信息网络安全 ›› 2023, Vol. 23 ›› Issue (6): 43-54.doi: 10.3969/j.issn.1671-1122.2023.06.005
基于LCNN和LSTM混合结构的物联网设备识别方法
- 江南大学人工智能与计算机学院,无锡 214122
-
收稿日期:2023-03-15出版日期:2023-06-10发布日期:2023-06-20 -
通讯作者:王志豪wzh313239727@163.com -
作者简介:李志华(1969—),男,湖南,教授,博士,主要研究方向为云、边、端关键技术,信息安全及其与人工智能等学科交叉的研究|王志豪(1998—),男,河南,硕士研究生,主要研究方向为物联网安全 -
基金资助:国家自然科学基金(60704047);工业和信息化部智能制造项目(ZH-XZ-180004);中央高校基本科研业务费专项资金(JUSRP211A41);中央高校基本科研业务费专项资金(JUSRP42003);111基地建设项目(B2018)
IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure
- School of Artificial Intelligence and Computer Science, Jiangnan University, Wuxi 214122, China
-
Received:2023-03-15Online:2023-06-10Published:2023-06-20
摘要:
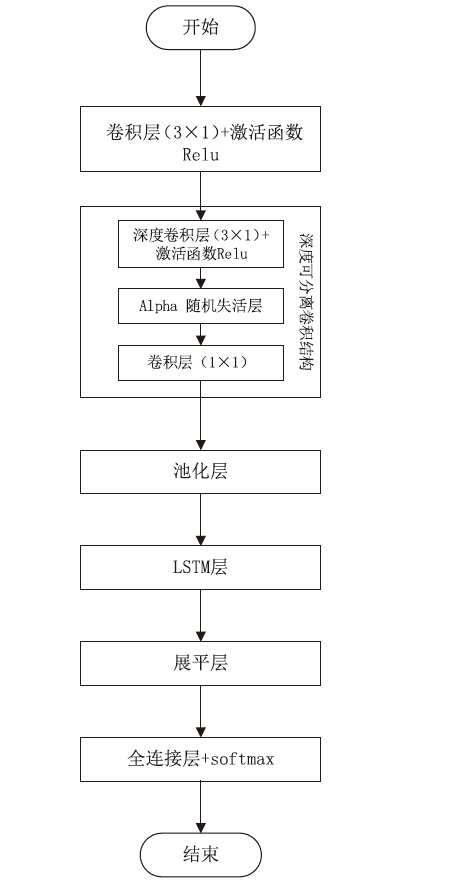
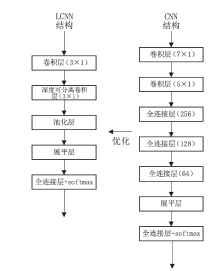
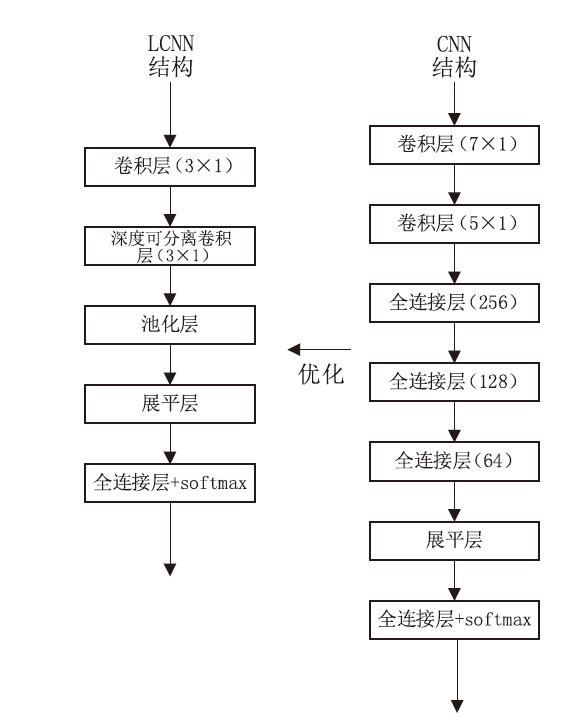
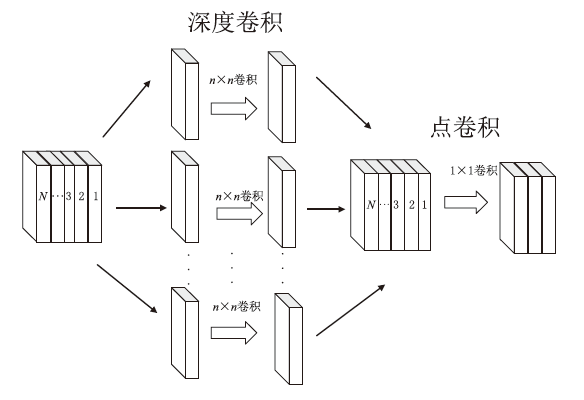
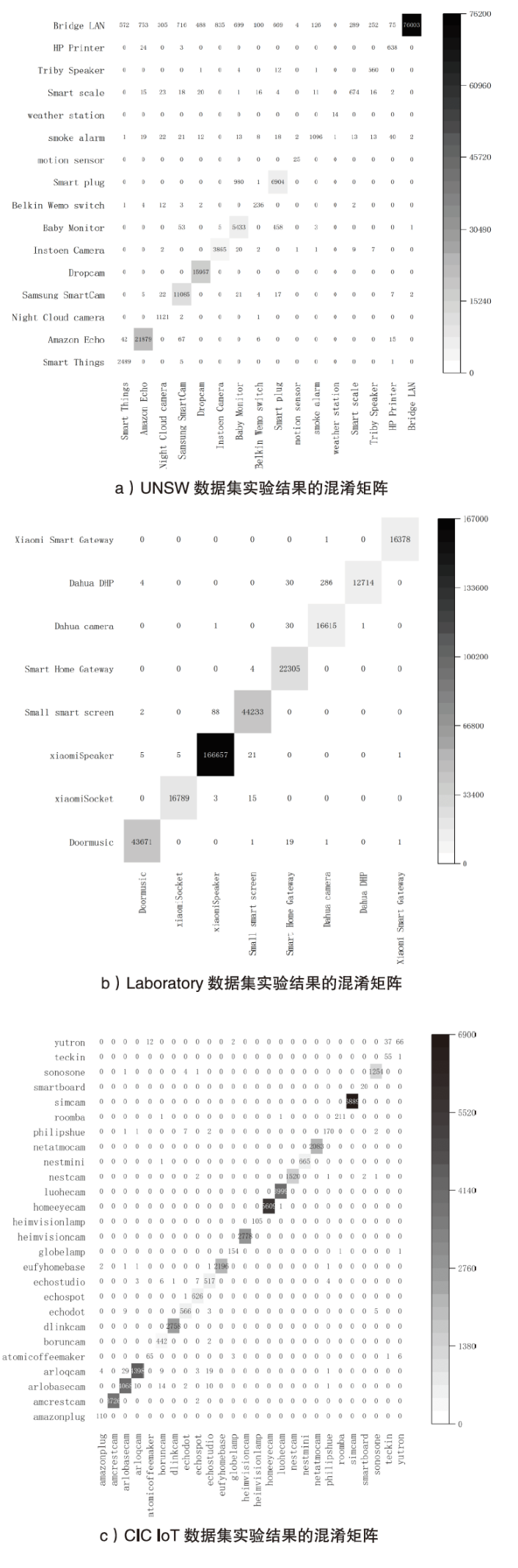
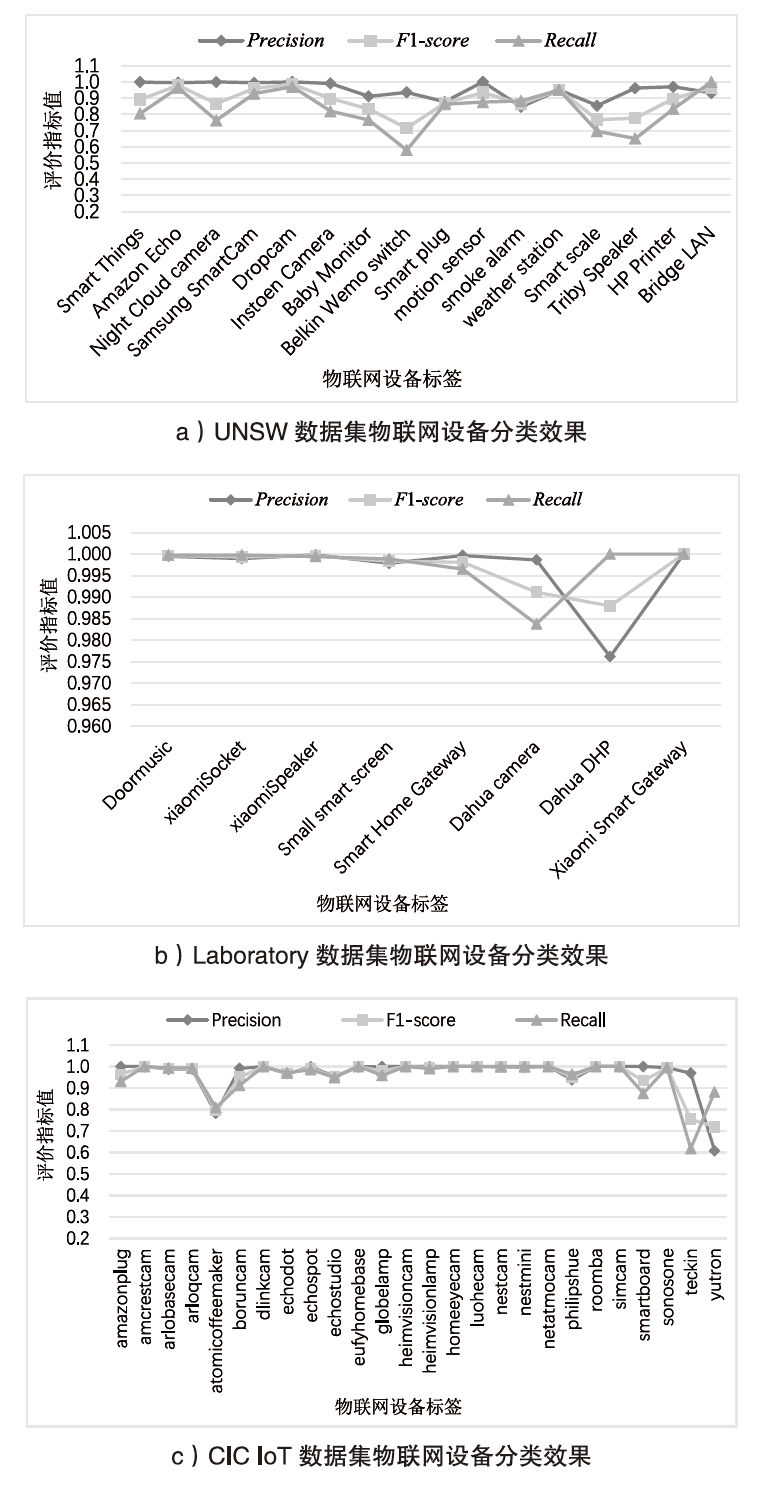
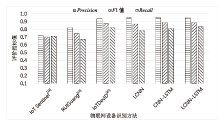
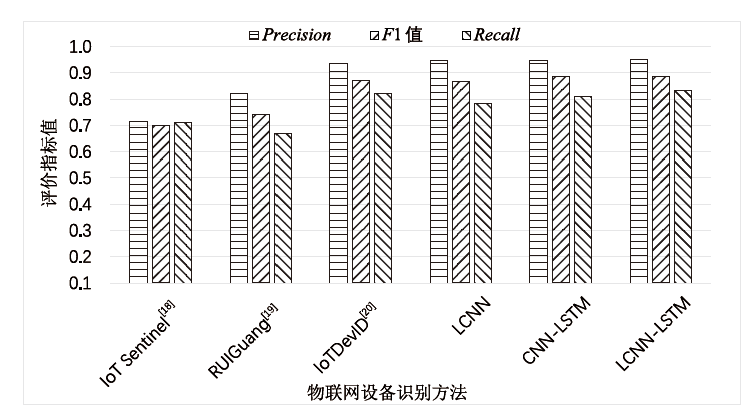
随着物联网设备数量的与日俱增,物联网环境中网络流量的规模也随之剧增,为了从海量的网络流量中高效地实现物联网设备的识别和分类,文章提出一种物联网设备识别方法。首先,为了消除网络流量中不规范的数据样本,研究并提出一种基于滑动窗口的数据预处理(Sliding Window-Based Data Pre-Processing,SW-Based DPP)算法,使用SW-Based DPP算法对数据进行清洗;然后,为了降低物联网设备识别方法的复杂度,通过把轻量级卷积神经网络(Lightwight Convolution Neural Network,LCNN)和LSTM结构进行结合,提出一种基于LCNN-LSTM混合结构的神经网络模型;接着,将数据预处理后的网络流量输入到LCNN-LSTM模型中进行物联网设备分类;最后,基于上述混合结构的神经网络模型,进一步提出一种基于LCNN和LSTM混合结构的物联网设备识别(Internet of Things Devices Identification Based on LCNN and LSTM Hybrid Structure,LCNN-LSTM-Based IoTDI)方法。该方法通过迭代训练LCNN-LSTM模型,深度挖掘网络流量中的时间和空间双重特征,并使用softmax分类器实现物联网设备识别的目标。实验结果表明,在UNSW、CIC IoT和Laboratory数据集上,LCNN-LSTM模型的运行时间与CNN-LSTM模型相比平均降低了约47.63%,并且LCNN-LSTM-Based IoTDI方法的F1值分别为88.6%、95.6%和99.7%。证明了该方法具有高效的设备识别能力。
中图分类号:
引用本文
李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54.
LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure[J]. Netinfo Security, 2023, 23(6): 43-54.
| [1] | STATISTA R D. Internet of Things-Number of Connected Devices Worldwide 2015-2025[EB/OL]. (2016-11-27)[2023-03-02]. https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/,2019. |
| [2] | NGUYEN-AN H, SILVERSTON T, YAMAZAKI T, et al. Entropy-Based IoT Devices Identification[C]// IEEE. 2020 21st Asia-Pacific Network Operations and Management Symposium (APNOMS). New York:IEEE, 2020: 73-78. |
| [3] | LI Weiyuan, LI Qin, LIU Rongxin. IoT Devices Identification Based on Machine Learning[C]// IEEE. 2021 IEEE 21st International Conference on Communication Technology (ICCT). New York:IEEE, 2021: 770-777. |
| [4] | AMMAR N, NOIRIE L, TIXEUIL S. Autonomous Identification of IoT Device Types Based on a Supervised Classification[C]// IEEE. ICC 2020-2020 IEEE International Conference on Communications (ICC). New York:IEEE, 2020: 1-6. |
| [5] | ULLAH I, MAHMOUD Q H. Network Traffic Flow Based Machine Learning Technique for IoT Device Identification[C]// IEEE. 2021 IEEE International Systems Conference (SysCon). New York:IEEE, 2021: 1-8. |
| [6] | SUN Yizhen, FU Shupo, ZHANG Shigeng, et al. Accurate IoT Device Identification from Merely Packet Length[C]// IEEE. 2020 16th International Conference on Mobility, Sensing and Networking (MSN). New York:IEEE, 2020: 774-778. |
| [7] | ZHANG Liwu, GONG Liangliang, QIAN Hankun. An Effiective IoT Device Identification Using Machine Learning Algorithm[C]// IEEE. 2020 IEEE 6th International Conference on Computer and Communications (ICCC). New York:IEEE, 2020: 874-877. |
| [8] | NGUYEN T D, MARCHAL S, MIETTINEN M, et al. DIoT: A Federated Self-Learning Anomaly Detection system for IoT[C]// IEEE. 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS). New York:IEEE, 2019: 756-767. |
| [9] | YIN Feihong, LI Yang, WANG Yuchen, et al. IoT etei: End-to-End IoT Device Identification Method[C]// IEEE. 2021 IEEE Conference on Dependable and Secure Computing (DSC). New York:IEEE, 2021: 1-8. |
| [10] | CHEN Qinggang, DU Yanhui, HAN Yi, et al. IoT Device Recognition Model Based on Depthwise Separable Convolution[J]. Netinfo Seurity, 2021, 21(9): 67-73. |
| 陈庆港, 杜彦辉, 韩奕, 等. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. | |
| [11] |
QING Guangwei, WANG Huifang, GUO Liang, et al. Device Type Identification via Network Traffic and Lightweight Convolutional Neural Network for Internet of Things[J]. IEEE Access, 2020, 8: 200219-200228.
doi: 10.1109/Access.6287639 URL |
| [12] |
RADHAKRISHNAN S V, ULUAGAC A S, BEYAH R. GTID: A Technique for Physical Device and Device Type Fingerprinting[J]. IEEE Transactions on Dependable and Secure Computing, 2014, 12(5): 519-532.
doi: 10.1109/TDSC.2014.2369033 URL |
| [13] |
KOHNO T, BROIDO A, CLAFFY K C. Remote Physical Device Fingerprinting[J]. IEEE Transactions on Dependable and Secure Computing, 2005, 2(2): 93-108.
