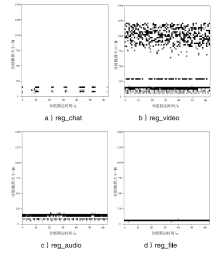
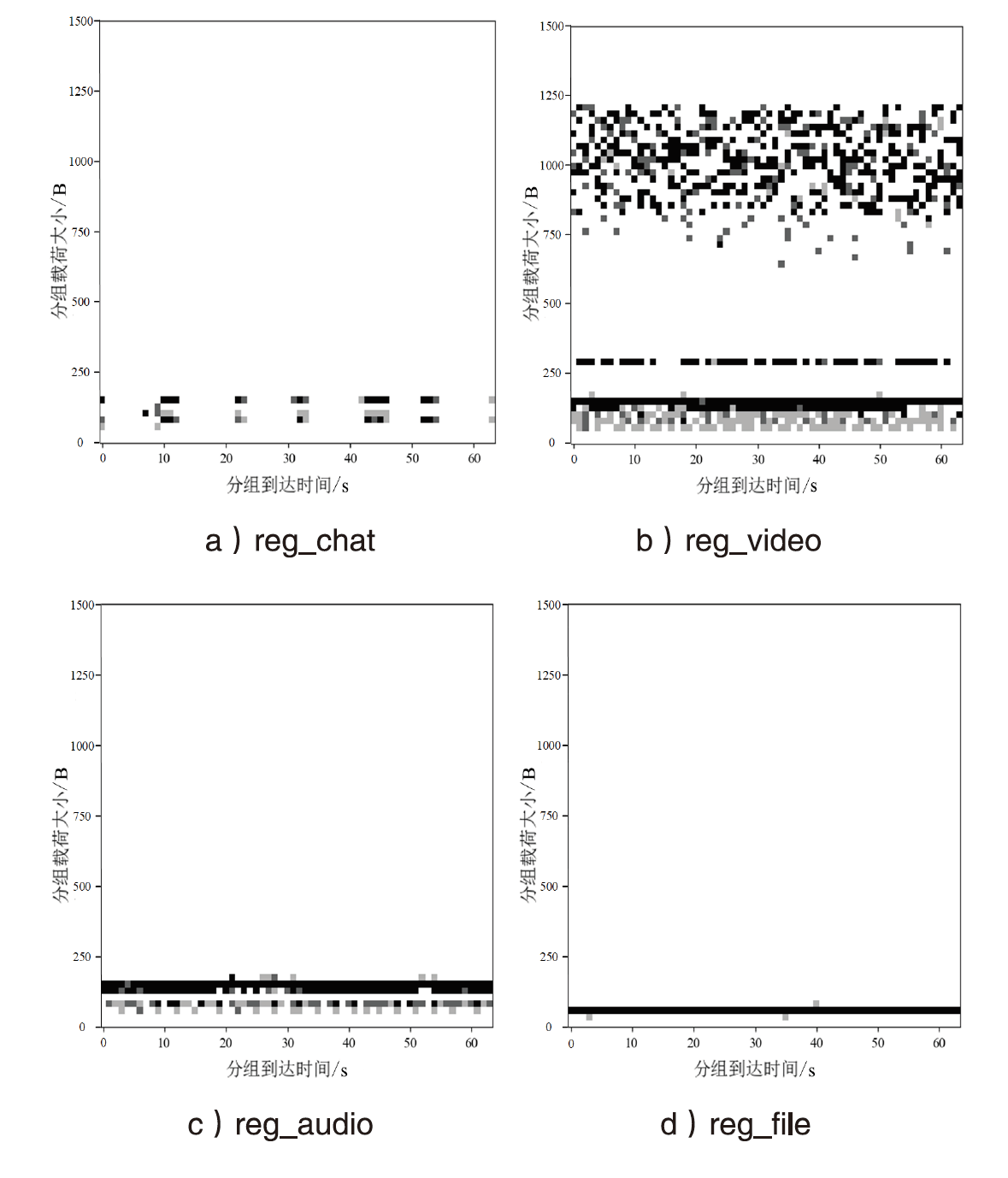
Netinfo Security ›› 2024, Vol. 24 ›› Issue (12): 1882-1895.doi: 10.3969/j.issn.1671-1122.2024.12.007
Previous Articles Next Articles
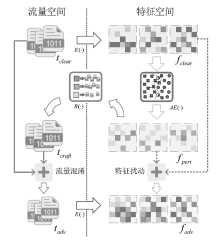
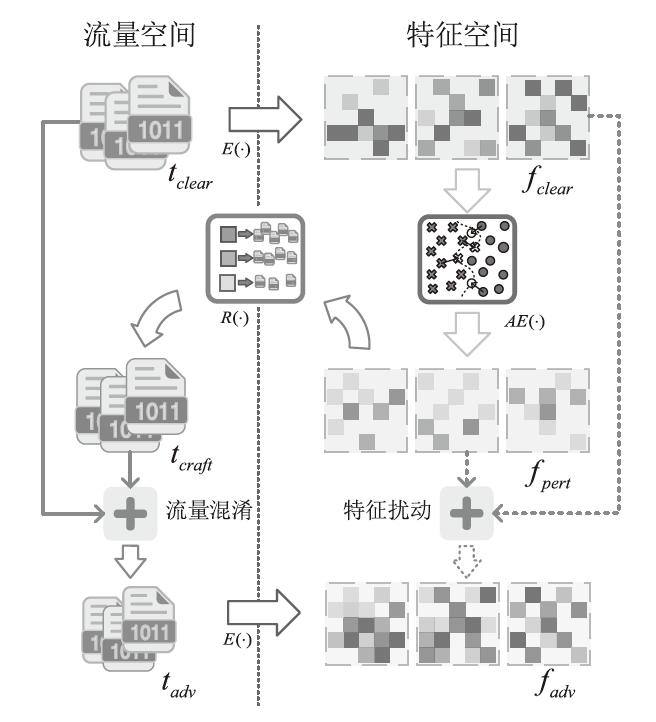
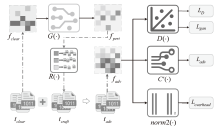
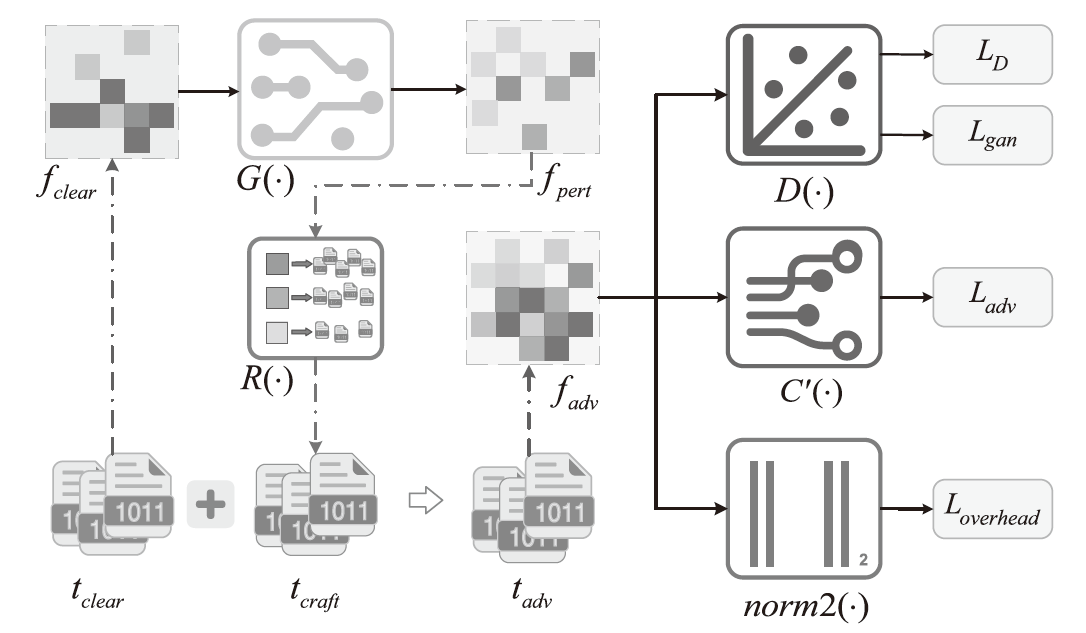
Traffic Obfuscation Method for Temporal Features Based on Adversarial Example
ZHANG Guomin, TU Zhixin( ), XING Changyou, WANG Zipeng, ZHANG Junfeng
), XING Changyou, WANG Zipeng, ZHANG Junfeng
- Institute of Command and Control Engineering, Army Engineering University of PLA, Nanjing 210007, China
-
Received:2024-05-08Online:2024-12-10Published:2025-01-10
CLC Number:
Cite this article
ZHANG Guomin, TU Zhixin, XING Changyou, WANG Zipeng, ZHANG Junfeng. Traffic Obfuscation Method for Temporal Features Based on Adversarial Example[J]. Netinfo Security, 2024, 24(12): 1882-1895.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.12.007
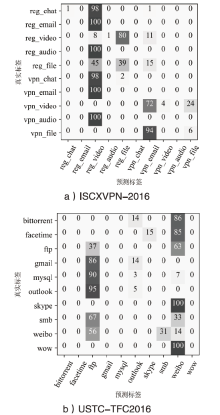
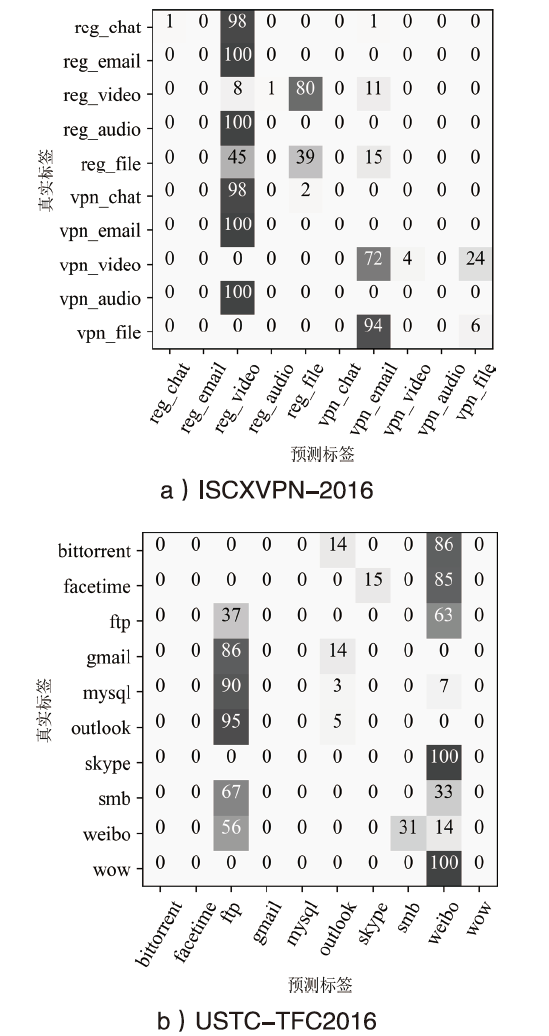
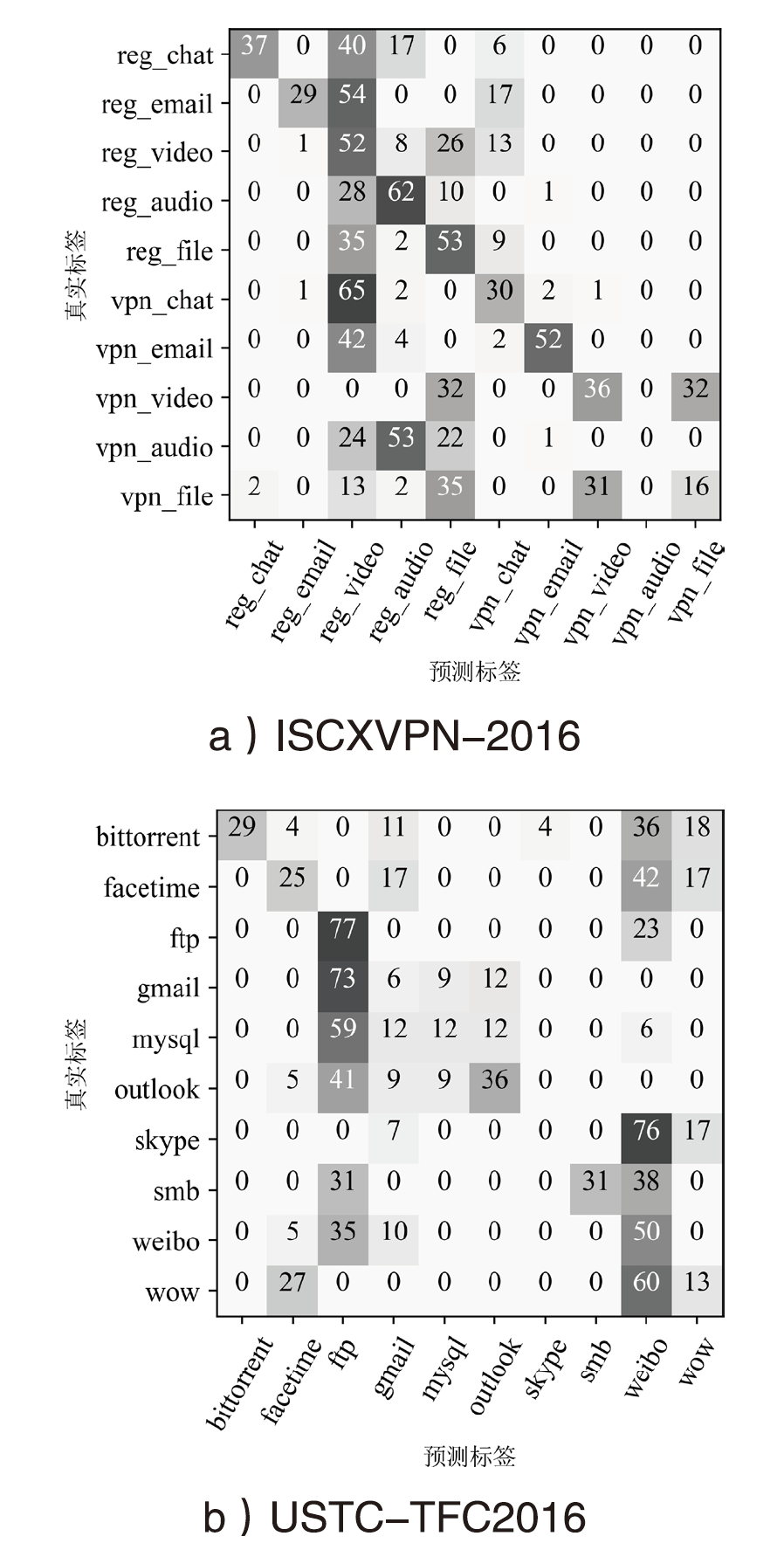
| 数据集 | 类别 | 混淆前 | 混淆后 | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PRC | REC | F1-Score | ACC | PRC | REC | F1-Score | ACC | OHR | ||
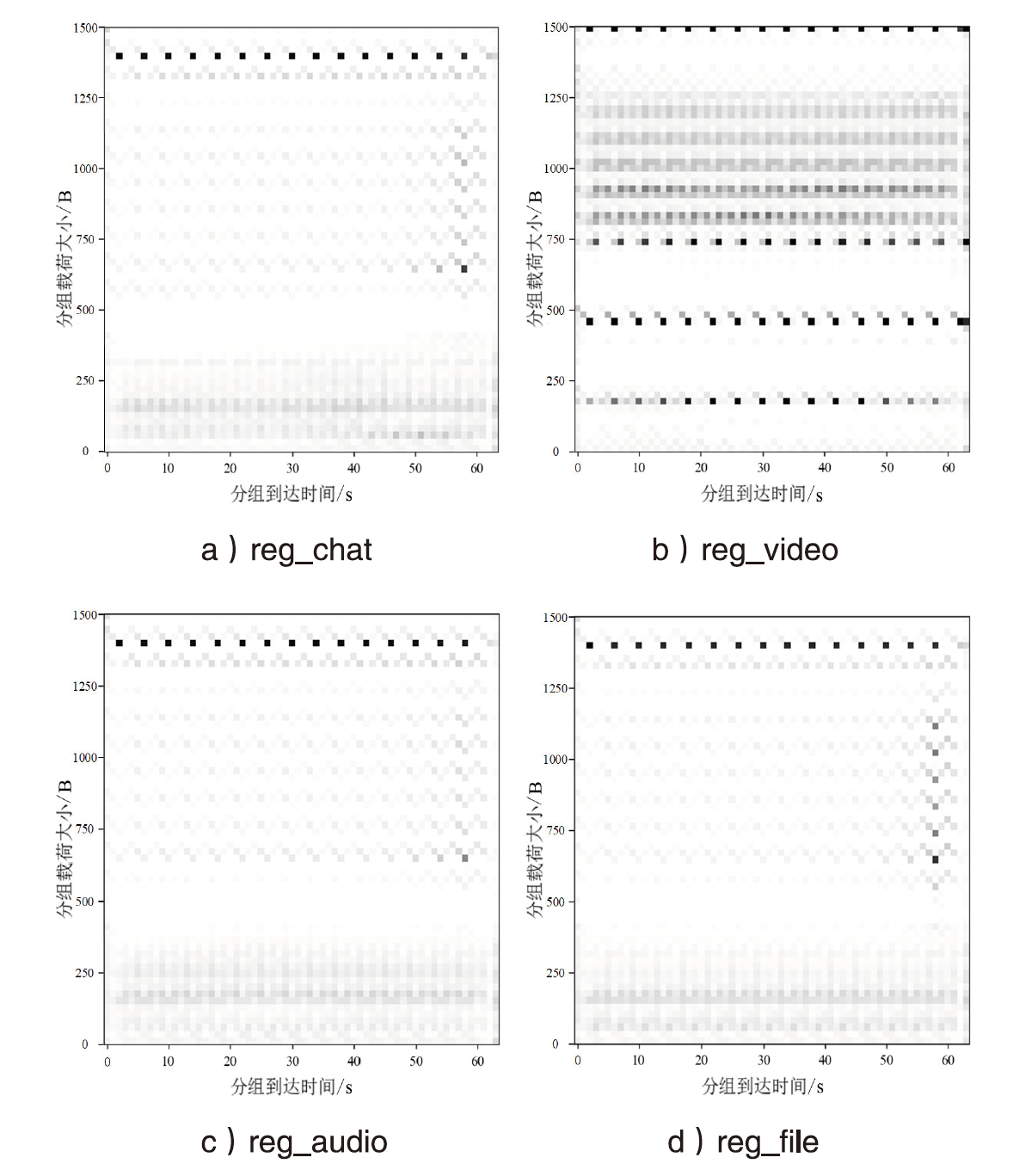
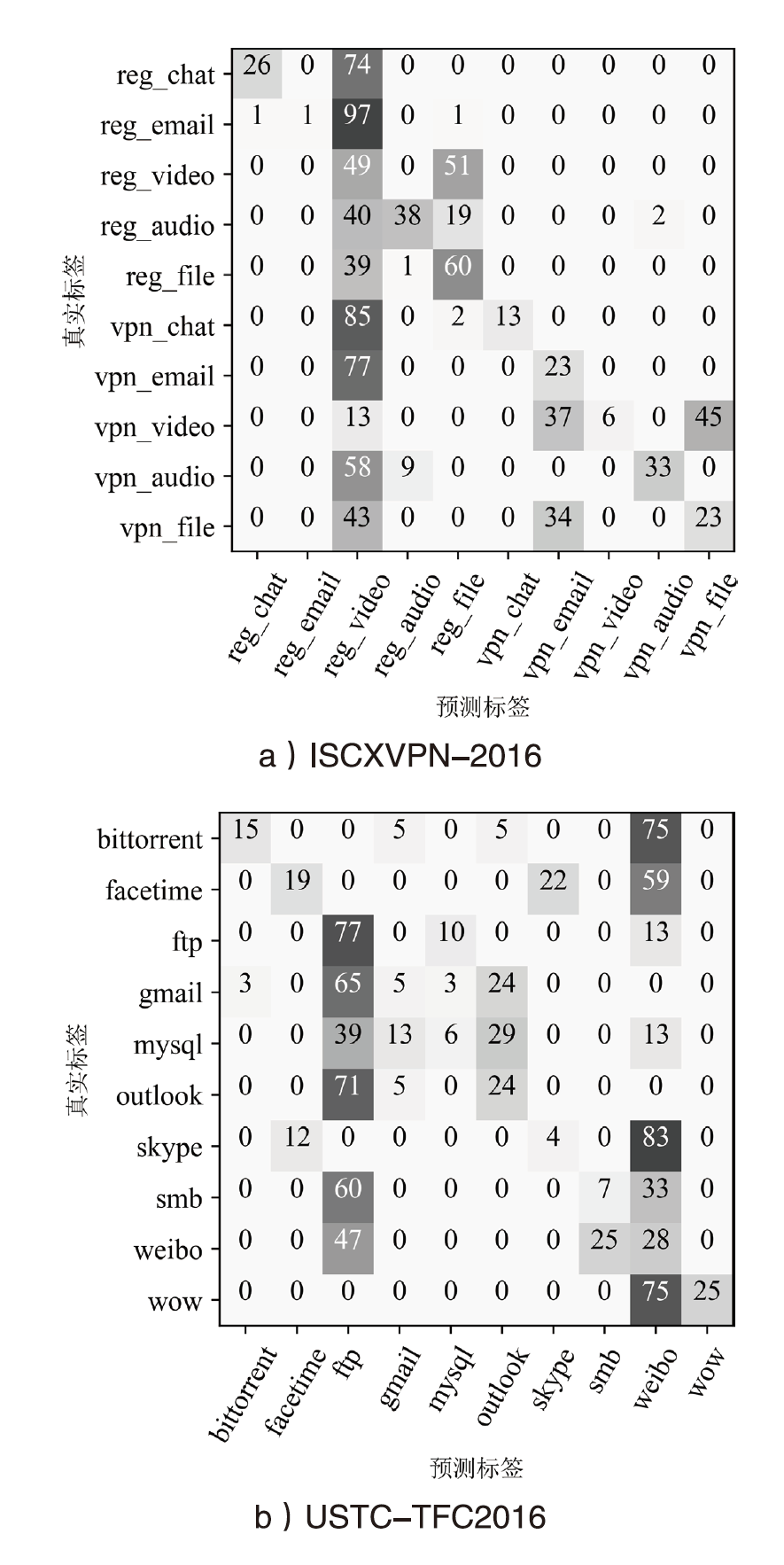
| ISCXVPN- 2016 | reg_chat | 98.1% | 100% | 99.0% | 95.9% | 100% | 1.0% | 2.0% | 6.4% | 5.1% |
| reg_email | 100% | 96.6% | 98.3% | 0 | 0 | 0 | ||||
| reg_video | 100% | 100% | 100% | 1.0% | 8.0% | 2.2% | ||||
| reg_audio | 91.8% | 75.0% | 82.5% | 0 | 0 | 0 | ||||
| reg_file | 98.3% | 97.4% | 97.9% | 36.5% | 39.3% | 37.9% | ||||
| vpn_chat | 96.2% | 97.2% | 96.7% | 0 | 0 | 0 | ||||
| vpn_email | 99.0% | 100% | 99.5% | 0 | 0 | 0 | ||||
| vpn_video | 100% | 100% | 100% | 100% | 4.0% | 7.4% | ||||
| vpn_audio | 76.8% | 92.5% | 83.9% | 0 | 0 | 0 | ||||
| vpn_file | 100% | 100% | 100% | 2.0% | 6.0% | 8.3% | ||||
| USTC- TFC2016 | bittorrent | 90.0% | 94.7% | 92.3% | 96.7% | 0 | 0 | 0 | 6.1% | 6.6% |
| facetime | 96.7% | 100% | 98.3% | 0 | 0 | 0 | ||||
| ftp | 100% | 96.9% | 98.4% | 7.3% | 36.7% | 12.2% | ||||
| gmail | 92.1% | 94.6% | 93.3% | 0 | 0 | 0 | ||||
| mysql | 100% | 93.9% | 96.9% | 0 | 0 | 0 | ||||
| outlook | 95.5% | 95.5% | 95.5% | 18.2% | 4.8% | 7.6% | ||||
| skype | 100% | 95.8% | 97.9% | 0 | 0 | 0 | ||||
| smb | 93.8% | 96.8% | 95.2% | 0 | 0 | 0 | ||||
| 100% | 100% | 100% | 4.2% | 13.9% | 6.4% | |||||
| wow | 100% | 100% | 100% | 0 | 0 | 0 | ||||
| 数据集 | 类别 | 混淆前 | 混淆后 | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PRC | REC | F1-Score | ACC | PRC | REC | F1-Score | ACC | OHR | ||
| ISCXVPN- 2016 | reg_chat | 98.0% | 100% | 99.0% | 96.7% | 95.2% | 25.6% | 40.4% | 27.9% | 5.1% |
| reg_email | 99.3% | 98.6% | 98.9% | 100% | 1.2% | 2.4% | ||||
| reg_video | 99.4% | 99.4% | 99.4% | 8.1% | 48.9% | 13.9% | ||||
| reg_audio | 92.3% | 76.2% | 83.5% | 81.6% | 38.5% | 52.3% | ||||
| reg_file | 100% | 98.0% | 99.0% | 50.4% | 60.0% | 54.8% | ||||
| vpn_chat | 97.8% | 97.8% | 97.8% | 100% | 13.5% | 23.7% | ||||
| vpn_email | 99.4% | 100% | 99.7% | 22.7% | 22.7% | 22.7% | ||||
| vpn_video | 100% | 100% | 100% | 100% | 5.8% | 11.0% | ||||
| vpn_audio | 81.6% | 94.3% | 87.5% | 93.9% | 33.3% | 49.2% | ||||
| vpn_file | 100% | 100% | 100% | 30.3% | 22.7% | 26.0% | ||||
| USTC- TFC2016 | bittorrent | 86.4% | 95.1% | 90.6% | 96.4% | 75.0% | 14.3% | 24.0% | 21.9% | 6.6% |
| facetime | 100% | 96.3% | 98.1% | 62.5% | 28.5% | 28.6% | ||||
| ftp | 96.9% | 93.9% | 95.3% | 18.9% | 76.7% | 30.4% | ||||
| gmail | 94.8% | 97.3% | 96.1% | 28.6% | 8.1% | 12.6% | ||||
| mysql | 93.9% | 96.9% | 95.4% | 38.5% | 7.8% | 13.0% | ||||
| outlook | 97.7% | 95.4% | 96.5% | 36.7% | 26.2% | 30.6% | ||||
| skype | 96.1% | 100% | 98.0% | 14.3% | 4.2% | 6.5% | ||||
| smb | 96.6% | 90.3% | 93.3% | 18.2% | 6.7% | 9.8% | ||||
| 100% | 100% | 100% | 10.8% | 27.8% | 15.5% | |||||
| wow | 100% | 100% | 100% | 66.7% | 25.0% | 36.4% | ||||
| 数据集 | 类别 | 混淆前 | 混淆后 | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PRC | REC | F1-Score | ACC | PRC | REC | F1-Score | ACC | OHR | ||
| ISCXVPN- 2016 | reg_chat | 98.6% | 100% | 99.3% | 96.4% | 93.6% | 37.2% | 53.2% | 36.9% | 5.1% |
