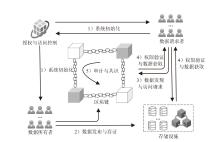
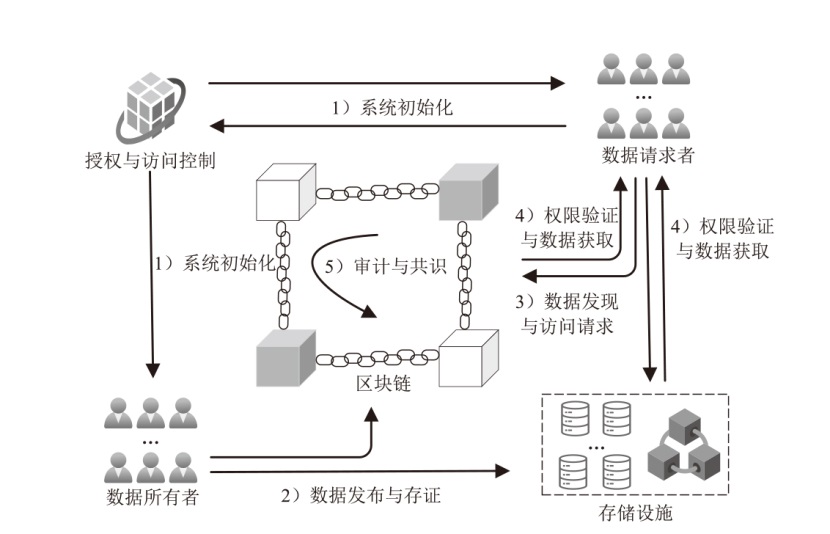
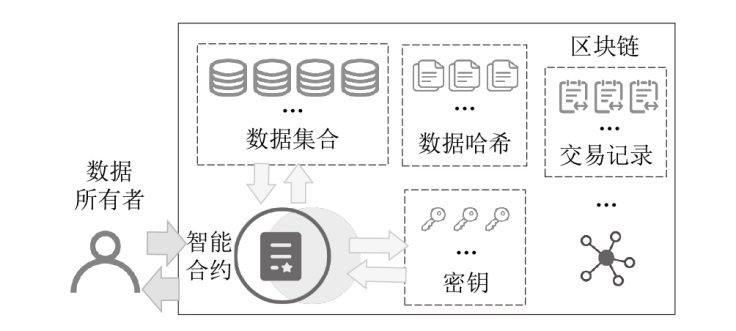
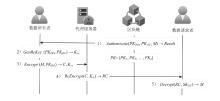
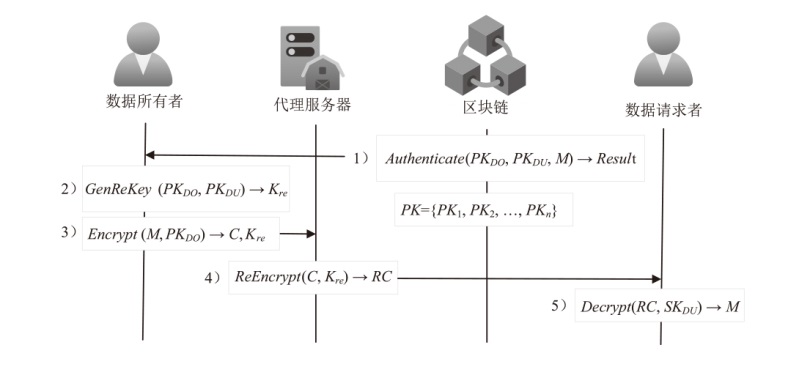
Netinfo Security ›› 2026, Vol. 26 ›› Issue (1): 1-23.doi: 10.3969/j.issn.1671-1122.2026.01.001
Previous Articles Next Articles
A Review of Data Security Sharing Based on Blockchain
GUO Yi1,2, LI Xuqing1( ), ZHANG Zijiao3, ZHANG Hongtao3, ZHANG Liancheng2, ZHANG Xiangli3,4
), ZHANG Zijiao3, ZHANG Hongtao3, ZHANG Liancheng2, ZHANG Xiangli3,4
- 1. School of Cyber Science and Engineering, Zhengzhou University, Zhengzhou 450002, China
2. School of Cyberspace Security, Cyberspace Force Information Engineering University, Zhengzhou 450001, China
3. Network Center of Zhengzhou University, Zhengzhou 450002, China
4. School of Management, Northwest Normal University, Lanzhou 730070, China
-
Received:2025-07-22Online:2026-01-10Published:2026-02-13
CLC Number:
Cite this article
GUO Yi, LI Xuqing, ZHANG Zijiao, ZHANG Hongtao, ZHANG Liancheng, ZHANG Xiangli. A Review of Data Security Sharing Based on Blockchain[J]. Netinfo Security, 2026, 26(1): 1-23.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2026.01.001
| 存储 设施 | 文献 | 核心思想 | 容灾性 | 扩展性 | 上链时延 /ms | 应用 场景 | 区块链配置 | ||
|---|---|---|---|---|---|---|---|---|---|
| 多链 | 类型 | 实现 | |||||||
| 云存储 | 文献[ | 存储文件的Merkle哈希树及群签名 | 中 | 高 | — | — | × | 私有链 | Truffle |
| 文献[ | 存储密文和标签并支持部分密文更新 | 中 | 高 | — | 物联网 | × | 私有链 | Substrate | |
| 文献[ | 使用集中式云核对数据交易 | 中 | 高 | — | 物联网 | × | — | — | |
| 文献[ | 共享数据分层加密并存储 | 中 | 高 | — | — | × | — | — | |
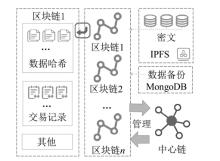
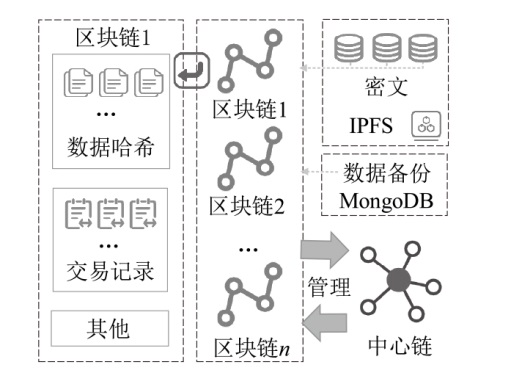
| IPFS | 文献[ | 多区块链、IPFS和MongoDB联合存储 | 高 | 中 | 2073 | 电力 网络 | √ | 联盟链 | Hyperledger |
| 文献[ | 双链隔离用户信息、IPFS存储共享数据 | 高 | 中 | 1045 | — | √ | 联盟链 | Hyperledger | |
| 文献[ | 私有IPFS集群与区块链联合存储 | 高 | 中 | — | 主数据管理 | × | 联盟链 | Hyperledger | |
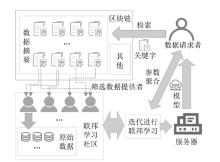
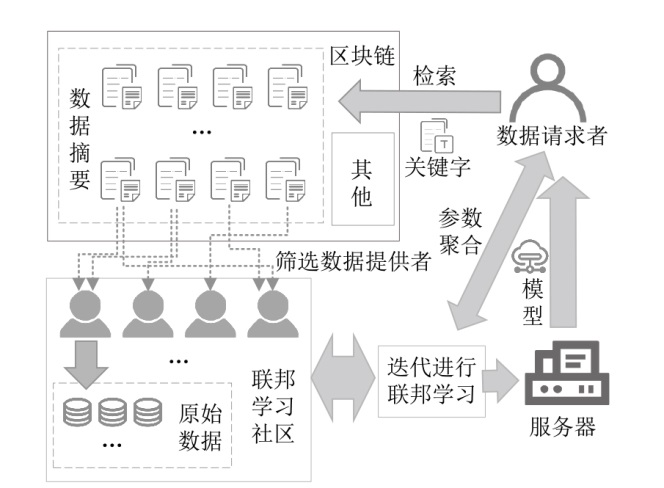
| 本地 存储 | 文献[ | 用户在本地进行联邦学习间接共享数据 | 低 | 低 | — | — | × | 联盟链 | — |
| 文献[ | 采用本地服务器存储数据 | 低 | 低 | 279 | 医疗 系统 | √ | 私有和联盟链 | — | |
| 文献[ | 本地数据经隐私计算处理后再进行传输 | 低 | 低 | — | — | × | 联盟链 | — | |
| 类型 | 策略 | 文献 | 核心思想 | 细粒度 | 用户驱动 | 属性撤销 | 加密 开销 /ms | 解密开销 /ms | 应用 场景 |
|---|---|---|---|---|---|---|---|---|---|
| 基于密码学的访问控制 | 属性基加密 | 文献[ | 使用线性秘密共享矩阵制定的访问策略加密明文 | √ | × | × | — | — | — |
| 文献[ | 属性密钥加密分级对称密钥,不同权限解密不同级别的密钥 | √ | × | × | 101.2 | 26.4 | — | ||
| 文献[ | 用户属性变化时更新用户属性密钥 | √ | × | √ | 937.6 | 277.0 | 供应链 | ||
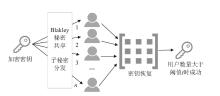
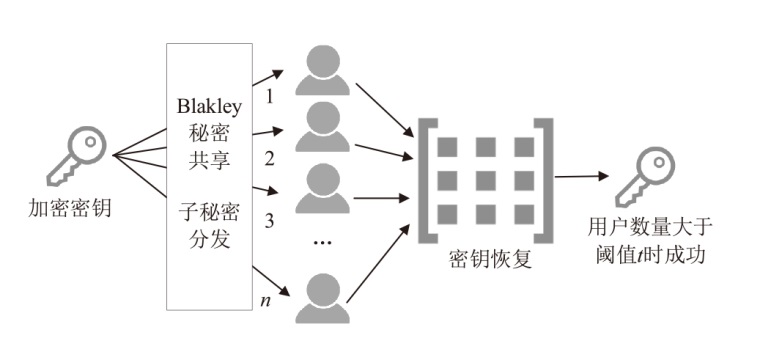
| 门限秘密共享 | 文献[ | 共享用户数量大于阈值t时恢复密钥 | × | × | × | — | — | — | |
| 公钥密码学 | 文献[ | 有权限直接解密,无权限代理重加密后 解密 | × | × | × | 607.0 | 279.0 | 医疗 | |
| 文献[ | 基于公钥、环公钥的加密和签名 | × | × | × | 117.0 | 240.0 | 物联网 | ||
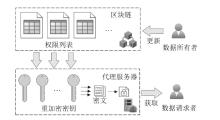
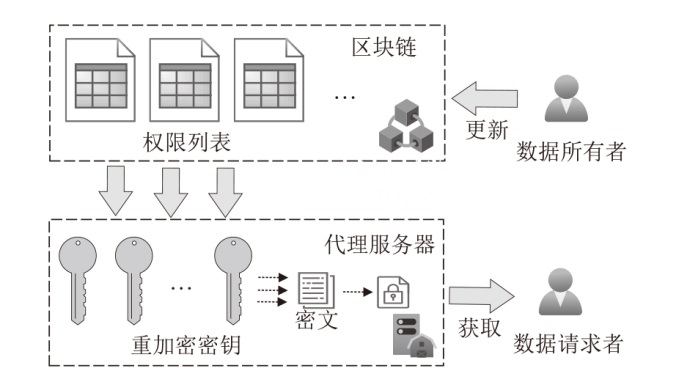
| 基于区块链的访问控制 | 区块链存证 | 文献[ | 权限列表重加密密钥动态 关联 | × | √ | √ | 158.1 | 40.9 | — |
| 文献[ | 模糊属性集保护用户隐私 | √ | × | × | 1220.0 | 446.0 | — | ||
| 文献[ | 私有链共享和联盟链共享、根据身份目的细分权限 | × | √ | × | 32.0 | 41.0 | 医疗 | ||
| 智能 合约 | 文献[ | 多权限属性加密与智能合约结合 | √ | √ | √ | 159.0 | 48.0 | — | |
| 文献[ | 区块链密钥管理、智能合约验证权限 | × | × | × | — | — | — | ||
| 文献[ | 分层属性加密与智能合约 结合 | √ | √ | × | 834.0 | 50.0 | 物联网 |
| 类型 | 文献及 方法 | 数据安全 机制 | 匿名性 | 隐私性 | 可追溯性 | 不可抵赖性 | 应用 场景 |
|---|---|---|---|---|---|---|---|
| 身份匿名与验证技术 | 组签名[ | 组签名、匿名数据共享 | √ | × | √ | √ | 群体数据共享 |
| 环签名[ | 环签名派生的公钥加密和知识签名 | √ | × | × | √ | 物联网 | |
| 部分 盲签名[ | 一次性公钥地址和盲化支付信息 | × | √ | × | × | 物联网 | |
| 计算过程隐私技术 | 联邦 学习[ | 联邦学习、同态加密、间接数据共享 | √ | √ | × | × | — |
| 零知识 证明[ | 安全验证数据共享各方声明和真实性 | √ | √ | × | × | 医疗系统 | |
| 安全多方 计算[ | 多方联合计算、解决数据孤岛 问题 | × | √ | × | × | 金融数据共享 | |
| 可信执行环境[ | 代码和数据放入SGX中执行 | × | √ | √ | √ | — | |
| 数据内容隐私技术 | 差分 隐私[ | 本地差分隐私模糊敏感数据 | × | √ | × | × | — |
| 代理重 加密[ | 权限列表和重加密参数动态关联 | √ | × | × | × | 个人数据共享 | |
| 分布式密钥生成[ | 没有可信第三方的情况下生成密钥值 | × | √ | × | √ | 金融数据共享 | |
| 匿名密钥 生成[ | 用户和属性权威结构的协商生成密钥 | √ | × | × | × | 供应链信息共享 |
| [1] |
SHREE S, ZHOU Chen, BARATI M. Data Protection in Internet of Medical Things Using Blockchain and Secret Sharing Method[J]. The Journal of Supercomputing, 2024, 80(4): 5108-5135.
doi: 10.1007/s11227-023-05657-7 |
| [2] |
BYABAZAIRE J, OHARE G, DELANEY D. Data Quality and Trust: Review of Challenges and Opportunities for Data Sharing in IOT[J]. Electronics, 2020, 9(12): 2083-2104.
doi: 10.3390/electronics9122083 URL |
| [3] |
JIANG Shan, CAO Jiannong, WU Hanqing, et al. Privacy-Preserving and Efficient Data Sharing for Blockchain-Based Intelligent Transportation Systems[J]. Information Sciences, 2023, 635: 72-85.
doi: 10.1016/j.ins.2023.03.121 URL |
| [4] |
FENG Yawen, ZENG Shengke. Secure and Flexible Authorized Data Sharing for Smart Grid[J]. Peer-to-Peer Networking and Applications, 2024, 17(3): 1208-1224.
doi: 10.1007/s12083-024-01649-3 |
| [5] |
ROMAN R, LOPEZ J, MAMBO M. Mobile Edge Computing, Fog et al. : A Survey and Analysis of Security Threats and Challenges[J]. Future Generation Computer Systems, 2018, 78: 680-698.
doi: 10.1016/j.future.2016.11.009 URL |
| [6] |
ZENG Shiqin, HUO Ru, HUANG Tao, et al. Survey of Blockchain: Principle, Progress and Application[J]. Journal on Communications, 2020, 41(1): 134-151.
doi: 10.11959/j.issn.1000-436x.2020027 |
|
曾诗钦, 霍如, 黄韬, 等. 区块链技术研究综述:原理、进展与应用[J]. 通信学报, 2020, 41(1): 134-151.
doi: 10.11959/j.issn.1000-436x.2020027 |
|
| [7] | ZHOU Chao, REN Zhiyu. Research of Access Control Model Combined Attribute with Role[J]. Journal of Chinese Computer Systems, 2018, 39(4): 782-786. |
| 周超, 任志宇. 结合属性与角色的访问控制模型综述[J]. 小型微型计算机系统, 2018, 39(4): 782-786. | |
| [8] | BATRA G. Attribute-Based Access Control[M]. Heidelberg: Springer, 2024. |
| [9] |
SONG Rui, XIAO Bin, SONG Yubo, et al. A Survey of Blockchain-Based Schemes for Data Sharing and Exchange[J]. IEEE Transactions on Big Data, 2023, 9(6): 1477-1495.
doi: 10.1109/TBDATA.2023.3293279 URL |
| [10] | LUO Yuhan, LIU Mingzhe, WANG Jianping, et al. When Secure Data Sharing Meets Blockchain: Overview, Challenges and Future Prospects[C]// ACM. The 2022 4th International Conference on Blockchain Technology. New York: ACM, 2022: 1-8. |
| [11] |
FENG Tao, CHEN Liqiu, FANG Junli, et al. Blockchain Data Sharing Scheme Based on Localized Difference Privacy and Attribute-Based Searchable Encryption[J]. Journal on Communications, 2023, 44(5): 224-233.
doi: 10.11959/j.issn.1000-436x.2023103 |
|
冯涛, 陈李秋, 方君丽, 等. 基于本地化差分隐私和属性基可搜索加密的区块链数据共享方案[J]. 通信学报, 2023, 44(5): 224-233.
doi: 10.11959/j.issn.1000-436x.2023103 |
|
| [12] | YAO Yao, CEN Xingxing, LIU Yingqian, et al. Blockchain-Based Electronic Medical Record Security Sharing Scheme[C]// IEEE. 2023 45th Annual International Conference of the IEEE Engineering in Medicine & Biology Society (EMBC). New York: IEEE, 2023: 1-4. |
| [13] | DING Jiaxu, YAN Biwei, WANG Guijuan, et al. Blockchain-Aided Hierarchical Attribute-Based Encryption for Data Sharing[C]// Springer. International Conference on Wireless Algorithms, Systems, and Applications. Heidelberg: Springer, 2022: 364-376. |
| [14] | MA Baoluo, CHI Cheng, TIAN Juan, et al. Research on Data Security Sharing Mechanism and Application Based on Blockchain and Privacy Computing[C]// IEEE. 2022 4th International Academic Exchange Conference on Science and Technology Innovation (IAECST). New York: IEEE, 2022: 777-782. |
| [15] |
CHEN Yanru, LI Jingpeng, WANG Fan, et al. DS2PM: A Data-Sharing Privacy Protection Model Based on Blockchain and Federated Learning[J]. IEEE Internet of Things Journal, 2021, 10(14): 12112-12125.
doi: 10.1109/JIOT.2021.3134755 URL |
| [16] |
WU Tong, WANG Weijie, ZHANG Chuan, et al. Blockchain-Based Anonymous Data Sharing with Accountability for Internet of Things[J]. IEEE Internet of Things Journal, 2022, 10(6): 5461-5475.
doi: 10.1109/JIOT.2022.3222453 URL |
| [17] | LI Jinghan, SHEN Guohua, YANG Yang, et al. Secure Data Sharing Mechanism of Internet of Things Based on Blockchain[J]. Journal of Chinese Computer Systems, 2023, 44(8): 1812-1818. |
| 李井涵, 沈国华, 杨阳, 等. 结合区块链的物联网数据安全共享机制[J]. 小型微型计算机系统, 2023, 44(8): 1812-1818. | |
| [18] |
KHOWAJA S A, KHUWAJA P, DEV K, et al. A Secure Data Sharing Scheme in Community Segmented Vehicular Social Networks for 6G[J]. IEEE Transactions on Industrial Informatics, 2022, 19(1): 890-899.
doi: 10.1109/TII.2022.3188963 URL |
| [19] |
KANG Jiawen, XIONG Zehui, NIYATO D, et al. Securing Data Sharing from the Sky: Integrating Blockchains into Drones in 5G and Beyond[J]. IEEE Network, 2021, 35(1): 78-85.
doi: 10.1109/MNET.011.2000183 |
| [20] | LIU Yansong, XIA Qi, LI Zhu, et al. Research on Secure Data Sharing System Based on Blockchain[J]. Big Data Research, 2020, 6(5): 92-105. |
|
刘彦松, 夏琦, 李柱, 等. 基于区块链的链上数据安全共享体系研究[J]. 大数据, 2020, 6(5): 92-105.
doi: 10.11959/j.issn.2096-0271.2020046 |
|
| [21] | LIU Chenlei, XIANG Feng, SUN Zhixin. Multiauthority Attribute-Based Access Control for Supply Chain Information Sharing in Blockchain[J]. Security and Communication Networks, 2022, 2022(1): 1-18. |
| [22] | KESHTA I, AOUDNI Y, SANDHU M, et al. Blockchain Aware Proxy Re-Encryption Algorithm-Based Data Sharing Scheme[J]. Physical Communication, 2023, 58(1): 1-14. |
| [23] |
TAO Qi, CUI Xiaohui. B-FLACS: Blockchain-Based Flexible Lightweight Access Control Scheme for Data Sharing in Cloud[J]. Cluster Computing, 2023, 26(6): 3931-3941.
doi: 10.1007/s10586-022-03782-1 |
| [24] | ZHANG Jin, GU Fu, GU Xinjian, et al. Blockchain-Based Data Sharing Method for Multi-Value Chain Collaboration[J]. Computer Integrated Manufacturing Systems, 2024, 30(10): 3643-3657. |
| 张今, 顾复, 顾新建, 等. 基于区块链的多价值链协同数据共享方法[J]. 计算机集成制造系统, 2024, 30(10): 3643-3657. | |
| [25] | CHEN Lu, ZHANG Xin, SUN Zhixin. Blockchain Data Sharing Query Scheme Based on Threshold Secret Sharing[J]. Security and Communication Networks, 2022, 2022(1): 1-12. |
| [26] | HUANG Hui, CHEN Xiaofeng, WANG Jianfeng. Blockchain-Based Multiple Groups Data Sharing with Anonymity and Traceability[J]. Science China Information Sciences, 2020, 63(1): 1-13. |
| [27] | RAMANA K, MOHANA R M, REDDY C K K, et al. A Blockchain-Based Data-Sharing Framework for Cloud Based Internet of Things Systems with Efficient Smart Contracts[C]// IEEE. 2023 IEEE International Conference on Communications Workshops (ICC Workshops). New York: IEEE, 2023: 452-457. |
| [28] |
CHENG Xu, CHEN Fulong, XIE Dong, et al. Design of a Secure Medical Data Sharing Scheme Based on Blockchain[J]. Journal of Medical Systems, 2020, 44(2): 44-52.
doi: 10.1007/s10916-019-1481-4 |
| [29] |
LI Dagang, DU Rong, FU Yue, et al. Meta-Key: A Secure Data-Sharing Protocol under Blockchain-Based Decentralized Storage Architecture[J]. IEEE Networking Letters, 2019, 1(1): 30-33.