doi: 10.1109/TDSC.2005.26 URL |
| [14] | LANZE F, PANCHENKO A, BRAATZ B, et al. Clock Skew Based Remote Device Fingerprinting Demystified[C]// IEEE. 2012 IEEE Global Communications Conference (GLOBECOM). New York:IEEE, 2012: 813-819. |
| [15] | FENG Xuan, LI Qiang, ZHU Hongsong, et al. Active Profiling of Physical Devices at Internet Scale[C]// IEEE. 2016 25th International Conference on Computer Communication and Networks (ICCCN). New York:IEEE, 2016: 1-9. |
| [16] | AMMAR N, NOIRIE L, TIXEUIL S. Network-Protocol-Based IoT Device Identification[C]// IEEE. 2019 Fourth International Conference on Fog and Mobile Edge Computing (FMEC). New York:IEEE, 2019: 204-209. |
| [17] |
YU Changhong, LU Ya, WANG Haixin, et al. IoT Device Traffic Classification Algorithm Based on Sliding Time Window[J]. Computer Engineering, 2022, 10(8): 1-13.
doi: 10.1007/BF01206535 URL |
| 余长宏, 陆雅, 王海鑫, 高明. 基于滑动时间窗的物联网设备流量分类算法[J]. 计算机工程: 2022, 10(8): 1-13. | |
| [18] | MIETTINEN M, MARCHAL S, HAFEEZ I, et al. IoT Sentinel: Automated Device-Type Identification for Security Enforcement in IoT[C]// IEEE. 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS). New York:IEEE, 2017: 2177-2184. |
| [19] | LI Ruiguang, DUAN Pengyu, SHEN Meng, et al. Traffic Classification Algorithm of Internet of Things Devices Based on Random Forest[J]. Journal of Beijing University of Aeronautics and Astronautics, 2022, 48(2): 233-239. |
| 李锐光, 段鹏宇, 沈蒙, 等. 基于随机森林的物联网设备流量分类算法[J]. 北京航空航天大学学报, 2022, 48(2): 233-239. | |
| [20] |
KOSTAS K, JUST M, Lones M A. IoTDevID: A Behavior-Based Device Identification Method for the IoT[J]. IEEE Internet of Things Journal, 2022, 9(23): 23741-23749.
doi: 10.1109/JIOT.2022.3191951 URL |
| [21] | HOWARD A G, ZHU Menglong, CHEN Bo, et al. Mobilenets: Efficient Convolutional Neural Networks for Mobile Vision Applications[EB/OL]. (2017-04-17)[2023-03-02]. http://arxiv.org/abs/1704.04861, 2017-04-17. |
| [22] |
GREFF K, SRIVASTAVA R K, KOUTNÍK J, et al. LSTM: A Search Space Odyssey[J]. IEEE Transactions on Neural Networks and Learning Systems, 2016, 28(10): 2222-2232.
doi: 10.1109/TNNLS.2016.2582924 URL |
| [23] | SIVANATHAN A, SHERRATT D, GHARAKHEILI H H, et al. Characterizing and Classifying IoT Traffic in Smart Cities and Campuses[C]// IEEE. 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York:IEEE, 2017: 559-564. |
| [24] | DADKHAH S, MAHDIKHANI H, DANSO P K, et al. Towards the Development of a Realistic Multidimensional IoT Profiling Dataset[C]// IEEE. 2022 19th Annual International Conference on Privacy, Security & Trust (PST). New York:IEEE, 2022: 1-11. |
| [1] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [2] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [3] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [4] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| [5] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [6] | 刘光杰, 段锟, 翟江涛, 秦佳禹. 基于多特征融合的移动流量应用识别[J]. 信息网络安全, 2022, 22(7): 18-26. |
| [7] | 赵洪, 李姗, 左珮良, 魏占祯. 基于强化学习的物联网安全资源分配方法[J]. 信息网络安全, 2022, 22(6): 44-52. |
| [8] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [9] | 张光华, 闫风如, 张冬雯, 刘雪峰. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10. |
| [10] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [11] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [12] | 韩俐, 宋吉祥, 孙士民. SD-IoT中基于设备地址的移动目标防御机制研究[J]. 信息网络安全, 2022, 22(11): 36-46. |
| [13] | 林发鑫, 张健. 虚拟化平台异常行为检测系统的设计与实现[J]. 信息网络安全, 2022, 22(11): 62-67. |
| [14] | 张郅, 李欣, 叶乃夫, 胡凯茜. 融合多重风格迁移和对抗样本技术的验证码安全性增强方法[J]. 信息网络安全, 2022, 22(10): 129-135. |
| [15] | 高昌锋, 肖延辉, 田华伟. 基于多阶段渐进式神经网络的图像相机指纹提取算法[J]. 信息网络安全, 2022, 22(10): 15-23. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||