Netinfo Security ›› 2024, Vol. 24 ›› Issue (3): 411-426.doi: 10.3969/j.issn.1671-1122.2024.03.007
Previous Articles Next Articles
Unsupervised Network Intrusion Detection Method Based on Ensemble Learning
JIANG Rong1, LIU Haitian1, LIU Cong2( )
)
- 1. College of Computer, National University of Defence Technology, Changsha 410073, China
2. Information Center, Logistic Support Department of Central Military Commission, Beijing 100842, China
-
Received:2023-11-17Online:2024-03-10Published:2024-04-03 -
Contact:LIU Cong E-mail:congliu2005@163.com
CLC Number:
Cite this article
JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning[J]. Netinfo Security, 2024, 24(3): 411-426.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.03.007
| 攻击 | 工具 | |
|---|---|---|
| CIC-IDS 2017 | CIC-IDS 2018 | |
| Brute Force | FTP-Patator SSH-Patator | FTP-Patator SSH-Patator |
| DoS | DoS slowloris DoS Slowhttptest DoS Hulk DoS GoldenEye | Hulk, GoldenEye, Slowloris, Slowhttptest, Heartleech |
| Heartbleed | Heartbleed Port 444 | — |
| Web Attack | Brute XSS Sql Injection | DVWA XSS and Brute-force |
| Infiltration | Dropbox download Cool disk | First level: Dropbox download Second Level: Nmap and portscan |
| Botnet | Botnet-ARES | Ares screenshots and key logging |
| Port Scan | Port (sS, sT, sF, sX, sN, sP, sV, sU, sO, sA, sW, sR, sL, sI, b) | — |
| DDoS | DDoS-LOIT | Low Orbit Ion Canon (LOIC) for UDP, TCP, or HTTP requests |
| 序号 | 攻击类型 | 攻击数量/个 |
|---|---|---|
| 1 | DoS attacks-SlowHTTPTest | 139890 |
| DoS attacks -Hulk | 461912 | |
| 2 | DoS attacks -GoldenEye | 41508 |
| DoS attacks-Slowloris | 10990 | |
| 3 | DDoS attack -LOIC-UDP | 1730 |
| DDoS attack-HOIC | 686012 | |
| 4 | DDoS attacks -LOIC-HTTP | 576191 |
| 5 | Brute force-XSS | 151 |
| Brute force-web | 362 | |
| 6 | SSH-brute force | 187589 |
| FTP-brute force | 193360 |
| 方法 | 精确度 | 召回率 | F1 |
|---|---|---|---|
| PCA | 60.66% | 37.69% | 0.47 |
| KNN | 45.51% | 18.98% | 0.27 |
| FB | 48.98% | 19.36% | 0.28 |
| AE | 80.59% | 42.36% | 0.55 |