| reg_email | 96.9% | 81.6% | 88.6% | 92.6% | 28.7% | 43.9% | ||||
| reg_video | 100% | 100% | 100% | 15.1% | 51.6% | 23.4% | ||||
| reg_audio | 87.5% | 100% | 93.3% | 44.1% | 61.5% | 51.4% | ||||
| reg_file | 100% | 100% | 100% | 27.4% | 52.9% | 36.1% | ||||
| vpn_chat | 97.6% | 96.4% | 97.0% | 41.9% | 29.5% | 34.6% | ||||
| vpn_email | 86.2% | 97.4% | 91.5% | 92.9% | 52.0% | 66.7% | ||||
| vpn_video | 98.7% | 97.5% | 98.1% | 56.1% | 35.9% | 43.8% | ||||
| vpn_audio | 89.4% | 93.3% | 91.3% | 0 | 0 | 0 | ||||
| vpn_file | 100% | 100% | 100% | 29.8% | 15.7% | 20.6% | ||||
| USTC- TFC2016 | bittorrent | 96.9% | 95.0% | 95.9% | 96.8% | 100% | 28.6% | 44.4% | 26.3% | 6.6% |
| facetime | 100% | 100% | 100% | 46.2% | 25.0% | 32.4% | ||||
| ftp | 100% | 100% | 100% | 17.2% | 76.9% | 28.2% | ||||
| gmail | 100% | 90.8% | 95.2% | 6.3% | 6.1% | 6.2% | ||||
| mysql | 92.2% | 94.6% | 93.4% | 36.4% | 11.8% | 17.8% | ||||
| outlook | 100% | 99.1% | 99.6% | 66.7% | 36.4% | 47.1% | ||||
| skype | 94.2% | 93.7% | 93.9% | 0 | 0 | 0 | ||||
| smb | 94.6% | 100% | 97.2% | 100% | 31.3% | 47.6% | ||||
| 92.0% | 100% | 95.8% | 13.0% | 50.0% | 20.6% | |||||
| wow | 99.5% | 94.4% | 96.9% | 12.5% | 13.3% | 12.9% | ||||
| ISCXVPN-2016 | USTC-TFC2016 | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| DSR: 代理 | DSR: Flowpic | DSR: FS-Net | OHR | DSR: 代理 | DSR: Flowpic | DSR: FS-Net | OHR | ||
| 1 | 1 | 83.26% | 36.69% | 31.43% | 3.77% | 81.85% | 39.49% | 36.27% | 4.26% |
| 5 | 2 | 93.60% | 72.07% | 63.13% | 5.05% | 93.92% | 78.10% | 73.68% | 6.64% |
| 5 | 1 | 93.75% | 81.68% | 75.52% | 18.84% | 95.19% | 85.67% | 82.59% | 22.26% |
| 10 | 1 | 94.63% | 88.07% | 84.82% | 25.36% | 96.20% | 89.21% | 87.74% | 29.78% |
| 20 | 1 | 96.85% | 90.33% | 89.61% | 44.13% | 96.52% | 92.86% | 91.05% | 46.58% |
| 方法 | ISCXVPN-2016 | USTC-TFC2016 | ||||
|---|---|---|---|---|---|---|
| DSR: Flowpic | DSR: FS-Net | OHR | DSR: Flowpic | DSR: FS-Net | OHR | |
| WTF-PAD[ | 36.32% | 35.01% | 57.95% | 35.77% | 38.19% | 54.68% |
| Manipulator[ | 65.83% | 62.75% | 26.10% | 73.13% | 71.81% | 24.41% |
| Prism[ | 87.08% | 85.73% | 19.26% | 82.75% | 86.15% | 20.37% |
