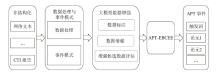
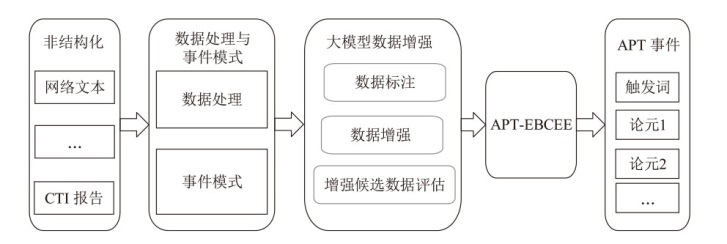
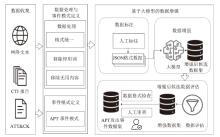
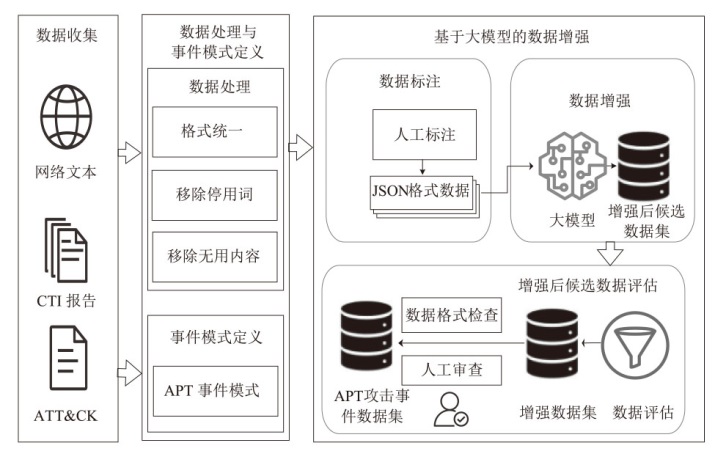
Netinfo Security ›› 2025, Vol. 25 ›› Issue (9): 1338-1347.doi: 10.3969/j.issn.1671-1122.2025.09.002
Previous Articles Next Articles
Small-Sample APT Attack Event Extraction Method Based on Large Model
CAO Jun1, XIANG Ga1,2( ), REN Yawei1, TAN Zicheng1, YANG Qunsheng1
), REN Yawei1, TAN Zicheng1, YANG Qunsheng1
- 1. College of Computer Science, Beijing Information Science and Technology University, Beijing 102206, China
2. Intelligent Information Processing Institute, Beijing Information Science and Technology University, Beijing 102206, China
-
Received:2025-06-08Online:2025-09-10Published:2025-09-18
CLC Number:
Cite this article
CAO Jun, XIANG Ga, REN Yawei, TAN Zicheng, YANG Qunsheng. Small-Sample APT Attack Event Extraction Method Based on Large Model[J]. Netinfo Security, 2025, 25(9): 1338-1347.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.09.002
| 编号 | 类型 | 事件类型 | 论元1 | 论元2 | 论元3 | 论元4 | 论元5 |
|---|---|---|---|---|---|---|---|
| 1 | 攻击准备 阶段 | 鱼叉攻击 | 伪造文件 | 真实文件 | 攻击者 | 受害目标 | 攻击战术 |
| 2 | 水坑攻击 | 伪造文件 | 真实文件 | 攻击者 | 受害目标 | — | |
| 3 | 扫描 | 受害目标 | — | — | — | — | |
| 4 | 窃取信息 | 受害目标 | 攻击者 | 被窃取 目标 | 攻击武器 | — | |
| 5 | 攻击实施阶段 | 特洛伊 木马 | 攻击者 | 受害目标 | 攻击武器 | 攻击战术 | — |
| 6 | 蠕虫 | 攻击者 | 受害目标 | 攻击武器 | — | — | |
| 7 | 漏洞利用 | 攻击者 | 受害目标 | 攻击武器 | 攻击战术 | — | |
| 8 | 零日漏洞 利用 | 攻击者 | 受害目标 | 攻击武器 | — | — | |
| 9 | 持续攻击 阶段 | 后门 | 攻击者 | 受害目标 | 攻击武器 | — | — |
| 10 | 病毒 | 攻击者 | 受害目标 | 攻击武器 | 攻击战术 | — | |
| 11 | 凭据收集 | 攻击者 | 受害目标 | 攻击武器 | 攻击战术 | — | |
| 12 | 远程访问 木马 | 攻击者 | 受害目标 | 攻击武器 | 攻击战术 | — | |
| 13 | 数据泄露 | 攻击者 | 受害目标 | 攻击武器 | 攻击战术 | — |
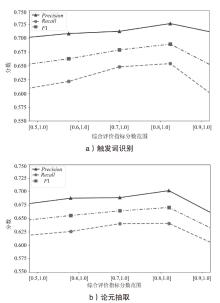
| 模型 | 触发词识别 | 论元抽取 | ||||
|---|---|---|---|---|---|---|
| Precision | Recall | F1 | Precision | Recall | F1 | |
| APT-EBCEE | 71.34% | 65.31% | 68.26% | 68.26% | 64.18% | 66.19% |
| 移除ERNIE | 60.68% | 53.75% | 57.04% | 59.43% | 55.69% | 57.47% |
| 移除BiLSTM | 66.71% | 62.15% | 64.34% | 64.36% | 60.18% | 62.20% |
| 移除CRF | 68.71% | 64.18% | 66.36% | 65.82% | 63.12% | 64.44% |
| 移除Prompt | 67.34% | 62.14% | 64.66% | 64.85% | 61.76% | 63.28% |
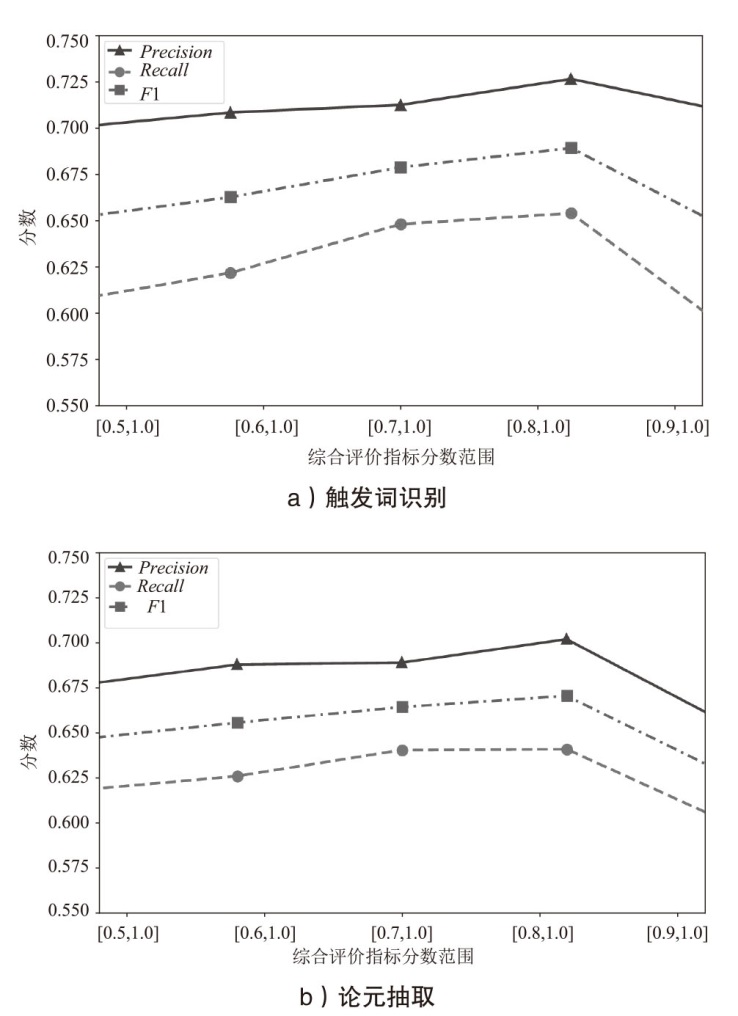
| 模型 | 触发词识别 | 论元抽取 | ||||
|---|---|---|---|---|---|---|
| Precisio | Recall | F1 | Precision | Recall | F1 | |
| BiLSTM-CRF | 78.12% | 80.36% | 79.24% | 70.11% | 69.66% | 69.88% |
| BERT-CRF | 81.10% | 79.92% | 80.50% | 75.29% | 74.28% | 74.78% |
| BERT-BiLSTM-CRF | 83.01% | 81.78% | 82.42% | 80.75% | 80.49% | 80.62% |
| UIE | 84.33% | 83.12% | 83.72% | 82.52% | 83.66% | 83.09% |
| APT-EBCEE | 85.14% | 84.28% | 84.71% | 83.02% | 82.61% | 82.81% |
| [1] | CHEN Ping, DESMET L, HUYGENS C. A Study on Advanced Persistent Threats[C]// Springer. IFIP International Conference on Communications and Multimedia Security. Heidelberg: Springer, 2014: 63-72. |
| [2] | LI Yuancheng, LUO Hao, WANG Qingle, et al. An Advanced Persistent Threat Model of New Power System Based on ATT&CK[J]. Netinfo Security, 2023, 23(2): 26-34. |
| 李元诚, 罗昊, 王庆乐, 等. 一种基于ATT&CK的新型电力系统APT攻击建模[J]. 信息网络安全, 2023, 23(2): 26-34. | |
| [3] | GUO Zimeng, ZHU Guangjie, YANG Yijie, et al. Research on Railway Network Security Performance Based on APT Characteristics[J]. Netinfo Security, 2024, 24(5): 802-811. |
| 郭梓萌, 朱广劼, 杨轶杰, 等. 基于APT特征的铁路网络安全性能研究[J]. 信息网络安全, 2024, 24(5): 802-811. | |
| [4] | ALSHAMRANI A, MYNENI S, CHOWDHARY A, et al. A Survey on Advanced Persistent Threats: Techniques, Solutions, Challenges, and Research Opportunities[J]. IEEE Communications Surveys & Tutorials, 2019, 21(2): 1851-1877. |
| [5] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery[J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| 赵新强, 范博, 张东举. 基于威胁发现的APT攻击防御体系研究[J]. 信息网络安全, 2024, 24(7): 1122-1128. | |
| [6] | WAGNER T D, MAHBUB K, PALOMAR E, et al. Cyber Threat Intelligence Sharing: Survey and Research Directions[EB/OL]. (2019-08-06)[2025-06-02]. https://doi.org/10.1016/j.cose.2019.101589. |
| [7] | LI Zhenyuan, ZENG Jun, CHEN Yan. AttacKG: Constructing Technique Knowledge Graph from Cyber Threat Intelligence Reports[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2022: 589-609. |
| [8] | ZHANG Tongtao, JI Heng. Event Extraction with Generative Adversarial Imitation Learning[EB/OL]. (2018-04-21)[2025-06-02]. https://doi.org/10.48550/arXiv.1804.07881. |
| [9] | LUO Ning, DU Xiangyu, HE Yitong, et al. A Framework for Document-Level Cybersecurity Event Extraction from Open Source Data[C]// IEEE. IEEE 24th International Conference on Computer Supported Cooperative Work in Design(CSCWD). New York: IEEE, 2021: 422-427. |
| [10] | SATYAPANICH T, FERRARO F, FININ T. Casie: Extracting Cybersecurity Event Information from Text[J]. AAAI Technical Track: Natural Language Processing, 2020, 34(5): 8749-8757. |
| [11] | HUANG Zhiheng, XU Wei, YU Kai. Bidirectional LSTM-CRF Models for Sequence Tagging[EB/OL]. (2015-08-09)[2025-06-02]. https://arxiv.org/pdf/1508.01991. |
