信息网络安全 ›› 2016, Vol. 16 ›› Issue (9): 118-123.doi: 10.3969/j.issn.1671-1122.2016.09.024
APT攻击原理及防护技术分析
- 河南省人民检察院,河南郑州 450004
Analysis of APT Attack Principle and Protection Technology
- People's Procuratorate of Henan Province, Zhengzhou Henan 450004, China
摘要:
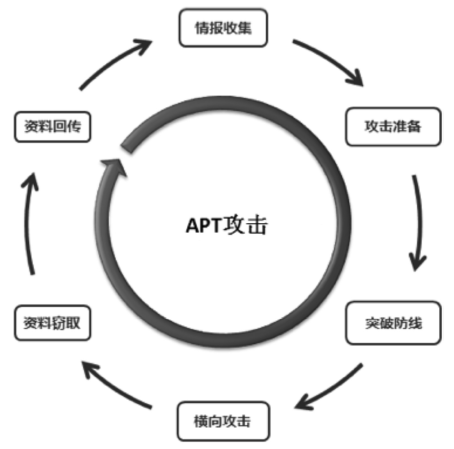
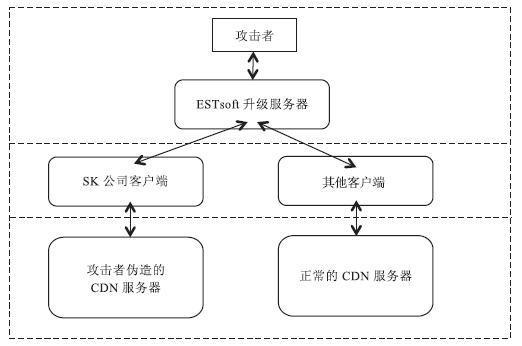
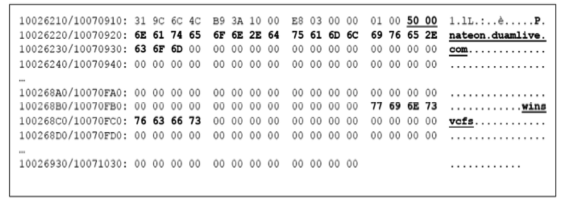
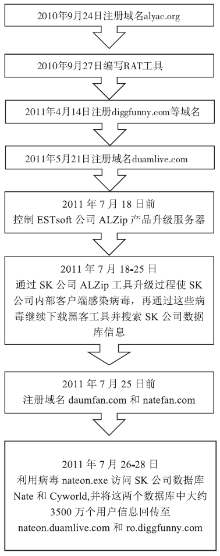
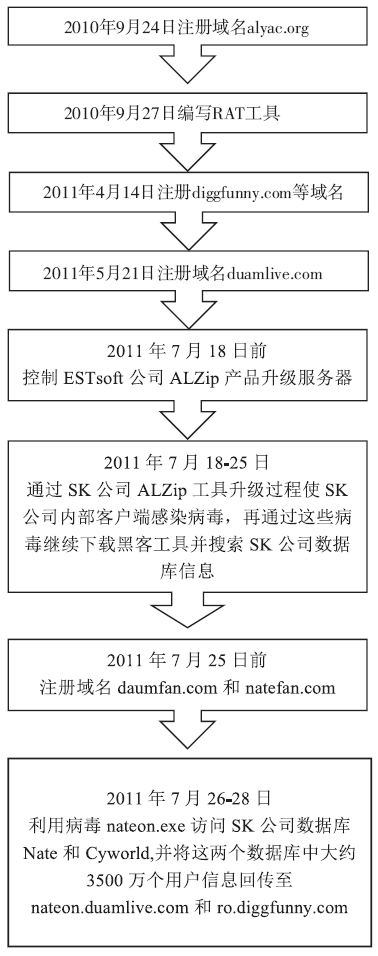
全球信息技术的不断演变,使得APT攻击更具有侵略性和目的性。先进的技术应用、长期的潜伏隐匿、获利方的资助,是APT攻击与其他网络攻击的显著区别。文章介绍了近年流行的APT攻击,首先以NIST对于APT攻击的定义说明APT攻击的特点,并指明攻击者通常使用APT攻击的目标,分析近年APT攻击的实例;然后又详细分析了APT攻击的常见步骤,并以韩国SK公司遭受APT攻击的案件为实例说明了各个步骤的攻击内容;进而提出全面应对APT攻击的宏观持续性改进的防护思想及微观的结构化最佳实践应对方法。
中图分类号: