信息网络安全 ›› 2021, Vol. 21 ›› Issue (1): 10-18.doi: 10.3969/j.issn.1671-1122.2021.01.002
基于TD-ERCS序列的S盒非线性度优化算法
- 1.西安邮电大学网络空间安全学院,西安 710121
2.国家计算机网络应急技术处理协调中心,北京 100029
-
收稿日期:2020-08-19出版日期:2021-01-10发布日期:2021-02-23 -
通讯作者:卫凯莉 E-mail:2863045812@qq.com -
作者简介:张雪锋(1975—),男,陕西,教授,博士,主要研究方向为信息安全、图像加密和生物识别|卫凯莉(1996—),女,山西,硕士研究生,主要研究方向为分组密码算法和图像加密|姜文(1983—),男,安徽,高级工程师,博士,主要研究方向为信息安全和工业互联网安全 -
基金资助:陕西省自然科学基础研究计划(2017JQ6010);陕西省教育厅专项科学研究计划(18JK0717)
The Nonlinearity Optimization Algorithm of S-box Based on TD-ERCS Sequence
ZHANG Xuefeng1, WEI Kaili1( ), JIANG Wen2
), JIANG Wen2
- 1. College of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China;
2. National Internet Emergency Center, Beijing 100029, China
-
Received:2020-08-19Online:2021-01-10Published:2021-02-23 -
Contact:WEI Kaili E-mail:2863045812@qq.com
摘要:
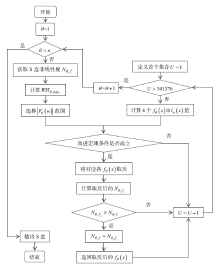
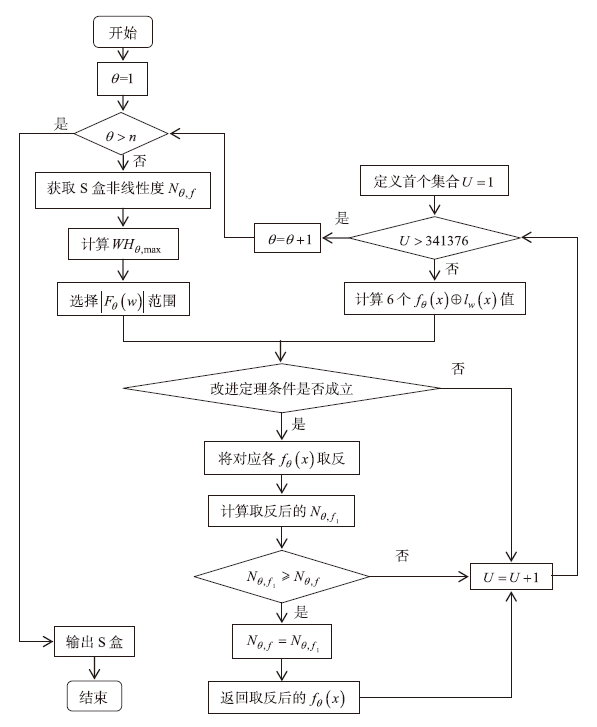
针对基于混沌系统生成的S盒存在非线性度较低等问题,文章针对基于切延迟椭圆反射腔映射系统(TD-ERCS)生成S盒的方法,首先证明了生成的S盒具有双射性,在此基础上,设计了一种改进的爬山算法,通过动态缩小布尔函数Walsh-Hadamard变换(WHT)的选取范围,将满足条件的6个布尔值进行取反运算,有效提升了双射S盒非线性度。理论和实验仿真分析表明,采用优化算法生成的S盒性能得到了有效提升,在算法效率、非线性度、严格雪崩准则和差分逼近概率等方面具备更好的性能。
中图分类号:
引用本文
张雪锋, 卫凯莉, 姜文. 基于TD-ERCS序列的S盒非线性度优化算法[J]. 信息网络安全, 2021, 21(1): 10-18.
ZHANG Xuefeng, WEI Kaili, JIANG Wen. The Nonlinearity Optimization Algorithm of S-box Based on TD-ERCS Sequence[J]. Netinfo Security, 2021, 21(1): 10-18.
表1
第三个布尔函数的产生过程
| 混沌值取值范围 | ${{\chi }_{{g}/{{{2}^{3}}}\;}}\left( X \right)$取值 | d3(X )取值 |
|---|---|---|
| $0\le \left| X \right|<{1}/{8}\;$ | 0 0 0 0 0 0 0 | 0 |
| ${1}/{8}\;\le \left| X \right|<{2}/{8}\;$ | 1 0 0 0 0 0 0 | 1 |
| ${2}/{8}\;\le \left| X \right|<{3}/{8}\;$ | 1 1 0 0 0 0 0 | 0 |
| ${3}/{8}\;\le \left| X \right|<{4}/{8}\;$ | 1 1 1 0 0 0 0 | 1 |
| ${4}/{8}\;\le \left| X \right|<{5}/{8}\;$ | 1 1 1 1 0 0 0 | 0 |
| ${5}/{8}\;\le \left| X \right|<{6}/{8}\;$ | 1 1 1 1 1 0 0 | 1 |
| ${6}/{8}\;\le \left| X \right|<{7}/{8}\;$ | 1 1 1 1 1 1 0 | 0 |
| ${7}/{8}\;\le \left| X \right|\le 1$ | 1 1 1 1 1 1 1 | 1 |
表3
优化后的S盒
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 195 | 230 | 252 | 255 | 222 | 193 | 2 | 141 | 198 | 26 | 132 | 117 | 61 | 199 | 6 | 10 |
| 1 | 112 | 184 | 82 | 244 | 170 | 5 | 145 | 73 | 236 | 237 | 93 | 163 | 54 | 121 | 97 | 12 |
| 2 | 20 | 78 | 226 | 247 | 188 | 233 | 67 | 126 | 164 | 214 | 116 | 25 | 196 | 246 | 18 | 43 |
| 3 | 95 | 229 | 177 | 189 | 28 | 192 | 32 | 46 | 88 | 106 | 90 | 45 | 21 | 31 | 62 | 72 |
| 4 | 225 | 115 | 100 | 42 | 108 | 186 | 178 | 234 | 59 | 220 | 200 | 148 | 134 | 65 | 161 | 130 |
| 5 | 86 | 11 | 165 | 238 | 150 | 50 | 210 | 219 | 51 | 187 | 48 | 181 | 75 | 1 | 190 | 99 |
| 6 | 153 | 172 | 251 | 80 | 92 | 84 | 212 | 30 | 13 | 221 | 142 | 201 | 152 | 91 | 89 | 71 |
| 7 | 232 | 47 | 211 | 179 | 135 | 197 | 175 | 182 | 156 | 125 | 129 | 9 | 29 | 41 | 64 | 63 |
| 8 | 228 | 103 | 127 | 107 | 120 | 171 | 34 | 44 | 105 | 102 | 96 | 57 | 242 | 58 | 85 | 94 |
| 9 | 70 | 224 | 215 | 208 | 217 | 7 | 14 | 131 | 119 | 144 | 60 | 138 | 37 | 19 | 174 | 40 |
| A | 239 | 69 | 33 | 203 | 206 | 194 | 216 | 39 | 167 | 22 | 111 | 24 | 169 | 76 | 35 | 56 |
| B | 253 | 241 | 87 | 250 | 77 | 159 | 139 | 147 | 151 | 223 | 66 | 101 | 204 | 68 | 23 | 231 |
| C | 136 | 173 | 122 | 243 | 207 | 162 | 0 | 16 | 160 | 191 | 185 | 118 | 79 | 183 | 15 | 3 |
| D | 245 | 218 | 254 | 227 | 104 | 249 | 157 | 166 | 36 | 149 | 158 | 205 | 154 | 53 | 49 | 113 |
| E | 168 | 133 | 137 | 83 | 202 | 4 | 114 | 110 | 140 | 124 | 176 | 248 | 27 | 81 | 55 | 180 |
| F | 143 | 209 | 38 | 240 | 213 | 17 | 123 | 155 | 235 | 52 | 146 | 128 | 98 | 8 | 109 | 74 |
表4
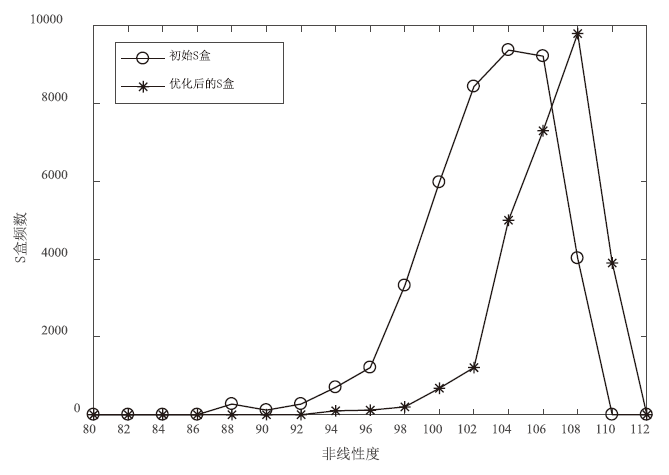
S盒非线性度对比
| S盒 | 非线性度 | 平均值 | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 初始S盒[ | 94 | 102 | 102 | 108 | 106 | 106 | 106 | 102 | 103.25 |
| 优化后 | 100 | 108 | 108 | 110 | 108 | 108 | 108 | 108 | 107.25 |
| 文献[ | 106 | 102 | 104 | 104 | 108 | 108 | 106 | 104 | 105.25 |
| 文献[ | 104 | 100 | 106 | 102 | 104 | 102 | 104 | 104 | 103.20 |
| 文献[ | 108 | 106 | 106 | 106 | 106 | 106 | 108 | 108 | 106.75 |
