信息网络安全 ›› 2021, Vol. 21 ›› Issue (12): 31-37.doi: 10.3969/j.issn.1671-1122.2021.12.005
基于离散轨迹的重点人员伴随关系挖掘模型
- 1.湖南警察学院网络侦查技术湖南省重点实验室,长沙 410138
2.国防科技大学系统工程学院,长沙 410073
3.警务物联网应用技术公安部重点实验室,北京 100089
4.国防科技大学计算机学院,长沙 410073
-
收稿日期:2021-09-25出版日期:2021-12-10发布日期:2022-01-11 -
通讯作者:赵薇 E-mail:zhaowei08a@nudt.edu.cn -
作者简介:康文杰(1987—),男,山西,讲师,博士,主要研究方向为复杂网络、物联网安全、警务大数据|赵薇(1982—),女,湖南,副教授,硕士,主要研究方向为大数据与网络安全|刘绪崇(1974—),男,湖南,教授,博士,主要研究方向为警务大数据|苏欣(1983—),男,湖南,副教授,博士,主要研究方向为警务大数据 -
基金资助:湖南省科技厅重点研发项目(2022SK2109);长沙市自然科学基金(kq2007088);高新技术产业科技创新引领计划(2020GK2029);网络犯罪侦查湖南省普通高校重点实验室开放基金课题(2020WLZC003);湖南警察学院2021年度高层次人才科研启动基金(2021KYQD16);湖南警察学院2021年度高层次人才科研启动基金(2021KYQD15);警务物联网应用技术公安部重点实验室2020年度开放课题
Adjoint Relation Mining Model of Key Personnel Based on Discrete Trajectory
KANG Wenjie1,2,3, ZHAO Wei1,4( ), LIU Xuchong1, SU Xin1
), LIU Xuchong1, SU Xin1
- 1. Hunan Provincial Key Laboratory of Network Investigational Technology, Hunan Police Academy, Changsha 410138, China
2. College of Systems Engineering, National University of Defense Technology, Changsha 410073, China
3. The Key Laboratory of Police Internet of Things Application Ministry of Public Security, Beijing 100089, China
4. College of Computer, National University of Defense Technology, Changsha 410073, China
-
Received:2021-09-25Online:2021-12-10Published:2022-01-11 -
Contact:ZHAO Wei E-mail:zhaowei08a@nudt.edu.cn
摘要:
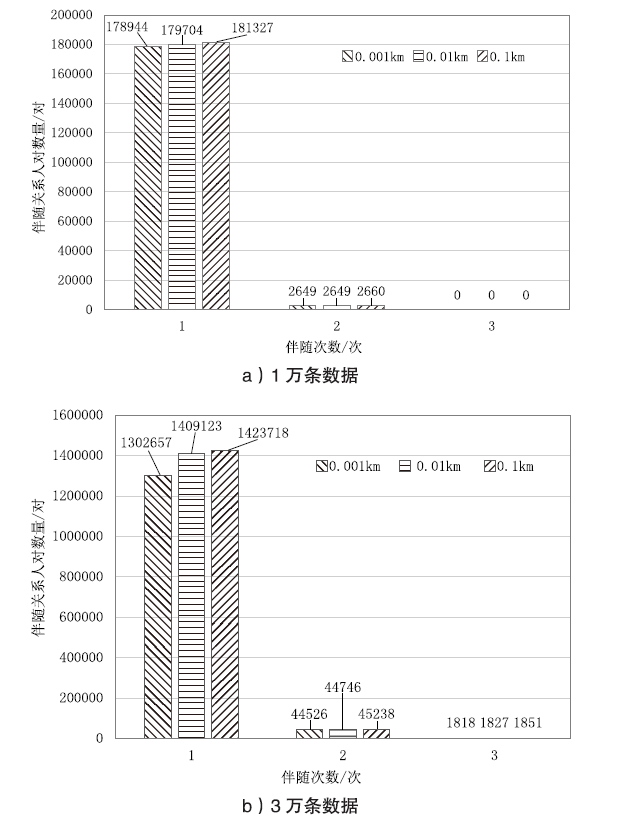
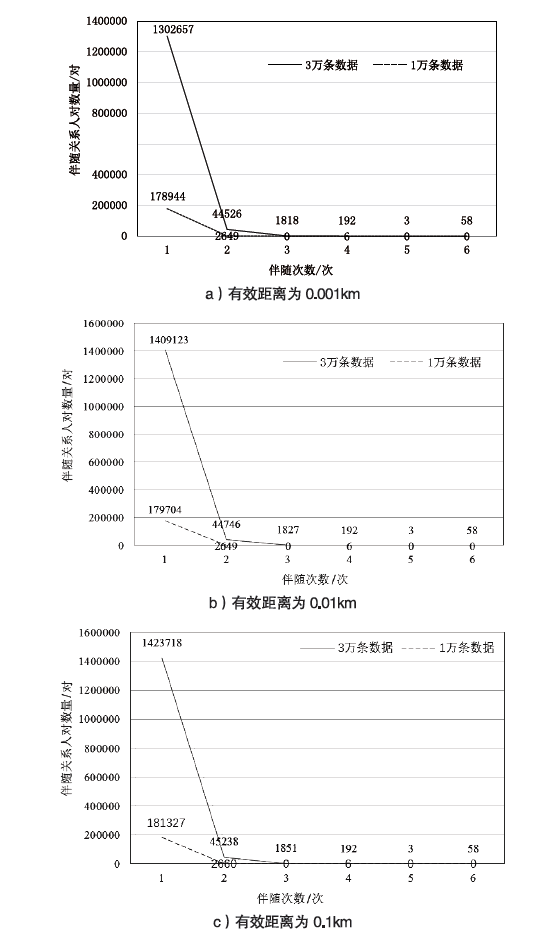
文章提出一种基于离散空间轨迹矩阵分析的重点人员伴随关系挖掘方法,针对离散空间轨迹构建人与地址的映射矩阵,通过对人员地址关系矩阵进行关联分析识别伴随关系,针对离散时空轨迹构建基于有效距离判定的伴随关系挖掘模型,通过距离、时间、空间等特征对重点人员进行伴随关系挖掘。实验结果表明,基于离散空间轨迹矩阵分析方法可以快速识别人群中存在伴随关系的人,且在给定某个重点人员的情况下,可以快速找到与之存在伴随关系的人群,并对这些人的伴随次数进行排序,便于安防人员溯源和追踪;伴随人的数量与有效距离在一定程度上成正比,伴随次数与数据量正相关。
中图分类号:
引用本文
康文杰, 赵薇, 刘绪崇, 苏欣. 基于离散轨迹的重点人员伴随关系挖掘模型[J]. 信息网络安全, 2021, 21(12): 31-37.