doi: 10.1109/LNET URL |
| [30] | QIN Sihang, DAI Weiqi, ZENG Haiyan, et al. Secure Sharing of Power Application Data Based on Blockchain[J]. Netinfo Security, 2023, 23(8): 52-65. |
| 覃思航, 代炜琦, 曾海燕, 等. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. | |
| [31] | LI Benyu, YANG Jing, WANG Yuxiang, et al. A Blockchain-Based Privacy-Preserving Data Sharing Scheme with Security-Enhanced Access Control[C]// IEEE. 2023 26th International Conference on Computer Supported Cooperative Work in Design (CSCWD). New York: IEEE, 2023: 825-830. |
| [32] | WANG Yiran, ZHANG Haisu, ZHANG Xiong, et al. Master Data Management Method Based on Blockchain and CP-ABE[C]// IEEE. 2022 10th International Conference on Information Systems and Computing Technology (ISCTech). New York: IEEE, 2022: 328-335. |
| [33] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain[J]. Netinfo Security, 2022, 22(2): 55-63. |
| 侯雨桐, 马兆丰, 罗守山. 基于区块链的数据安全共享与受控分发技术研究与实现[J]. 信息网络安全, 2022, 22(2): 55-63. | |
| [34] | SHEERAZ M M, MOZUMDER M A I, KHAN M O, et al. Blockchain System for Trustless Healthcare Data Sharing with Hyperledger Fabric in Action[C]// IEEE. 2023 25th International Conference on Advanced Communication Technology (ICACT). New York: IEEE, 2023: 437-440. |
| [35] | LIN Shaofeng, ZHANG Yao, ZHOU Yao, et al. Research on Anti-Leakage and Tampering Guarantee Strategy for Experimental Data Sharing Based on Blockchain[C]// IEEE. 2023 IEEE 3rd International Conference on Electronic Technology, Communication and Information (ICETCI). New York: IEEE, 2023: 277-281. |
| [36] | WANG Zhenqi, GUAN Shaopeng. A Blockchain-Based Traceable and Secure Data-Sharing Scheme[J]. PeerJ Computer Science, 2023, 9(1): 1-20. |
| [37] |
LIU Wei, BAI Xiaodan, SHE Wei, et al. Searchable Encrypted Data Sharing Scheme Based on Inverted Index[J]. Computer Engineering and Applications, 2023, 59(10): 270-279.
doi: 10.3778/j.issn.1002-8331.2201-0159 |
|
刘炜, 白晓丹, 佘维, 等. 基于倒排索引的可搜索加密数据共享方案[J]. 计算机工程与应用, 2023, 59(10): 270-279.
doi: 10.3778/j.issn.1002-8331.2201-0159 |
|
| [38] | WANG Xiaowei. Design and Implementation of a Data Sharing Model for Improving Blockchain Technology[J]. Advances in Multimedia, 2022, 2022(1): 1-8. |
| [39] | MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding a Revolutionary and Flawed Grand Experiment in Blockchain: The DAO Attack[J]. Journal of Cases on Information Technology (JCIT), 2019, 21(1): 19-32. |
| [40] | DERLER D, SAMELIN K, SLAMANIG D, et al. Fine-Grained and Controlled Rewriting in Blockchains: Chameleon-Hashing Gone Attribute-Based[C]// ISOC. The 26th Annual Network and Distributed System Security Symposium. Reston: Internet Society, 2019: 1-15. |
| [41] |
JIA Meng, CHEN Jing, HE Kun, et al. Redactable Blockchain from Decentralized Chameleon Hash Functions[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2771-2783.
doi: 10.1109/TIFS.2022.3192716 URL |
| [42] |
DUAN Junke, WANG Wei, WANG Licheng, et al. Controlled Redactable Blockchain Based on T-Times Chameleon Hash and Signature[J]. IEEE Transactions on Information Forensics and Security, 2024, 19(1): 7560-7572.
doi: 10.1109/TIFS.2024.3436925 URL |
| [43] | BIERI C. An Overview into the InterPlanetary File System (IPFS): Use Cases, Advantages, and Drawbacks[J]. Communication Systems XIV, 2021, 28(1): 78-99. |
| [44] | OUYANG Zhiqiang, SHAO Jie, ZENG Yifeng. PoW and PoS and Related Applications[C]// IEEE. 2021 International Conference on Electronic Information Engineering and Computer Science. New York: IEEE, 2021: 59-62. |
| [45] |
SALEH F. Blockchain without Waste: Proof-of-Stake[J]. The Review of Financial Studies, 2021, 34(3): 1156-1190.
doi: 10.1093/rfs/hhaa075 URL |
| [46] |
MANOLACHE M A, MANOLACHE S, TAPUS N. Decision Making Using the Blockchain Proof of Authority Consensus[J]. Procedia Computer Science, 2022, 199(1): 580-588.
doi: 10.1016/j.procs.2022.01.071 URL |
| [47] |
ZHANG Lihua, CAO Yu, ZHANG Ganzhe, et al. Blockchain-Based Secure Data Sharing Scheme for Microgrid[J]. Computer Engineering, 2022, 48(1): 43-50.
doi: 10.19678/j.issn.1000-3428.0060957 |
|
张利华, 曹宇, 张赣哲, 等. 基于区块链的微电网数据安全共享方案[J]. 计算机工程, 2022, 48(1): 43-50.
doi: 10.19678/j.issn.1000-3428.0060957 |
|
| [48] |
CUMMING D J, JOHAN S, PANT A. Regulation of the Cryp-to-Economy: Managing Risks, Challenges, and Regulatory Uncertainty[J]. Journal of Risk and Financial Management, 2019, 12(3): 126-139.
doi: 10.3390/jrfm12030126 URL |
| [49] |
PIAO Yangheran, YE Kai, CUI Xiaohui. A Data Sharing Scheme for GDPR-Compliance Based on Consortium Blockchain[J]. Future Internet, 2021, 13(8): 217-233.
doi: 10.3390/fi13080217 URL |
| [50] | QU Jia. Security Research of Blockchain Technology in Electronic Medical Records[J]. Medicine, 2022, 101(35): 1-6. |
| [51] | ZHANG Gengrui, PAN Fei, MAO Yunhao, et al. Reaching Consensus in the Byzantine Empire: A Comprehensive Review of BFT Consensus Algorithms[J]. ACM Computing Surveys, 2024, 56(5): 1-41. |
| [52] | HU Junjie, LIU Ke. Raft Consensus Mechanism and the Applications[EB/OL]. [2025-06-20]. https://iopscience.iop.org/article/10.1088/1742-6596/1544/1/012079?utm_source=researchgate.net&utm_medium=article. |
| [53] |
SI Haiping, SUN Changxia, LI Yanling, et al. IoT Information Sharing Security Mechanism Based on Blockchain Technology[J]. Future Generation Computer Systems, 2019, 101(1): 1028-1040.
doi: 10.1016/j.future.2019.07.036 URL |
| [54] |
DEWANGAN N K, CHANDRAKAR P. TempChain: A Blockchain Scheme for Telehealth Data Sharing between Two Blockchains Using Property Mapping Function[J]. The Journal of Supercomputing, 2023, 79(13): 14808-14826.
doi: 10.1007/s11227-023-05259-3 |
| [55] |
BATHULA A, MUHURI S, GUPTA S, et al. Secure Certificate Sharing Based on Blockchain Framework for Online Education[J]. Multimedia Tools and Applications, 2023, 82(11): 16479-16500.
doi: 10.1007/s11042-022-14126-x |
| [56] |
GAO Tingting, YAO Zhongyuan, JIA Miao. Overview of On-Chain and Off-Chain Consistency Protection Technologies[J]. Journal of Computer Applications, 2024, 44(12): 3658-3668.
doi: 10.11772/j.issn.1001-9081.2023121818 |
|
高婷婷, 姚中原, 贾淼, 等. 链上链下一致性保护技术综述[J]. 计算机应用, 2024, 44(12): 3658-3668.
doi: 10.11772/j.issn.1001-9081.2023121818 |
|
| [57] | PASDAR A, LEE Y C, DONG Zhongli. Connect API with Blockchain: A Survey on Blockchain Oracle Implementation[J]. ACM Computing Surveys, 2023, 55(10): 1-39. |
| [58] |
NEGKA L D, SPATHOULAS G P. Blockchain State Channels: A State of the Art[J]. IEEE Access, 2021, 9: 160277-160298.
doi: 10.1109/ACCESS.2021.3131419 URL |
| [59] | ZHANG Wuqi, WEI Lili, LI Shuqing, et al. Ðarcher: Detecting On-Chain-Off-Chain Synchronization Bugs in Decentralized Applications[C]// ACM. The 29th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering. New York: ACM, 2021: 553-565. |
| [60] |
HAN Mingjia, YANG Xinyi, SU Huachang, et al. Spatio-Temporal Big Data Collaborative Storage Mechanism Based on Incremental Aggregation Subvector Commitment in On-Chain and Off-Chain Systems[J]. ISPRS International Journal of Geo-Information, 2024, 13(8): 1-20.
doi: 10.3390/ijgi13010001 URL |
| [61] |
YU Bei, FENG Libo, ZHU Hongyu, et al. MeHLDT: A Multielement Hash Lock Data Transfer Mechanism for On-Chain and Off-Chain[J]. Peer-to-Peer Networking and Applications, 2023, 16(4): 1927-1943.
doi: 10.1007/s12083-023-01491-z |
| [62] | WIJESEKARA P A D S N. A Literature Review on Access Control in Networking Employing Blockchain[J]. Indonesian Journal of Computer Science, 2024, 13(1): 734-768. |
| [63] | LI Feng. Parameterized Role Based on Access Control Model[J]. Journal of Xinjiang Normal University (Natural Sciences Edition), 2023, 42(1): 1-5. |
| 李峰. 基于角色的参数化访问控制模型[J]. 新疆师范大学学报(自然科学版), 2023, 42(1): 1-5. | |
| [64] | DAVARI M, ZULKERNINE M. Policy Modeling and Anomaly Detection in ABAC Policies[C]// Springer. International Conference on Risks and Security of Internet and Systems. Heidelberg: Springer, 2021: 137-152. |
| [65] |
WALID R, JOSHI K P, CHOI S G. Comparison of Attribute-Based Encryption Schemes in Securing Healthcare Systems[J]. Scientific Reports, 2024, 14(1): 1-14.
doi: 10.1038/s41598-023-50600-8 |
| [66] |
YAN Li, WANG Gaozhou, YIN Tian, et al. Attribute-Based Searchable Encryption: A Survey[J]. Electronics, 2024, 13(9): 1-22.
doi: 10.3390/electronics13010001 URL |
| [67] | ZHANG Yinghui, DENG R H, XU Shengmin, et al. Attribute-Based Encryption for Cloud Computing Access Control: A Survey[J]. ACM Computing Surveys (CSUR), 2020, 53(4): 1-41. |
| [68] |
WANG Taochun, WU Qingshan, CHEN Jian, et al. Health Data Security Sharing Method Based on Hybrid Blockchain[J]. Future Generation Computer Systems, 2024, 153: 251-261.
doi: 10.1016/j.future.2023.11.032 URL |
| [69] |
XU Hong, HE Qian, LI Xuecong, et al. BDSS-FA: A Blockchain-Based Data Security Sharing Platform with Fine-Grained Access Control[J]. IEEE Access, 2020, 8(1): 87552-87561.
doi: 10.1109/Access.6287639 URL |
| [70] | MAKHDOOM I, ZHOU I, ABOLHASAN M, et al. PrivySharing: A Blockchain-Based Framework for Privacy-Preserving and Secure Data Sharing in Smart Cities[J]. Computers & Security, 2020, 88(1): 1-24. |
| [71] | YU Kechen, GUO Li, YIN Hongwei, et al. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers[J]. Netinfo Security, 2022, 22(6): 73-85. |
| 于克辰, 郭莉, 阴宏伟, 等. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. | |
| [72] | LIN Jiehe, ZHANG Shaohua, LI Chao, et al. A Blockchain Data Sharing System Based on ECC[J]. Computer Engineering & Science, 2022, 44(5): 810-818. |
| 林洁和, 张绍华, 李超, 等. 基于ECC的区块链数据共享系统设计[J]. 计算机工程与科学, 2022, 44(5): 810-818. | |
| [73] | HUANG Haiping, ZHU Peng, XIAO Fu, et al. A Blockchain-Based Scheme for Privacy-Preserving and Secure Sharing of Medical Data[J]. Computers & Security, 2020, 99(1): 1-13. |
| [74] | LEI Hong, YAN Yun, BAO Zijian, et al. SDSBT: A Secure Multi-Party Data Sharing Platform Based on Blockchain and Tee[C]// Springer. International Symposium on Cyberspace Safety and Security. Heidelberg: Springer, 2020: 184-196. |
| [75] | YU Sicong, HUANG Ying, TANG Libo, et al. Research on Information Sharing Mechanism Based on Blockchain Technology[C]// IEEE. 2022 7th International Conference on Computational Intelligence and Applications (ICCIA). New York: IEEE, 2022: 210-214. |
| [76] | ZHANG Heng, LIU Wenguo. Research on the Application of Blockchain in the Safe and Trusted Sharing of Government Data[C]// IEEE. 2023 2nd International Conference on Artificial Intelligence and Blockchain Technology (AIBT). New York: IEEE, 2023: 52-55. |
| [77] |
YANG Yalong, LIU Muhua, WANG Lin, et al. A Ring Signature Scheme with Linkability and Traceability for Blockchain-Based Medical Data Sharing System[J]. Peer-to-Peer Networking and Applications, 2025, 18(3): 103-121.
