信息网络安全 ›› 2015, Vol. 15 ›› Issue (3): 33-37.doi: 10.3969/j.issn.1671-1122.2015.03.007
针对手机的APT攻击方式的研究
- 1.公安部第一研究所,北京 100048
2. 北京邮电大学计算机学院,北京 100876
Research for APT Attack Technology
CHEN Chen1( ), WANG Yi-Jun1, HU Guang-jun1, GUO Yan-hui2
), WANG Yi-Jun1, HU Guang-jun1, GUO Yan-hui2
- 1.The First Research Institute of the Ministry of Public Security of P.R.C,Bejing 100048,China
2.School of Computer Science, Beijing University of Posts and Telecommunications, Beijing 100876, China
摘要:
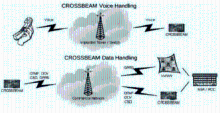
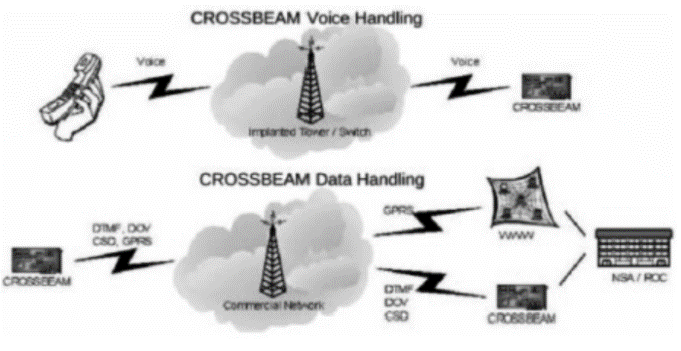
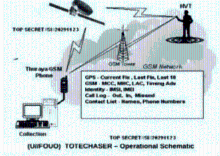
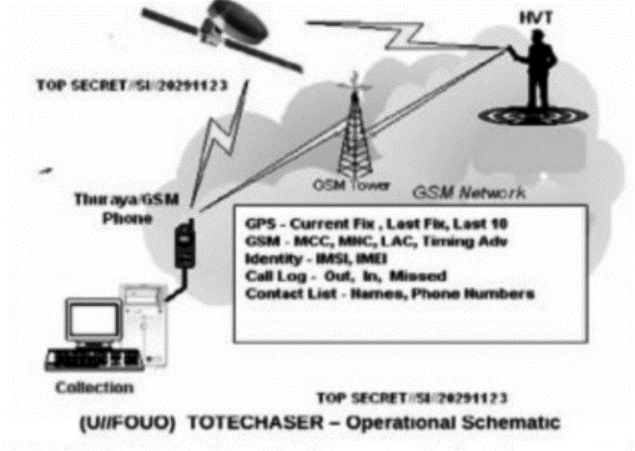
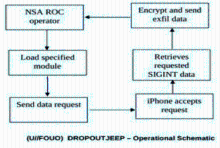
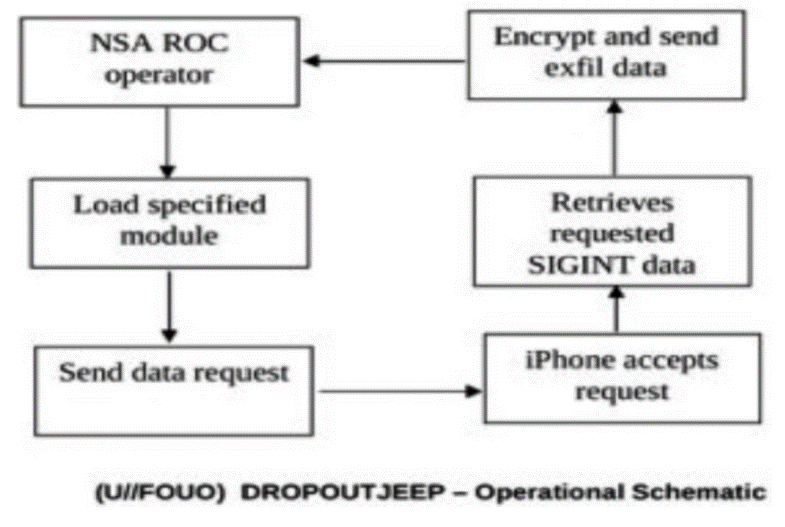
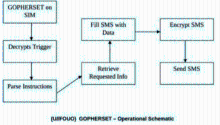
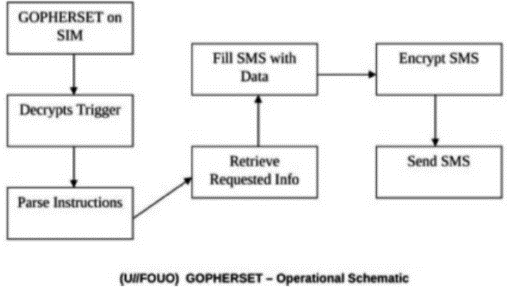
自2007年以来,高级持续威胁(Advanced Persistent Threat,APT)攻击不断被发现,如 2009 年的 Ghost Net攻击,专门盗取各国大使馆、外交部等政府机构以及银行的机密信息, 两年内就已渗透到至少 103个国家的1295 台政府和重要人物的电脑中;2010 年 6 月, Stuxnet首次被发现,是已知的第一个以关键工业基础设施为目标的蠕虫,其感染并破坏了伊朗纳坦兹核设施,并最终使伊朗布什尔核电站推迟启动;2011 年 9月发现的Duqu病毒, 被用来从工业控制系统制造商收集情报信息,目前已监测到来自法国、荷兰、瑞士及印度等 8个国家的 6家组织受到该病毒感染。安全专家认为一定还有 APT 攻击没有被人们发现,还有更多的公司由于种种原因而没有公布它们遭到 APT 攻击以及造成的损失。APT攻击已经成为近几年给国家、社会、企业、组织及个人造成了重大损失和影响的攻击形式。而越来越多的终端应用开始从传统的个人电脑向便携的个人智能手机上迁移,人们使用智能手机收发邮件、处理文件、与其他人进行即时通讯。为此,本文首先介绍APT攻击的定义,之后给出APT攻击的技术特点,最后介绍目前APT攻击中针对手机的最新攻击方式,以提高应对此类攻击的防范意识。
中图分类号: