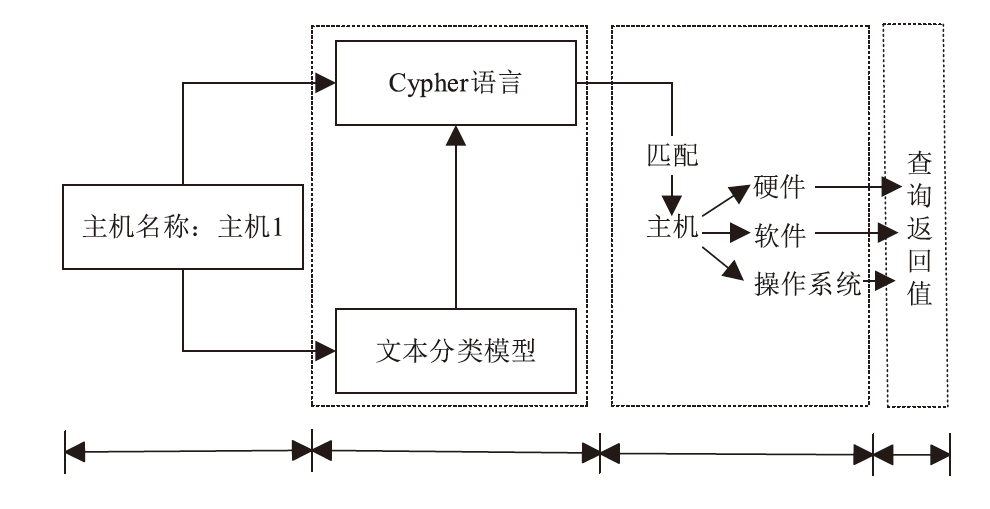
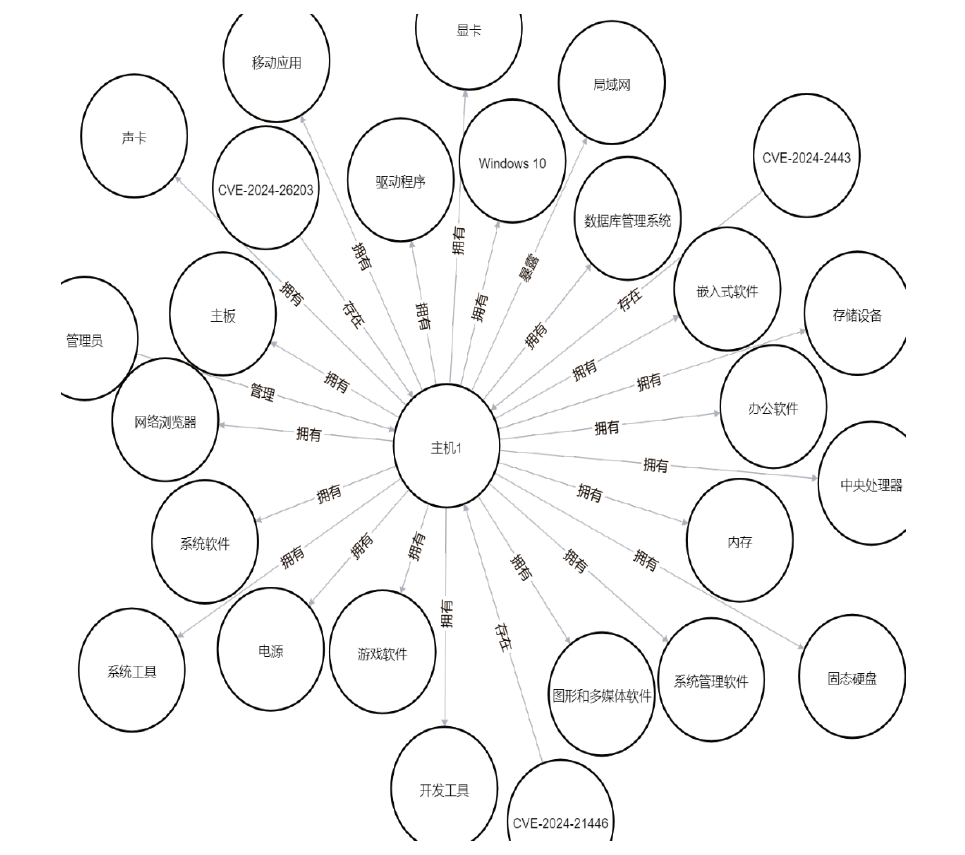
信息网络安全 ›› 2025, Vol. 25 ›› Issue (3): 451-466.doi: 10.3969/j.issn.1671-1122.2025.03.008
基于本体的网络安全知识图谱构建方法
- 1.北京交通大学网络空间安全学院,北京 100044
2.国家信息中心,北京 100045
-
收稿日期:2024-12-30出版日期:2025-03-10发布日期:2025-03-26 -
通讯作者:常晓林 E-mail:xlchang@bjtu.edu.cn -
作者简介:许智双(1999—),女,山东,硕士研究生,主要研究方向为网络安全|张昆(1976—),男,甘肃,高级工程师,本科,主