:Springer, 2004: 506-522. |
| [17] |
KO K T, HLAING H H, MAMBO M. A PEKS-Based NDN Strategy for Name Privacy[J]. Future Internet, 2020, 12(8): 1-22.
doi: 10.3390/fi12010001 URL |
| [18] | DIBENEDETTO S, GASTI P, TSUDIK G, et al. ANDaNA: Anonymous Named Data Networking Application[EB/OL]. (2012-01-10)[2023-03-20]. https://arxiv.org/abs/1112.2205. |
| [19] | SYVERSON P, DINGLEDINE R, MATHEWSON N. Tor: The Second Generation Onion Router[C]// USENIX. Proceedings of the 13th USENIX Security Symposium. San Diego: USENIX, 2004: 303-320. |
| [20] | GOODRISH M T, TAMASSIA R, SCHWERIN A. Implementation of an Authenticated Dictionary with Skip Lists and Commutative Hashing[C]// IEEE. Proceedings DARPA Information Survivability Conference and Exposition II. DISCEX'01. New York:IEEE, 2001, 2: 68-82. |
| [21] |
SPRING N, MAHAJAN R, WETHERALL D. Measuring ISP Topologies with Rocketfuel[J]. ACM SIGCOMM Computer Communication Review, 2002, 32(4): 133-145.
doi: 10.1145/964725.633039 URL |
| [1] | 杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60. |
| [2] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [3] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [4] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| [5] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [6] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [7] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [8] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [9] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [10] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [11] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [12] | 王思蝶, 马兆丰, 罗守山, 徐单恒. 面向异构多链的区块链链上数据隐私保护方案[J]. 信息网络安全, 2022, 22(12): 67-75. |
| [13] | 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11): 24-35. |
| [14] | 梁广俊, 辛建芳, 倪雪莉, 马卓. 智能音箱安全与取证研究[J]. 信息网络安全, 2022, 22(10): 108-113. |
| [15] | 顾海艳, 蒋铜, 马卓, 朱季鹏. k-匿名改进算法及其在隐私保护中的应用研究[J]. 信息网络安全, 2022, 22(10): 52-58. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||