信息网络安全 ›› 2025, Vol. 25 ›› Issue (1): 78-87.doi: 10.3969/j.issn.1671-1122.2025.01.007
对抗DDoS攻击的新型分布式大规模流量清洗方案
- 1.南京邮电大学计算机学院,南京 210023
2.江苏省无线传感网高技术研究重点实验室,南京 210023
-
收稿日期:2024-11-02出版日期:2025-01-10发布日期:2025-02-14 -
通讯作者:黄海平 E-mail:hhp@njupt.edu.cn -
作者简介:高汉成(1998—),男,河南,博士研究生,主要研究方向为网络信息安全|黄海平(1981—),男,福建,教授,博士,CCF会员,主要研究方向为物联网技术、网络信息安全和数据隐私保护技术 -
基金资助:国家自然科学基金(62072252)
A Novel Distributed Large-Scale Traffic Cleaning Scheme against DDoS Attacks
GAO Hancheng1, HUANG Haiping1,2( )
)
- 1. School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. Jiangsu High Technology Research Key Laboratory for Wireless Sensor Networks, Nanjing 210023, China
-
Received:2024-11-02Online:2025-01-10Published:2025-02-14 -
Contact:HUANG Haiping E-mail:hhp@njupt.edu.cn
摘要:
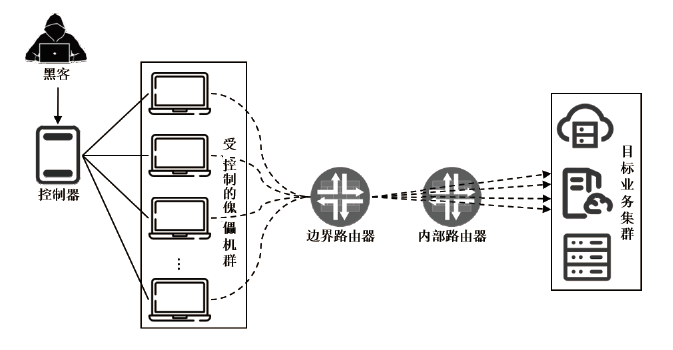
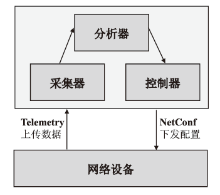
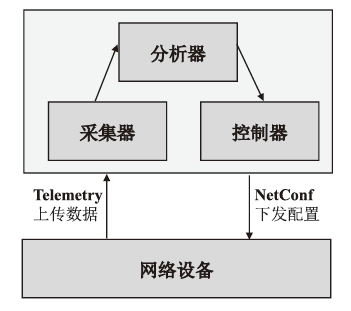
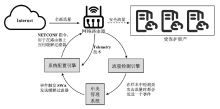
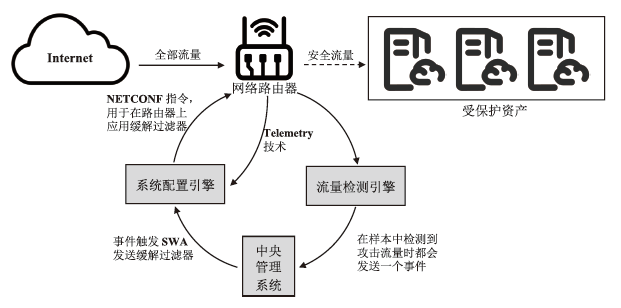
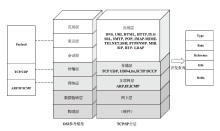
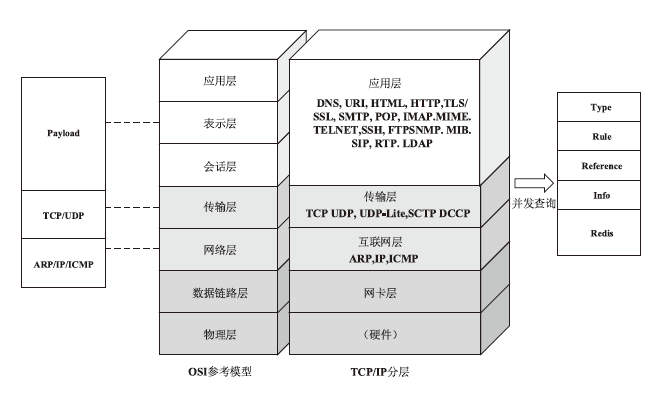
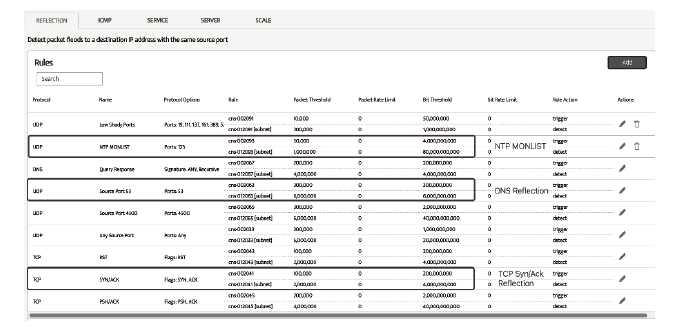
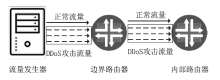
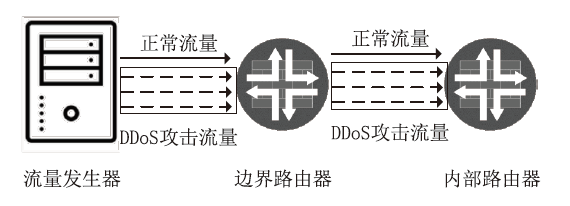
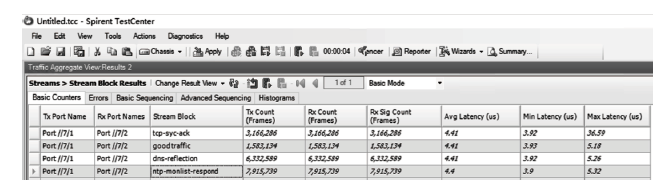
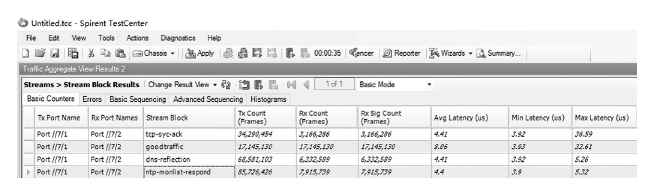
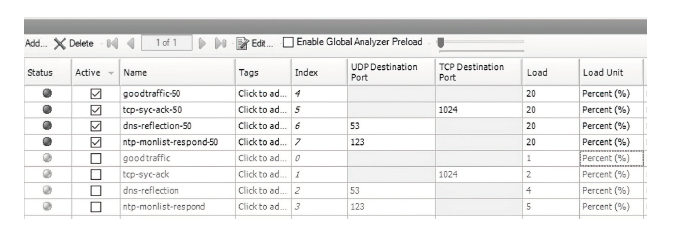
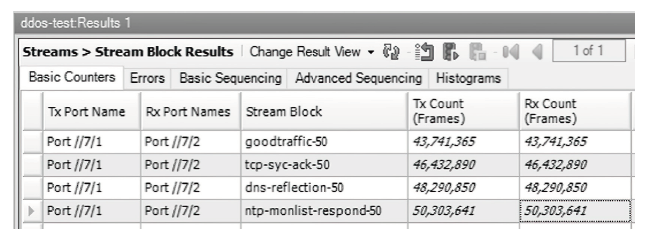
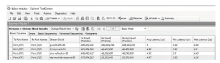
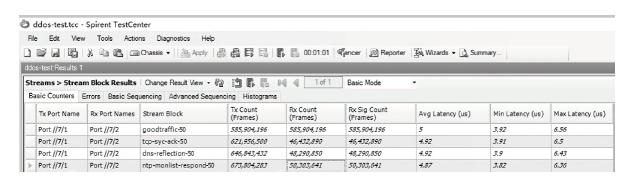
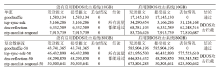
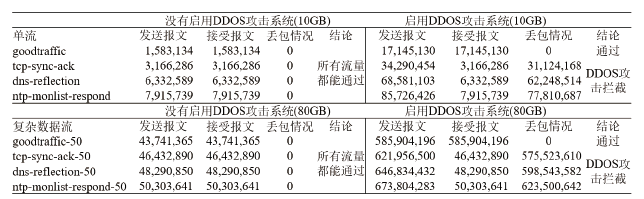
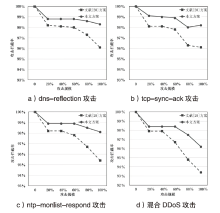
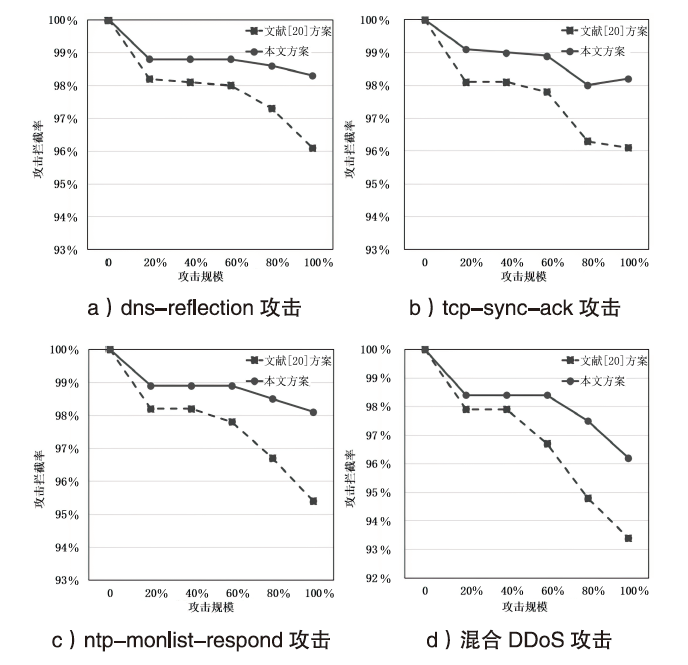
随着网络安全威胁的不断加剧,分布式拒绝服务对网络稳定性和业务连续性带来了前所未有的挑战。文章提出一种新型分布式大规模流量清洗方案,旨在有效应对DDoS攻击。该方案利用实时端口流量镜像技术和深度包检测技术,实现对恶意流量的快速识别和清洗,并且通过在网络边缘设备上直接清洗攻击流量,避免了带宽浪费和网络拥塞。实验通过模拟正常流量和恶意流量,利用所提方案对流量进行监控和清洗,实验结果表明,该方案能显著提高DDoS攻击流量的拦截和清洗效率,具有较好的实际应用价值。
中图分类号:
引用本文
高汉成, 黄海平. 对抗DDoS攻击的新型分布式大规模流量清洗方案[J]. 信息网络安全, 2025, 25(1): 78-87.
GAO Hancheng, HUANG Haiping. A Novel Distributed Large-Scale Traffic Cleaning Scheme against DDoS Attacks[J]. Netinfo Security, 2025, 25(1): 78-87.
| [1] | KUMAR M J, MISHRA S, ELANGOVAN G R, et al. Bayesian Decision Model Based Reliable Route Formation in Internet of Things[J]. Indonesian Journal of Electrical Engineering and Computer Science, 2024, 34(3): 1677-1685. |
| [2] | DOULIGERIS C, MITROKOTSA A. DDoS Attacks and Defense Mechanisms: Classification and State-of-the-Art[J]. Computer Networks, 2004, 44(5): 643-666. |
| [3] | KUMARI P, JAIN A K. A Comprehensive Study of DDoS Attacks over IoT Network and their Countermeasures[EB/OL]. (2022-01-13)[2024-10-11]. https://www.sciencedirect.com/science/article/abs/pii/S0167404823000068. |
| [4] | DEHKORDI A B, SOLTANAGHAEI M R, BOROUJENI F Z. The DDoS Attacks Detection through Machine Learning and Statistical Methods in SDN[J]. The Journal of Supercomputing, 2021, 77(3): 2383-2415. |
| [5] | HE Qiang, WANG Cheng, CUI Guangming, et al. A Game-Theoretical Approach for Mitigating Edge DDoS Attack[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(4): 2333-2348. |
| [6] | AHUJA N, SINGAL G, MUKHOPADHYAY D, et al. Automated DDoS Attack Detection in Software Defined Networking[EB/OL]. (2021-05-19)[2024-10-11]. https://www.sciencedirect.com/science/article/abs/pii/S1084804521001296. |
| [7] | SHAFIQ M, TIAN Zhihong, BASHIR A K, et al. CorrAUC: A Malicious BOT-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques[J]. IEEE Internet of Things Journal, 2020, 8(5): 3242-3254. |
| [8] | GUO Yutong, GAO Yang, WANG Yan, et al. DPI & DFI: A Malicious Behavior Detection Method Combining Deep Packet Inspection and Deep Flow Inspection[J]. Procedia Engineering, 2017, 174: 1309-1314. |
| [9] | PARRA G D L T, RAD P, CHOO K K R. Implementation of Deep Packet Inspection in Smart Grids and Industrial Internet of Things: Challenges and Opportunities[J]. Journal of Network and Computer Applications, 2019, 135: 32-46. |
