信息网络安全 ›› 2019, Vol. 19 ›› Issue (7): 31-41.doi: 10.3969/j.issn.1671-1122.2019.07.004
基于程序切片技术的云计算软件安全模型研究
- 西安电子科技大学,陕西西安 710071
-
收稿日期:2018-10-15出版日期:2019-07-19发布日期:2020-05-11 -
作者简介:作者简介:崔艳鹏(1978—),女,陕西,副教授,博士,主要研究方向为信号处理、系统模拟;冯璐铭(1994—),男,山西,硕士研究生,主要研究方向网络安全、二进制安全、恶意代码分析;闫峥(1972—),女,陕西,教授,博士,主要研究方向为信息安全与隐私保护、信任管理与可信计算;蔺华庆(1994—),男,山东,硕士研究生,主要研究方向为安全数据采集与分析、网络威胁检测。
-
基金资助:国家自然科学基金[61672410,61802293]
Research on Software Security Model of Cloud Computing Based on Program Slicing Technology
Yanpeng CUI, Luming FENG( ), Zheng YAN, Huaqing LIN
), Zheng YAN, Huaqing LIN
- Xidian University, Xi’an Shaanxi 710071, China
-
Received:2018-10-15Online:2019-07-19Published:2020-05-11
摘要:
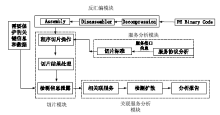
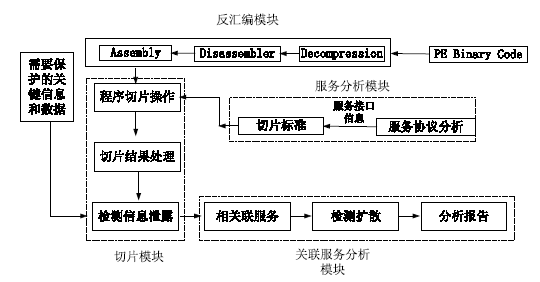
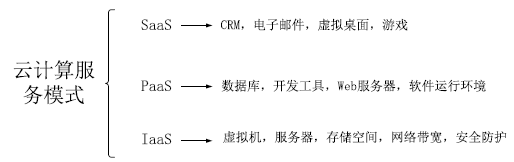
云计算是新一代信息技术产业的重要组成部分,是继个人计算机、互联网之后信息技术的第三次浪潮。虽然各界都一致认为云计算有着巨大的增长空间,但在推广中依然面临着用户认可度不高、运营经验不足、产业链不完善等诸多问题。在诸多不利因素中,云计算的安全性问题一直排在首位,云安全逐渐成为制约云计算发展的瓶颈。在云计算应用场景中,由于云计算的大规模、高动态、高开放等特点使其不但面临着一般的安全问题,而且还面临着由其固有特点所带来的安全风险。这些安全风险包括服务模式、虚拟化技术、云计算管理软件等所带来的安全问题。由于程序切片技术可以很好的辅助安全测试人员来分析云计算软件,因此文章提出了一种基于程序切片技术的云计算软件安全分析模型,该模型可以用于发现云计算软件中存在的关键信息泄露漏洞以及此类漏洞的扩散情况,从而提高对关键信息的保护能力。最后,文章讨论了云计算软件安全模型现存研究中的主要问题,并对未来的研究方向提出了建议。
中图分类号:
引用本文
崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41.
Yanpeng CUI, Luming FENG, Zheng YAN, Huaqing LIN. Research on Software Security Model of Cloud Computing Based on Program Slicing Technology[J]. Netinfo Security, 2019, 19(7): 31-41.