| EGAN | 92.00% | 95.82% | 0.94 |
| MAD-GAN* | 94.92% | 19.14% | 0.32 |
| MAD-GAN** | 81.58% | 96.33% | 0.88 |
| MAD-GAN*** | 86.91% | 94.79% | 0.90 |
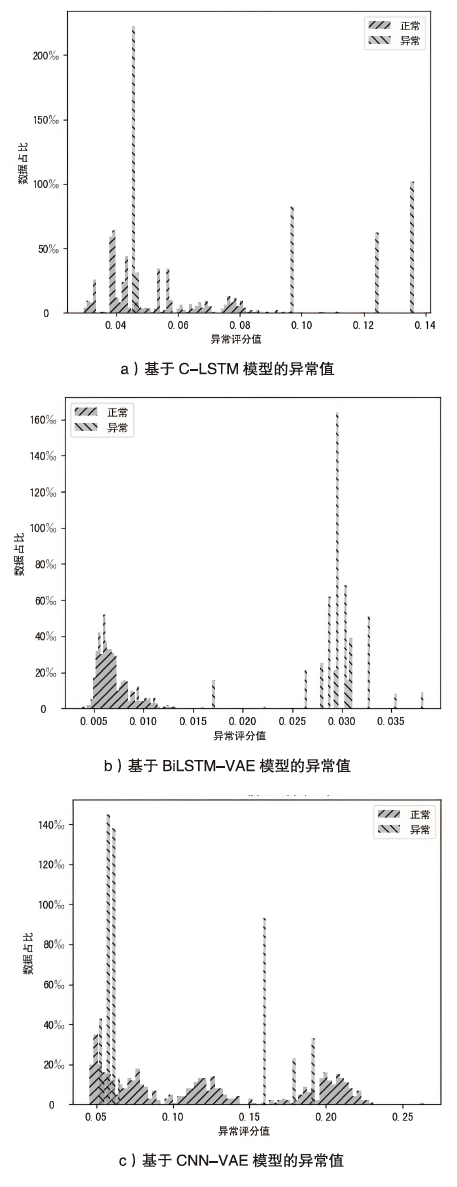
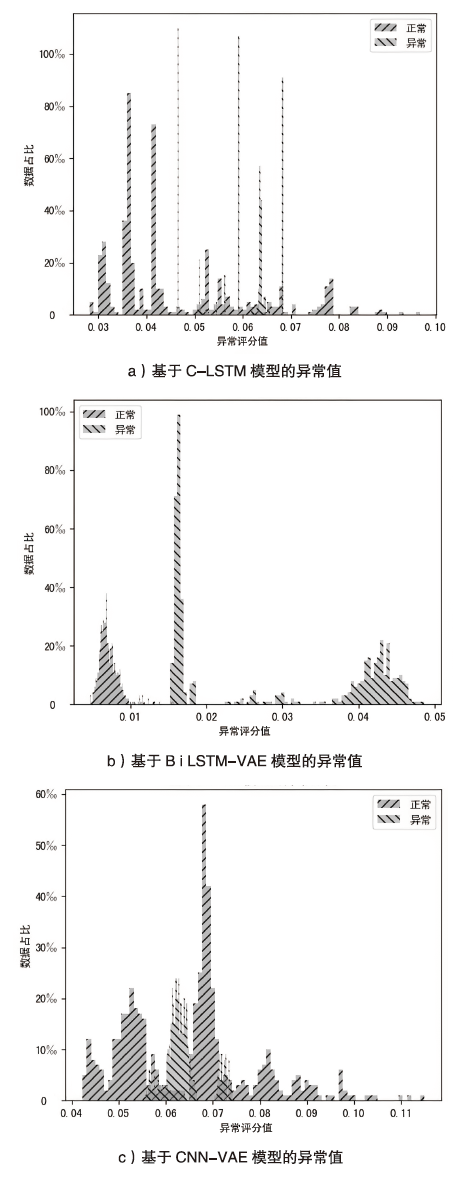
| Bi-LSTM-VAE | 97.10% | 99.52% | 0.98 |
| C-LSTM | 97.48% | 97.98% | 0.98 |
| CNN-VAE | 99.71% | 71.64% | 0.83 |
| Proposed-Vote | 99.22% | 99.11% | 0.99 |
| Proposed-And | 99.98% | 71.36% | 0.83 |
| Proposed-Or | 95.09% | 99.73% | 0.97 |
| 攻击类型 | UTEN-IDS | AE-IDS | AE | C-LSTM | Bi-LSTM-VAE | CNN-VAE | Vote | And | Or |
|---|---|---|---|---|---|---|---|---|---|
| DoS attacks- SlowHTTPTest | 94.7% | 99.8% | 85.9% | 99.1% | 99.6% | 94.7% | 99.9% | 97.8% | 96.2% |
| DoS attacks -Hulk | 48.6% | 63.2% | 41.6% | 99.9% | 95.8% | 91.2% | 99.9% | 98.1% | 94.1% |
| DoS attacks -GoldenEye | 94.9% | 49.4% | 87.9% | 79.2% | 94.1% | 50.5% | 94.3% | 50.6% | 73.0% |
| DoS attacks-Slowloris | 94.7% | 71.2% | 87.8% | 83.1% | 98.3% | 82.5% | 83.3% | 84.5% | 96.6% |
| DDoS attack -LOIC-UDP | 91.6% | 98.5% | 86.8% | 51.0% | 91.7% | 96.7% | 97.0% | 82.6% | 51.1% |
| DDoS attack-HOIC | 92.5% | 52.5% | 87.7% | 69.8% | 95.9% | 99.6% | 96.0% | 59.4% | 50.0% |
| DDoS attacks -LOIC-HTTP | 88.9% | 54.4% | 80.5% | 72.5% | 83.2% | 57.7% | 78.9% | 80.7% | 55.8% |
| Brute force-XSS | 66.8% | 44.9% | 55.8% | 73.66% | 99.5% | 58.9% | 95.3% | 58.9% | 76.6% |
| Brute force-web | 72.3% | 58.8% | 69.5% | 68.56% | 98.8% | 62.2% | 98.7% | 63.4% | 68.5% |
| SSH-brute force | 93.2% | 57.5% | 80.4% | 76.87% | 96.1% | 64.0% | 79.3% | 96.9% | 56.3% |
| FTP-brute force | 95.1% | 79.4% | 80.4% | 81.71% | 99.9% | 59.3% | 82.4% | 94.0% | 64.5% |
| 攻击类型 | UTEN- IDS | AE-IDS | AE | C- LSTM | Bi-LSTM- VAE | CNN-VAE | Vote | And | Or |
|---|---|---|---|---|---|---|---|---|---|
| DoS attacks- SlowHTTPTest | 96.7% | 99.8% | 91.7% | 98.8% | 99.5% | 94.2% | 99.9% | 98.2% | 95.3% |
| DoS attacks -Hulk | 14.6% | 41.7% | 18.7% | 99.9% | 91.6% | 92.3% | 99.9% | 98.7% | 97.0% |
| DoS attacks -GoldenEye | 80.7% | 26.2% | 63.3% | 44.0% | 82.9% | 49.2% | 89.2% | 49.2% | 43.8% |
