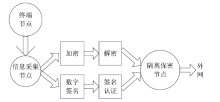
| [1] |
王景中,凌晨. 基于节点认证的物联网感知层信息安全传输机制的研究[J]. 信息网络安全,2014,(2):53-57.
|
| [2] |
笪林梅. 物联网感知层RFID和WSN信息安全技术研究[J]. 南京工业职业技术学院学报,2014,(1):8-11.
|
| [3] |
袁明山. 面向特殊行业物联网监测平台可信度的提高与实现研究[D]. 广州:华南理工大学,2012.
|
| [4] |
张晓惠,林柏钢. 基于平衡二叉决策树SVM算法的物联网安全研究[J]. 信息网络安全,2015,(8):20-25.
|
| [5] |
陈雷. 物联网中认证技术与密钥管理的研究[D]. 长沙:中南大学,2013.
|
| [6] |
袁艳祥. 基于身份的密钥管理研究[D]. 杭州:杭州电子科技大学,2014.
|
| [7] |
王沂,韩广国,李慧智. 无线网络中可证安全的移动用户密钥交换协议[J]. 信息网络安全,2015,(3):54-58.
|
| [8] |
胡向东,王凯. 物联网感知层安全簇维护方法[J]. 重庆:重庆邮电大学学报(自然科学版),2015,(1):103-110.
|
| [9] |
闫韬. 物联网隐私保护及密钥管理机制中若干关键技术研究[D]. 北京:北京邮电大学,2012.
|
| [10] |
RAY B R, ABAWAJY J, CHOWDHURY M.Scalable RFID security framework and protocol supporting Internet of Things[J]. Computer Networks, 2014, 67(10):89-103.
|
| [11] |
马骏. 物联网感知环境分层访问控制机制研究[D]. 西安:西安电子科技大学,2014.
|
| [12] |
牛春诚. 物联网安全与隐私问题研究[D]. 长春:长春工业大学,2013.
|
| [13] |
范月,许晋,高宇童. eID移动身份认证系统的研究与实现[J]. 信息网络安全,2015,(3):48-53.
|
| [14] |
Liu C, Yang C, Zhang X, et al.External integrity verification for outsourced big data in cloud and IoT: A big picture[J]. Future Generation Computer Systems, 2015, (49): 58-67.
|
| [15] |
高浩文. 基于信任的物联网安全路由技术研究[D]. 沈阳:辽宁大学,2013.
|
| [16] |
朱艳. 面向物联网的身份认证和访问控制的研究[D]. 南京:南京邮电大学,2014.
|
| [17] |
聂金慧,苏红旗. 物联网位置数据安全策略研究[J]. 信息网络安全,2014,(6):6-10.
|
| [18] |
刘文懋. 物联网感知环境安全机制的关键技术研究[D]. 哈尔滨:哈尔滨工业大学,2013.
|
| [19] |
郝方超,王海春. 物联网安全中基于博弈论的BP-1模型研究[J]. 数字技术与应用,2014,(8):195-196.
|
| [20] |
马骏,郭渊博,马建峰,等. 物联网感知层基于资源分层的多用户访问控制方案[J]. 电子学报,2014,(1):28-35.
|
| [21] |
RAZA S, DUQUENNOY S, HÖGLUND J, et al. Secure communication for the Internet of Things -a comparison of link-layer security and IPsec for 6LoWPAN[J]. Security & Communication Networks, 2014, 7(12): 2654-2668.
|
| [22] |
马纪丰,梁浩. 物联网感知层信息安全分析与建议[J]. 现代电子技术,2012,(19):76-78.
|
| [23] |
崔振山,马春光,李迎涛. 物联网感知层的安全威胁与安全技术[J]. 保密科学技术,2012,(11):61-65.
|