| [12] | JI Zhongxiang, WU Yue. Event Extraction of Chinese Text Based on Composite Neural Network[J]. Journal of Shanghai University(Natural Science), 2021, 27(3): 535-543. |
|
季忠祥, 吴悦. 基于组合神经网络的中文事件抽取[J]. 上海大学学报(自然科学版), 2021, 27(3): 535-543.
doi: 10.12066/j.issn.1007-2861.2223 |
|
| [13] | WANG Bo, WEI Wei, WU Yang, et al. Event Recognition in Chinese Emergencies Corpus Using ALBERT-BiLSTM-CRF[C]// IEEE. 2020 IEEE International Conference on Power, Intelligent Computing and Systems(ICPICS). New York: IEEE, 2020: 392-397. |
| [14] | XIANG Ga, SHI Chen, ZHANG Yangsen. An APT Event Extraction Method Based on BERT-BiGRU-CRF for APT Attack Detection[EB/OL]. (2023-08-04)[2025-06-02]. https://arxiv.org/pdf/1508.01991. |
| [15] | SUN Yu, WANG Shuohuan, FENG Shikun, et al. Ernie 3.0: Large-Scale Knowledge Enhanced Pre-Training for Language Understanding and Generation[EB/OL]. (2021-07-05)[2025-06-02]. https://doi.org/10.48550/arXiv.2107.02137. |
| [16] | GAO Yue, ZENG Chongqing, LIU Zhenye, et al. ERNIE-BC: An ERNIE-BiLSTM-CRF Fusion Model for Segmentation-Based Event Extraction[C]// IEEE. 2023 IEEE 9th International Conference on Cloud Computing and Intelligent Systems(CCIS). New York: IEEE, 2023: 424-428. |
| [17] | LIU Wanli, YONG Xinyou, CAO Kaichen, et al. Universal Information Extraction Method Based on Prompt Learning with ERNIE-BiLSTM-PN[J]. Journal of University of Electronic Science and Technology of China, 2025, 54(3): 411-423. |
| 刘万里, 雍新有, 曹开臣, 等. 基于提示学习的ERNIE-BiLSTM-PN通用信息抽取方法研究[J]. 电子科技大学学报, 2025, 54(3): 411-423. | |
| [18] | WEI J, ZOU Kai. EDA: Easy Data Augmentation Techniques for Boosting Performance on Text Classification Tasks[EB/OL]. (2019-08-25)[2025-06-02]. https://doi.org/10.48550/arXiv.1901.11196. |
| [19] | NAIR A R, SINGH R P, GUPTA D, et al. Evaluating the Impact of Text Data Augmentation on Text Classification Tasks Using DistilBERT[J]. Procedia Computer Science, 2024, 235: 102-111. |
| [20] | ZHANG Shaokang, RAN Ning. Contrastive Learning Based on Linguistic Knowledge and Adaptive Augmentation for Text Classification[EB/OL]. (2024-09-27)[2025-06-02]. https://doi.org/10.1016/j.knosys.2024.112189. |
| [21] | FENG Zijian, ZHOU Hanzhang, ZHU Zixiao, et al. Tailored Text Augmentation for Sentiment Analysis[EB/OL]. (2022-11-01)[2025-06-02]. https://doi.org/10.1016/j.eswa.2022.117605. |
| [22] | MENG Zihao, LIU Tao, ZHANG Heng, et al. CEAN: Contrastive Event Aggregation Network with LLM-Based Augmentation for Event Extraction[C]// ACL. The 18th Conference of the European Chapter of the Association for Computational Linguistics. Malta: ACL, 2024: 321-333. |
