信息网络安全 ›› 2015, Vol. 15 ›› Issue (3): 19-22.doi: 10.3969/j.issn.1671-1122.2015.03.004
基于微聚集的a-多样性k-匿名大数据隐私保护
- 中国科学技术大学计算机学院,安徽合肥230027
-
收稿日期:2015-01-21出版日期:2015-03-10发布日期:2015-05-08 -
作者简介:作者简介: 程亮(1991-),男,安徽,硕士研究生主要研究方向:信息安全;;蒋凡(1956-),安徽硕士,教授,主要研究方向:计算机网络,协议与软件测试,信息安全。
-
基金资助:高等学校博士学科点专项科研基金[201134021206];安徽省自然科学基金[1208085QF112];安徽省高等学位优秀青年人才基金[2012SQRL001ZD];中央高校基本科研业务费专项资金[WK2101020004,WK011000007]
a-diversity and k-anonymity Big Data Privacy Preservation Based On Micro-aggregation
- School of Computer Science and Technology, University of Science and Technology of China, Hefei Anhui 230027, China
-
Received:2015-01-21Online:2015-03-10Published:2015-05-08
摘要:
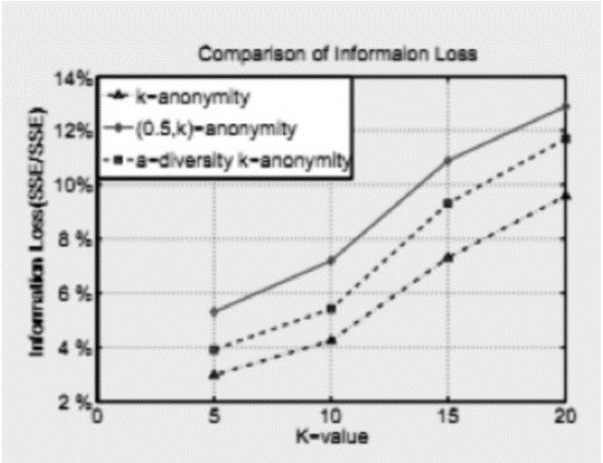
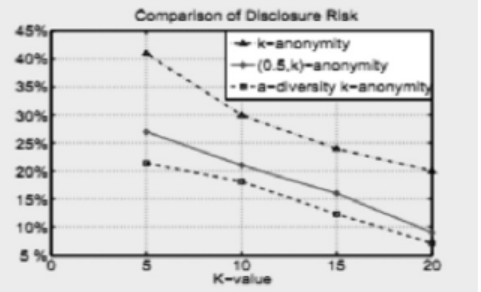
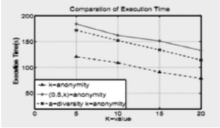
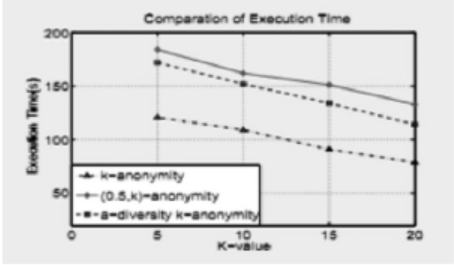
基于敏感信息的数据发布面临的主要问题在于如何保证数据的有用性和隐私保护。匿名化是一个很好的方法,目前有多种匿名化模型。然而大多数的模型主要侧重于使用预先定义的参数为整个数据集提供无差别的隐私保护,这并不能适应不同个体对不同敏感属性的多样性保护需求。基于此,文章提出了一种满足敏感信息的多样性非相关约束的a-多样性 k-匿名化模型;同时,设计了一个改进的微聚集算法的框架替代了传统的泛化/抑制实现匿名化。使用这个框架,能够提高数据的有用性并降低隐私泄露的风险。通过在真实数据集上进行多次试验验证了此方案的有效性。
中图分类号:
引用本文
程亮, 蒋凡. 基于微聚集的a-多样性k-匿名大数据隐私保护[J]. 信息网络安全, 2015, 15(3): 19-22.