| 文献[ | 108 | 110 | 102 | 106 | 100 | 106 | 106 | 106 | 105.50 |
| 文献[ | 106 | 106 | 108 | 106 | 108 | 106 | 108 | 106 | 106.75 |
表5
优化S盒的依赖矩阵
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | |
|---|---|---|---|---|---|---|---|---|
| 0 | 0.4688 | 0.4688 | 0.5781 | 0.5156 | 0.4688 | 0.4531 | 0.4844 | 0.5313 |
| 1 | 0.4219 | 0.5156 | 0.5781 | 0.5000 | 0.5156 | 0.5469 | 0.5000 | 0.4531 |
| 2 | 0.5156 | 0.4531 | 0.5000 | 0.5000 | 0.5469 | 0.5000 | 0.5156 | 0.5000 |
| 3 | 0.4375 | 0.4844 | 0.5156 | 0.5000 | 0.4844 | 0.4219 | 0.5469 | 0.6094 |
| 4 | 0.4531 | 0.4844 | 0.3906 | 0.4531 | 0.5625 | 0.5313 | 0.5313 | 0.4844 |
| 5 | 0.4688 | 0.5156 | 0.4219 | 0.4844 | 0.5625 | 0.5156 | 0.5313 | 0.4844 |
| 6 | 0.4823 | 0.4748 | 0.4593 | 0.4593 | 0.4748 | 0.4966 | 0.4672 | 0.4966 |
| 7 | 0.5000 | 0.5000 | 0.4219 | 0.5781 | 0.5000 | 0.5156 | 0.4688 | 0.5156 |
表7
优化S盒的相关系数分布
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | |
|---|---|---|---|---|---|---|---|---|
| 0 | 0.0000 | -0.0361 | -0.0070 | -0.0038 | -0.0157 | -0.0150 | 0.0361 | 0.0212 |
| 1 | -0.0361 | 0.0000 | -0.0180 | 0.0938 | -0.0052 | 0.0159 | 0.0238 | -0.0385 |
| 2 | -0.0070 | -0.0180 | 0.0000 | 0.0098 | -0.0734 | -0.0251 | 0.0102 | -0.0520 |
| 3 | -0.0038 | 0.0938 | 0.0098 | 0.0000 | -0.0059 | -0.0039 | -0.0235 | -0.0274 |
| 4 | -0.0157 | -0.0052 | -0.0734 | -0.0059 | 0.0000 | 0.0092 | -0.0105 | -0.0306 |
| 5 | -0.0150 | 0.0159 | -0.0251 | -0.0039 | 0.0092 | 0.0000 | 0.0271 | 0.0035 |
| 6 | 0.0361 | 0.0238 | 0.0102 | -0.0235 | -0.0105 | 0.0271 | 0.0000 | 0.0307 |
| 7 | 0.0212 | -0.0385 | -0.0520 | -0.0274 | -0.0306 | 0.0035 | 0.0307 | 0.0000 |
表10
优化S盒的差分逼近分布
| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 6 | 6 | 8 | 10 | 6 | 6 | 10 | 6 | 6 | 6 | 6 | 8 | 10 | 8 | 6 | 10 |
| 1 | 8 | 6 | 6 | 8 | 6 | 10 | 8 | 6 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 8 |
| 2 | 8 | 6 | 6 | 6 | 6 | 8 | 6 | 8 | 8 | 6 | 8 | 6 | 6 | 6 | 8 | 6 |
| 3 | 6 | 6 | 8 | 8 | 8 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 10 | 6 | 6 | 6 |
| 4 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 8 | 6 | 8 | 8 | 6 | 10 | 8 | 8 | 6 |
| 5 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 6 | 10 | 8 | 6 |
| 6 | 6 | 6 | 8 | 10 | 6 | 6 | 8 | 8 | 6 | 8 | 8 | 6 | 6 | 6 | 8 | 8 |
| 7 | 6 | 6 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 8 | 6 | 6 | 10 | 6 |
| 8 | 6 | 6 | 8 | 8 | 6 | 6 | 8 | 8 | 6 | 6 | 6 | 6 | 8 | 8 | 6 | 6 |
| 9 | 8 | 6 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 10 | 6 | 6 | 8 | 6 |
| A | 6 | 6 | 8 | 6 | 6 | 6 | 10 | 6 | 4 | 6 | 6 | 6 | 6 | 8 | 8 | 6 |
| B | 6 | 6 | 6 | 6 | 6 | 8 | 8 | 8 | 8 | 6 | 6 | 6 | 8 | 8 | 6 | 8 |
