信息网络安全 ›› 2022, Vol. 22 ›› Issue (8): 44-54.doi: 10.3969/j.issn.1671-1122.2022.08.006
基于前后端关联性分析的固件漏洞静态定位方法
刘翎翔1,2, 潘祖烈1,2( ), 李阳1,2, 李宗超1,2
), 李阳1,2, 李宗超1,2
- 1.国防科技大学电子对抗学院,合肥 230037
2.网络空间安全态势感知与评估安徽省重点实验室,合肥 230037
-
收稿日期:2022-05-29出版日期:2022-08-10发布日期:2022-09-15 -
通讯作者:潘祖烈 E-mail:panzulie17@nudt.edu.cn -
作者简介:刘翎翔(1998—),男,湖南,硕士研究生,主要研究方向为网络空间安全|潘祖烈(1976—),男,安徽,教授,博士,主要研究方向为网络空间安全。|李阳(1990—),男,河北,讲师,硕士,主要研究方向为网络空间安全|李宗超(2000—),男,云南,主要研究方向为网络空间安全 -
基金资助:国家重点研发计划(2021YFB3100500)
Firmware Vulnerability Static Localization Method Based on Front-End and Back-End Correlation Analysis
LIU Lingxiang1,2, PAN Zulie1,2( ), LI Yang1,2, LI Zongchao1,2
), LI Yang1,2, LI Zongchao1,2
- 1. College of Electronic Engineering, National University of Defense Technology, Hefei 230037, China
2. Anhui Province Key Laboratory of Cyberspace Security Situation Awareness and Evaluation, Hefei 230037, China
-
Received:2022-05-29Online:2022-08-10Published:2022-09-15 -
Contact:PAN Zulie E-mail:panzulie17@nudt.edu.cn
摘要:
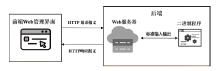
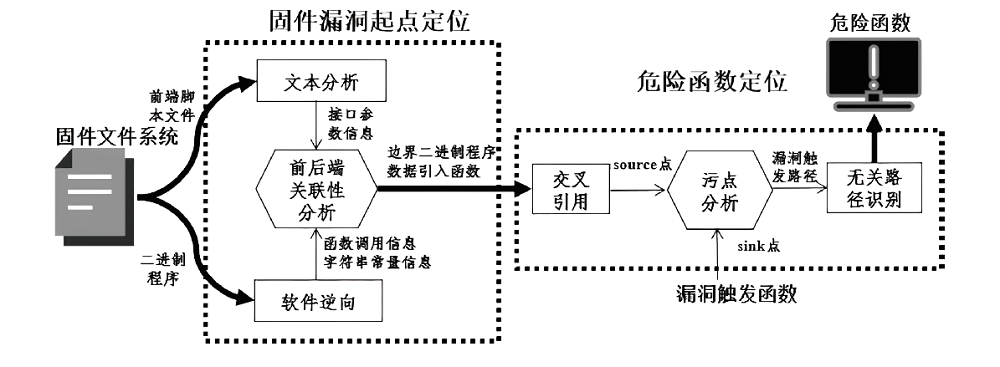
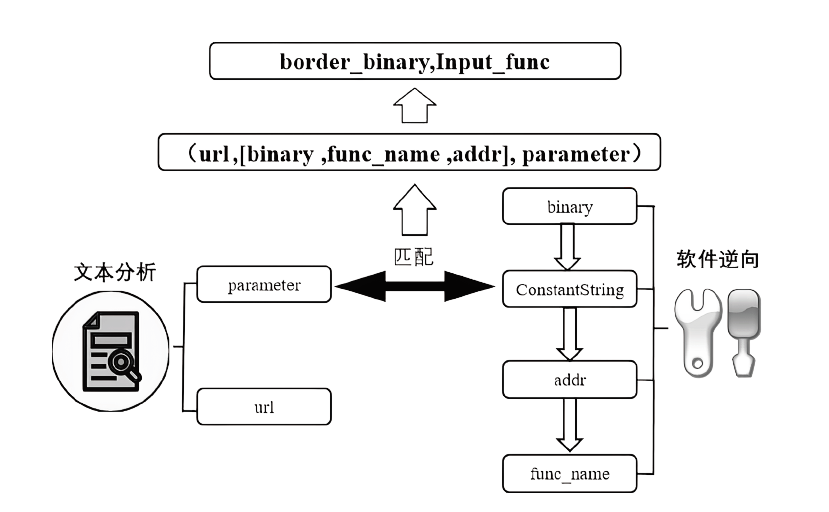
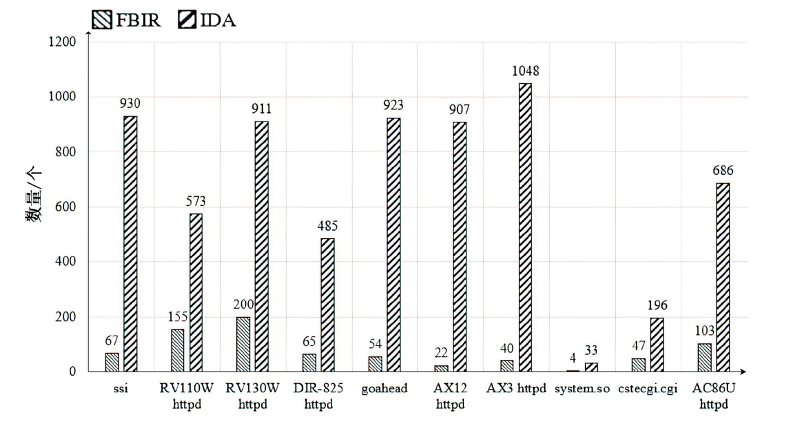
目前大多数物联网设备通过Web服务接口进行远程管理,利用Web服务漏洞发起攻击成为当前物联网设备安全面临的主要威胁之一。文章提出一种针对物联网设备Web服务漏洞的静态挖掘方法,首先基于前端脚本文件与边界二进制程序之间的关联性特征,通过对前后端文件进行关联分析,识别固件中的边界二进制程序,确定在边界二进制程序中针对Web输入数据的起始处理位置。然后利用污点分析技术判断输入数据是否会被漏洞触发函数处理,定位程序中的危险函数区域。最后实现固件漏洞静态方法的原型系统FBIR,并对10款固件进行实验,通过定位危险函数的方式验证45个已知漏洞并挖掘出12个零日漏洞。在漏报率只有14.9%的基础上,与传统人工分析的方法对比,文章所提方法将程序函数分析范围平均缩小了86%。
中图分类号:
引用本文
刘翎翔, 潘祖烈, 李阳, 李宗超. 基于前后端关联性分析的固件漏洞静态定位方法[J]. 信息网络安全, 2022, 22(8): 44-54.
LIU Lingxiang, PAN Zulie, LI Yang, LI Zongchao. Firmware Vulnerability Static Localization Method Based on Front-End and Back-End Correlation Analysis[J]. Netinfo Security, 2022, 22(8): 44-54.
表3
关联性验证结果
| 设备名 | 数据引入函数 | 边界二进制程序 | 漏洞数据引入函数 | 漏洞 程序 | 漏报 情况 |
|---|---|---|---|---|---|
| RV110W | get_cgi nvram_get | httpd blink_diag_led boot_env | get_cgi | httpd | 无 |
| RV130W | sub_1D170 nvram_get | httpd blink_diag_led boot_env | sub_1D170 | httpd | 无 |
| DIR-825 | nvram_safe_get get_cgi | httpd rc | nvram_safe_get get_cgi | httpd | 无 |
| DIR-816 | websGetVar | goahead | websGetVar nvram_bufget | goahead | 有 |
| AX12 | sub_4151AC sub_425F70 sub_42B5AC | httpd | sub_4151AC | httpd | 无 |
| AX3 | websGetVar | httpd | websGetVar GetValue | httpd | 有 |
| A3100R | websGetVar | ipv6.so wan.so system.so | websGetVar | system.so | 无 |
| X5000R | websGetVar | cstecgi.cgi | websGetVar nvram_safe_get | cstecgi.cgi rc | 有 |
| TEW-827DRU | getenv | ssi | getenv query_vars safe_getenv | ssi | 有 |
| RT-AC86U | sub_1D0F0 nvram_get_int sub_1BDF4 sub_1BE38 nvram_get | httpd asus_sr asus_tty | sub_1BE38 | httpd | 无 |
表5
已知漏洞
| 设备 | 漏洞编号 |
|---|---|
| RV110W | CVE-2020-3331 |
| RV130W | CVE-2020-3145、CVE-2020-3146 |
| DIR-825 | CVE-2020-10216、CVE-2020-10213、CVE-2020-10214、CVE-2019-9122、CVE-2020-10215 |
| DIR-816 | CVE-2021-26810、CVE-2021-27113、CVE-2021-27114、CVE-2018-17068、CVE-2018-17066、CVE-2018-20305、CVE-2019-10039 |
| AX12 | CVE-2022-25561、CVE-2022-25560、CVE-2022-25556、CVE-2021-45391、CVE-2021-45392 |
| AX3 | CVE-2022-24163、CVE-2022-24162、CVE-2022-24160、CVE-2022-24159、CVE-2022-24157、CVE-2022-24155、CVE-2022-24154、CVE-2022-24153、CVE-2022-24151、CVE-2022-24152、CVE-2022-24144、CVE-2022-24143、CVE-2022-24162、CVE-2022-24145、CVE-2022-24147、CVE-2022-24149 |
| A3100R | CVE-2021-44246、CVE-2021-44247 |
| TEW-827DRU | CVE-2020-14076、CVE-2020-14079、CVE-2020-14080、CVE-2020-14077、CVE-2020-14078 |
| X5000R | CVE-2021-45738、CVE-2021-45733 |
表6
已公开漏洞成果
| 编号 | 设备 | 参数名 | 边界二进制程序 | 数据引入 函数 | 漏洞触发 函数 |
|---|---|---|---|---|---|
| CVE-2021- 1360 | RV110W | guest_new_pwdguest_name | httpd | get_cgi | sprintf |
| RV130W | sub_1D170 | ||||
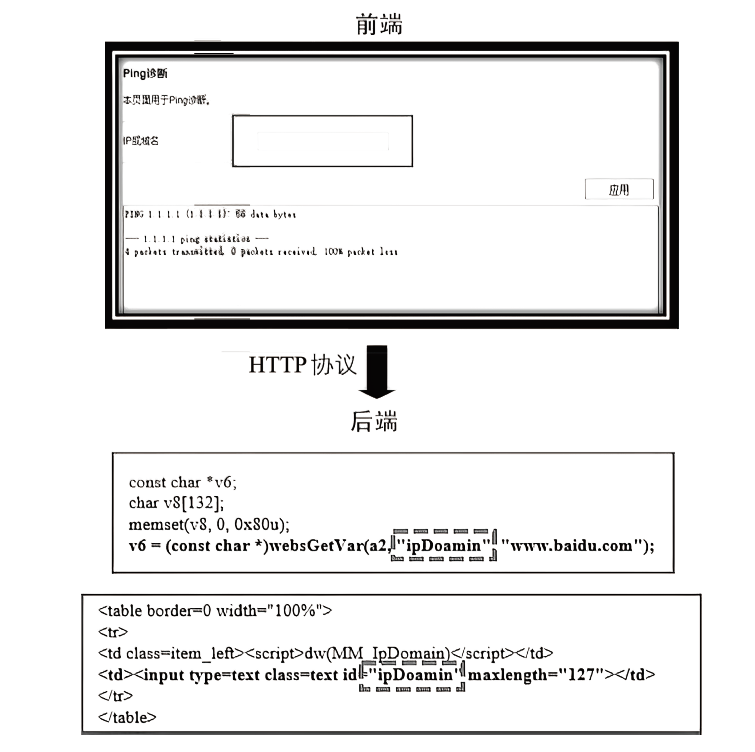
| CNNVD- 202112-953 | A3100R | ipDoamin | system.so | websGetVar | CsteSystem |
| CNNVD- 202112-954 | A3100R | hostTime | system.so | websGetVar | CsteSystem |
| CNNVD- 202112-2688 | X5000R | hostName | cstecgi.cgi | websGetVar | doSystem |
| [1] | YU Yingchao, CHEN Zuoning, GAN Shuitao, et al. Research on the Technologies of Security Analysis Technologies on the Embedded Device Firmware[J]. Chinese Journal of Computers, 2021, 44(5): 859-881. |
| 于颖超, 陈左宁, 甘水滔, 等. 嵌入式设备固件安全分析技术研究[J]. 计算机学报, 2021, 44(5): 859-881. | |
