信息网络安全 ›› 2015, Vol. 15 ›› Issue (3): 38-43.doi: 10.3969/j.issn.1671-1122.2015.03.008
基于权限控制和脚本检测的Webview漏洞防护方案研究
- 国防科学技术大学电子科学与工程学院,湖南长沙 410073
An Webview Vulnerability Protection Based On Access Control And Script Detection
YE Jia-xi, ZHANG Quan( ), WANG Jian
), WANG Jian
- College of Electronic and Engineer, National University of Defense Technology, Changsha Hunan 410073, China
摘要:
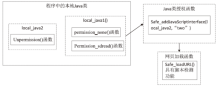
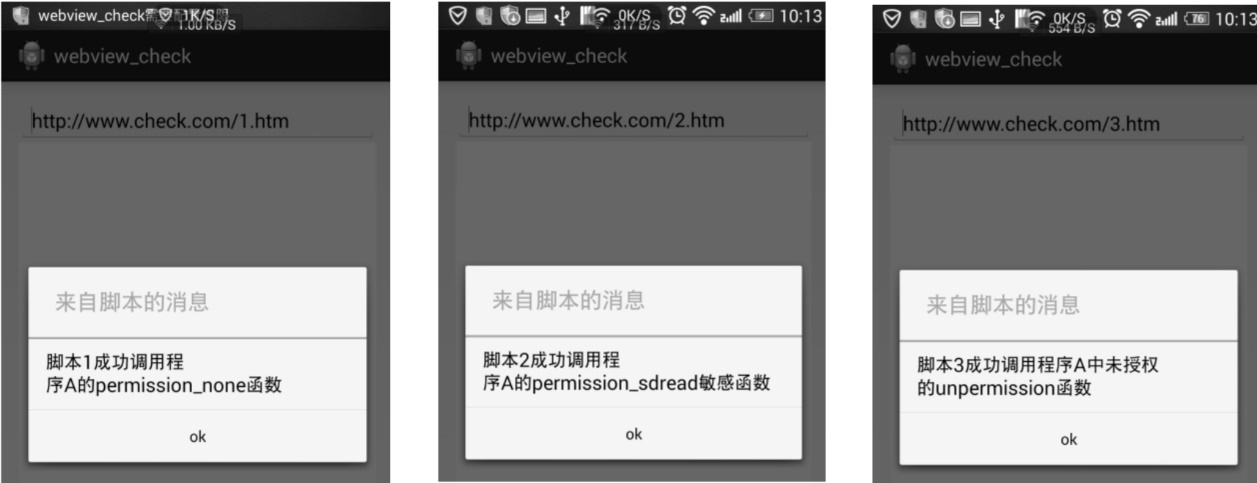
文章通过研究Webview漏洞的形成机理,获悉漏洞是由程序调用了不安全的系统API且未对Java反射机制进行防范而产生的。目前,Webview漏洞的检测方法主要是基于黑盒测试思想,准确率不高。文章提出了一种结合静态分析和动态分析的检测方法:通过静态分析对不安全函数进行定位,通过动态分析对不安全函数进行测试,能有效、精确地检测出Webview漏洞。同时,文章研究了Google公司提出的Webview漏洞防护方案,指出该方案存在的三大防护缺陷,并提出了一种基于权限控制和脚本检测的漏洞防护方法,该方法通过权限控制严格限制了访问者的权限上限,并及时向用户反馈情况;通过脚本检测区别出安全脚本和恶意脚本,在未削弱Webview组件能力的前提下,提高了漏洞防护能力。最后,文章设计了一组实验,对比了未添加Webview防护的程序和添加了Webview防护的程序对恶意代码的执行结果,证实该防护方法的有效性。
中图分类号: