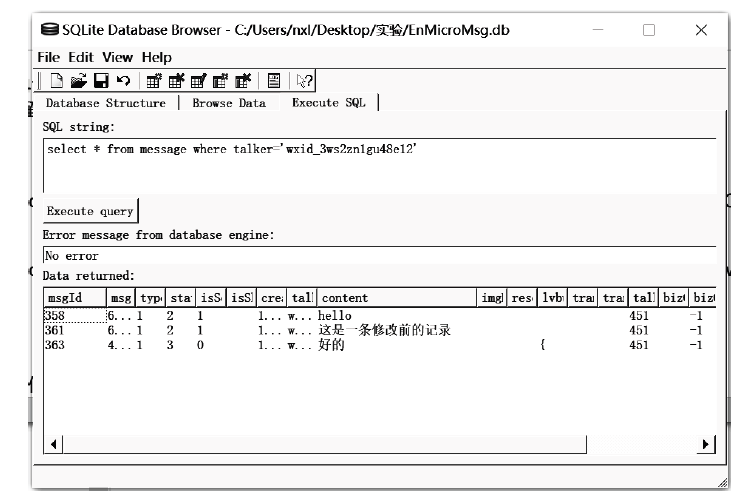
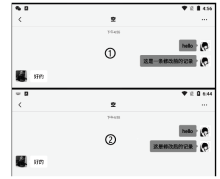
信息网络安全 ›› 2021, Vol. 21 ›› Issue (12): 60-69.doi: 10.3969/j.issn.1671-1122.2021.12.009
微信证据的鉴真方法研究
- 1.江苏警官学院计算机信息与网络安全系,南京 210031
2.江苏省电子数据取证分析工程研究中心,南京 210031
3.江苏省公安厅数字取证重点实验室,南京 210031
-
收稿日期:2021-09-22出版日期:2021-12-10发布日期:2022-01-11 -
通讯作者:倪雪莉 E-mail:nixueli@jspi.edu.cn -
作者简介:倪雪莉(1990—),女,江苏,讲师,硕士,主要研究方向为信息安全、电子数据取证|王群(1971—),男,甘肃,教授,博士, 主要研究方向为网络空间安全治理、电子数据取证|梁广俊(1982—),男,安徽,讲师,博士,主要研究方向为电子数据取证、网络空间安全 -
基金资助:江苏省高校自然科学研究重大项目(20KJA520004)
Research on Authentication Method of WeChat Evidence
NI Xueli1,2,3( ), WANG Qun1,2,3, LIANG Guangjun1,2,3
), WANG Qun1,2,3, LIANG Guangjun1,2,3
- 1. Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
2. Jiangsu Electronic Data Forensics and Analysis Engineering Research Center, Nanjing 210031, China
3. Jiangsu Provincial Public Security Department Key Laboratory of Digital Forensics,Nanjing 210031, China
-
Received:2021-09-22Online:2021-12-10Published:2022-01-11 -
Contact:NI Xueli E-mail:nixueli@jspi.edu.cn
摘要:
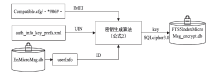
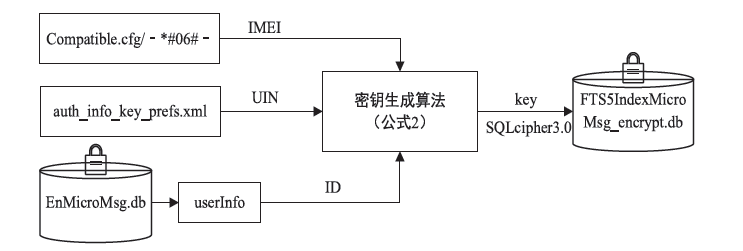
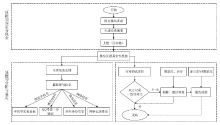
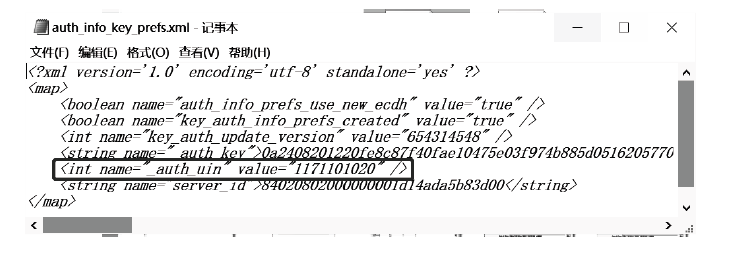
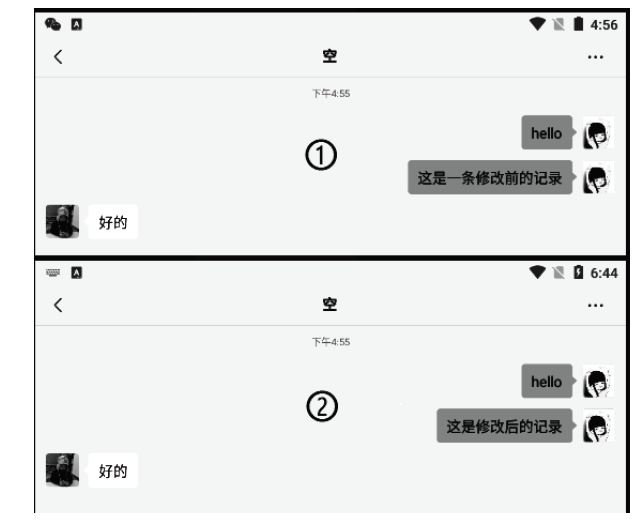
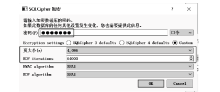
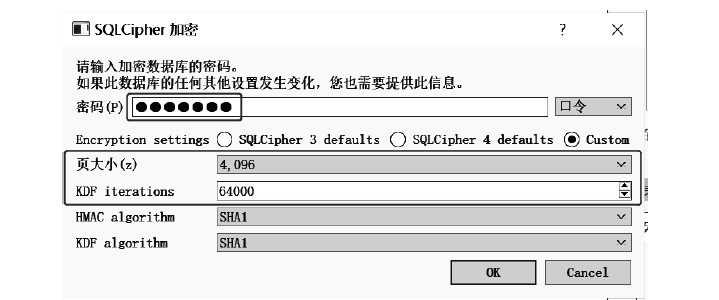
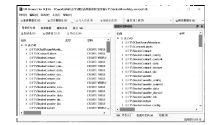
近年来,微信证据在庭审中出现的频率越来越高,与传统证据相比,微信证据由于主体和内容的虚拟性,其真实性常常受到质疑。现有的微信证据审查实践缺乏明确的流程规范且鉴真技术尚不完善,针对这一现状,基于微信账户的特征及微信数据库的存储加密原理,文章提出一种针对微信证据的鉴真取证模型,该模型结合法律维度,从主体的认证、消息的完整性确认、消息内容的鉴真等方面着手,覆盖证据的固定保全、分析鉴定全流程,体现了程序规则与技术措施的有效结合。通过引入微信索引库比对技术进行微信消息的篡改检测实验,验证了该模型的正确性和可行性。
中图分类号:
引用本文
倪雪莉, 王群, 梁广俊. 微信证据的鉴真方法研究[J]. 信息网络安全, 2021, 21(12): 60-69.
NI Xueli, WANG Qun, LIANG Guangjun. Research on Authentication Method of WeChat Evidence[J]. Netinfo Security, 2021, 21(12): 60-69.
| [1] | GU Guoyan, LOU Linli, GONG Feng, et al. Authentication of Electronic Evidence-Taking WeChat as an Example[J]. Journal of Southeast University(Philosophy and Social Science), 2017, 19(S2):62-66. |
| 古国妍, 娄琳莉, 贡凤, 等. 电子证据的鉴真——以微信为例[J]. 东南大学学报(哲学社会科学版), 2017, 19(S2):62-66. | |
