信息网络安全 ›› 2021, Vol. 21 ›› Issue (12): 1-8.doi: 10.3969/j.issn.1671-1122.2021.12.001
• 入选论文 • 下一篇
基于HMM的Domain-Flux恶意域名检测及分析
郭向民1,2,3, 梁广俊1,2,3( ), 夏玲玲1,2,3
), 夏玲玲1,2,3
- 1.江苏警官学院计算机信息与网络安全系,南京 210031
2.江苏省电子数据取证分析工程研究中心,南京 210031
3.江苏省公安厅数字取证重点实验室,南京 210031
-
收稿日期:2021-08-28出版日期:2021-12-10发布日期:2022-01-11 -
通讯作者:梁广俊 E-mail:liangguangjun@jspi.cn -
作者简介:郭向民(1989—),男,讲师,硕士,主要研究方向为网络空间安全、电子数据取证|梁广俊(1983—),男,讲师,博士,主要研究方向为物联网取证、电子数据取证|夏玲玲(1988—),女,讲师,博士,主要研究方向为网络空间安全、社交网络分析 -
基金资助:国家自然科学基金(61802155);江苏省高等学校自然科学基金(21KJD520003);江苏省公安厅科技研究项目(2020KX008);国家地方联合工程实验室开放课题(KFJJ20200201);江苏警官学院教育教学改革研究项目(2020A05)
Domain-Flux Malicious Domain Name Detection and Analysis Based on HMM
GUO Xiangmin1,2,3, LIANG Guangjun1,2,3( ), XIA Lingling1,2,3
), XIA Lingling1,2,3
- 1. Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
2. Jiangsu Electronic Data Forensics and Analysis Engineering Research Center, Nanjing 210031, China
3. Jiangsu Provincial Public Security Department Key Laboratory of Digital Forensics, Nanjing 210031, China
-
Received:2021-08-28Online:2021-12-10Published:2022-01-11 -
Contact:LIANG Guangjun E-mail:liangguangjun@jspi.cn
摘要:
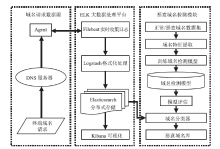
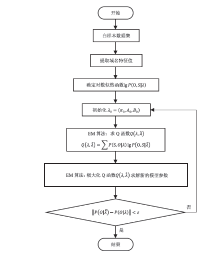
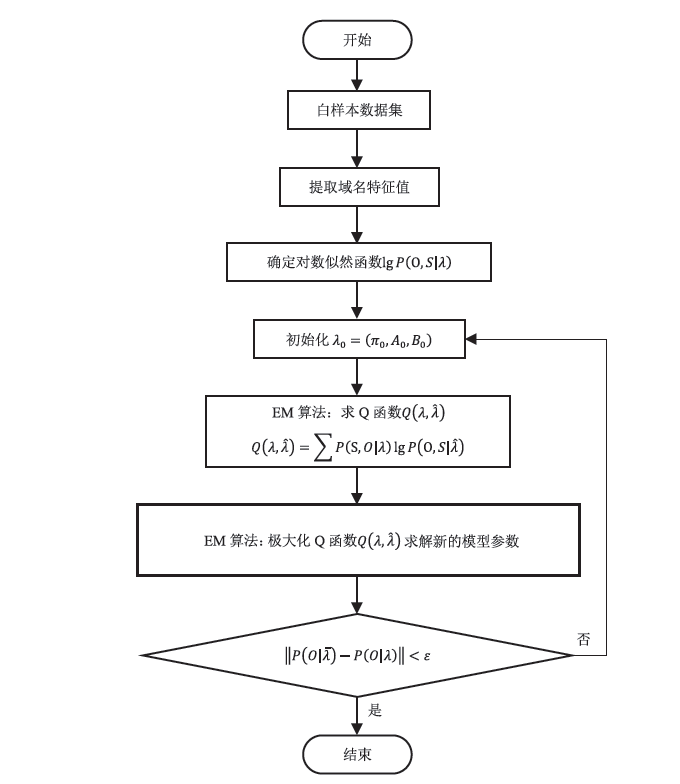
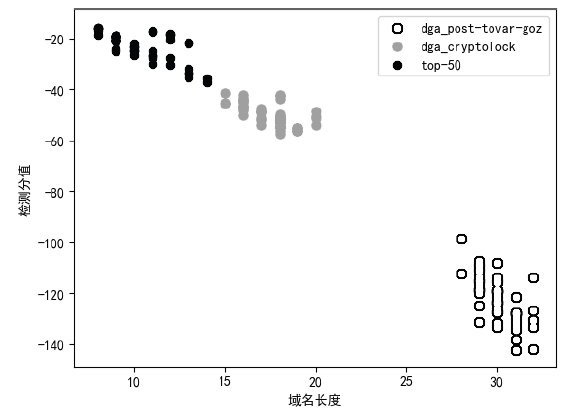
目前,僵尸网络广泛采用域名生成算法(Domain Generation Algorithm,DGA)生成大量随机域名躲避检测,这种躲避检测的方法已经成为破坏网络安全的主要威胁。因此,研究DGA域名识别方法对于检测恶意程序、打击僵尸网络、保障信息安全具有重要的现实意义。文章设计了基于ELK大数据平台的DGA域名检测分析框架,在充分研究黑名单等现有DGA域名识别方法的基础上,收集域名解析(Domain Name Server,DNS)业务系统的请求查询日志,以DGA域名为识别对象,基于隐式马尔可夫模型(Hidden Markov Model,HMM)对恶意域名进行聚类分析,从而实现对DGA域名的判定,进一步为僵尸网络等网络攻击行为的取证、溯源提供思路。实验结果表明,文章采用的轻量级检测分类器对正常域名和恶意域名的区分效果较好。
中图分类号:
引用本文
郭向民, 梁广俊, 夏玲玲. 基于HMM的Domain-Flux恶意域名检测及分析[J]. 信息网络安全, 2021, 21(12): 1-8.
GUO Xiangmin, LIANG Guangjun, XIA Lingling. Domain-Flux Malicious Domain Name Detection and Analysis Based on HMM[J]. Netinfo Security, 2021, 21(12): 1-8.
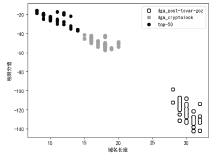
表1
正常域名和DGA家族域名的长度对比
| 正常域名 (长度) | crytolocker中域名 (长度) | post-tovar-goz中域名 (长度) |
|---|---|---|
| google.com (9) | wwkahhnyqvxdfq.com(17) | 1vw732fl1xtlak0d9gcdqts1.com(27) |
| youtube.com(10) | kpudegrfqeuadh.net (17) | 1hhxat2jy9ifweb2yvdkxcoo1.net(28) |
| facebook.com(11) | xraxhxvadmpgdn.biz(17) | fnh1oolf37hjgasfma1p40f80.biz(28) |
| baidu.com (8) | ldjhqijygqrudp.ru (16) | y4vv24qb5q13q9m9y115hf8cp.org(28) |
| wikipedia.org(12) | yfoctantsymbmt.org (17) | 17ag7la1cpqv96x4kc210zbouf.com(29) |
| [1] | XU Guotian. Crack of Malicious Program Domain Name Generation Algorithm Based on DGA[J]. Netinfo Security, 2017, 17(9):4-8. |
| 徐国天. 基于DGA的恶意程序域名生成算法破解[J]. 信息网络安全, 2017, 17(9):4-8. | |
| [2] | McAfee Labs. Threats Report[EB/OL]. https://www.mcafee.com/enterprise/zh-cn/assets/reports/rp-quarterly-threats-nov-2020.pdf, 2020-11-13. |
| [3] | ACARALIA D, RAJARAJANA M, KOMNINOSA N, et al. Survey of Approaches and Features for the Identification of HTTP-based Botnet Traffic[J]. Journal of Network and Computer Applications, 2016, 16(76):1-15. |
| [4] | ZHAUNIAROVICH Y, KHALIL I, YU Ting, et al. A Survey on Malicious Domains Detection Through DNS Data Analysis[J]. ACM Computing Surveys, 2018, 51(4):1-35. |
| [5] | ZANG Xiaodong, GONG Jian, HU Xiaoyan. Malicious Domain Name Detection Based on AGD[J]. Journal on Communications, 2018, 39(7):15-25. |
| 臧小东, 龚俭, 胡晓艳. 基于AGD的恶意域名检测[J]. 通信学报, 2018, 39(7):15-25. | |
| [6] | JIN Jiandong, YANG Jia, ZHOU Changling, et al. Network Forensics Analysis on Email Scam Botnet[J]. Journal of Shenzhen University(Science & Engineering), 2020, 37(z1):78-83. |
| 金建栋, 杨加, 周昌令, 等. 勒索欺诈邮件僵尸网络的检测与分析[J]. 深圳大学学报理工版, 2020, 37(z1):78-83. | |
| [7] | THAPLIYAL M, BIJALWAN A, GARG N, et al. A Generic Process Model for Botnet Forensic Analysis[EB/OL]. https://www.atlantis-press.com/proceedings/cac2s-13/6285, 2013-04-24. |
| [8] | ANTONAKAKIS M, PERDISCI R, NADJI Y, et al. From Throw-away Traffic to Bots: Detecting the Rise of DGA-based Malware[EB/OL]. https://dl.acm.org/doi/10.5555/2362793.2362817, 2012-08-10. |
| [9] |
SHARIFNYA R, ABADI M. DFBotKiller: Domain-flux Botnet Detection Basedon the History of Group Activities and Failures in DNS Traffic[J]. Digital Investigation, 2015, 13(12):15-26.
doi: 10.1016/j.diin.2015.02.002 URL |
| [10] | ZHAO Yue. Research on Botnet Detection Method Based on DNS Traffic Characteristics[D]. Tianjin: Tianjin University, 2016. |
| 赵越. 基于DNS流量特征的僵尸网络检测方法研究[D]. 天津:天津大学, 2016. | |
| [11] | WAJEEHA A. Why Botnets Persist: Designing Effective Technical and Policy Interventions[J]. MIT Internet Policy Research Initiative (IPRI), 2019, 23(2):1-5. |
| [12] | XIONG Yan, CHENG Chuanhu, WU Jianshuang, et al. Research on Premise Selection Technology Based on Machine Learning Classification Algorithm[J]. Netinfo Security, 2021, 21(11):9-16. |
| 熊焰, 程传虎, 武建双, 等. 基于机器学习分类算法的前提选择技术研究[J]. 信息网络安全, 2021, 21(11):9-16. | |
| [13] | LI Deqi, HU Dasha, LIU Yunxia, et al. Research on Command Control Channel of Botnet Based on Blockchain Technology[J]. Modern Computer, 2020, 49(8):30-36. |
| 李德奇, 胡大裟, 刘云霞, 等. 基于区块链技术的僵尸网络命令控制信道研究[J]. 现代计算机, 2020, 49(8):30-36. | |
| [14] | LIU Yi, CAO Jianjun, DIAO Xingchun, et al. Review on Stability of Feature Selection[J]. Journal of Software, 2018, 29(9):2559-2579. |
| 刘艺, 曹建军, 刁兴春, 等. 特征选择稳定性研究综述[J]. 软件学报, 2018, 29(9):2559-2579. | |
| [15] |
ZHANG Xiao, MEI Changlin, CHEN Degang, et al. Feature Selection in Mixed Data: A Method Using A Novel Fuzzy Rough Set-based Information Entropy[J]. Pattern Recognition, 2016, 56(1):1-15.
doi: 10.1016/j.patcog.2016.02.013 URL |
| [16] | ZHAO Cheng, CHEN Junxin. Reflective XSS Detection Technology Based on Hidden Markov Model[J]. Journal of Zhejiang University of Technology, 2019, 47(4):6-12. |
| 赵澄, 陈君新. 基于隐马尔可夫模型的反射型XSS检测技术[J]. 浙江工业大学学报, 2019, 47(4):6-12. | |
| [17] | ZHANG Xiao, YING Shi, ZHANG Tao. Collection and Service Processing Framework of Application Software Running Log[J]. Computer Engineering and Applications, 2018, 54(10):81-89, 142. |
| 张骁, 应时, 张韬. 应用软件运行日志的收集与服务处理框架[J]. 计算机工程与应用, 2018, 54(10):81-89, 142. | |
| [18] | JIANG Hongling, DAI Junwei. DGA Malicious Domain Name Detection Method[J]. Journal of Beijing Institute of Machinery (Natural Science Edition), 2019, 34(5):6-22. |
| 蒋鸿玲, 戴俊伟. DGA恶意域名检测方法[J]. 北京信息科技大学学报(自然科学版), 2019, 34(5):6-22. |
| [1] | 郭烜臻, 潘祖烈, 沈毅, 陈远超. 一种基于被动DNS数据分析的DNS重绑定攻击检测技术[J]. 信息网络安全, 2021, 21(3): 87-95. |
| [2] | 罗峥, 张学谦. 基于思维进化算法优化S-Kohonen神经网络的恶意域名检测模型[J]. 信息网络安全, 2020, 20(6): 82-89. |
| [3] | 刘敏, 陈曙晖. 基于关联融合的VoLTE流量分析研究[J]. 信息网络安全, 2020, 20(4): 81-86. |
| [4] | 杨新宇, 王健. 对微云的网络取证研究[J]. 信息网络安全, 2015, 15(3): 69-73. |
| [5] | 刘平;陈琳. 基于入侵容忍的电子证据保护机制设计与实现[J]. , 2013, 13(10): 0-0. |
| [6] | 梅锋;孙东滨. IPv6环境下网络取证研究[J]. , 2012, 12(11): 0-0. |
| [7] | 丁丽萍. 网络取证及计算机取证的理论研究[J]. , 2010, (12): 0-0. |
| [8] | 王纲. 侦破网络销售假冒商品案之思考[J]. , 2009, 9(11): 0-0. |
| [9] | 段玲;王锋. 网络取证技术研究[J]. , 2009, 9(11): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||