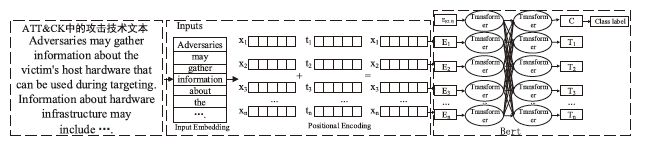
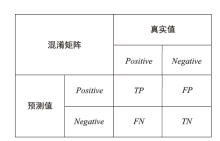
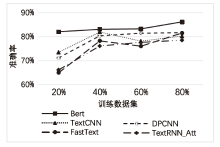
信息网络安全 ›› 2023, Vol. 23 ›› Issue (2): 26-34.doi: 10.3969/j.issn.1671-1122.2023.02.004
一种基于ATT&CK的新型电力系统APT攻击建模
- 华北电力大学控制与计算机工程学院,北京 102206
-
收稿日期:2022-10-09出版日期:2023-02-10发布日期:2023-02-28 -
通讯作者:李元诚 E-mail:ycli@ncepu.edu.cn -
作者简介:李元诚(1970—),男,山东,教授,博士,主要研究方向为网络信息安全|罗昊(1998—),男,湖北,硕士研究生,主要研究方向为网络信息安全|王庆乐(1987—),女,山东,副教授,博士,主要研究方向为量子密码|李建彬(1968—),男,山东,教授,博士,主要研究方向为网络空间安全
An Advanced Persistent Threat Model of New Power System Based on ATT&CK
LI Yuancheng( ), LUO Hao, WANG Qingle, LI Jianbin
), LUO Hao, WANG Qingle, LI Jianbin
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2022-10-09Online:2023-02-10Published:2023-02-28 -
Contact:LI Yuancheng E-mail:ycli@ncepu.edu.cn
摘要:
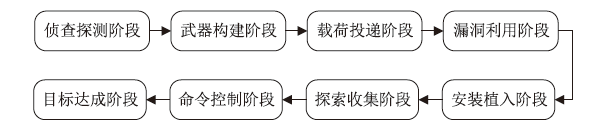
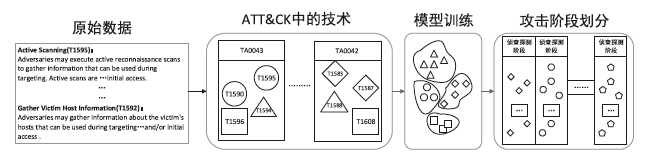
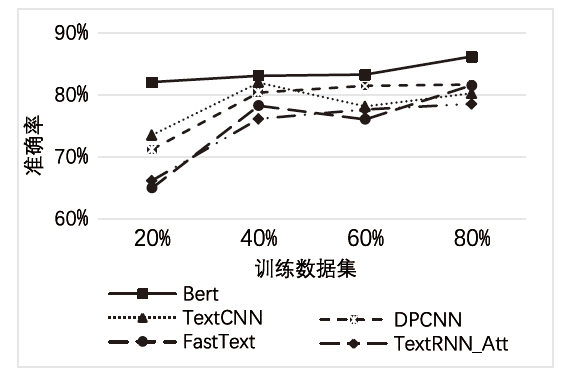
以新能源为主体的新型电力系统,新能源与多元负荷形态比例大幅提升。高比例的可再生新能源与电力电子设备的接入以及供给侧和需求侧的随机性,导致电网遭受的攻击面增大,攻击者利用隐蔽和复杂的手段针对新型电力系统发动高级可持续威胁攻击,严重影响电网调度与能源消纳。文章基于ATT&CK知识库建立了面向新型电力系统APT攻击的杀伤链模型,针对传统方法难以将 APT 攻击技术划分到杀伤链攻击阶段,从而导致安全员无法迅速做出防御决策的情况,提出了一种基于杀伤链模型的APT攻击技术阶段划分方法,并采用Bert模型对技术文本进行语义分析,自动将攻击技术划分到所属阶段。实验结果表明,文章所提方法比现有模型具有更好的效果。
中图分类号:
引用本文
李元诚, 罗昊, 王庆乐, 李建彬. 一种基于ATT&CK的新型电力系统APT攻击建模[J]. 信息网络安全, 2023, 23(2): 26-34.