| [2] | PAN Ziwen, HU Yingying. Discussion on WeChat Evidence Preservation Notarization[J]. Legal System and Society, 2015(36):137-139, 141. |
| 潘子文, 胡莹莹. 关于微信证据保全公证的探讨[J]. 法制与社会, 2015(36):137-139,141. | |
| [3] | TAN Yuzhe. Analysis of the Obstacles and Countermeasures in the Application of Electronic Evidence in Civil Litigation-Taking WeChat Evidence as an Example[D]. Chengdu: Southwestern University of Finance and Economics, 2019. |
| 谭羽哲. 探析电子证据在民事诉讼中的运用障碍与对策——以微信证据为例[D]. 成都:西南财经大学, 2019. | |
| [4] | BAI Jinguo, SUN Hongsheng, HU Zeming. A Recovery Method of Deleted Data Based on SQLite3 File Format[J]. Journal of Chinese Computer Systems, 2016, 37(3):505-509. |
| 白晋国, 孙红胜, 胡泽明. 一种基于SQLite3文件格式的删除数据恢复方法[J]. 小型微型计算机系统, 2016, 37(3):505-509. | |
| [5] | WU Hao, CHEN Liquan, SHA Jing, et al. SQLite Data Recovery Scheme Based on Feature Matching Localization[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2018, 38(1):106-112. |
| 吴昊, 陈立全, 沙晶, 等. 一种基于特征匹配定位的SQLite数据恢复方法[J]. 南京邮电大学学报(自然科学版), 2018, 38(1):106-112. | |
| [6] | ZHANG Lijun, FEI Yu, JI Qingbing. The Forensic Analysis of WeChat Message[C]// IEEE. 2016 Sixth International Conference on Instrumentation & Measurement, Computer, Communication and Control(IMCCC), July 21-23, 2016, Harbin, China. Piscataway: IEEE, 2016: 500-503. |
| [7] | NI Xueli, LIANG Guangjun. Recovery Method of WeChat Revoking Message Based on Dynamic Memory Analysis[J]. Computer Engineering and Applications, 2021, 56(23):146-153. |
| 倪雪莉, 梁广俊. 引入动态内存分析的微信撤回消息恢复方法[J]. 计算机工程与应用, 2021, 56(23):146-153. | |
| [8] | ZENG Yudi. Study on the Quotation Rules of Electronic Evidence[D]. Changchun: Jilin University, 2018. |
| 曾宇迪. 电子数据质证规则研究[D]. 长春:吉林大学, 2018. | |
| [9] | JIANG Hongming, WU Pingping. Several Issues of Blockchain Evidence in the Online Procedure Rule of People’s Court[J]. Journal of Law Application, 2021, 32(7):150-163. |
| 蒋鸿铭, 吴平平. 《人民法院在线诉讼规则》区块链证据规则若干问题探析[J]. 法律适用, 2021, 32(7):150-163. | |
| [10] |
SHARMA P, ARORA D, SAKTHIVEL T. Enhanced Forensic Process for Improving Mobile Cloud Traceability in Cloud-based Mobile Applications[J]. Procedia Computer Science, 2020, 167(1):907-917.