| C | 6 | 8 | 8 | 8 | 6 | 6 | 8 | 8 | 8 | 8 | 6 | 6 | 6 | 6 | 6 | 8 |
| D | 6 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 8 | 8 | 8 | 8 | 6 |
| E | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 8 | 10 | 8 | 6 | 8 | 6 | 8 | 6 | 8 |
| F | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 6 | 8 | 6 | 8 | 6 | 8 | 6 | 6 |
| [1] |
AYESHA R, MAJID K. Construction of New S-boxes Based on Triangle Groups and Its Applications in Copyright Protection[J]. Multimedia Tools and Applications, 2019,78(6):15527-15544.
doi: 10.1007/s11042-018-6953-x URL |
| [2] | SELCUK K, SEVDENUR B. Results on Symmetric S-boxes Constructed by Concatenation of RSSBs[J]. Cryptography and Communications, 2019,11(7):641-660. |
| [3] | IMRAN S, QAISER M, ABDUL R. Construction of New S-box Using Action of Quotient of the Modular Group for Multimedia Security[J]. Security and Communication Networks, 2019,2019(11):1-13. |
| [4] | FIRAT A, FATIH Ö. A Novel Method for Performance Improvement of Chaos Based Substitution Boxes[J]. Symmetry, 2020,12(4):1-13. |
| [5] | ZHU Honghong, TONG Xiaojun, WANG Zhu, et al. A Novel Method of Dynamic S-box Design Based on Combined Chaotic Map and Fitness Function[J]. Multimedia Tools and Applications, 2020,79(5):12329-12347. |
| [6] | HUSSAM A A, MOHAMAD F Z, MUSHEER A. A Novel Efficient Substitution-box Design Based on Firefly Algorithm and Discrete Chaotic Map[J]. Neural Computing and Applications, 2019,31(11):7201-7210. |
| [7] | FATIH Ö, AHMET B Ö. A Method for Designing Strong S-Boxes Based on Chaotic Lorenz System[J]. Physics Letters A, 2010,374(36):3733-3738. |
| [8] | DRAGAN L. A Novel Method of S-box Design Based on Discrete Chaotic Map[J]. Nonlinear Dynamics, 2017,87(3):2407-2413. |
| [9] | AKRAM B, AHMED A A E. A Simple Yet Efficient S-box Method Based on Chaotic Sine Map[J]. Optik, 2017,130(2):1438-1444. |
| [10] |
FATIH Ö. Construction of Robust Substitution Boxes Based on Chaotic Systems[J]. Neural Computing and Applications, 2019,31(8):3317-3326.
doi: 10.1007/s00521-017-3287-y URL |
| [11] | KHAWAJA M A, MAJID K. Application Based Construction and Optimization of Substitution Boxes Over 2D Mixed Chaotic Maps[J]. International Journal of Theoretical Physics, 2019,58(9):3091-3117. |
| [12] |
ARSLAN S. A New Algorithm for the Construction of Substitution Box by Using Chaotic Map[J]. The European Physical Journal Plus, 2020,135(9):1-13.
doi: 10.1140/epjp/s13360-019-00059-2 URL |
| [13] |
SHENG Liyuan, SUN Kehui, LI Chuanbing. Study on Discrete Chaotic System of Elliptic Reflection Cavity Based on Tangent Delay and Its Performance[J]. Acta Physica Sinica, 2004,53(9):2871-2876.