LI Yuancheng, LUO Hao, WANG Qingle, LI Jianbin. An Advanced Persistent Threat Model of New Power System Based on ATT&CK[J]. Netinfo Security, 2023, 23(2): 26-34.
使用本文
| [1] |
HAN Xueyuan, PASQUIER T, BATES A, et al. UNICORN: Runtime Provenance-Based Detector for Advanced Persistent Threats[EB/OL]. (2020-01-06)[2022-08-20]. https://doi.org/10.48550/arXiv.2001.01525.
doi: https://doi.org/10.48550/arXiv.2001.01525 |
| [2] |
KARANTZAS G, PATSAKIS C. An Empirical Assessment of Endpoint Detection and Response Systems Against Advanced Persistent Threats Widely Used Attack Vectors[J]. Journal of Cybersecurity and Privacy, 2021, 1(3): 387-421.
doi: 10.3390/jcp1030021 URL |
| [3] |
LIU Jinxin, SHEN Yu, SIMSEK M, et al. A New Realistic Benchmark for Advanced Persistent Threats in Network Traffic[J]. IEEE Networking Letters, 2022, 4(3): 1-8.
doi: 10.1109/LNET.2022.3141489 URL |
| [4] |
HOFER-SCHMITZ K, KLEB U, STO-JANOVIC B. The Influences of Feature Sets on the Detection of Advanced Persistent Threats[J]. Electronics, 2021, 10(6): 704-712.
doi: 10.3390/electronics10060704 URL |
| [5] | SIDAHMED B, GHITA B, JAMES C, et al. A Rule Mining-Based Advanced Persistent Threats Detection System[EB/OL]. (2021-05-20)[2022-07-28]. https://doi.org/10.48550/arXiv.2105.10053. |
| [6] |
DONG Jun, LIU Dongran, DOU Xihao, et al. Key Issues and Technical Applications in the Study of Power Markets as the System Adapts to the New Power System in China[J]. Sustainability, 2021, 13(23): 13409-13418.
doi: 10.3390/su132313409 URL |
| [7] | MENG Zijie, CAI Xinlei, ZHU Jinzhou, et al. Study on the Influence of Extreme Weather on Power Grid Operation under New Power System[C]// ACM. 2021 4th International Conference on Algorithms. Engineering. New York: ACM, 2021: 1-6. |
| [8] | YOON K. Convolutional Neural Networks for Sentence Classification[EB/OL]. (2020-08-23)[2022-08-26]. https://arxiv.org/abs/1408.5882. |
| [9] |
LIU Pengfei, QIU Xipeng, HUANG Xuanjing. Recurrent Neural Network for Text Classification with Multi-Task Learning[EB/OL]. (2016-05-17)[2022-08-21]. https://doi.org/10.48550/arXiv.1605.05101.
doi: https://doi.org/10.48550/arXiv.1605.05101 |
| [10] | PAN Yafeng, ZHOU Tianyang, ZHU Junhu, et al. Construction of APT Attack Semantic Rules Based on ATT&CK[J]. Journal of Cyber Security, 2021, 6(3): 77-90. |
| 潘亚峰, 周天阳, 朱俊虎, 等. 基于ATT&CK的APT攻击语义规则构建[J]. 信息安全学报, 2021, 6(3):77-90. | |
| [11] | MILAJERDI S M, GJOMEMO R, ESHETE B, et al. HOLMES: Real-Time APT Detection Through Correlation of Suspicious Information Flows[C]// IEEE. 2019 IEEE Symposium on Security and Privacy, New York: IEEE, 2019: 1137-1152. |
| [12] |
TOUNSI W, RAIS H. A Survey on Technical Threat Intelligence in the Age of Sophisticated Cyber Attacks[J]. Computers & Security, 2018, 72: 212-233.
doi: 10.1016/j.cose.2017.09.001 URL |
| [13] | DAISUKE M. MITRE ATT&CK Based Evaluation on In-Network Deception Technology for Modernized Electrical Substation Systems[J]. Sustainability, 14(3): 1256-1264. |
| [14] |
XIONG Wenjun, LEGRAND E, ABERG O, et al. Cyber Security Threat Modeling Based on the MITRE Enterprise ATT&CK Matrix[J]. Software and Systems Modeling, 2021, 21: 157-177.
doi: 10.1007/s10270-021-00898-7 URL |
| [15] |
KIM Kyoungmin, SHIN Y, LEE Justin, et al. Automatically Attributing Mobile Threat Actors by Vectorized ATT&CK Matrix and Paired Indicator[J]. Sensors, 2021, 21(19): 6522-6532.
doi: 10.3390/s21196522 URL |
| [16] |
GEORGIADOU A, MOUZAKITIS S, ASKOUNIS D. Assessing MITRE ATT&CK Risk Using a Cyber-Security Culture Framework[J]. Sensors, 2021, 21(9): 3267-3278.
doi: 10.3390/s21093267 URL |
| [17] | BENITEZANDRADES J A, ALIJA-PEREZ J, VIDAL M, et al. Traditional Machine Learning Models and Bidirectional Encoder Representations From Transformer (BERT)-Based Automatic Classi-Fication of Tweets About Eating Disorders: Algorithm Development and Validation Study[J]. JMIR Medical Informatics, 2022, 10(2): 34492-34503. |
| [18] | LI Jing, ZHANG Dezheng, WULAMU Aziguli. Chinese Text Classification Based on ERNIE-RNN[C]// IEEE. 2021 2nd International Conference on Electronics. New York: IEEE, 2021: 368-372. |
| [19] |
LIU Shuaiqi, CAO Jiannong, YANG Ruosong, et al. Key Phrase Aware Transformer for Abstractive Summarization[J]. Information Processing and Management, 2022, 59(3): 102913-102923.
doi: 10.1016/j.ipm.2022.102913 URL |
| [20] |
LI Hongwei, MAO Hongyan, WANG Jingzi. Part-of-Speech Tagging with Rule-Based Data Preprocessing and Transformer[J]. Electronics, 2021, 11(1): 56-66.
doi: 10.3390/electronics11010056 URL |
| [1] | 周枝凝, 王斌君, 翟一鸣, 仝鑫. 基于ALBERT动态词向量的垃圾邮件过滤模型[J]. 信息网络安全, 2020, 20(9): 107-111. |
| [2] | 陈瑞滢, 陈泽茂, 王浩. 基于攻击图的工控网络威胁建模研究[J]. 信息网络安全, 2018, 18(10): 70-77. |
| [3] | 张家伟, 张冬梅, 黄偲琪. 一种抗APT攻击的可信软件基设计与实现[J]. 信息网络安全, 2017, 17(6): 49-55. |
| [4] | 程三军, 王宇. APT攻击原理及防护技术分析[J]. 信息网络安全, 2016, 16(9): 118-123. |
| [5] | 谈诚, 邓入弋, 王丽娜, 马婧. 针对APT攻击中恶意USB存储设备的防护方案研究[J]. 信息网络安全, 2016, 16(2): 7-8. |
| [6] | 李凤海, 李爽, 张佰龙, 宋衍. 高等级安全网络抗APT攻击方案研究[J]. 信息网络安全, 2014, 14(9): 109-114. |
| [7] | 翟立东;李跃;贾召鹏;郭莉. 融合网络空间的APT威胁检测与防护[J]. , 2013, 13(3): 0-0. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 161
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 384
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||