要研究方向为网络安全|范俊超(1998—),男,湖北,博士研究生,主要研究方向为人工智能安全|常晓林(1971—),女,福建,教授,博士,CCF会员,主要研究方向为网络安全与隐私保护 -
基金资助:国家自然科学基金(62272028)
Construction Method of Cybersecurity Knowledge Graph Based on Ontology
XU Zhishuang1, ZHANG Kun2, FAN Junchao1, CHANG Xiaolin1( )
)
- 1. School of Cyberspace Science and Technology, Beijing Jiaotong University, Beijing 100044, China
2. State Information Center, Beijing 100045, China
-
Received:2024-12-30Online:2025-03-10Published:2025-03-26 -
Contact:CHANG Xiaolin E-mail:xlchang@bjtu.edu.cn
摘要:
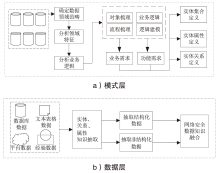
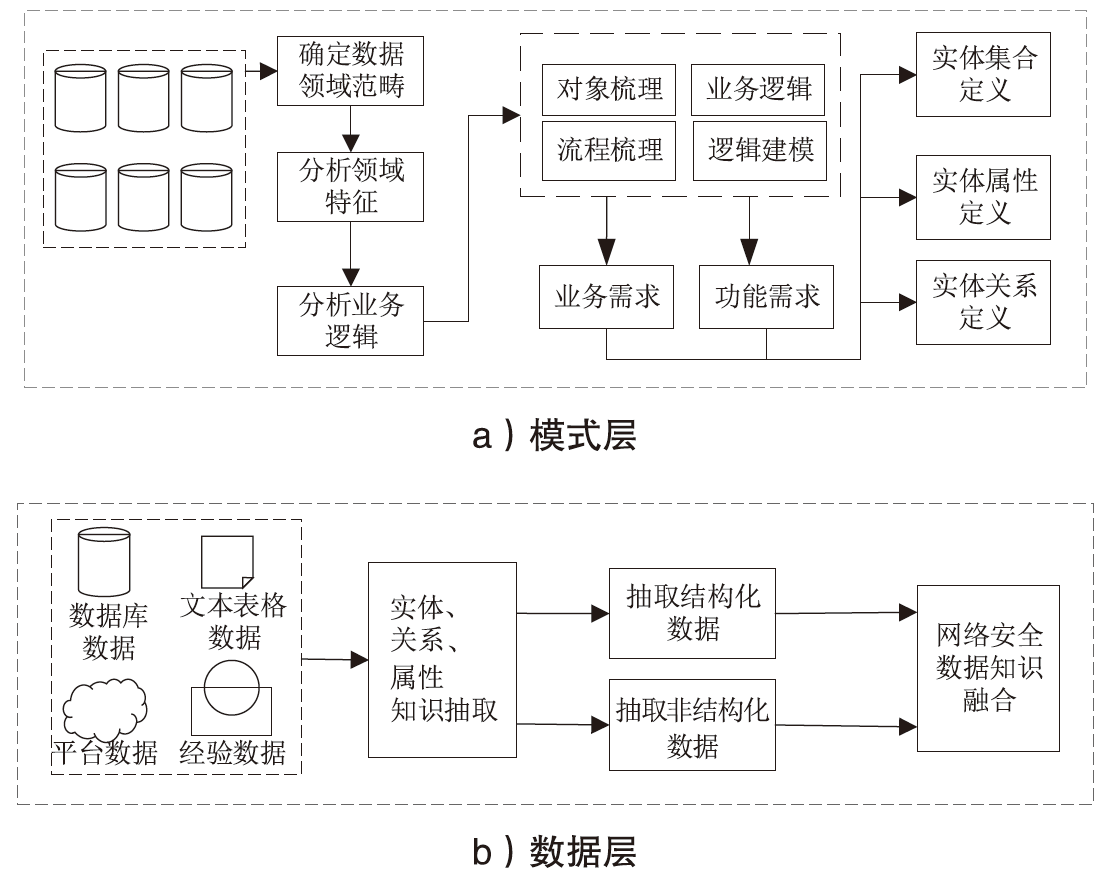
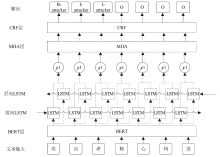
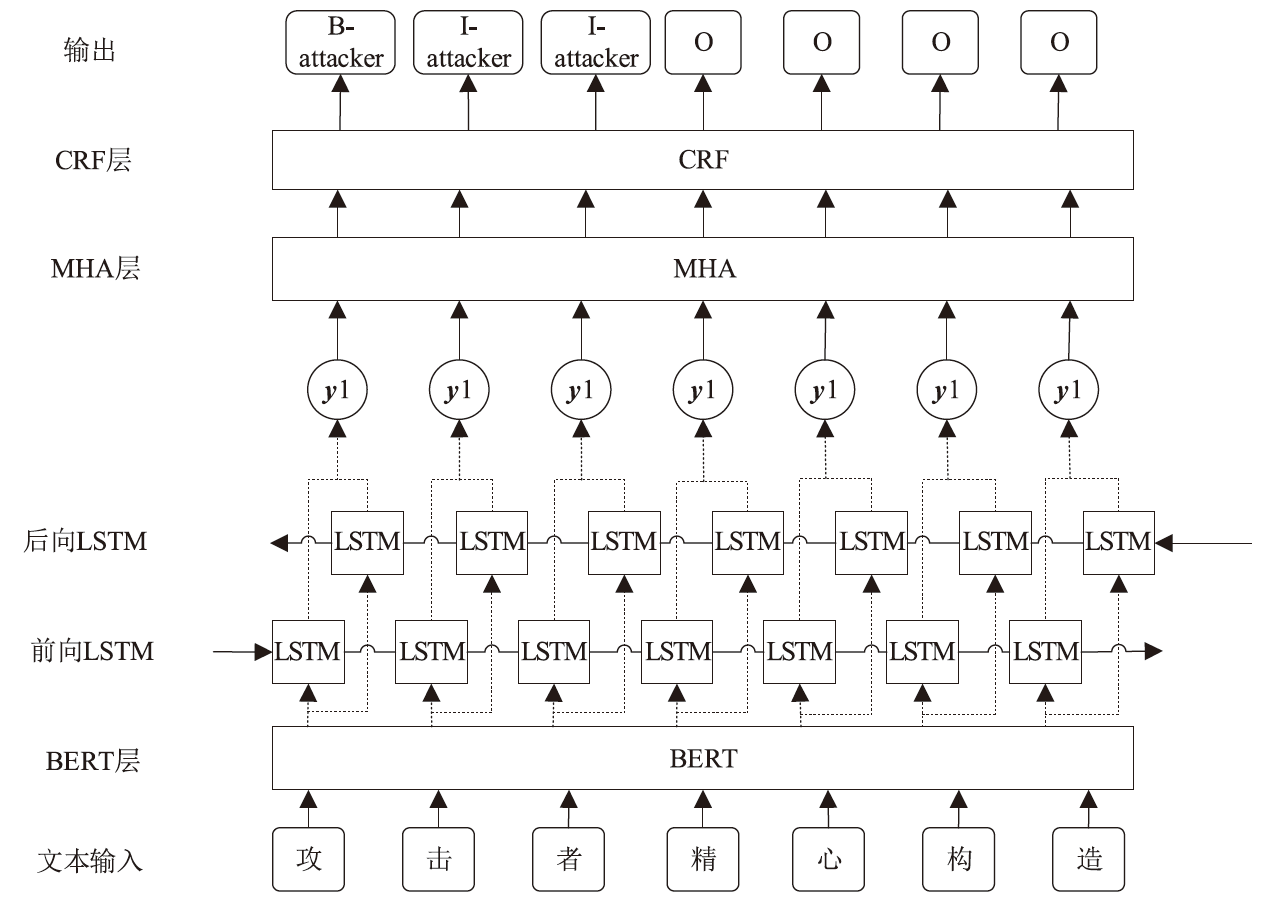
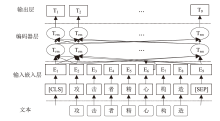
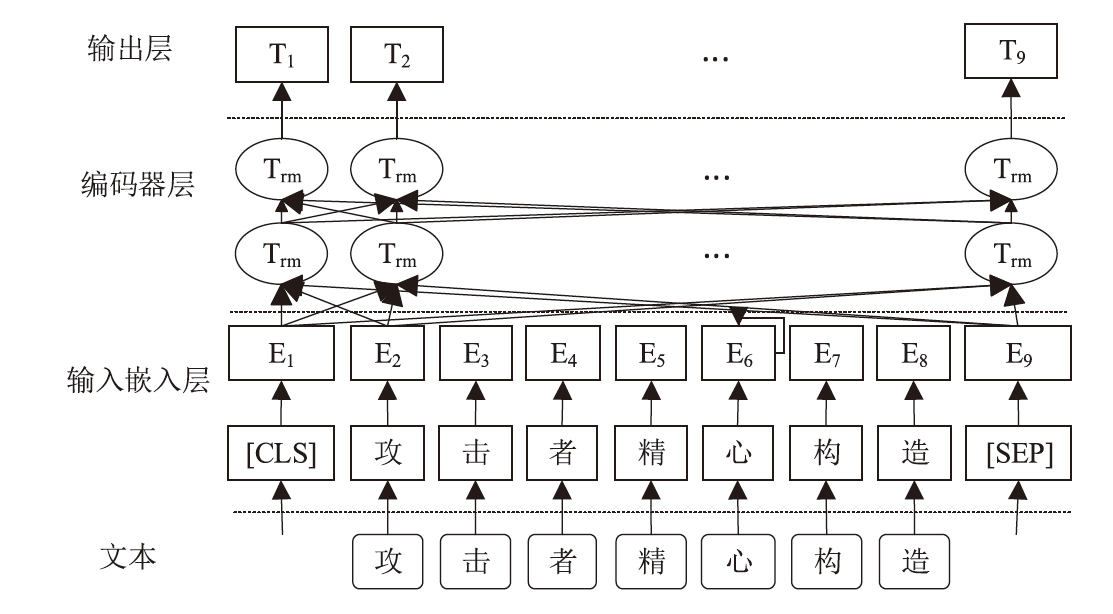