| TAP | 72.07% | 63.13% | 5.05% | 78.10% | 73.68% | 6.64% |
| TAP | 88.07% | 84.82% | 25.36% | 89.21% | 87.74% | 29.78% |
| [1] | WANG Chenggang, DANI J, LI Xiang, et al. Adaptive Fingerprinting: Website Fingerprinting over Few Encrypted Traffic[C]// ACM. Proceedings of the Eleventh ACM Conference on Data and Application Security and Privacy. New York: ACM, 2021: 149-160. |
| [2] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 1928-1943. |
| [3] | BHAT S, LU D, KWON A, et al. Var-CNN: A Data-Efficient Website Fingerprinting Attack Based on Deep Learning[J]. Proceedings on Privacy Enhancing Technologies, 2019(4): 292-310. |
| [4] | TAYLOR V F, SPOLAOR R, CONTI M, et al. AppScanner: Automatic Fingerprinting of Smartphone Apps from Encrypted Network Traffic[C]// IEEE. 2016 IEEE European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2016: 439-454. |
| [5] | VAN E T, BORTOLAMEOTTI R, CONTINELLA A, et al. FlowPrint: Semi-Supervised Mobile-App Fingerprinting on Encrypted Network Traffic[EB/OL]. (2020-02-26)[2024-04-22]. https://www.ndss-symposium.org/ndss-paper/flowprint-semi-supervised-mobile-app-fingerprinting-on-encrypted-network-traffic/. |
| [6] | SHAPIRA T, SHAVITT Y. FlowPic: Encrypted Internet Traffic Classification is as Easy as Image Recognition[C]// IEEE. IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2019: 680-687. |
| [7] | HOROWICZ E, SHAPIRA T, SHAVITT Y. A Few Shots Traffic Classification with Mini-FlowPic Augmentations[C]// ACM. Proceedings of the 22nd ACM Internet Measurement Conference. New York: ACM, 2022: 647-654. |
| [8] | LIU Chang, HE Longtao, XIONG Gang, et al. FS-Net: A Flow Sequence Network for Encrypted Traffic Classification[C]// IEEE. IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2019: 1171-1179. |
| [9] | GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[EB/OL]. (2022-11-02)[2024-04-22]. http://arxiv.org/abs/1412.6572. |
| [10] | MADRY A, MAKELOV A, SCHMIDT L, et al. Towards Deep Learning Models Resistant to Adversarial Attacks[EB/OL]. (2019-09-04)[2024-04-22]. https://arxiv.org/abs/1706.06083v4. |
| [11] | BROWN T B, MANÉ D, ROY A, et al. Adversarial Patch[EB/OL]. (2018-05-16)[2024-04-22]. https://doi.org/10.48550/arXiv.1712.09665. |
| [12] | MOOSAVI-DEZFOOLI S M, FAWZI A, FROSSARD P. DeepFool: A Simple and Accurate Method to Fool Deep Neural Networks[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2016: 2574-2582. |
| [13] | XIAO Chaowei, LI Bo, ZHU Junyan, et al. Generating Adversarial Examples with Adversarial Networks[EB/OL]. (2023-03-14)[2024-04-22]. http://arxiv.org/abs/1801.02610. |
| [14] | RAHMAN M S, IMANI M, MATHEWS N, et al. Mockingbird: Defending against Deep-Learning-Based Website Fingerprinting Attacks with Adversarial Traces[J]. IEEE Transactions on Information Forensics and Security, 2020(16): 1594-1609. |
| [15] | HOU Chengshang, GOU Gaopeng, SHI Junzheng, et al. WF-GAN: Fighting Back against Website Fingerprinting Attack Using Adversarial Learning[C]// IEEE. 2020 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2020: 1-7. |
| [16] | LIU Hao, DANI J, YU Hongkai, et al. AdvTraffic: Obfuscating Encrypted Traffic with Adversarial Examples[C]// IEEE. 2022 IEEE/ACM 30th International Symposium on Quality of Service (IWQoS). New York: IEEE, 2022: 1-10. |
| [17] | LI Wenhao, ZHANG Xiaoyu, BAO Huaifeng, et al. Prism: Real-Time Privacy Protection against Temporal Network Traffic Analyzers[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2524-2537. |
| [18] |
YANG Youhuan, SUN Lei, DAI Leyu, et al. Generate Transferable Adversarial Network Traffic Using Reversible Adversarial Padding[J]. Computer Science, 2023, 50(12): 359-367.
doi: 10.11896/jsjkx.221000155 |
|
杨有欢, 孙磊, 戴乐育, 等. 使用RAP生成可传输的对抗网络流量[J]. 计算机科学, 2023, 50(12): 359-367.
doi: 10.11896/jsjkx.221000155 |
|
| [19] | HAN Dongqi, WANG Zhiliang, ZHONG Ying, et al. Evaluating and Improving Adversarial Robustness of Machine Learning-Based Network Intrusion Detectors[J]. IEEE Journal on Selected Areas in Communications, 2021, 39(8): 2632-2647. |
| [20] | QIAO Litao, WU Bang, YIN Shuijun, et al. Resisting DNN-Based Website Fingerprinting Attacks Enhanced by Adversarial Training[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5375-5386. |