KANG Wenjie, ZHAO Wei, LIU Xuchong, SU Xin. Adjoint Relation Mining Model of Key Personnel Based on Discrete Trajectory[J]. Netinfo Security, 2021, 21(12): 31-37.
表1
某人出入某场所的次数统计
| 脱敏的身份证ID | 地址名 | 次数/次 |
|---|---|---|
| LKIJJPIQQPIIJJILIK3B | ***明明网吧 | 15 |
| LKIJJPIQQPIIJKILIQ3B | ***开心网吧 | 2 |
| LKIJJPIQQPIJHKLHML3B | ***大众网吧 | 1 |
| LKIJJPIQQPIJHMILIX3B | ***明明网吧 | 11 |
| LKIJJPIQQPIJIHIJMK3B | ***幻灵网吧 | 1 |
| LKIJJPIQQPIJIIIJIN3B | ***新浪网吧 | 2 |
| LKIJJPIQQPIJIKILIX3B | ***明明网吧 | 22 |
| LKIJJPIQQPIJILHLIJ3B | ***罗旧丁记网吧 | 1 |
| LKIJJPIQQPIJJHHHJL3B | ***飞宇网吧 | 1 |
| LKIJJPIQQPIJJIMHMP3B | ***飞宇网吧 | 1 |
| LKIJJPIQQPIJJJINIP3B | ***深蓝网吧 | 1 |
| LKIJJPIQQPIJJKKLIN3B | ***金连锁三星网吧分店 | 1 |
| LKIJJPIQQPIJJNHHIQ3B | ***梦工厂网咖旗舰店 | 1 |
| LKIJJPIQQPIJKHILIM3B | ***明明网吧 | 12 |
| ....... | ........ | ... |
| [1] | ZHENG Yu. Trajectory Data Mining: An Overview[J]. ACM Transactions on Intelligent Systems & Technology, 2015, 6(3):23-25. |
| [2] | SESTER M. Mining Group Movement Patterns[C]// ACM. ACM Sigspatial International Conference on Advances in Geographic Information Systems, November 5-7, 2013, Orlando, FL, United States. New York: ACM, 2013: 520-523. |
| [3] | LI Y, BAILEY J, KULIK L. Efficient Mining of Platoon Patterns in Trajectory Databases[M]. Amsterdam: Elsevier Science Publishers, 2015. |
| [4] |
YUAN Guan, SUN Penghui, ZHAO Jie, et al. A Review of Moving Object Trajectory Clustering Algorithms[J]. Artificial Intelligence Review, 2017, 47(1):123-144.
doi: 10.1007/s10462-016-9477-7 URL |
| [5] | WANG Shuang, WU Lina, ZHOU Fuchai, et al. Group Pattern Mining Algorithm of Moving Objects' Uncertain Trajectories[J]. International Journal of Computers Communications & Control, 2015, 10(3):428-440. |
| [6] |
DENG Ze, HU Yangyang, ZHU Mao, et al. A Scalable and Fast OPTICS for Clustering Trajectory Big Data[J]. Cluster Computing, 2015, 18(2):549-562.