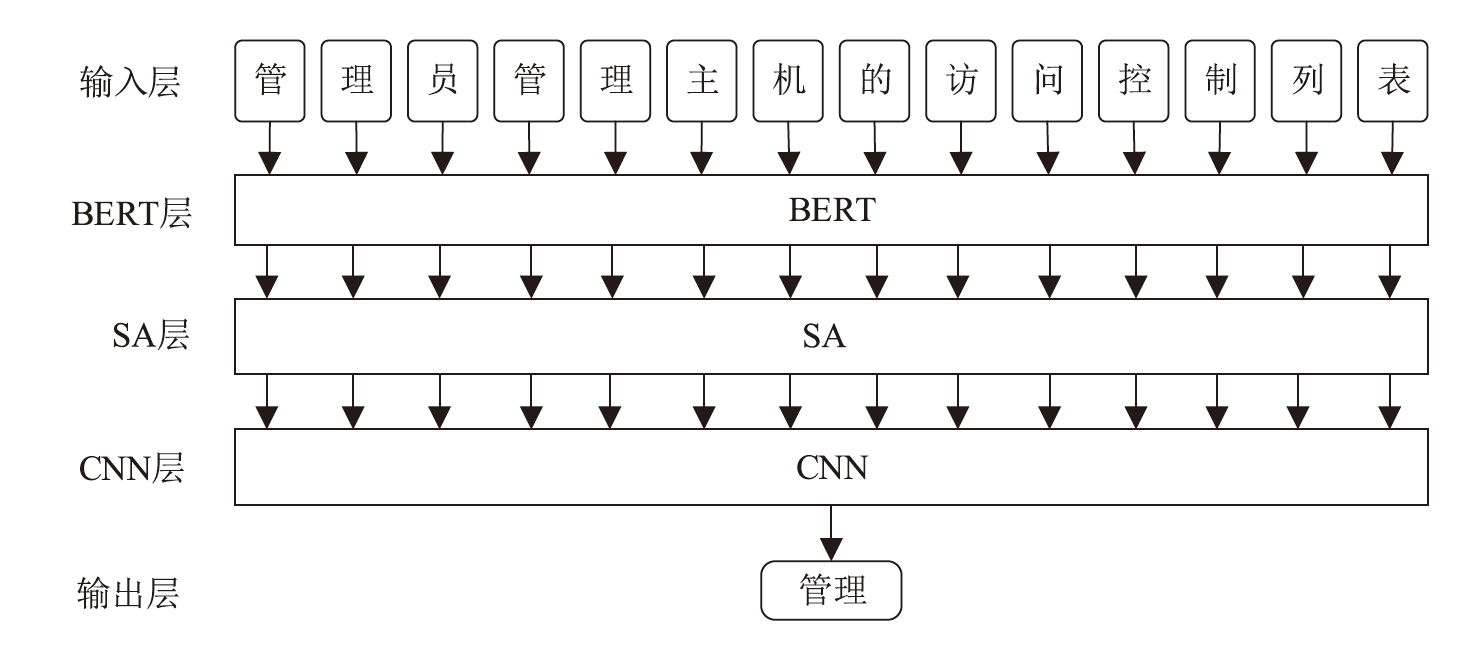
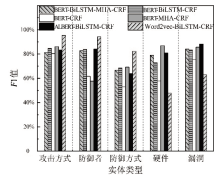
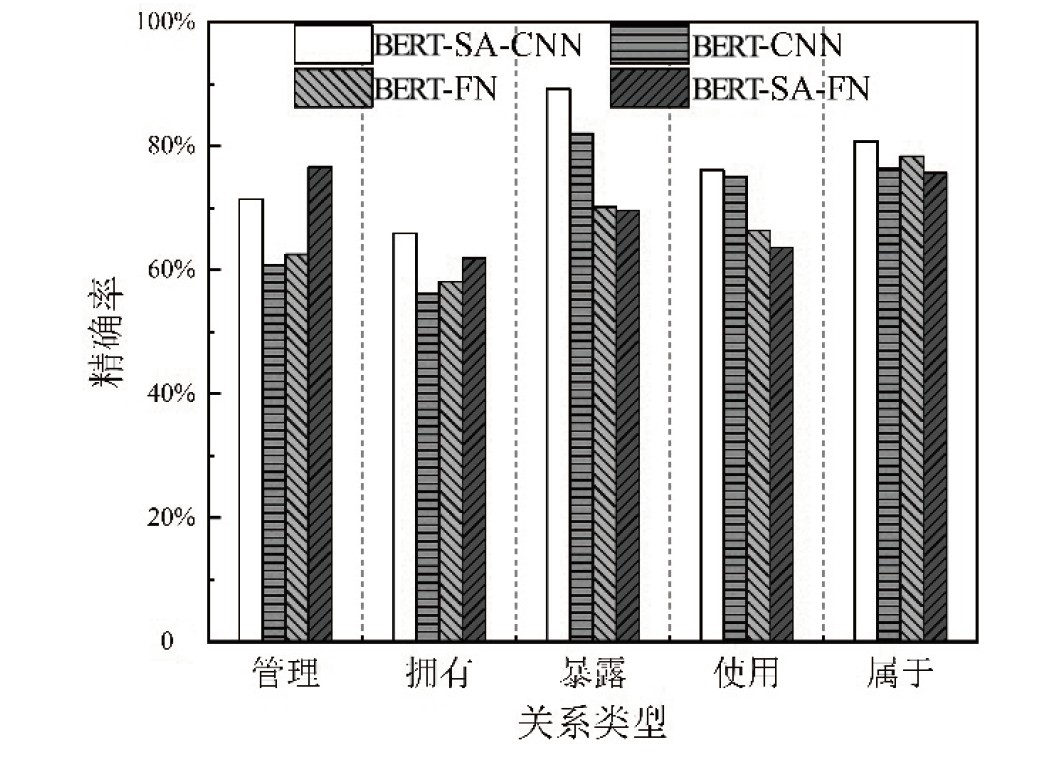
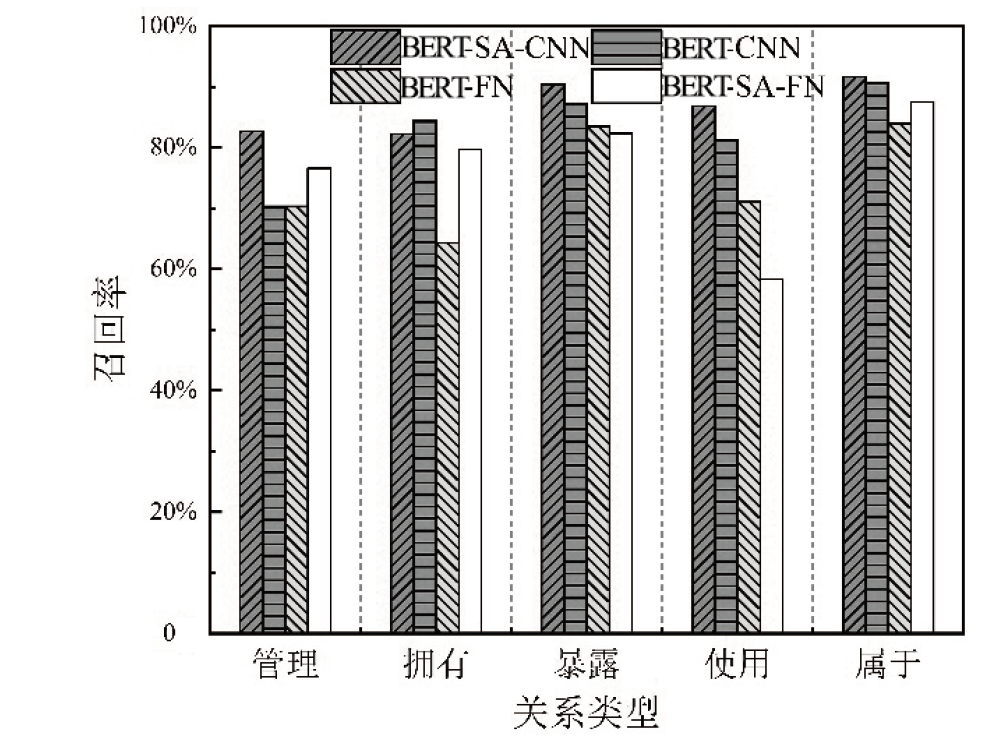
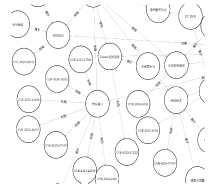
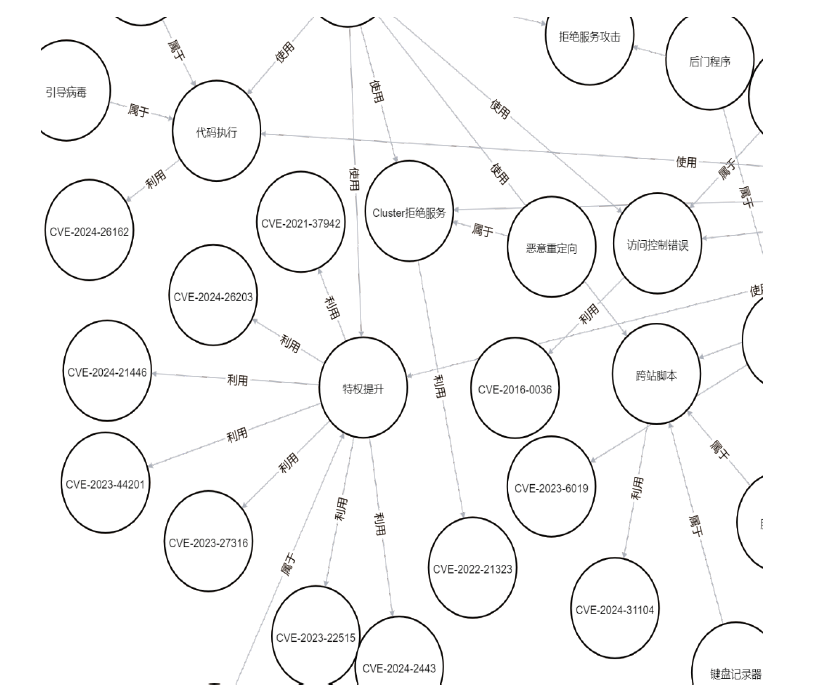
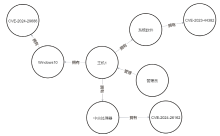
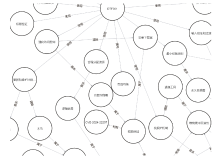
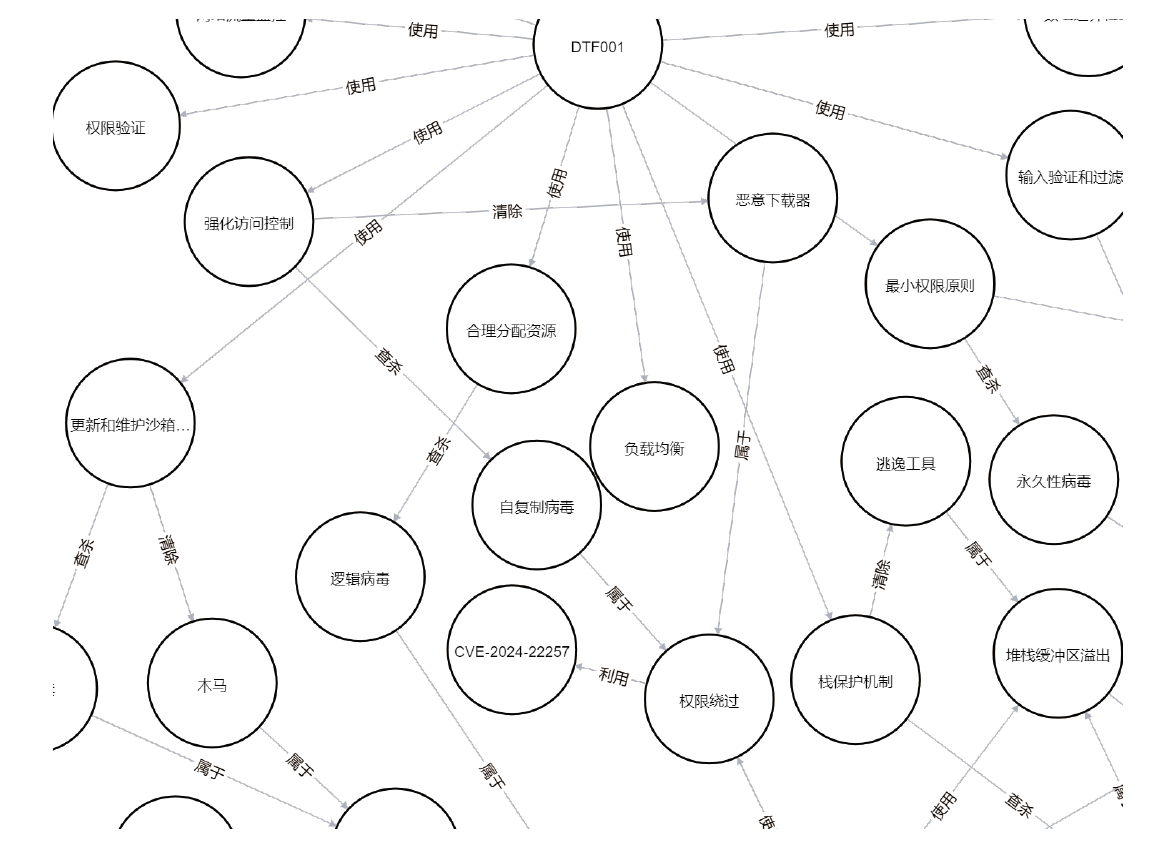
随着信息技术的高速发展,网络空间与现实世界连接越来越紧密。将知识图谱技术应用于网络安全领域,能够从网络空间海量数据中获取碎片化的有效安全知识进行整合,为决策提供支持。现有方法存在本体模型缺乏统一标准、知识抽取效果不佳等问题,因此,文章提出一种基于本体的网络安全知识图谱构建方法,该方法包含命名实体识别和关系抽取两个模型,其中命名实体识别模型结合BERT预训练模型、双向长短期记忆网络、多头注意力机制和条件随机场;关系抽取模型结合BERT预训练模型、自注意力机制和卷积神经网络。这两个模型提升了命名实体识别的准确率,并提升了关系抽取任务的准确率以及自动化程度。文章提出的网络安全知识图谱构建方法可整合并分析网络安全数据,实现网络安全知识的智能化检索以及知识图谱的自动更新和扩展。
中图分类号:
引用本文
许智双, 张昆, 范俊超, 常晓林. 基于本体的网络安全知识图谱构建方法[J]. 信息网络安全, 2025, 25(3): 451-466.