| [2] | CHEN D D, EGELE M, WOO M, et al. Towards Automated Dynamic Analysis for Linux-Based Embedded Firmware[EB/OL]. (2016-01-01)[2022-03-22]. https://www.researchgate.net/publication/316904631_Towards_Automated_Dynamic_Analysis_for_Linux-based_Embedded_Firmware. |
| [3] | KIM M, KIM D, KIM E, et al. FirmAE: Towards Large-Scale Emulation of IoT Firmware for Dynamic Analysis[C]//ACM. Annual Computer Security Applications Conference (ACSAC’20). New York: ACM, 2020: 733-745. |
| [4] | ZHENG Yaowen, DAVANIAN A, YIN Heng, et al. FIRM-AFL: High-Throughput Greybox Fuzzing of IoT Firmware via Augmented Process Emulation[C]//USENIX. 28th USENIX Security Symposium. Berkeley: USENIX, 2019: 1099-1114. |
| [5] | CNCERT/CC, NSFOCUS. 2020 IoT Security Annual Report[EB/OL]. (2021-07-05)[2022-04-08]. https://www.nsfocus.com.cn/html/2021/134_0705/158. html. |
| 国家互联网应急中心,绿盟科技. 2020物联网安全年报[EB/OL]. (2021- 07-05)[ 2022-04-08]. https://www.nsfocus.com.cn/html/2021/134_0705/158. html. | |
| [6] | CHENG Kai, LI Qiang, WANG Lei, et al. DTaint: Detecting the Taint-Style Vulnerability in Embedded Device Firmware[C]//IEEE. 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York: IEEE, 2018: 430-441. |
| [7] | SHOSHITAISHVILI Y, WANG Ruoyu, SALLS C, et al. SOK: (State of ) the Art of War: Offensive Techniques in Binary Analysis[C]//IEEE. 2016 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2016: 138-157. |
| [8] | ZHU Lipeng, FU Xiaotong, YAO Yao, et al. FIoT: Detecting the Memory Corruption in Lightweight IoT Device Firmware[C]//IEEE. 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2019: 248-255. |
| [9] | REDINI N, MACHIRY A, WANG Ruoyu, et al. KARONTE: Detecting Insecure Multi-Binary Interactions in Embedded Firmware[C]//IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1544-1561. |
| [10] | CHEN Libo, WANG Yanhao, CAI Quanpu, et al. Sharing More and Checking Less: Leveraging Common Input Keywords to Detect Bugs in Embedded Systems[C]//USENIX. 30th USENIX Security Symposium. Berkeley: USENIX, 2021: 303-319. |
| [11] | WANG Dong, ZHANG Xiaosong, CHEN Ting, et al. Discovering Vulnerabilities in COTS IoT Devices through Blackbox Fuzzing Web Management Interface[EB/OL].(2019-11-04)[2022-03-10]. https://dl.acm.org/doi/10.1155/2019/5076324. |