| [10] | WEI Bing, XU Zhen. Defense Approach against Application Level DDoS Attacks Based on Authentication Mechanism[J]. Computer Engineering and Design, 2010, 31(2): 231-234. |
| 魏冰, 徐震. 基于验证机制的应用层 DDoS 攻击防御方法[J]. 计算机工程与设计, 2010, 31(2): 231-234. | |
| [11] | DEVI S R, YOGESH P. An Effective Approach to Counter Application Layer DDoS Attacks[C]// IEEE. 2012 the Third International Conference on Computing, Communication and Networking Technologies (ICCCNT’12). New York: IEEE, 2012: 1-4. |
| [12] | ELSAYED M S, LE-KHAC N A, AZER M A, et al. A Flow-Based Anomaly Detection Approach with Feature Selection Method against DDoS Attacks in SDNs[J]. IEEE Transactions on Cognitive Communications and Networking, 2022, 8(4): 1862-1880. |
| [13] | YU Bowen. Research and Implementation of Key Technologies of Intrusion Detection Based on DPI and GAN[D]. Nanjing: Nanjing University of Posts and Telecommunications, 2021. |
| 于博文. 基于深度包检测和生成对抗网络的入侵检测关键技术研究与实现[D]. 南京: 南京邮电大学, 2021. | |
| [14] | SAINZ M, GARITANO I, ITURBE M, et al. Deep Packet Inspection for Intelligent Intrusion Detection in Software-Defined Industrial Networks: A Proof of Concept[J]. Logic Journal of the IGPL, 2020, 28(4): 461-472. |
| [15] | BISWAS R, KIM S, WU Jie. Sampling Rate Distribution for Flow Monitoring and DDoS Detection in Datacenter[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2524-2534. |
| [16] | SONG Wenguang, BESHLEY M, PRZYSTUPA K, et al. A Software Deep Packet Inspection System for Network Traffic Analysis and Anomaly Detection[EB/OL]. (2020-03-14)[2024-10-11]. https://www.mdpi.com/1424-8220/20/6/1637. |
| [17] | LI Jinling, WANG Binqiang, ZHANG Zhen. Detecting App-DDoS Attacks Based on Flow Analysis[J]. Application Research of Computers, 2013, 30(2): 487-490. |