doi: 10.1007/s10586-014-0413-9 URL |
| [7] | HU Wenbo, HUANG Wei, HU Guochao, et al. Trajectory Adjoint Pattern Analysis Based on OPTICS Clustering and Association Analysis[J]. Computer and Modernization, 2017, 16(12):82-87. |
| [8] | CAPDEVILA J, PERICACHO G, TORRES J, et al. Scaling DBSCAN Like Algorithms for Event Detection Systems in Twitter[M]. Heidelberg: Springer, 2016. |
| [9] |
FAN Tianhui, GUO Naijing, REN Yujie. Consumer Clusters Detection with Geo-tagged Social Network Data Using DBSCAN Algorithm: A Case Study of the Pearl River Delta in China[J]. GeoJournal, 2021, 86(6):317-337.
doi: 10.1007/s10708-019-10072-8 URL |
| [10] |
PERAFN-LPEZ J C, SIERRA-PREZ J. An Unsupervised Pattern Recognition Methodology Based on Factor Analysis and a Genetic-DBSCAN Algorithm to Infer Operational Conditions from Strain Measurements in Structural Applications[J]. Chinese Journal of Aeronautics, 2021, 34(2):165-181.
doi: 10.1016/j.cja.2020.09.035 URL |
| [11] | LI Yongnan. Research on Application of Spatial Patterns Mining in the Field of Counter Terrorism Intelligence Analysis[J]. Journal of Intelligence, 2018, 37(4):33-37. |
| 李勇男. 空间模式挖掘在反恐情报分析中的应用研究[J]. 情报杂志, 2018, 37(4):33-37. | |
| [12] | LI Yongnan. Research on Application of Frequent Spatiotemporal Trajectory Pattern Mining in the Field of Counter Terrorism Intelligence Analysis[J]. Journal of Intelligence, 2018, 37(8):51-55. |
| 李勇男. 时空轨迹频繁模式在反恐情报分析中的应用研究[J]. 情报杂志, 2018, 37(8):51-55. | |
| [13] | LI Wanqing, PENG Gao, FANG Fei, et al. Mining Method of Adjoint Behavior Pattern of Floating Vehicle Based on Big Data Analysis: China, CN105261218B[P]. 2017-08-08. |
| 李万清, 彭高, 方飞, 等. 基于大数据分析的浮动车伴随行为模式挖掘方法:中国,CN105261218B[P]. 2017-08-08. | |
| [14] | CHEN Peng, QU Ke, CHEN Gang, et al. The Constitution of Individual Feature Dataset and Analysis of Suspect in Counter-terrorism[J]. Journal of Intelligence, 2018, 37(4):38-41, 68. |
| 陈鹏, 瞿珂, 陈刚, 等. 反恐背景下的个人特征数据构成与涉恐个体的挖掘分析[J]. 情报杂志, 2018, 37(4):38-41,68. | |
| [15] | LI Yongnan. Clustering Analysis of Counter Terrorism Intelligence Based on Jaccard Index[J]. Modern Information, 2018, 38(1):51-55. |
| 李勇男. 基于雅卡尔系数的反恐情报聚类分析[J]. 现代情报, 2018, 38(1):51-55. | |
| [16] | YANG Yang, JI Genlin, BAO Peiming. Algorithm for Mining Adjoint Pattern of Spatial-temporal Trajectory Based on Grid Index[J]. Computer Science, 2016, 43(1):107-110. |
| 杨阳, 吉根林, 鲍培明. 基于网格索引的时空轨迹伴随模式挖掘算法[J]. 计算机科学, 2016, 43(1):107-110. | |
| [17] | HU Wenbo, HUANG Wei, HU Guochao. Trajectory Adjoint Pattern Analysis Based on OPTICS Clustering and Association Analysis[J]. Computer and Modernization, 2017(12):82-87. |
| 胡文博, 黄蔚, 胡国超. 基于OPTICS 聚类和关联分析的轨迹伴随模式分析[J]. 计算机与现代化, 2017(12):82-87. | |
| [18] |
XIA Huiyu. Navigational Risk Analysis Based on GIS Spatiotemporal Trajectory Mining: A Case Study in Nanjing Yangtze River Bridge Waters[J]. Arabian Journal of Geosciences, 2021, 14(3):1-15.