CHENG Liang, JIANG Fan. a-diversity and k-anonymity Big Data Privacy Preservation Based On Micro-aggregation[J]. Netinfo Security, 2015, 15(3): 19-22.
| [1] | Josep Domingo-Ferrer, Antoni Mart´nez-Ballest é,Josep Maria Mateo-Sanz, et al. Efficient multivariate data-oriented microaggregation. The VLDB Journal, 15(4):355-369, 2006. |
| [2] | Josep Domingo-Ferrer and Josep Maria Mateo-Sanz.Practicaldata-oriented microaggrega-tion for statistical disclosure control. Knowledge and Data Engineering, IEEE Transactionson, 14(1):189-201, 2002. |
| [3] | Josep Domingo-Ferrer, Agusti Solanas,Antoni Martinez-Balleste.Privacy in statisticaldatabases: k-anonymity through microaggregation. In GrC, pages 774-777, 2006. |
| [4] | Raymond Chi-Wing Wong, Jiuyong Li, Ada Wai-Chee Fu,Ke Wang.(a,k)-anonymity:an enhanced k-anonymity model for privacy preserving data publishing. In Proceedings of the 12th ACM SIGKDD international conference on Knowledge discovery and data mining,pages 754-759. ACM, 2006. |
| [5] | Bugra Gedik and Ling Liu. Protecting location privacy with personalized k-anonymity:Architecture and algorithms. Mobile Computing, IEEE Transactions on, 7(1):1-18, 2008 . |
| [6] | Yabo Xu, Ke Wang, Benyu Zhang,Zheng Chen.Privacy-enhancing personalized websearch. In Proceedings of the 16th international conference on World Wide Web, pages 591-600. ACM, 2007. |
| [7] | Mingxuan Yuan, Lei Chen,Philip S Yu.Personalized privacy protection in social networks. Proceedings of the VLDB Endowment, 4(2):141-150, 2010. |
| [8] | Ashwin Machanavajjhala, Daniel Kifer, Johannes Gehrke,Muthuramakrishnan Venkita-subramaniam. l-diversity: Privacy beyond k-anonymity. ACM Transactions on KnowledgeDiscovery from Data (TKDD), 1(1):3, 2007. |
| [9] | Jordi Soria-Comas, Josep Domingo-Ferrer, David Sánchez,Sergio Mart´ınez.Enhancing data utility in differential privacy via microaggregation-based k-anonymity. The VLDBJournal, pages 1-24, 2014. |
| [10] | Latanya Sweeney. k-anonymity: A model for protecting privacy.International Journal ofUncertainty, Fuzziness and Knowledge-Based Systems, 10(05):557-570, 2002. |
| [11] | Ninghui Li, Tiancheng Li,Suresh Venkatasubramanian. t-closeness: Privacy beyondk-anonymity and l-diversity. In ICDE, volume 7, pages 106-115, 2007. |
| [1] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [2] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [3] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [4] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [5] | 董云云, 朱玉玲, 姚绍文. 基于改进U-Net和混合注意力机制的高质量全尺寸图像隐写方法[J]. 信息网络安全, 2024, 24(7): 1050-1061. |
| [6] | 周书丞, 李杨, 李传荣, 郭璐璐, 贾辛洪, 杨兴华. 基于上下文的异常根因算法[J]. 信息网络安全, 2024, 24(7): 1062-1075. |
| [7] | 任昌禹, 张玲, 姬航远, 杨立群. 基于预训练模型和中英文威胁情报的TTP识别方法研究[J]. 信息网络安全, 2024, 24(7): 1076-1087. |
| [8] | 蔡满春, 席荣康, 朱懿, 赵忠斌. 一种Tor网站多网页多标签指纹识别方法[J]. 信息网络安全, 2024, 24(7): 1088-1097. |
| [9] | 项慧, 薛鋆豪, 郝玲昕. 基于语言特征集成学习的大语言模型生成文本检测[J]. 信息网络安全, 2024, 24(7): 1098-1109. |
| [10] | 申秀雨, 姬伟峰. 考虑安全的边—云协同计算卸载成本优化[J]. 信息网络安全, 2024, 24(7): 1110-1121. |
| [11] | 赵新强, 范博, 张东举. 基于威胁发现的APT攻击防御体系研究[J]. 信息网络安全, 2024, 24(7): 1122-1128. |
| [12] | 问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137. |
| [13] | 刘一丹, 马永柳, 杜宜宾, 程庆丰. 一种车联网中的无证书匿名认证密钥协商协议[J]. 信息网络安全, 2024, 24(7): 983-992. |
| [14] | 罗铭, 詹骐榜, 邱敏蓉. 面向V2I通信的异构跨域条件隐私保护环签密方案[J]. 信息网络安全, 2024, 24(7): 993-1005. |
| [15] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||