doi: 10.1007/s12083-025-01913-0 |
| [78] | NIU Geng. A Blockchain-Based Secure and Privacy-Preserving Healthcare Data Management Framework with SHA-256 and PoW Consensus[J]. Informatica, 2025, 49(20): 1-14. |
| [79] |
ZHANG Xiaohong, CHEN Xiaofeng. Data Security Sharing and Storage Based on a Consortium Blockchain in a Vehicular Ad-Hoc Network[J]. IEEE Access, 2019, 7(1): 58241-58254.
doi: 10.1109/Access.6287639 URL |
| [80] |
LU Yunlong, HUANG Xiaohong, ZHANG Ke, et al. Blockchain Empowered Asynchronous Federated Learning for Secure Data Sharing in Internet of Vehicles[J]. IEEE Transactions on Vehicular Technology, 2020, 69(4): 4298-4311.
doi: 10.1109/TVT.2020.2973651 |
| [81] | TU Zhitian, ZHU Kun, YI Changyi, et al. Blockchain-Based Privacy-Preserving Dynamic Spectrum Sharing[C]// Springer. The 15th International Conference on Wireless Algorithms, Systems, and Applications. Heidelberg: Springer, 2020: 444-456. |
| [82] | SU Zhan, WANG Hejian, WANG Huanjuan, et al. A Financial Data Security Sharing Solution Based on Blockchain Technology and Proxy Re-Encryption Technology[C]// IEEE. 2020 IEEE 3rd International Conference of Safe Production and Informatization (IICSPI). New York: IEEE, 2020: 462-465. |
| [83] | VIJAY A R, ALAGIRI I, JAYALAKSHMI P, et al. Lattice Homomorphic Assisted Privacy Preserving Electronic Health Records Data Transmission in Internet of Medical Things Using Blockchain[J]. Transactions on Emerging Telecommunications Technologies, 2025, 36(2): 1-17. |
| [84] |
LIU Yizhong, ZHAO Boyu, LIN Xun, et al. Quantum-Resistant Sharding Blockchain and Its Application in Secure Data Transmission[J]. IEEE Journal on Selected Areas in Communications, 2025, 43(8): 2732-2746.
doi: 10.1109/JSAC.2025.3568043 URL |
| [85] |
XIONG Anping, LIU Guihua, ZHU Qingyi, et al. A Notary Group-Based Cross-Chain Mechanism[J]. Digital Communications and Networks, 2022, 8(6): 1059-1067.
doi: 10.1016/j.dcan.2022.04.012 URL |
| [86] | XIONG Runqun, CHENG Jing, PU Jiahang, et al. Enhancing Trust and Collaboration: A Reputation-Driven Mechanism for Cross-Chain IoT Data Sharing[J]. Computer Networks, 2025, 264(1): 1-14. |
| [87] | SUN Yangyang, YI Longyang, DUAN Li, et al. A Decentralized Cross-Chain Service Protocol Based on Notary Schemes and Hash-Locking[C]// IEEE. 2022 IEEE International Conference on Services Computing (SCC). New York: IEEE, 2022: 152-157. |
| [88] |
TAN Zhongsheng, CHEN Chunhui, CHEN Xuebin, et al. A Study on Privacy Protection of Cross-Chain Transactions Based on Improved Notary Mechanisms[J]. IEEE Access, 2024, 12(1): 95846-95856.
doi: 10.1109/ACCESS.2024.3425475 URL |
| [89] |
YIN Lingyuan, XU Jing, TANG Qiang. Sidechains with Fast Cross-Chain Transfers[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(6): 3925-3940.
doi: 10.1109/TDSC.2021.3114151 URL |
| [90] |
DENG Zhihong, LI Taotao, TANG Chunming, et al. PSSC: Practical and Secure Sidechain Construction for Heterogeneous Blockchains Orienting IoT[J]. IEEE Internet of Things Journal, 2023, 11(3): 4600-4613.
doi: 10.1109/JIOT.2023.3302291 URL |
| [91] |
LI Min, TANG H, HUSSEIN A R, et al. A Sidechain-Based Decentralized Authentication Scheme via Optimized Two-Way Peg Protocol for Smart Community[J]. IEEE Open Journal of the Communications Society, 2020, 1: 282-292.
doi: 10.1109/OJCOMS URL |
| [92] | CHEN Mao, JIANG Yuan, HUANG Ju, et al. An Attribute-Encryption-Based Cross-Chain Model in Urban Internet of Vehicles[J]. Computers and Electrical Engineering, 2024, 115(1): 1-22. |
| [93] |
MAO Hanyu, NIE Tiezheng, SUN Hao, et al. A Survey on Cross-Chain Technology: Challenges, Development, and Prospect[J]. IEEE Access, 2022, 11(1): 45527-45546.
doi: 10.1109/ACCESS.2022.3228535 URL |
| [94] | DENG Liping, CHEN Huan, ZENG Jing, et al. Research on Cross-Chain Technology Based on Sidechain and Hash-Locking[C]// Springer. Edge Computing-EDGE 2018. Heidelberg: Springer, 2018: 144-151. |
| [95] |
HAN Yutong, WANG Chundong, WANG Huaibin, et al. A Study of Liquidity Cross-Chain Models Based on Convex Optimization[J]. Scientific Reports, 2024, 14(1): 1-11.
