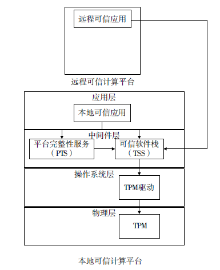
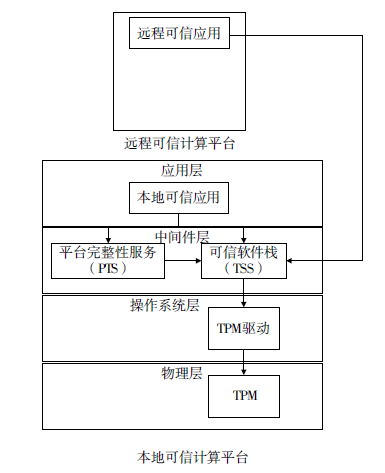
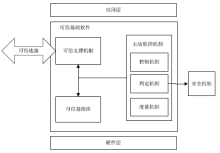
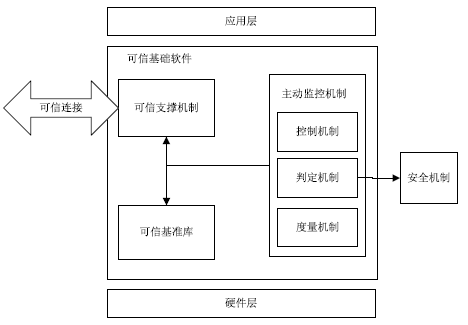
| [1] |
张耀祥. 云计算和虚拟化技术[J].计算机安全,2011,(5):80-82.
|
| [2] |
Michael Armbrust, Armando Fox,Rean Griffith, et al.A view of cloud computing[J].Communications of the ACM, 2010, 53(4) : 50-58.
|
| [3] |
Greg Gianforte.Multiple-Tenancy Hosted Applications: The Death and Rebirth of the Software Industry[EB/OL].RighNow Technologies,2005.
|
| [4] |
Wayne Jansen, Timothy Grance.Guidelines on Security and Privacy in Public Cloud Computing[S]2011.
|
| [5] |
Hashizume K, Rosado D G, Femádez-Medina E, et al. An analysis of security issues for cloud computing[J]. Journal of Internet Services and Applications2013, 4 (5) : l-13.
|
| [6] |
马威,韩臻,成阳. 可信云计算中的多级管理机制研究[J]. 信息网络安全,2015,(7):20-25.
|
| [7] |
张志勇,常亚楠,王剑,等.云计算环境下的可信接入安全协议研究进展[J].网络安全技术与应用,2013,(08):112-116.
|
| [8] |
Trusted Computing Group.TCG Architecture Overview, Version 1.4[EB/OL]..
|
| [9] |
李刚. 创新驱动构筑网络强国安全保障——沈昌祥院士谈技术可信计算的创新与发展[J].中国信息安全,2015,(2):46-51.
|
| [10] |
T.C.P.Alliance.TCPA design philosophies and concepts (version 1.0) [EB/OL]. https://www.trustedcomputinggroup.org,2001.
|
| [11] |
Santos N,Gummadi K P, Rodrigues R.Towards trusted cloud computing[C]//Proc.of the 2009 Workshop on Hot Topics in Cloud Computing.Berkeley: USENIX Association, 2009.
|
| [12] |
Sadeghi A R,Schneider T,Winandy M.Token-based cloud computing: secure outsourcing of data and arbitrary computations with lower latency[C]//Proceedings of the 3rd international conference on Trust and trustworthy computing. Berlin: Springer-Verlag,2010:417-429.
|
| [13] |
王刚. 一种基于SDN技术的多区域安全云计算架构研究[J]. 信息网络安全,2015,(9):20-24.
|
| [14] |
王惠莅,杨晨,杨建军.美国云计算安全标准跟踪及研究[R].中国:中国电子技术标准化研究院信息安全研究中心,2012.
|
| [15] |
侯晓峰,媵腾.云计算参考架构在央企信息化中的应用[J],信息技术与标准化,2013,(3):26-29,74.
|
| [16] |
郑周,张大军,李运发. 云计算中面向数据存储的安全访问控制机制[J]. 信息网络安全,2015,(9):221-226.
|
| [17] |
沈昌祥. 云可信架构研究报告[R].北京:中国工程院咨询研究项目,2012.
|
| [18] |
张建. 云计算服务等级协议(SLA)研究[J].电信网技术,2012,(2):2.
|
| [19] |
宋好好. 云计算信息系统信息安全等级保护测评关键技术研究[J]. 信息网络安全,2015,(9):167-169.
|
| [20] |
Kandukuri B R, Ramakrishna P V, Rakshit A.Cloud security issues[C]//Proc. of the 2009 IEEE International Conference on Services Computing. Piscataway: IEEE Computer Society, 2009: 517-520.
|
| [21] |
De Chaves S A, Westphall C B, Lamin F R.SLA perspective in security management for cloud computing[C]//Proc.of the 6th International Conference on Networking and Services.Piscataway:IEEE Computer Society,2010:212-217.
|