| DoS attacks -Slowloris | 52.6% | 19.8% | 31.3% | 70.0% | 92.9% | 66.6% | 71.2% | 90.0% | 72.1% |
| DDoS attack -LOIC-UDP | 22.3% | 62.2% | 15.4% | 51.9% | 92.7% | 96.7% | 97.9% | 82.1% | 32.1% |
| DDoS attack-HOIC | 99.2% | 9.51% | 98.7% | 28.6% | 68.6% | 99.8% | 74.4% | 16.1% | 49.9% |
| DDoS attacks -LOIC-HTTP | 93.0% | 63.6% | 95.4% | 49.1% | 80.0% | 32.1% | 58.0% | 80.3% | 20.2% |
| Brute force-XSS | 0.72% | 0.10% | 0.20% | 27.0% | 93.2% | 64.8% | 91.2% | 64.8% | 27.0% |
| Brute force-web | 2.11% | 0.48% | 0.78% | 35.5% | 97.3% | 62.5% | 84.7% | 69.6% | 32.4% |
| SSH-brute force | 94.7% | 76.7% | 87.7% | 69.0% | 94.1% | 52.5% | 73.6% | 95.2% | 39.5% |
| FTP-brute force | 96.7% | 87.5% | 88.1% | 77.1% | 99.9% | 51.2% | 78.0% | 95.0% | 54.0% |
| [1] | MOHAMMED S S, HUSSAIN R, SENKO O, et al. A New Machine Learning-Based Collaborative DDoS Mitigation Mechanism in Software-Defined Network[C]// IEEE. 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob). New York: IEEE, 2018: 1-8. |
| [2] | DENNING D E. An Intrusion-Detection Model[J]. IEEE Transactions on Software Engineering, 1987, 13(2): 222-232. |
| [3] | MIRSKY Y, DOITSHMAN T, ELOVICI Y, et al. Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection[EB/OL]. (2018-05-27)[2023-05-26]. https://arxiv.org/abs/1802.09089. |
| [4] | ZHANG Tianyue, CHEN Wei, LIU Yuxiao, et al. An Intrusion Detection Method Based on Stacked Sparse Autoencoder and Improved Gaussian Mixture Model[J]. Computers & Security, 2023(128): 103-144. |
| [5] | ATALLAH M, SZPANKOWSKI W, GWADERA R. Detection of Significant Sets of Episodes in Event Sequences[C]// IEEE. Fourth IEEE International Conference on Data Mining (ICDM’04). New York: IEEE, 2004: 3-10. |
| [6] | CHANDOLA V, BANERJEE A, KUMAR V. Anomaly Detection: A Survey[J]. ACM Computing Surveys (CSUR), 2009, 41(3): 1-58. |
| [7] |
AHMED M, MAHMOOD A N. Novel Approach for Network Traffic Pattern Analysis Using Clustering-Based Collective Anomaly Detection[J]. Annals of Data Science, 2015, 2(1): 111-130.