| 李锦玲, 汪斌强, 张震. 基于流量分析的 App-DDoS 攻击检测[J]. 计算机应用研究, 2013, 30(2): 487-490. | |
| [18] | ZHANG Zhe. Research on DDoS Attack Defense System Based on Flowcleaning Strategy[D]. Xi’an: Xidian University, 2018. |
| 张哲. 基于流量清洗策略的DDoS攻击防御系统研究[D]. 西安: 西安电子科技大学, 2018. | |
| [19] | ZHANG Qian. Exploration and Practice of Traffic Analysis Technology in Network Security Confrontation[J]. Netinfo Security, 2020(S2): 114-117. |
| 张倩. 流量分析技术在网络安全对抗上的探索实践[J]. 信息网络安全, 2020(S2): 114-117. | |
| [20] | LIU Tao, YIN Sheng. Detection and Identification of DDoS Attacks Based on Cross Entropy in SDN Environment[J]. Computer Application and Software, 2021, 38(2): 328-333. |
| 刘涛, 尹胜. SDN环境中基于交叉熵的分阶段DDoS攻击检测与识别[J]. 计算机应用与软件, 2021, 38(2): 328-333. |
| [1] | 问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137. |
| [2] | 张长琳, 仝鑫, 佟晖, 杨莹. 面向网络安全领域的大语言模型技术综述[J]. 信息网络安全, 2024, 24(5): 778-793. |
| [3] | 杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410. |
| [4] | 金志刚, 陈旭阳, 武晓栋, 刘凯. 增量式入侵检测研究综述[J]. 信息网络安全, 2024, 24(12): 1819-1830. |
| [5] | 李娇, 张玉清, 吴亚飚. 面向网络安全关系抽取的大语言模型数据增强方法[J]. 信息网络安全, 2024, 24(10): 1477-1483. |
| [6] | 何开宇, 王彬, 于哲, 陈方. ARP欺骗攻击与硬件防御研究[J]. 信息网络安全, 2024, 24(10): 1604-1610. |
| [7] | 付静. 水利关键信息基础设施安全保护探索与实践[J]. 信息网络安全, 2023, 23(8): 121-127. |
| [8] | 孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6): 104-110. |
| [9] | 王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6): 11-21. |
| [10] | 李冬, 于俊清, 文瑞彬, 谢一丁. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28. |
| [11] | 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. |
| [12] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [13] | 孙鹏宇, 谭晶磊, 李晨蔚, 张恒巍. 基于时间微分博弈的网络安全防御决策方法[J]. 信息网络安全, 2022, 22(5): 64-74. |
| [14] | 金波, 唐前进, 唐前临. CCF计算机安全专业委员会2022年网络安全十大发展趋势解读[J]. 信息网络安全, 2022, 22(4): 1-6. |
| [15] | 陈妍, 韦湘, 陆臻. 云计算环境下网络安全产品检测方法研究[J]. 信息网络安全, 2022, 22(12): 1-6. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||