XU Zhishuang, ZHANG Kun, FAN Junchao, CHANG Xiaolin. Construction Method of Cybersecurity Knowledge Graph Based on Ontology[J]. Netinfo Security, 2025, 25(3): 451-466.
使用本文
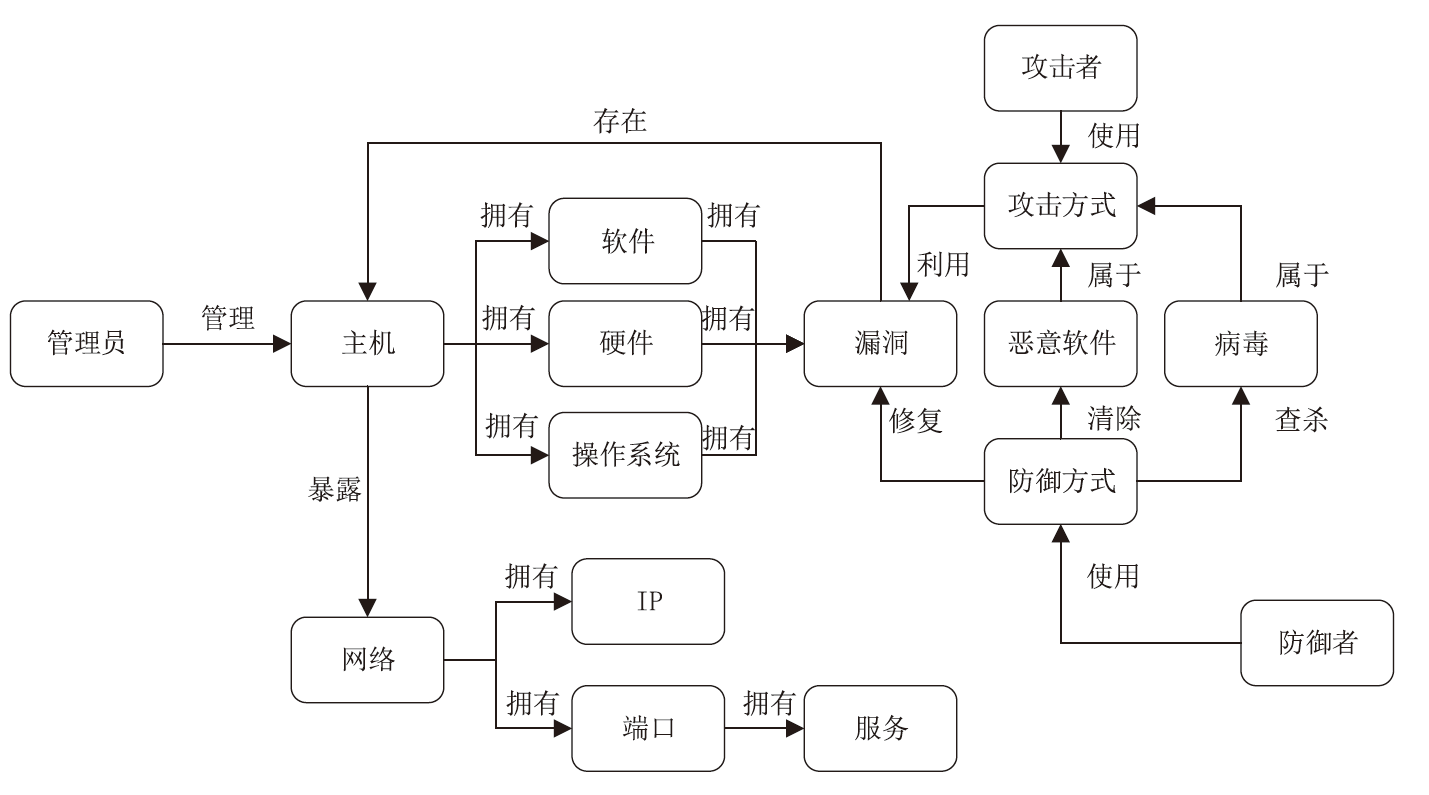
表1
BIO模式命名的标注符号及其含义
| 符号 | 含义 | 符号 | 含义 |
|---|---|---|---|
| B-administrator | 管理员实体的开始部分 | I-network | 网络实体的其余部分 |
| I-administrator | 管理员实体的其余部分 | B-attacker | 攻击者实体的开始部分 |
| B-host | 主机实体的开始 部分 | I-attacker | 攻击者实体的其余部分 |
| I-host | 主机实体的其余 部分 | B-attack_mode | 攻击方式实体的开始 部分 |
| B-system | 操作系统实体的 开始部分 | I-attack_mode | 攻击方式实体的其余 部分 |
| I-system | 操作系统实体的 其余部分 | B-loophole | 漏洞实体的开始部分 |
| B-hardware | 硬件实体的开始 部分 | I-loophole | 漏洞实体的其余部分 |
| I-hardware | 硬件实体的其余 部分 | B-malware | 恶意软件实体的开始 部分 |
| B-software | 软件实体的开始 部分 | I-malware | 恶意软件实体的其余 部分 |
| I-software | 软件实体的其余 部分 | B-virus | 病毒实体的开始部分 |
| B-ip | IP实体的开始部分 | I-virus | 病毒实体的其余部分 |
| I-ip | IP实体的其余部分 | B-defender | 防御者实体的开始部分 |
| B-port | 端口实体的开始 部分 | I-defender | 防御者实体的其余部分 |
| I-port | 端口实体的其余 部分 | B-defense_mode | 防御方式实体的开始 部分 |
| B-service | 服务实体的开始 部分 | I-defense_mode | 防御方式实体的其余 部分 |
| I-service | 服务实体的其余 部分 | O | 非实体 |
| B-network | 网络实体的开始 部分 | — | — |
| [1] | REN Yitong, XIAO Yanjun, ZHOU Yinghai, et al. CSKG4APT: A Cybersecurity Knowledge Graph for Advanced Persistent Threat Organization Attribution[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(6): 5695-5709. |
| [2] | JIANG Yuning, JEUSFELD M A, DING Jianguo, et al. Model-Based Cybersecurity Analysis: Extending Enterprise Modeling to Critical Infrastructure Cybersecurity[J]. Business & Information Systems Engineering, 2023, 65(6): 643-676. |
| [3] | SIKOS L F. Cybersecurity Knowledge Graphs[J]. Knowledge and Information Systems, 2023, 65(9): 3511-3531. |
| [4] | LIU Kai, WANG Fei, DING Zhaoyun, et al. Recent Progress of Using Knowledge Graph for Cybersecurity[J]. Electronics, 2022, 11(15): 2287-2314. |
| [5] | WANG Gaosheng, LIU Peipei, HUANG Jintao, et al. KnowCTI: Knowledge-Based Cyber Threat Intelligence Entity and Relation Extraction[J]. Computers & Security, 2024, 141(6): 1-12. |
| [6] | WANG Xiaodi, HUANG Cheng, LIU Jiayong. Research Overview on Knowledge Graphs for Open Source Intelligence in Cybersecurity[J]. Netinfo Security, 2023, 23(6): 11-21. |
| 王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6):11-21. | |
| [7] | LI Hongyi, ZE Shi, PAN Chengwei, et al. Cybersecurity Knowledge Graphs Construction and Quality Assessment[J]. Complex & Intelligent Systems, 2024, 10(1): 5-16. |
| [8] | CHEN Jiarui, LU Yiqin, ZHANG Yang, et al. A Management Knowledge Graph Approach for Critical Infrastructure Protection: Ontology Design, Information Extraction and Relation Prediction[J]. International Journal of Critical Infrastructure Protection, 2023, 43(4): 3-7. |
| [9] | PREUVENEERS D, JOOSEN W. An Ontology-Based Cybersecurity Framework for AI-Enabled Systems and Applications[J]. Future Internet, 2024, 16(3): 4-18. |