doi: 10.1016/j.procs.2020.03.390 URL |
| [11] | MING Zhenya. Analysis on Forensics of WeChat Program Database Based on Android System[D]. Shanghai: East China University of Political Science and Law, 2019. |
| 明振亚. 基于Android系统的微信小程序数据库取证问题分析[D]. 上海:华东政法大学, 2019. | |
| [12] | DONG Hui. Research On Extraction and Authenticity Identification Method of WeChat Voice[D]. Lanzhou: Gansu Political Science and Law Institute, 2019. |
| 董慧. 微信语音的提取及真实性鉴定方法研究[D]. 兰州:甘肃政法学院, 2019. | |
| [13] | HAN Bei. Research and Application of SQLite Data-base[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2019. |
| 韩贝. SQLite数据库研究与应用[D]. 南京:南京邮电大学, 2019. | |
| [14] | WANG Chunlan, KANG Pengcheng. Overview of SQLite Data Recovery Technology for Android Phones[J]. Technology Innovation and Application, 2019, 8(32):160-161, 164. |
| 王春兰, 康鹏程. Android手机的Sqlite数据恢复技术综述[J]. 科技创新与应用, 2019, 8(32):160-161,164. | |
| [15] | KIM G, PARK M, LEE S, et al. A Study on the Decryption Methods of Telegram X and BBM-enterprise Databases in Mobile and PC[EB/OL]. https://doi.org/10.1016/j.fsidi.2020.300998, 2021-08-30. |
| [16] | CHANG Yacui. Research and Application of Remote Forensics Analysis for Android Phone[D]. Chongqin: Chongqing University of Posts and Telecommunications, 2017. |
| 常亚翠. 面向Android手机远程取证分析的研究与应用[D]. 重庆:重庆邮电大学, 2017. | |
| [17] | ZHU Yashuai. Research on Authentication Rules of Electronic Evidence in Criminal Cases[D]. Beijing: People’s Public Security University of China, 2019. |
| 朱亚帅. 刑事案件电子数据认证规则问题研究[D]. 北京:中国人民公安大学, 2019. | |
| [18] | LI Xiaolong, YU Nenghai, ZHANG Xinpeng, et al. Overview of Digital Media Forensics Technology[J]. Journal of Image and Graphics, 2021, 26(6):1216-1226. |
| 李晓龙, 俞能海, 张新鹏, 等. 数字媒体取证技术综述[J]. 中国图象图形学报, 2021, 26(6):1216-1226. | |
| [19] | CAO Taixun. Network Crime Profile Based on Intelligent Analysis of Electronic Data Forensics[J]. Netinfo Security, 2019, 19(9):31-35. |
| 曹太训. 基于电子数据取证智能化分析技术的网络犯罪侧写[J]. 信息网络安全, 2019, 19(9):31-35. | |
| [20] | LIAO Genwei. Research on Forensic Expertise of Electronic Data Authenticity[M]. Beijing: Law Press China, 2015. |
| 廖根为. 电子数据真实性司法鉴定研究[M]. 北京: 法律出版社, 2015. |
| [1] | 陈光宣, 吴家健, 操丹妮, 谢清泉. 一种基于Checkm8漏洞的iPhone取证方法研究[J]. 信息网络安全, 2021, 21(12): 44-50. |
| [2] | 丁丽萍, 刘雪花, 陈光宣, 李引. Android智能手机动态内存取证技术综述[J]. 信息网络安全, 2019, 19(2): 10-17. |
| [3] | 刘浩阳. MS SQL数据库在线取证研究[J]. 信息网络安全, 2016, 16(9): 26-30. |
| [4] | 韩马剑. 路由器取证研究[J]. 信息网络安全, 2016, 16(9): 51-55. |
| [5] | 刘浩阳. Android设备取证研究[J]. 信息网络安全, 2015, 15(9): 29-32. |
| [6] | 罗文华, 沈成轩. 利用KPCR结构获取内存敏感信息[J]. 信息网络安全, 2015, 15(3): 44-47. |
| [7] | . 基于虚拟机与API调用监控技术的APT木马取证研究[J]. , 2014, 14(4): 78-. |
| [8] | 贺滢睿;陆道宏;李建新;徐云峰. 面向iPhone手机的电子数据取证分析[J]. , 2013, 13(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||