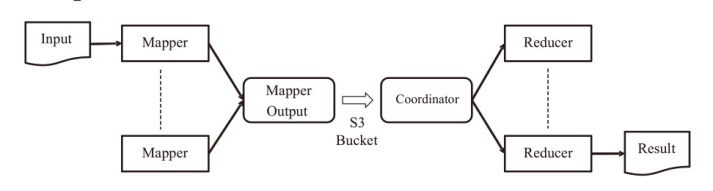
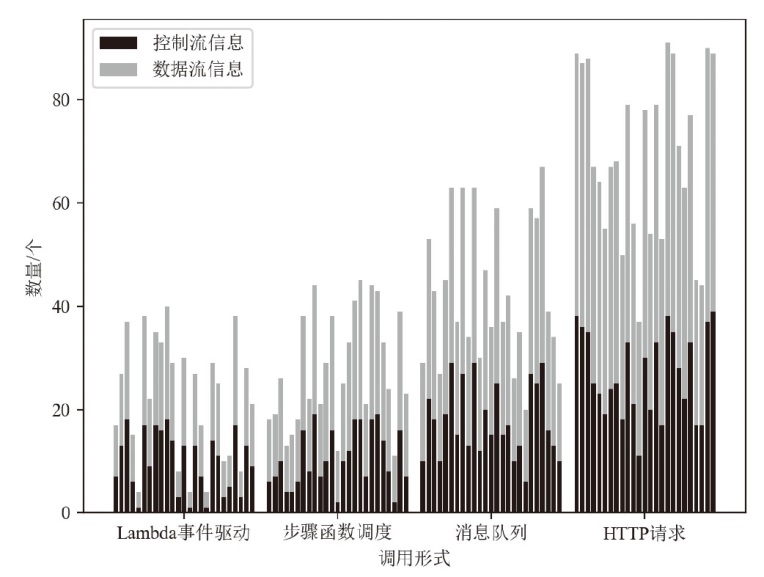
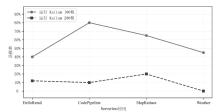
| [1] |
LI Yongkang, LIN Yanying, WANG Yang, et al. Serverless Computing: State-of-the-Art, Challenges and Opportunities[J]. IEEE Transactions on Services Computing, 2022, 16(2): 1522-1539.
|
| [2] |
GEORGE J. Comparing Scalable Serverless Analytics Architecture on Amazon Web Services and Google Cloud[EB/OL]. (2024-10-31)[2025-03-27]. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4963383.
|
| [3] |
LI Zijun, CHENG Jiagan, CHEN Quan, et al. RunD: A Lightweight Secure Container Runtime for High-Density Deployment and High-Concurrency Startup in Serverless Computing[C]// USENIX. 2022 USENIX Annual Technical Conference. Berkeley: USENIX, 2022: 53-68.
|
| [4] |
AHMADI S. Challenges and Solutions in Network Security for Serverless Computing[J]. International Journal of Current Science Research and Review, 2024, 7(1): 218-229.
|
| [5] |
KIM Y, KOO J, KIM U M. Vulnerabilities and Secure Coding for Serverless Applications on Cloud Computing[C]// Springer. International Conference on Human-Computer Interaction. Heidelberg: Springer, 2022: 145-163.
|
| [6] |
HEDIN D, SABELFELD A. A Perspective on Information-Flow Control[M]. Amsterdam: IOS Press, 2012.
|
| [7] |
LI Xing, LENG Xue, CHEN Yan. Securing Serverless Computing: Challenges, Solutions, and Opportunities[J]. IEEE Network, 2022, 37(2): 166-173.
|
| [8] |
ZHU Xiaogang, WEN Sheng, CAMTEPE S, et al. Fuzzing: A Survey for Roadmap[J]. ACM Computing Surveys (CSUR), 2022, 54(11): 1-36.
|
| [9] |
DATTA P, KUMAR P, MORRIS T, et al. Valve: Securing Function Workflows on Serverless Computing Platforms[C]// ACM. The Web Conference 2020. New York: ACM, 2020: 939-950.
|
| [10] |
LIN W T, KRINTZ C, WOLSKI R, et al. Tracking Causal Order in AWS Lambda Applications[C]// IEEE. IEEE International Conference on Cloud Engineering (IC2E). New York: IEEE, 2018: 50-60.
|
| [11] |
JEGAN D S, WANG Liang, BHAGAT S, et al. Guarding Serverless Applications with Kalium[C]// USENIX. 32nd USENIX Security Symposium. Berkeley: USENIX, 2023: 4087-4104.
|
| [12] |
OBETZ M, PATTERSON S, MILANOVA A. Static Call Graph Construction in AWS Lambda Serverless Applications[EB/OL]. (2019-07-08)[2025-03-27]. https://www.usenix.org/conference/hotcloud19/presentation/obetz.
|
| [13] |
WEN Jinfeng, CHEN Zhenpeng, JIN Xin, et al. Rise of the Planet of Serverless Computing: A Systematic Review[J]. ACM Transactions on Software Engineering and Methodology, 2023, 32(5): 1-61.
|
| [14] |
WU Xiaojun, WANG Ziyi, YUAN Sheng, et al. Improved Construction Scheme of Fully-Extended Call Graph to Enhance Observability of Serverless-Based Applications[C]// IEEE. IEEE International Conference on Software Engineering and Artificial Intelligence (SEAI). New York: IEEE, 2024: 139-145.
|
| [15] |
NAM J, LEE S, SEO H, et al. BASTION: A Security Enforcement Network Stack for Container Networks[C]// USENIX. USENIX Annual Technical Conference (USENIX ATC 20). Berkeley: USENIX, 2020: 81-95.
|
| [16] |
TAFT S T. Sound and Precise Static Analysis Using a Generalization of Static Single Assignment and Value Numbering[J]. International Journal on Software Tools for Technology Transfer, 2024, 26(5): 621-632.
|
| [17] |
THOTA R C. Efficient Serverless Architectures: Leveraging AWS Lambda and SageMaker for Scalable Workflow Solutions[J]. Journal of Science & Technology, 2024, 5(3): 133-152.
|
| [18] |
GUO Fu, ZHANG Yanfeng, GE Yu. A Fair Comparison of Message Queuing Systems[J]. IEEE Access, 2020, 9: 421-432.
|
| [19] |
TIWARI P, SHARMA S. Automation of FaaS Serverless Frameworks OpenFaaS and OpenWhisk in Private Cloud[C]// IEEE. World Conference on Communication & Computing (WCONF). New York: IEEE, 2023: 1-11.
|
| [20] |
ESKANDANI N, SALVANESCHI G. The Wonderless Dataset for Serverless Computing[C]// IEEE. IEEE/ACM International Conference on Mining Software Repositories (MSR). New York: IEEE, 2021: 565-569.
|
 ), YU Zhaofeng1, HE Zheng2, ZHANG Hongli1
), YU Zhaofeng1, HE Zheng2, ZHANG Hongli1