| [23] | YANG Lishan, FAN Xi, WANG Xiangyu, et al. Event Extraction Based on Self-Data Augmentation with Large Language Models[EB/OL]. (2025-01-31)[2025-06-02]. https://doi.org/10.1007/s12293-025-00436-8. |
| [1] | JIN Zhigang, LI Zimeng, CHEN Xuyang, LIU Zepei. Review of Network Intrusion Detection System for Unbalanced Data [J]. Netinfo Security, 2025, 25(8): 1240-1253. |
| [2] | ZHANG Xuewang, LU Hui, XIE Haofei. A Data Augmentation Method Based on Graph Node Centrality and Large Model for Vulnerability Detection [J]. Netinfo Security, 2025, 25(4): 550-563. |
| [3] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [4] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [5] | GUO Zimeng, ZHU Guangjie, YANG Yijie, SI Qun. Research on Railway Network Security Performance Based on APT Characteristics [J]. Netinfo Security, 2024, 24(5): 802-811. |
| [6] | LI Jiao, ZHANG Yuqing, WU Yabiao. Data Augmentation Method via Large Language Model for Relation Extraction in Cybersecurity [J]. Netinfo Security, 2024, 24(10): 1477-1483. |
| [7] | WU Shangyuan, SHEN Guowei, GUO Chun, CHEN Yi. Threat Intelligence-Driven Dynamic Threat Hunting Method [J]. Netinfo Security, 2023, 23(6): 91-103. |
| [8] | GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph [J]. Netinfo Security, 2023, 23(12): 59-68. |
| [9] | YE Huanrong, LI Muyuan, JIANG Bo. Research on DGA Malicious Domain Name Detection Method Based on Transfer Learning and Threat Intelligence [J]. Netinfo Security, 2023, 23(10): 8-15. |
| [10] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [11] | MA Rui, CAI Manchun, PENG Shufan. A Deep Forgery Video Detection Model Based on Improved Xception Network [J]. Netinfo Security, 2021, 21(12): 109-117. |
| [12] | CHENG Shunhang, LI Zhihua. Research on Threat Intelligence Entity Recognition Method Based on MRC [J]. Netinfo Security, 2021, 21(10): 76-82. |
| [13] | ZHANG Yongsheng, WANG Zhi, WU Yijie, DU Zhenhua. Cyber Threat Intelligence Propagation Based on Conformal Prediction [J]. Netinfo Security, 2020, 20(6): 90-95. |
| [14] | WANG Changjie, LI Zhihua, ZHANG Ye. A Threat Intelligence Generation Method for Malware Family [J]. Netinfo Security, 2020, 20(12): 83-90. |
| [15] | Chenxi MA, Xingshu CHEN, Wenxian WANG, Haizhou WANG. Chinese Event Detection Based on Recurrent Neural Network [J]. Netinfo Security, 2018, 18(5): 75-81. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||