| [1] | KRSUL I V.Software Vulnerability Analysis[M]. West Lafayette: Purdue University, 1998. |
| [2] | ABLON L, BOGART A. Zero Days, Thousands of Nights: The Life and Times of Zero-Day Vulnerabilities and Their Exploits[M]. California: Rand Corporation, 2017. |
| [3] | MCGRAW G.Software Security[J]. Security & Privacy IEEE, 2012, 36(9): 662-665. |
| [4] | WEISER M.Program Slices: Formal,Psychological,Practical Investigations of An Automatic Program Abstraction Method[EB/OL]. , 2018-9-15. |
| [5] | WEISER M.Program Slicing[C]//IEEE. Proceedings of the 5th International Conference on Software Engineering, March 9-12, 1981, San Diego, California, USA. New Jersey: IEEE, 1981: 439-449. |
| [6] | WEISER M.Programmers Use Slices When Debugging[J]. Communications of the ACM, 1982, 25(7): 446-452. |
| [7] | GALLAGHER K B, LYLE J R.Using Program Slicing in Software Maintenance[J]. IEEE Transactions on Software Engineering, 1991, 17(8): 751-761. |
| [8] | LUCIA A.Program Slicing: Methods and Applications[C]//IEEE. Proceedings First IEEE International Workshop on Source Code Analysis and Manipulation, November 10-December 10, 2001, Florence, Italy. Washington: IEEE, 2001: 142-149. |
| [9] | GALLAGHER K B, LYLE J R.Software Safety and Program Slicing[C]//IEEE. COMPASS’93: Proceedings of the Eighth Annual Conference on Computer, June 14-17, 1993, Gaithersburg, MD, USA. Maryland: IEEE, 1993: 71-80. |
| [10] | OTTENSTEIN K J, OTTENSTEIN L M.The Program Dependence Graph in a Software Development Environment[J]. ACM Sigplan Notices, 1993, 19(5): 177-184. |
| [11] | KUCK D J, KUHN R H, PADUA D A, et al.Dependence Graphs and Compiler Optimizations[C]//ACM. Proceedings of the 8th ACM SIGPLAN-SIGACT symposium on Principles of Programming Languages, January 26-28, 1981, Williamsburg, Virginia. New York: ACM, 1981: 207-218. |
| [12] | FERRANTE J, OTTENSTEIN K J, WARREN J D.The Program Dependence Graph and Its Use in Optimization[J]. ACM Transactions on Programming Languages and Systems (TOPLAS), 1987, 9(3): 319-349. |
| [13] | KOREL B, LASKI J.Dynamic Slicing of Computer Programs[J]. Journal of Systems and Software, 1990, 13(3): 187-195. |
| [14] | KRSU L.Software Vulnerability Analysis[M]. West Lafayette: Purdue University, 1998. |
| [15] | LIU B, SHI L, CAI Z, et al.Software Vulnerability Discovery Techniques: A Survey[C]//IEEE. 2012 Fourth International Conference on Multimedia Information Networking and Security, November 2-4, 2012, Washington, DC, USA. Washington: IEEE Computer Society, 2012: 152-156. |
| [16] | STAVROULAKIS P, Stamp M.Handbook of Information and Communication Security[M]. Berlin: Springer Science & Business Media, 2010. |
| [17] | MCGRAW G, MORRISETT G.Attacking Malicious Code: A Report to the Infosec Research Council[J]. IEEE software, 2000 (5): 33-41. |
| [18] | COLLBERG C S, THOMBORSON C.Watermarking, Tamper-proofing, and Obfuscation-tools for Software Protection[J]. IEEE Transactions on Software Engineering, 2002, 28(8): 735-746. |
| [19] | LIU M, JIA C, LIU L, et al.Extracting Sent Message Formats from Executables Using Backward Slicing[C]//IEEE. 2013 Fourth International Conference on Emerging Intelligent Data and Web Technologies, September 9-11, 2013, Washington, DC, USA. Washington: IEEE Computer Society, 2013: 377-384. |
| [20] | ROZINOV K.Efficient Static Analysis of Executables for Detecting Malicious Behaviors[EB/OL]. , 2018-9-15. |