doi: 10.1038/s41598-023-50600-8 |
| [96] |
TIAN Hangyu, XUE Kaiping, LUO Xinyi, et al. Enabling Cross-Chain Transactions: A Decentralized Cryptocurrency Exchange Protocol[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3928-3941.
doi: 10.1109/TIFS.2021.3096124 URL |
| [97] |
LIN Ting, YANG Xu, WANG Taoyi, et al. Implementation of High-Performance Blockchain Network Based on Cross-Chain Technology for IoT Applications[J]. Sensors, 2020, 20(11): 1-24.
doi: 10.3390/s20010001 URL |
| [98] | CAO Yinfeng, CAO Jiannong, BAI Dongbin, et al. Map the Blockchain World: A Trustless and Scalable Blockchain Interoperability Protocol for Cross-Chain Applications[C]// ACM. The ACM on Web Conference 2025. New York: ACM, 2025: 717-726. |
| [99] | RAJUROY A, JOHN B. Cross-Chain Data Access Verification in Multi-Blockchain Ecosystems[EB/OL]. (2025-06-03)[2025-06-12]. https://www.researchgate.net/profile/Adam-Rajuroy/publication/392363433_Cross-Chain_Data_Access_Verification_in_Multi-Blockchain_Ecosystems/links/683efa11d1054b0207f93588/Cross-Chain-Data-Access-Verification-in-Multi-Blockchain-Ecosystems.pdf. |
| [100] |
HE Yunhua, ZHANG Cui, WU Bin, et al. Cross-Chain Trusted Service Quality Computing Scheme for Multichain-Model-Based 5G Network Slicing SLA[J]. IEEE Internet of Things Journal, 2021, 10(14): 12126-12139.
doi: 10.1109/JIOT.2021.3132388 URL |
| [101] | GUO Hongyu, LIANG Haozhe, HUANG Ju, et al. A Framework for Efficient Cross-Chain Token Transfers in Blockchain Networks[J]. Journal of King Saud University-Computer and Information Sciences, 2024, 36(2): 1-15. |
| [102] | LIU Yizhong, LIU Jianwei, SALLES M A V, et al. Building Blocks of Sharding Blockchain Systems: Concepts, Approaches, and Open Problems[J]. Computer Science Review, 2022, 46(1): 1-44. |
| [103] |
LI Li, WU Jiahao, CUI Wei. A Review of Blockchain Cross-Chain Technology[J]. IET Blockchain, 2023, 3(3): 149-158.
doi: 10.1049/blc2.v3.3 URL |
| [104] | GAJALWAR Y, KHILARI S, KULKARNI H, et al. Erasure Coding and Data Deduplication: A Comprehensive Survey[C]// IEEE. 2024 3rd International Conference for Innovation in Technology (INOCON). New York: IEEE, 2024: 1-8. |
| [105] |
TAHERDOOST H. Smart Contracts in Blockchain Technology: A Critical Review[J]. Information, 2023, 14(2): 117-135.
doi: 10.3390/info14020117 URL |
| [1] | DONG Jiayu, GAO Hongmin, MA Zhaofeng, LAI Guanhui. Research and Implementation of Multi-Signature Mechanism in Blockchain [J]. Netinfo Security, 2026, 26(1): 125-138. |
| [2] | ZHAN Dongyang, HUANG Zilong, TAN Kai, YU Zhaofeng, HE Zheng, ZHANG Hongli. Cross-Function Behavior Analysis and Constraint Technology for Serverless Applications [J]. Netinfo Security, 2025, 25(9): 1329-1337. |
| [3] | YANG Jianxin, WANG Xiaoding, LIN Hui. Improved Consensus Algorithm Based on HotStuff and Multi-Ary Trees [J]. Netinfo Security, 2025, 25(9): 1447-1455. |
| [4] | SHE Wei, MA Tianxiang, FENG Haige, LIU Wei. Tracing-Free Blockchain Covert Communication Method Based on RBF Mechanism [J]. Netinfo Security, 2025, 25(8): 1302-1312. |
| [5] | LIU Feng, HUANG Hao. A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks [J]. Netinfo Security, 2025, 25(6): 898-909. |
| [6] | YE Jiajun, GAO Cuifeng, XUE Yinxing. Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis [J]. Netinfo Security, 2025, 25(5): 732-746. |
| [7] | QIN Jinlei, KANG Yimin, LI Zheng. Lightweight Fine-Grained Multi-Dimensional Multi-Subset Privacy-Preserving Data Aggregation for Smart Grid [J]. Netinfo Security, 2025, 25(5): 747-757. |
| [8] | ZHU Xiaoqiang, ZHANG Haowen, LIN Yanzi, LIU Jiqiang. Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity [J]. Netinfo Security, 2025, 25(5): 817-827. |
| [9] | YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication [J]. Netinfo Security, 2025, 25(4): 640-653. |
| [10] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [11] | ZHANG Guanping, WEI Fushan, CHEN Xi, GU Chunxiang. Blockchain-Based Privacy-Preserving Cross-Domain Authentication Protocol [J]. Netinfo Security, 2025, 25(12): 1948-1960. |
| [12] | GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments [J]. Netinfo Security, 2025, 25(11): 1673-1690. |
| [13] | REN Fengyuan, ZHANG Xinyue, LEI Zhuoyi, LIU Xin. Research on Key-Value Data Storage and Operation Optimization Method Based on Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1707-1717. |
| [14] | SHEN Haoting, PENG Zhigang, LIU Yuxuan, WANG Yafei. Hardware Authentication Mechanism for Consortium Blockchain Based on Differentiated Physical Unclonable Function Models [J]. Netinfo Security, 2025, 25(11): 1732-1744. |
| [15] | WANG Yong, WU Yifan, WAN Qiancheng. Research on Redactable Blockchain Scheme Based on the Chinese Remainder Theorem [J]. Netinfo Security, 2025, 25(1): 36-47. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||