| [21] | GONG Jiajun, ZHANG Wuqi, ZHANG C, et al. Surakav: Generating Realistic Traces for a Strong Website Fingerprinting Defense[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 1558-1573. |
| [22] | SHAN S, BHAGOJI A N, ZHENG Haitao, et al. A Real-Time Defense against Website Fingerprinting Attacks[EB/OL]. (2021-02-08)[2024-04-22]. https://doi.org/10.48550/arXiv.2102.04291. |
| [23] | ZHU Ye, FU Xinwen, GRAHAM B, et al. Correlation-Based Traffic Analysis Attacks on Anonymity Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2010, 21(7): 954-967. |
| [24] | LI Huaxin, ZHU Haojin, MA Di. Demographic Information Inference through Meta-Data Analysis of Wi-Fi Traffic[J]. IEEE Transactions on Mobile Computing, 2018, 17(5): 1033-1047. |
| [25] | LI Huaxin, XU Zheyu, ZHU Haojin, et al. Demographics Inference through Wi-Fi Network Traffic Analysis[C]// IEEE. IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications. New York: IEEE, 2016: 1-9. |
| [26] | YANG Bowen, LIU Dong. Research on Network Traffic Identification Based on Machine Learning and Deep Packet Inspection[C]// IEEE. 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC). New York: IEEE, 2019: 1887-1891. |
| [27] | LOTFOLLAHI M, JAFARI S M, SHIRALI H Z R, et al. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3): 1999-2012. |
| [28] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [29] | CHEN Zihan, CHENG Guang, XU Ziheng, et al. A Survey on Internet Encrypted Traffic Detection, Classification and Identification[J]. Chinese Journal of Computers, 2023, 46(5): 1060-1085. |
| 陈子涵, 程光, 徐子恒, 等. 互联网加密流量检测、分类与识别研究综述[J]. 计算机学报, 2023, 46(5): 1060-1085. | |
| [30] | DONG Cong, LU Zhigang, CUI Zelin, et al. MBTree: Detecting Encryption RATs Communication Using Malicious Behavior Tree[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3589-3603. |
| [31] | SHAPIRA T, SHAVITT Y. FlowPic: A Generic Representation for Encrypted Traffic Classification and Applications Identification[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1218-1232. |
| [32] | SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing Properties of Neural Networks[EB/OL]. (2022-12-20)[2024-04-22]. https://doi.org/10.48550/arXiv.1312.6199. |