| [12] | WANG Lei, LI Feng, LI Lian, et al. Principle and Practice of Taint Analysis[J]. Journal of Software, 2017, 28(4): 860-882. |
| 王蕾, 李丰, 李炼, 等. 污点分析技术的原理和实践应用[J]. 软件学报, 2017, 28(4): 860-882. | |
| [13] | DAI Zhonghua, FEI Yongkang, ZHAO Bo, et al. Research on the Localization of Firmware Vulnerability Based on Stain Tracking[J]. Journal of Shandong University(Natural Science), 2016, 51(9): 41-46. |
| 戴忠华, 费永康, 赵波, 等. 基于污点跟踪的固件漏洞定位研究[J]. 山东大学学报(理学版), 2016, 51(9): 41-46. | |
| [14] | ZHAO Jian, WANG Rui, LI Siqi. Research on Smart Home Vulnerability Mining Technology Based on Taint Analysis[J]. Netinfo Security, 2018, 18(6): 36-44. |
| 赵健, 王瑞, 李思其. 基于污点分析的智能家居漏洞挖掘技术研究[J]. 信息网络安全, 2018, 18(6): 36-44. | |
| [15] | CELIK Z B, BABUN L, SIKDER A K, et al. Sensitive Information Tracking in Commodity IoT[C]//USENIX. 27th USENIX Security Symposium. Berkeley: USENIX, 2018: 1687-1704. |
| [1] | 张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7. |
| [2] | 刘芹, 张标, 涂航. 基于twisted Edwards曲线的无证书盲签名方案[J]. 信息网络安全, 2022, 22(8): 19-25. |
| [3] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [4] | 伍麟珺, 刘洋, 袁涛, 胡玉鹏. 抗温度干扰的STT-MRAM随机数生成器及其安全性分析[J]. 信息网络安全, 2022, 22(8): 36-43. |
| [5] | 高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8): 55-63. |
| [6] | 魏松杰, 李成豪, 沈浩桐, 张文哲. 基于深度森林的网络匿名流量检测方法研究与应用[J]. 信息网络安全, 2022, 22(8): 64-71. |
| [7] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [8] | 佟晓筠, 苏煜粤, 张淼, 王翥. 基于混沌和改进广义Feistel结构的轻量级密码算法[J]. 信息网络安全, 2022, 22(8): 8-18. |
| [9] | 顾兆军, 刘婷婷, 高冰, 隋翯. 基于GAN-Cross的工控系统类不平衡数据异常检测[J]. 信息网络安全, 2022, 22(8): 81-89. |
| [10] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [11] | 杨婉霞, 陈帅, 管磊, 杨忠良. 宋词自动生成的信息隐藏算法[J]. 信息网络安全, 2022, 22(7): 46-54. |
| [12] | 于成丽, 张阳, 贾世杰. 云环境中数据安全威胁与防护关键技术研究[J]. 信息网络安全, 2022, 22(7): 55-63. |
| [13] | 张梦杰, 王剑, 黄恺杰, 杨刚. 一种基于字节波动特征的ROP流量静态检测方法[J]. 信息网络安全, 2022, 22(7): 64-72. |
| [14] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [15] | 傅志彬, 祁树仁, 张玉书, 薛明富. 基于稠密连接的深度修复定位网络[J]. 信息网络安全, 2022, 22(7): 84-93. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||