| [10] | GRANDIN A. An Ontology of Cyberspace as a Basis for Decision-Making in Cyberoperations[C]// IEEE. International Conference on Cyber Warface and Security. New York: IEEE, 2024: 84-94. |
| [11] | BUGHIO K S, COOK D M, SHAH S A A. Developing a Novel Ontology for Cybersecurity in Internet of Medical Things-Enabled Remote Patient Monitoring[J]. Sensors, 2024, 24(9): 5-20. |
| [12] | BERNARDINI A, D’ALTERIO F, SAGRATELLA L, et al. “Work-in-Progress” Structuring the Complexity: an Ontological Approach to Analyze the Cybersecurity of a 5G Service[C]// IEEE. 2024 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW). New York: IEEE, 2024: 691-700. |
| [13] | KOUGIOUMTZIDOU A, PAPOUTSIS A, KAVALLIEROS D, et al. An End-to-End Framework for Cybersecurity Taxonomy and Ontology Generation and Updating[C]// IEEE. 2024 IEEE International Conference on Cyber Security and Resilience (CSR). New York: IEEE, 2024: 247-254. |
| [14] | XU Derong, CHEN Wei, PENG Wenjun, et al. Large Language Models for Generative Information Extraction: A Survey[J]. Frontiers of Computer Science, 2024, 18(6): 2-14. |
| [15] | WANG Yaxin, ZHANG Jian. Electronic Medical Record Fingerprint Feature Extraction Based on Few-Shot Named Entity Recognition Technology[J]. Netinfo Security, 2024, 24(10): 1537-1543. |
| 王亚欣, 张健. 基于少样本命名实体识别技术的电子病历指纹特征提取[J]. 信息网络安全, 2024, 24(10):1537-1543. | |
| [16] | STUDIAWAN H, HASAN M F, PRATOMO B A. Rule-Based Entity Recognition for Forensic Timeline[C]// IEEE. 2023 Conference on Information Communications Technology and Society (ICTAS). New York: IEEE, 2023: 1-6. |
| [17] | HU Chenxi, WU Tao, LIU Chunsheng, et al. Joint Contrastive Learning and Belief Rule Base for Named Entity Recognition in Cybersecurity[J]. Cybersecurity, 2024, 7(1): 3-12. |
| [18] | SARHAN M, LAYEGHY S, MOUSTAFA N, et al. Feature Extraction for Machine Learning-Based Intrusion Detection in IoT Networks[J]. Digital Communications and Networks, 2024, 10(1): 205-216. |
| [19] | MUMTAZ G, AKRAM S, IQBAL M W, et al. Classification and Prediction of Significant Cyber Incidents (SCI) Using Data Mining and Machine Learning (DM-ML)[J]. IEEE Access, 2023, 11: 94486-94496. |
| [20] | LI Jiao, ZHANG Yuqing, WU Yabiao. Large Language Model Data Augmentation Methods for Relationship Extraction in Cybersecurity[J]. Netinfo Security, 2024, 24(10): 1477-1483. |
| 李娇, 张玉清, 吴亚飚. 面向网络安全关系抽取的大语言模型数据增强方法[J]. 信息网络安全, 2024, 24(10):1477-1483. | |
| [21] | WANG Fei, DING Zhaoyun, LIU Kai, et al. Multi-Relation Extraction for Cybersecurity Based on Ontology Rule-Enhanced Prompt Learning[J]. Electronics, 2024, 13(12): 1-25. |
| [22] | AHMED K, KHURSHID S K, HINA S. CyberEntRel: Joint Extraction of Cyber Entities and Relations Using Deep Learning[J]. Computer & Security, 2024, 136(1): 1-11. |
| [23] | JI Bin, LI Shasha, XU Hao, et al. Span-Based Joint Entity and Relation Extraction Augmented with Sequence Tagging Mechanism[J]. Science China Information Sciences, 2024, 67(5): 1-15. |