| [21] | JOHNSON N M, CABALLERO J, CHEN K Z, et al.Differential Slicing: Identifying Causal Execution Differences for Security Applications[C]//IEEE. 2011 IEEE Symposium on Security and Privacy, May 22-25, 2011, Berkeley, California, USA. California: Security and Privacy (SP), 2011: 347-362. |
| [22] | ZHU E, LIU F, FANG X, et al.DYBS: A Lightweight Dynamic Slicing Framework for Diagnosing Attacks on x86 Binary Programs[J]. Journal of Software, 2014, 9(3): 560-568. |
| [23] | HUANG S, ZHENG Y, ZHANG R.Attack Diagnosis on Binary Executables Using Dynamic Program Slicing[J]. . |
| [24] | LU Y, YI S, LEI Z, et al.Binary Software Vulnerability Analysis Based on Bidirectional-slicing[C]//IEEE. 2012 Second International Conference on Instrumentation, Measurement, Computer, Communication and Control, December 8-10, 2012, Washington, DC, USA. Washington: IEEE Computer Society, 2012: 842-845. |
| [25] | LESTRINGANT P,GUIHÉRY F,FOUQUE P A. Assisted Identification of Mode of Operation in Binary Code with Dynamic Data Flow Slicing[C]//Springer. International Conference on Applied Cryptography and Network Security, June 19-22, 2016, London (Guildford), United Kingdom. Berlin: Springer, Cham, 2016: 561-579. |
| [26] | DENG X, XU G, SUN G, et al.Software Watermarking Based on Dynamic Program Slicing[C]//IEEE. 2008 International Conference on Intelligent Information Hiding and Multimedia Signal Processing, August 15-17, 2008, Harbin, China. Washington: IEEE, 2008: 461-464. |
| [27] | LI X, CAO Y, FENG Z, et al.Web Service Security Analysis Model Based on Program Slicing[C]//IEEE. 2010 10th International Conference on Quality Software, July 14-15, 2010, Zhangjiajie, China. Washington: IEEE, 2010: 422-428. |
| [28] | FU W, ZHANG Y, ZHU X, et al.WSSecTool: A Web Service Security Analysis Tool Based on Program Slicing[C]//IEEE. 2012 IEEE Eighth World Congress on Services, June 24-29, 2012, Washington, DC, USA. Washington: IEEE Computer Society, 2012: 179-183. |
| [29] | TONG F, YAN Z.A Hybrid Approach of Mobile Malware Detection in Android[J]. Journal of Parallel and Distributed Computing, 2017, 103(5): 22-31. |
| [30] | YAN P, YAN Z.A Survey on Dynamic Mobile Malware Detection[J]. Software Quality Journal, 2018, 26(3): 891-919. |
| [1] | 刘渊, 乔巍. 云环境下基于Kubernetes集群系统的容器网络研究与优化[J]. 信息网络安全, 2020, 20(3): 36-44. |
| [2] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [3] | 任良钦, 王伟, 王琼霄, 鲁琳俪. 一种新型云密码计算平台架构及实现[J]. 信息网络安全, 2019, 19(9): 91-95. |
| [4] | 余奕, 吕良双, 李肖坚, 王天博. 面向移动云计算场景的动态网络拓扑描述语言[J]. 信息网络安全, 2019, 19(9): 120-124. |
| [5] | 王紫璇, 吕良双, 李肖坚, 王天博. 基于共享存储的OpenStack虚拟机应用分发策略[J]. 信息网络安全, 2019, 19(9): 125-129. |
| [6] | 刘玉岭, 唐云善, 张琦, 李枫. 电力调度自动化软件安全态势评估方法[J]. 信息网络安全, 2019, 19(8): 15-21. |
| [7] | 葛新瑞, 崔巍, 郝蓉, 于佳. 加密云数据上支持可验证的关键词排序搜索方案[J]. 信息网络安全, 2019, 19(7): 82-89. |
| [8] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [9] | 赵谱, 崔巍, 郝蓉, 于佳. 一种针对El-Gamal数字签名生成的安全外包计算方案[J]. 信息网络安全, 2019, 19(3): 81-86. |
| [10] | 张振峰, 张志文, 王睿超. 网络安全等级保护2.0云计算安全合规能力模型[J]. 信息网络安全, 2019, 19(11): 1-7. |
| [11] | 冯新扬, 沈建京. 一种基于Yarn云计算平台与NMF的大数据聚类算法[J]. 信息网络安全, 2018, 18(8): 43-49. |
| [12] | 陶源, 黄涛, 张墨涵, 黎水林. 网络安全态势感知关键技术研究及发展趋势分析[J]. 信息网络安全, 2018, 18(8): 79-85. |
| [13] | 张琦, 林喜军, 曲海鹏. 云计算中支持授权相等测试的基于身份加密方案[J]. 信息网络安全, 2018, 18(6): 52-60. |
| [14] | 张建标, 杨石松, 涂山山, 王晓. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4): 9-14. |
| [15] | 陈妍, 戈建勇, 赖静, 陆臻. 云上信息系统安全体系研究[J]. 信息网络安全, 2018, 18(4): 79-86. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||