doi: 10.7498/aps.53.2871 URL |
|
盛利元, 孙克辉, 李传兵. 基于切延迟的椭圆反射腔离散混沌系统及其性能研究[J]. 物理学报, 2004,53(9):2871-2876.
doi: 10.7498/aps.53.2871 URL |
|
| [14] | ZHANG Linhua, DENG Shaojiang. S-box Construction of Tangent Delay Elliptic Reflection Cavity Mapping System[J]. Journal of Chongqing University, 2009,32(10):1226-1230. |
| 张林华, 邓绍江. 切延迟椭圆反射腔映射系统的S盒构造[J]. 重庆大学学报, 2009,32(10):1226-1230. | |
| [15] |
IQTADAR H, TARIQ S, MUHAMMAD A G, et al. A Novel Method for Designing Nonlinear Component for Block Cipher Based on TD-ERCS Chaotic Sequence[J]. Nonlinear Dynamics, 2013,73(7):633-637.
doi: 10.1007/s11071-013-0816-9 URL |
| [16] |
ALI H A, IQTADAR H, MUHAMMAD A G. A Novel Design for the Construction of Safe S-boxes Based on TDERC Sequence[J]. Alexandria Engineering Journal, 2015,54(1):65-69.
doi: 10.1016/j.aej.2015.01.003 URL |
| [17] | WEN Qiaoyan, YANG Yixian. Construction of Boolean Functions with High Nonlinearity[J]. Acta Electronica Sinica, 1997,27(7):108-112. |
| 温巧燕, 杨义先. 高非线性度布尔函数的构造[J]. 电子学报, 1997,27(7):108-112. | |
| [18] | YANG Tingting. Design of Multi-output Elastic Boolean Functions with High Nonlinearity[D]. Xi’an: Xi’an University of Electronic Science and Technology, 2018. |
| 杨婷婷. 具有高非线性度的多输出弹性布尔函数的设计[D]. 西安:西安电子科技大学, 2018. | |
| [19] | WANG Yong, ZHANG Zhiqiang, ZHANG Leyu, et al. A Genetic Algorithm for Constructing Bijective Substitution Boxes with High Nonlinearity[J]. Information Sciences, 2020,523(6):152-166. |
| [20] | KIM K. Construction of DES-like S-Boxes Based on Boolean Functions Satisfying the SAC[EB/OL]. https://doi.org/10.1007/3-540-57332-1_5, 2020-07-12. |
| [21] | MUHAMMAD A K, VARUN J. A Novel Design of Chaos Based S-Box Using Difference Distribution Table (CD S-Box)[J]. Communications in Computer and Information Science, 2014,42(3):223-230. |
| [22] | MUHAMMAD A K, ASIM A, VARUN J, et al. A Chaos-based Substitution Box (S-Box) Design with Improved Differential Approximation Probability(DP)[J]. Iranian Journal of Science and Technology Transactions of Electrical Engineering, 2018,42(2):219-238. |
| [23] | WILLIAM M. How to Improve the Nonlinearity of Bijective S-boxes[J]. Lecture Notes in Computer Science, 1998,38(7):181-192. |
| [24] | GAO Sheng, MA Wenping, GUO Na, et al. A New Algorithm for Improving the Nonlinearity of S-box[J]. Journal of Xi’an University of Electronic Science and Technology, 2010,37(6):1017-1021. |
| 高胜, 马文平, 郭娜, 等. 一种提高S盒非线性度的新算法[J]. 西安电子科技大学学报, 2010,37(6):1017-1021. | |
| [25] | YU Yizhou, OU Haiwen. Two Methods to Improve the Nonlinearity of Bijective S-boxes and the Comparison[J]. China New Communication, 2007,9(3):36-39. |
| 于亦舟, 欧海文. 两种提高双射S盒非线性度的方法及其比较[J]. 中国新通信, 2007,9(3):36-39. | |
| [26] | QIN Guanjie, MA Jianshe, CHENG Xuemin. Method of Improving S-box Nonlinearity Based on Combined Hill Climbing Algorithm[J]. Computer Applications, 2015,35(8):2195-2198. |
|
覃冠杰, 马建设, 程雪岷. 基于组合式爬山算法提高S盒非线性度的方法[J]. 计算机应用, 2015,35(8):2195-2198.