| [24] | CHEN S S, HWANG R H, SUN C Y, et al. Enhancing Cyber Threat Intelligence with Named Entity Recognition Using BERT-CRF[C]// IEEE. IEEE Global Communiacations Conference 2023. New York: IEEE, 2023: 7532-7537. |
| [25] | LIU Yafei, WEI Siqi, HUANG Haijun, et al. Naming Entity Recognition of Citrus Pests and Diseases Based on the BERT-BiLSTM-CRF Model[J]. Expert Systems with Applications, 2023, 234(27): 1-10. |
| [26] | PAN Xuefeng, CAO Yuanyuan, HOU Xiaorui, et al. Named Entity Recognition of TCM Electronic Medical Records Based on the ALBERT-BiLSTM-CRF Model[C]// IEEE. 2022 12th International Conference on Information Technology in Medicine and Education (ITME 2022). New York: IEEE, 2022: 575-582. |
| [27] | KE Jia, WANG Weiji, CHEN Xiaojun, et al. Medical Entity Recognition and Knowledge Map Relationship Analysis of Chinese EMRs Based on Improved BiLSTM-CRF[J]. Computers and Electrical Engineering, 2023, 108(4): 1-18. |
| [28] | 360 Total Security. Security Report[EB/OL]. (2024-05-09) [2024-11-14]. https://cert.360.cn/report. |
| 360安全安全报告[EB/OL]. (2024-05-09) [2024-11-14]. https://cert.360.cn/report. | |
| [29] | National Computer Network Emergency Response Technical Team/Coordination Center of China. Security Report[EB/OL]. (2023-06-28) [2024-11-20]. https://www.cert.org.cn/publish/main/17/index.html. |
| 国家计算机网络应急技术处理协调中心. 安全报告[EB/OL]. (2023-06-28)[2024-11-20]. https://www.cert.org.cn/publish/main/17/index.html. | |
| [30] | KAUR K, KAUR P. BERT-CNN: Improving BERT for Requirements Classification Using CNN[J]. Procedia Computer Science, 2023, 218(3): 2604-2611. |
| [31] | BELLO A, NG S C, LEUNG M F. A BERT Framework to Sentiment Analysis of Tweets[J]. Sensors, 2023, 23(1): 1-14. |
| [1] | 李海龙, 崔治安, 沈燮阳. 网络流量特征的异常分析与检测方法综述[J]. 信息网络安全, 2025, 25(2): 194-214. |
| [2] | 张新有, 高志超, 冯力, 邢焕来. 基于FFT-iTransformer的网络安全态势特征插补与预测[J]. 信息网络安全, 2025, 25(2): 228-239. |
| [3] | 高汉成, 黄海平. 对抗DDoS攻击的新型分布式大规模流量清洗方案[J]. 信息网络安全, 2025, 25(1): 78-87. |
| [4] | 问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137. |
| [5] | 张长琳, 仝鑫, 佟晖, 杨莹. 面向网络安全领域的大语言模型技术综述[J]. 信息网络安全, 2024, 24(5): 778-793. |
| [6] | 杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410. |
| [7] | 金志刚, 陈旭阳, 武晓栋, 刘凯. 增量式入侵检测研究综述[J]. 信息网络安全, 2024, 24(12): 1819-1830. |
| [8] | 秦振凯, 徐铭朝, 蒋萍. 基于提示学习的案件知识图谱构建方法及应用研究[J]. 信息网络安全, 2024, 24(11): 1773-1782. |
| [9] | 李娇, 张玉清, 吴亚飚. 面向网络安全关系抽取的大语言模型数据增强方法[J]. 信息网络安全, 2024, 24(10): 1477-1483. |
| [10] | 何开宇, 王彬, 于哲, 陈方. ARP欺骗攻击与硬件防御研究[J]. 信息网络安全, 2024, 24(10): 1604-1610. |
| [11] | 浦珺妍, 李亚辉, 周纯杰. 基于概率攻击图的工控系统跨域动态安全风险分析方法[J]. 信息网络安全, 2023, 23(9): 85-94. |
| [12] | 付静. 水利关键信息基础设施安全保护探索与实践[J]. 信息网络安全, 2023, 23(8): 121-127. |
| [13] | 孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6): 104-110. |
| [14] | 王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6): 11-21. |
| [15] | 李冬, 于俊清, 文瑞彬, 谢一丁. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 38
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 39
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||