| [33] | CARLINI N, WAGNER D. Towards Evaluating the Robustness of Neural Networks[C]// IEEE. 2017 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2017: 39-57. |
| [34] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11): 139-144. |
| [35] | PAPERNOT N, MCDANIEL P, GOODFELLOW I, et al. Practical Black-Box Attacks against Machine Learning[C]// ACM. Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security. New York: ACM, 2017: 506-519. |
| [36] | HU Yongjin, TIAN Jin, MA Jun. A Novel Way to Generate Adversarial Network Traffic Samples against Network Traffic Classification[EB/OL]. (2021-01-01)[2024-04-22]. https://doi.org/10.1155/2021/7367107. |
| [37] | JUAREZ M, IMANI M, PERRY M, et al. Toward an Efficient Website Fingerprinting Defense[M]. Heidelberg: Springer, 2016. |
| [38] | WANG Tao, GOLDBERG I. Walkie-Talkie: An Efficient Defense against Passive Website Fingerprinting Attacks[C]// USENIX. Proceedings of the 26th USENIX Conference on Security Symposium. Berkeley: USENIX, 2017: 1375-1390. |
| [39] | ABUSNAINA A, JANG R, KHORMALI A, et al. DFD: Adversarial Learning-Based Approach to Defend against Website Fingerprinting[C]// IEEE. IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2020: 2459-2468. |
| [40] | YIN Haoyu, LIU Yingjian, LI Yue, et al. Defeating Deep Learning Based De-Anonymization Attacks with Adversarial Example[EB/OL]. (2023-11-01)[2024-04-22]. https://doi.org/10.1016/j.jnca.2023.103733. |
| [41] | NASR M, BAHRAMALI A, HOUMANSADR A. Defeating DNN-Based Traffic Analysis Systems in Real-Time with Blind Adversarial Perturbations[EB/OL]. (2021-07-10)[2024-04-22]. https://www.usenix.org/conference/usenixsecurity21/presentation/nasr. |
| [42] | QIN Tao, WANG Lei, LIU Zhaoli, et al. Robust Application Identification Methods for P2P and VoIP Traffic Classification in Backbone Networks[J]. Knowledge-Based Systems, 2015, 82: 152-162. |
| [43] | DRAPER-GIL G, LASHKARI A H, MAMUN M S I, et al. Characterization of Encrypted and VPN Traffic Using Time-Related Features[C]// IEEE. The 2nd International Conference on Information Systems Security and Privacy. New York: IEEE, 2016: 407-414. |