doi: 10.1007/s12517-020-06304-8 URL |
| [19] | LIU Hongbin, WU Hao, SUN Weiwei, et al. Spatio-temporal GRU for Trajectory Classification[C]// IEEE. 2019 IEEE International Conference on Data Mining(ICDM), Noveber 8-11, 2019, Beijing, China. New Jersey: IEEE, 2020: 1228-1233. |
| [20] | JIN Fengmei, HUA Wen, ZHOU T, et al. Trajectory-based Spatiotemporal Entity Linking[EB/OL]. https://arxiv.org/abs/2010.01516v1, 2020-10-04. |
| [21] | ANSARI M Y, MAINUDDIN, AHMAD A, et al. Spatiotemporal Trajectory Clustering: A Clustering Algorithm for Spatiotemporal Data[EB/OL]. https://doi.org/10.1016/j.eswa.2021.115048, 2021-09-15. |
| [22] | SHANG Shuo, CHEN Lisi, ZHENG Kai, et al. Parallel Trajectory-to-Location Join[J]. IEEE Transactions on Knowledge & Data Engineering, 2019, 31(6):1194-1207. |
| [23] | PIELA M, KOTAS M, CONTRERAS-ORTIZ S H, et al. Spatio-temporal Filtering for Evoked Potentials Detection[C]// Springer. International Conference on Man-machine Interactions, October 2-4, 2019, Cracow, Poland. Heidelberg: Springer, 2019: 34-43. |
| [24] |
REGENS J L, MOULD N, JENSEN III C J, et al. Effect of Intelligence Collection Training on Suspicious Activity Recognition by front Line Police Officers[J]. Security Journal, 2017, 30(3):951-962.
doi: 10.1057/sj.2015.10 URL |
| [25] | LI Yongnan. Construction of Decision-making System of Counter Terrorism Intelligence Driven by Big Data[J]. Journal of Intelligence, 2018, 37(10):57-61. |
| 李勇男. 大数据驱动的反恐情报决策体系构建[J]. 情报杂志, 2018, 37(10):57-61. | |
| [26] | LI Yongnan. Relational Analysis of Anti-terrorism Intelligence Based on Frequent Sequential Pattern Mining[J]. Information Studies: Theory & Application, 2018, 41(10):100-104, 46. |
| 李勇男. 基于频繁序列模式挖掘的反恐情报关联分析[J]. 情报理论与实践, 2018, 41(10):100-104,46. |
| [1] | 郭向民, 梁广俊, 夏玲玲. 基于HMM的Domain-Flux恶意域名检测及分析[J]. 信息网络安全, 2021, 21(12): 1-8. |
| [2] | 代翔, 孙海春, 牛硕, 朱容辰. 融合互注意力机制与BERT的中文问答匹配技术研究[J]. 信息网络安全, 2021, 21(12): 102-108. |
| [3] | 马瑞, 蔡满春, 彭舒凡. 一种基于改进的Xception网络的深度伪造视频检测模型[J]. 信息网络安全, 2021, 21(12): 109-117. |
| [4] | 王曦锐, 芦天亮, 张建岭, 丁锰. 基于加权Stacking集成学习的Tor匿名流量识别方法[J]. 信息网络安全, 2021, 21(12): 118-125. |
| [5] | 王威, 黄淑华. 基于对称加密的透明数字文件保密柜系统[J]. 信息网络安全, 2021, 21(12): 19-24. |
| [6] | 罗文华, 张耀文. 基于贝叶斯网络的电信网络诈骗受害人特征分析[J]. 信息网络安全, 2021, 21(12): 25-30. |
| [7] | 李鹏超, 刘彦飞. 基于删除PE文件头的恶意代码内存取证方法[J]. 信息网络安全, 2021, 21(12): 38-43. |
| [8] | 陈光宣, 吴家健, 操丹妮, 谢清泉. 一种基于Checkm8漏洞的iPhone取证方法研究[J]. 信息网络安全, 2021, 21(12): 44-50. |
| [9] | 熊建英. 基于信息行为的社交网络节点信誉评估模型研究[J]. 信息网络安全, 2021, 21(12): 51-59. |
| [10] | 倪雪莉, 王群, 梁广俊. 微信证据的鉴真方法研究[J]. 信息网络安全, 2021, 21(12): 60-69. |
| [11] | 张淑清, 蔡志文. 云数据下基于可问责属性即可撤销的加密方案[J]. 信息网络安全, 2021, 21(12): 70-77. |
| [12] | 高见, 王凯悦, 黄淑华. 面向视频监控网络的安全评估指标体系研究[J]. 信息网络安全, 2021, 21(12): 78-85. |
| [13] | 胡刚毅, 彭金. 一种警务图像加密算法[J]. 信息网络安全, 2021, 21(12): 86-90. |
| [14] | 徐国天, 刘猛猛. 基于改进哈里斯鹰算法同步优化特征选择的恶意软件检测方法[J]. 信息网络安全, 2021, 21(12): 9-18. |
| [15] | 朱容辰, 李欣, 林小暖. 基于贝叶斯网络的视频专网安全风险分析方法[J]. 信息网络安全, 2021, 21(12): 91-101. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||