doi: 10.11772/j.issn.1001-9081.2015.08.2195 URL |
|
| [27] | LEI Peng. Research on Chaotic S-box Construction and Encryption Algorithm[D]. Chongqing: Chongqing University of Posts and Telecommunications, 2015. |
| 雷鹏. 基于混沌的S盒构造及其加密算法研究[D]. 重庆:重庆邮电大学, 2015. | |
| [28] | WANG Yong, LEI Peng. A Method for Constructing Bijective S-Box with High Nonlinearity Based on Chaos and Optimization[J]. International Journal of Bifurcation and Chaos, 2015,25(10):1-15. |
| [29] | PIEPRZYK J, FINKELSTEIN G. Towards Effective Nonlinear Cryptosystem Design[J]. IEEE Proceedings Computers and Digital Techniques, 1988,135(6):325-335. |
| [30] |
IQTADAR H, TARIQ S. Literature Survey on Nonlinear Components and Chaotic Nonlinear Components of Block Ciphers[J]. Nonlinear Dynamics, 2013,74(12):869-904.
doi: 10.1007/s11071-013-1011-8 URL |
| [31] |
JAKIMOSKI G, KOCAREV L. Chaos and Cryptography: Block Encryption Ciphers Based on Chaotic Maps[J]. IEEE Transactions on Circuits and Systems I: Fundamental Theory and Applications, 2001,48(2):163-169.
doi: 10.1109/81.904880 URL |
| [32] | WEBSTER A F, TAVARES S E. On the Design of S-boxes[EB/OL]. https://doi.org/10.1007/3-540-39799-X_41, 2020-07-12. |
| [33] | BIHAM E, SHAMIR A. Differential Cryptanalysis of DES-like Cryptosystems[J]. Journal of Cryptology, 1991,4(1):63-72. |
| [34] | MATSUI L. Linear Cryptanalysis Method for DES Cipher[EB/OL]. https://doi.org/10.1007/3-540-48285-7_33, 2020-07-12. |
| [1] | 金志刚, 王新建, 李根, 岳顺民. 融合攻击图和博弈模型的网络防御策略生成方法[J]. 信息网络安全, 2021, 21(1): 1-9. |
| [2] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [3] | 王鹃, 杨泓远, 樊成阳. 一种基于多阶段攻击响应的SDN动态蜜罐[J]. 信息网络安全, 2021, 21(1): 27-40. |
| [4] | 宋宇波, 耿益瑾, 李古月, 李涛. 基于差分星座轨迹图的LoRa设备识别方法[J]. 信息网络安全, 2021, 21(1): 41-48. |
| [5] | 陈福才, 周梦丽, 刘文彦, 梁浩. 云环境下面向拟态防御的反馈控制方法[J]. 信息网络安全, 2021, 21(1): 49-56. |
| [6] | 王建新, 周世强, 肖超恩, 张磊. 基于FPGA的FESH分组密码算法高速实现[J]. 信息网络安全, 2021, 21(1): 57-64. |
| [7] | 王跃达, 黄潘, 荆涛, 宋雅稀. 一种基于高速网络的WebShell综合检测溯源技术研究与实现[J]. 信息网络安全, 2021, 21(1): 65-71. |
| [8] | 张富成, 付绍静, 夏竟, 罗玉川. 基于GlusterFS的分布式数据完整性验证系统[J]. 信息网络安全, 2021, 21(1): 72-79. |
| [9] | 沈也明, 李贝贝, 刘晓洁, 欧阳远凯. 基于主动学习的工业互联网入侵检测研究[J]. 信息网络安全, 2021, 21(1): 80-87. |
| [10] | 董锵, 罗国明, 史宏逵, 张永跃. 基于IMS的移动通信专网认证和密钥协商方法研究[J]. 信息网络安全, 2021, 21(1): 88-96. |
| [11] | 尤玮婧, 刘丽敏, 马悦, 韩东. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. |
| [12] | 何泾沙, 韩松, 朱娜斐, 葛加可. 基于改进V-detector算法的入侵检测研究与优化[J]. 信息网络安全, 2020, 20(12): 19-27. |
| [13] | 张新跃, 胡安磊, 李炬嵘, 冯燕春. 一种自适应的异常流量检测方法[J]. 信息网络安全, 2020, 20(12): 28-32. |
| [14] | 赵国锋, 周文涛, 徐川, 徐磊. 一种基于双线性配对的天地一体化网络安全身份认证方案[J]. 信息网络安全, 2020, 20(12): 33-39. |
| [15] | 冯雁, 刘念, 谢四江. 一种量子密钥池的双向使用方案[J]. 信息网络安全, 2020, 20(12): 40-46. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||