| [1] | XU Ruzhi, ZHANG Ning, LI Min, LI Zixuan. Research on a High Robust Detection Model for Malicious Software [J]. Netinfo Security, 2024, 24(8): 1184-1195. |
| [2] | XU Zirong, GUO Yanping, YAN Qiao. Malicious Software Adversarial Defense Model Based on Feature Severity Ranking [J]. Netinfo Security, 2024, 24(4): 640-649. |
| [3] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [4] | ZHANG Xuan, WAN Liang, LUO Heng, YANG Yang. Automated Botnet Detection Method Based on Two-Stage Graph Learning [J]. Netinfo Security, 2024, 24(12): 1933-1947. |
| [5] | WANG Qiang, LIU Yizhi, LI Tao, HE Xiaochuan. Review of Encrypted Network Traffic Anonymity and Systemic Defense Tactics [J]. Netinfo Security, 2024, 24(10): 1484-1492. |
| [6] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [7] | LI Chenwei, ZHANG Hengwei, GAO Wei, YANG Bo. Transferable Image Adversarial Attack Method with AdaN Adaptive Gradient Optimizer [J]. Netinfo Security, 2023, 23(7): 64-73. |
| [8] | TONG Xin, JIN Bo, WANG Binjun, ZHAI Hanming. A Malicious SMS Detection Method Blending Adversarial Enhancement and Multi-Task Optimization [J]. Netinfo Security, 2023, 23(10): 21-30. |
| [9] | QIN Yifang, ZHANG Jian, LIANG Chen. Research on Feature Extraction Technology of Electronic Medical Record Data Based on Neural Networks [J]. Netinfo Security, 2023, 23(10): 70-76. |
| [10] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| [11] | XIA Qiang, HE Peisong, LUO Jie, LIU Jiayong. An Efficient Enhancement Algorithm of Cover Image Based on Universal Adversarial Noise [J]. Netinfo Security, 2022, 22(2): 64-75. |
| [12] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [13] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [14] | YI Xiaoyang, ZHANG Jian. Image-based Phishing Email Detection Method and Implementation [J]. Netinfo Security, 2021, 21(9): 52-58. |
| [15] | LEI Yu, LIU Jia, LI Jun, KE Yan. Research and Implementation of a Image Steganography Method Based on Conditional Generative Adversarial Networks [J]. Netinfo Security, 2021, 21(11): 48-57. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||