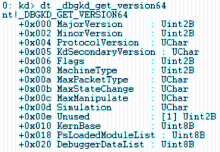
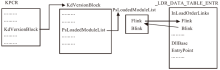
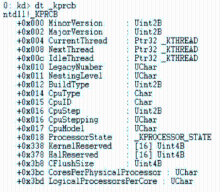
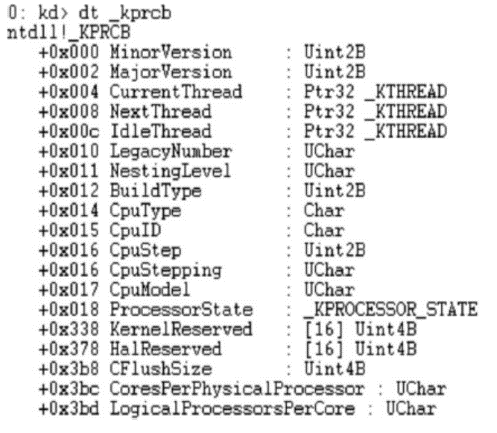
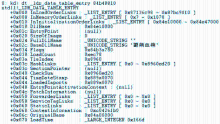
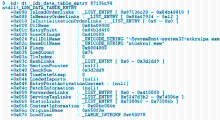
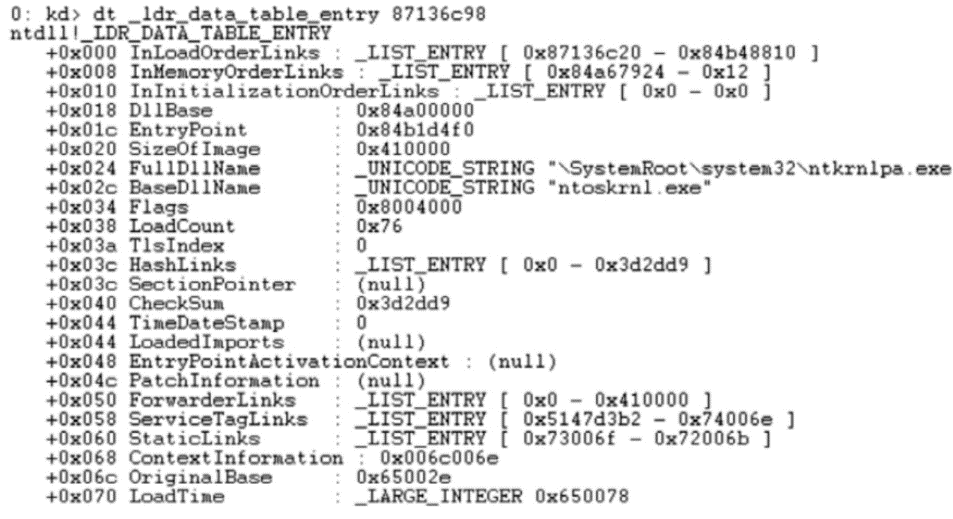
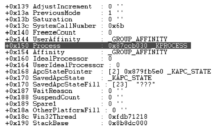
信息网络安全 ›› 2015, Vol. 15 ›› Issue (3): 44-47.doi: 10.3969/j.issn.1671-1122.2015.03.009
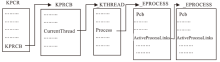
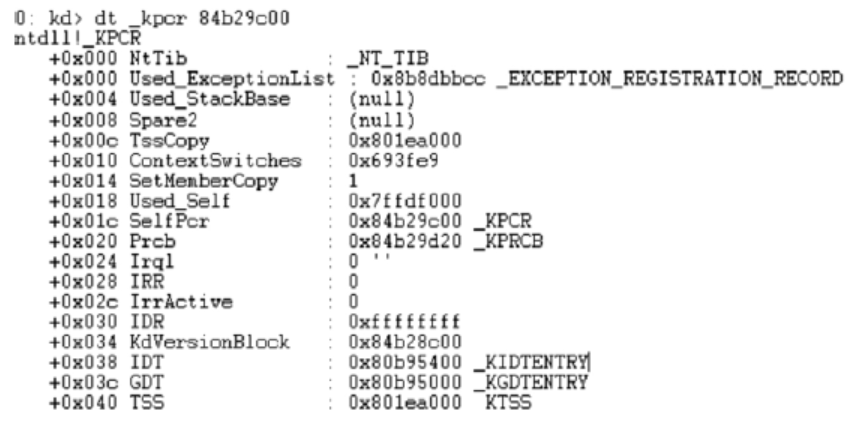
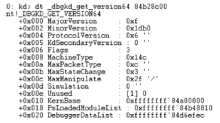
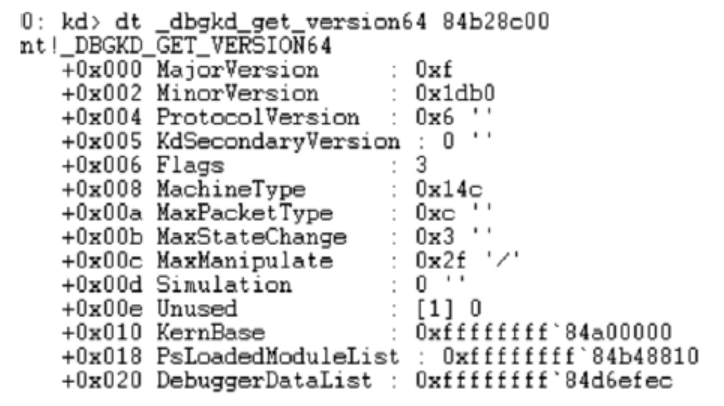
利用KPCR结构获取内存敏感信息
- 中国刑事警察学院网络犯罪侦查系,辽宁沈阳 110854
Obtaining Sensitive Information in RAM by Using the Structure of KPCR
LUO Wen-hua( ), SHEN Cheng-xuan
), SHEN Cheng-xuan
- Department of Cyber Crime Investigation, China Criminal Police University, Shenyang 110854, China