信息网络安全 ›› 2021, Vol. 21 ›› Issue (11): 85-94.doi: 10.3969/j.issn.1671-1122.2021.11.010
基于TCN和注意力机制的异常检测和定位算法
- 1.华东师范大学数据科学与工程学院,上海 200062
2.同济大学计算机科学与技术系,上海 201804
-
收稿日期:2020-05-06出版日期:2021-11-10发布日期:2021-11-24 -
通讯作者:王伟 E-mail:wwang@dase.ecnu.edu.cn -
作者简介:吴佳洁(1996—),女,浙江,硕士研究生,主要研究方向为异常检测|吴绍岭(1994—),男,山东,硕士研究生,主要研究方向为容器虚拟化技术|王伟(1979—),男,湖北,研究员,博士,主要研究方向为开源系统论、复杂信息网络 -
基金资助:国家自然科学基金(61672384)
An Anomaly Detection and Location Algorithm Based on TCN and Attention Mechanism
WU Jiajie1, WU Shaoling2, WANG Wei1( )
)
- 1. School of Data Science and Engineering, East China Normal University, Shanghai 200062, China
2. Department of Computer Science and Technology, Tongji University, Shanghai 201804, China
-
Received:2020-05-06Online:2021-11-10Published:2021-11-24 -
Contact:WANG Wei E-mail:wwang@dase.ecnu.edu.cn
摘要:
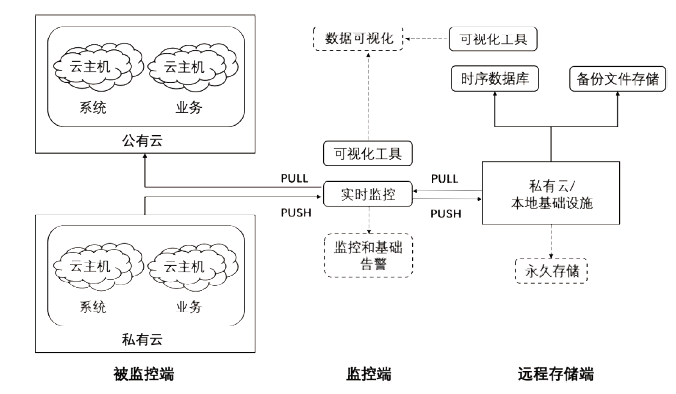
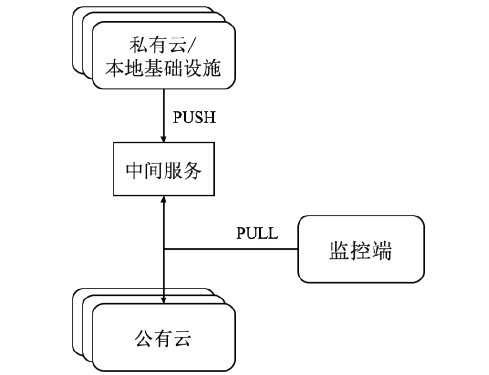
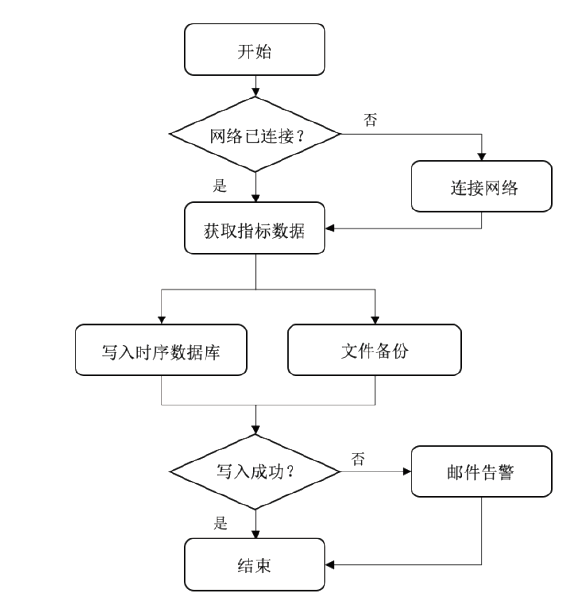
随着云计算时代的到来,应用上云已经成为主流的系统部署方案。为了满足业务需求,很多系统都在混合云环境采用微服务架构。系统本身的复杂性和运行环境的复杂性使得实时监控和运维数据处理、异常检测及定位都变得困难。文章设计了一个面向复杂云系统的实时监控和数据处理框架,同时提出了一种基于TCN和注意力机制的异常检测算法(TCN-AT)。前者可在复杂云环境的微服务系统中运行,后者用于时间序列数据中的点异常和窗口异常检测。文章在仿真数据、真实的微服务系统数据和开源的比赛数据上进行了大量实验,结果表明TCN-AT的性能优于其他前沿算法。
中图分类号:
引用本文
吴佳洁, 吴绍岭, 王伟. 基于TCN和注意力机制的异常检测和定位算法[J]. 信息网络安全, 2021, 21(11): 85-94.
WU Jiajie, WU Shaoling, WANG Wei. An Anomaly Detection and Location Algorithm Based on TCN and Attention Mechanism[J]. Netinfo Security, 2021, 21(11): 85-94.
| [1] | DRAGONI N, GIALLORENZO S, LAFUENTE A L, et al. Present and Ulterior Software Engineering || Microservices: Yesterday, Today, and Tomorrow[M]. Berlin: Springer-Verlag, 2017. |
| [2] | LI Chunxia. Overview of Microservice Architecture Research[J]. Software Guide, 2019, 18(8):1-3, 7. |
| 李春霞. 微服务架构研究概述[J]. 软件导刊, 2019, 18(8):1-3,7. | |
| [3] | TANG Zhitao, LIU Xing. Evolution of Enterprise Application System Architecture[EB/OL]. https://www.cnki.com.cn/Article/CJFDTOTAL-CXYY201735067.htm, 2021-02-27. |
| 唐志涛, 刘星. 企业应用系统架构演进[EB/OL]. https://www.cnki.com.cn/Article/CJFDTOTAL-CXYY201735067.htm, 2021-02-27. | |
| [4] | ZHANG Shifeng, PAN Shanliang. Application of Docker Technology in Microservices[J]. Electronic Technology and Software Engineering, 2019, 19(4):164. |
| 章仕锋, 潘善亮. Docker技术在微服务中的应用[J]. 电子技术与软件工程, 2019, 19(4):164. | |
| [5] | KHAZAEI H, BARNA C, BEIGI-MOHAMMADI N, et al. Efficiency Analysis of Provisioning Microservices[C]// IEEE. 2016 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), December 12-15, 2016, Piscataway, USA. New York: IEEE, 2016: 261-268. |
| [6] | FAN Yamin, FU Jian. The Way of Microservices: Metric Driven Development[M]. Beijing: China Machine Press, 2020. |
| 范亚敏, 傅健. 微服务之道:度量驱动开发[M]. 北京: 机械工业出版社, 2020. | |
| [7] | BLOHOWIAK A, BASIRI A. A Platform for Automating Chaos Experiments[C]// IEEE. 2016 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), October 23-27, 2016, Ottawa, Ontario, Canada. Piscataway: IEEE, 2016: 5-8. |
| [8] | SHYU Meiling, CHEN Shuching, SARINNAPAKORN K, et al. A Novel Anomaly Detection Scheme Based on Principal Component Classifier[C]// IEEE. Proceedings of the IEEE Foundations and New Directions of Data Mining Workshop, in Conjunction with the Third IEEE International Conference on Data Mining (ICDM03), November 19-22, 2003, Melbourne, Florida. USA. New York: IEEE, 2003: 172-179. |
| [9] | LIU Fei, TING Kaiming, ZHOU Zhihua, et al. Isolation Forest[C]// IEEE. 2008 Eighth IEEE International Conference on Data Mining, December 15-19, 2008, Washington, USA. New York: IEEE, 2008: 413-422. |
| [10] | ZONG Bo, SONG Qi, MIN M R, et al. Deep Autoencoding Gaussian Mixture Model for Unsupervised Anomaly Detection[C]// ICLR. International Conference on Learning Representations 2018, April 30-May 3, 2018, Vancouver, BC, Canada. USA: ICLR, 2018: 1-19. |
| [11] |
ZHANG Chuxu, SONG Dongjin, CHEN Yuncong, et al. A Deep Neural Network for Unsupervised Anomaly Detection and Diagnosis in Multivariate Time Series Data[J]. Proceedings of the AAAI Conference on Artificial Intelligence, 2019, 33(1):1409-1416.
doi: 10.1609/aaai.v33i01.33011409 URL |
| [12] | MALHOTRA P, RAMAKRISHNAN A, ANAND G, et al. LSTM-based Encoder-decoder for Multi-sensor Anomaly Detection[EB/OL]. https://arxiv.org/pdf/1607.00148.pdf, 2021-01-19. |
| [13] |
HE Yangdong, ZHAO Jiabao. Temporal Convolutional Networks for Anomaly Detection in Time Series[J]. Journal of Physics: Conference Series, 2019, 1213(4):42050.
doi: 10.1088/1742-6596/1213/4/042050 URL |
| [14] | MUNIR M, SIDDIQUI S A, DENGEL A, et al. DeepAnT: A Deep Learning Approach for Unsupervised Anomaly Detection in Time Series[J]. IEEE Access, 2019, 19(7):1991-2005. |
| [15] | LAPTEV N, AMIZADEH S, FLINT I, et al. Generic and Scalable Framework for Automated Time-series Anomaly Detection[C]// ACM. Proceedings of the 21th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 10-13, 2015, Sydney, NSW, Australia. New York: IEEE, 2015: 1939-1947. |
| [16] | Etsy. Skyline: It’ll Detect Your Anomalies[EB/OL]. https://github.com/etsy/skyline, 2021-01-15. |
| [17] | Netflix. Surus: A Collection of Tools for Analysis in Pig and Hive[EB/OL] https://github.com/netflix/surus, 2021-02-22. |
| [18] | XU Haowen, CHEN Wenxiao, ZHAO Nengwen, et al. Unsupervised Anomaly Detection via Variational Auto-encoder for Seasonal KPIs in Web Applications[C]// ACM. WWW 2018: International World Wide Web Conferences, April 23-27, 2018, Lyon, France. New York: ACM, 2018: 187-196. |
| [19] | LIU Dapeng, ZHAO Youjian, XU Haowen, et al. Opprentice: Towards Practical and Automatic Anomaly Detection Through Machine Learning[C]// ACM. Proceedings of the 2015 Internet Measurement Conference On, October 28-30, 2015, Tokyo, Japan. New York: ACM, 2015: 211-224. |
| [20] | BAI S, KOLTER Z, KOLTUN V, et al. An Empirical Evaluation of Generic Convolutional and Recurrent Networks for Sequence Modeling[EB/OL]. export.arxiv.org/pdf/1803.01271, 2021-01-16. |
| [21] | LUONG M T, PHAM H, MANNING C D, et al. Effective Approaches to Attention-based Neural Machine Translation[C]// ACL. Proceedings of the 2015 Conference on Empirical Methods in Natural Language Processing, September 17-18, 2015, Lisbon, Portugal. Stroudsbrug, Pennsylvania: ACL, 2015: 1412-1421. |
| [22] | CLEVELAND R B. STL: A Seasonal-trend Decomposition Procedure Based on Loess[J]. Journal of Office Statistics, 1990, 6(1):3-7. |
| [23] | TAYLOR S, LETHAM B. Forecasting at Scale[J]. The American Statistician, 2018, 7(1):37-45. |
| [24] |
HOCHREITER S, SCHMIDHUBER J. Long Short-term Memory[J]. Neural Computation, 1997, 9(8):1735-1780.
doi: 10.1162/neco.1997.9.8.1735 URL |
| [1] | 秦中元, 胡宁, 方兰婷. 基于免疫仿生机理和图神经网络的网络异常检测方法[J]. 信息网络安全, 2021, 21(8): 10-16. |
| [2] | 徐洪平, 马泽文, 易航, 张龙飞. 基于卷积循环神经网络的网络流量异常检测技术[J]. 信息网络安全, 2021, 21(7): 54-62. |
| [3] | 吴驰, 帅俊岚, 龙涛, 于俊清. 基于Linux Shell命令的用户异常操作检测方法研究[J]. 信息网络安全, 2021, 21(5): 31-38. |
| [4] | 李佳玮, 吴克河, 张波. 基于高斯混合聚类的电力工控系统异常检测研究[J]. 信息网络安全, 2021, 21(3): 53-63. |
| [5] | 陆佳丽. 基于改进时间序列模型的日志异常检测方法[J]. 信息网络安全, 2020, 20(9): 1-5. |
| [6] | 黄娜, 何泾沙, 吴亚飚, 李建国. 基于LSTM回归模型的内部威胁检测方法[J]. 信息网络安全, 2020, 20(9): 17-21. |
| [7] | 顾兆军, 任怡彤, 刘春波, 王志. 基于一致性预测算法的内网日志检测模型[J]. 信息网络安全, 2020, 20(3): 45-50. |
| [8] | 王玉娣, 刘晓洁, 王运鹏. 基于改进否定选择算法的异常检测方法研究[J]. 信息网络安全, 2020, 20(10): 75-82. |
| [9] | 王伟, 沈旭东. 基于实例的迁移时间序列异常检测算法研究[J]. 信息网络安全, 2019, 19(3): 11-18. |
| [10] | 杨威超, 郭渊博, 钟雅, 甄帅辉. 基于设备型号分类和BP神经网络的物联网流量异常检测[J]. 信息网络安全, 2019, 19(12): 53-63. |
| [11] | 朱海麒, 姜峰. 人工智能时代面向运维数据的异常检测技术研究与分析[J]. 信息网络安全, 2019, 19(11): 24-35. |
| [12] | 邓海莲, 刘宇靖, 葛一漩, 苏金树. 域间路由异常检测技术研究[J]. 信息网络安全, 2019, 19(11): 63-70. |
| [13] | 李巍, 狄晓晓, 王迪, 李云春. 基于子图的服务器网络行为建模及异常检测方法研究[J]. 信息网络安全, 2018, 18(2): 1-9. |
| [14] | 何利, 姚元辉. 基于上下文聚类的云虚拟机异常检测与识别策略[J]. 信息网络安全, 2018, 18(12): 54-65. |
| [15] | 赵刚, 姚兴仁. 基于用户画像的异常行为检测模型[J]. 信息网络安全, 2017, 17(7): 18-24. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||