doi: 10.1007/s40745-015-0035-y URL |
| [8] | AHMED M, MAHMOOD A N, HU Jiankun. A Survey of Network Anomaly Detection Techniques[J]. Journal of Network and Computer Applications, 2016(60): 19-31. |
| [9] | KOTSIANTIS S B, ZAHARAKIS I, PINTELAS P. Supervised Machine Learning: A Review of Classification Techniques[J]. Emerging Artificial Intelligence Applications in Computer Engineering, 2007, 160(1): 3-24. |
| [10] | KAUR H, PANNU H S. Anomaly Detection Survey for Information Security[C]// ACM. The 10th International Conference on Security of Information and Networks. New York: ACM, 2017: 251-258. |
| [11] | KIM T Y, CHO S B. Web Traffic Anomaly Detection Using C-LSTM Neural Networks[J]. Expert Systems with Applications, 2018(106): 66-76. |
| [12] |
YIN Chunyong, ZHANG Sun, WANG Jin, et al. Anomaly Detection Based on Convolutional Recurrent Autoencoder for IoT Time Series[J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2020, 52(1): 112-122.
doi: 10.1109/TSMC.2020.2968516 URL |
| [13] | AMER M, GOLDSTEIN M, ABDENNADHER S. Enhancing One-Class Support Vector Machines for Unsupervised Anomaly Detection[C]// ACM. The ACM SIGKDD Workshop on Outlier Detection and Description(ODD’13). New York: ACM, 2013: 8-15. |
| [14] | BREUNIG M M, KRIEGEL H P, NG R T, et al. LOF: Identifying Density-Based Local Outliers[C]// ACM. The 2000 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2000: 93-104. |
| [15] | TANG Jian, CHEN Zhixiang, FU A W C, et al. Enhancing Effectiveness of Outlier Detections for Low Density Patterns[C]// Springer. Knowledge Discovery and Data Mining:6th Pacific-Asia Conference (PAKDD 2002). Heidelberg: Springer, 2002: 535-548. |
| [16] |
HE Zengyou, XU Xiaofei, DENG Shengchun. Discovering Cluster-Based Local Outliers[J]. Pattern Recognition Letters, 2003, 24(9): 1641-1650.
doi: 10.1016/S0167-8655(03)00003-5 URL |
| [17] | GOLDSTEIN M, DENGEL A. Histogram-Based Outlier Score (HBOS): A Fast Unsupervised Anomaly Detection Algorithm[J]. KI-2012: Poster and Demo Track, 2012(1): 59-63. |
| [18] | YU Qin, LYU Jibin, JIANG Lirui. An Improved ARIMA-Based Traffic Anomaly Detection Algorithm for Wireless Sensor Networks[EB/OL]. (2016-01-18)[2023-05-26]. https://journals.sagepub.com/doi/10.1155/2016/9653230. |
| [19] | YAACOB A H, TAN I K T, CHIEN S F, et al. Arima Based Network Anomaly Detection[C]// IEEE. 2010 Second International Conference on Communication Software and Networks. New York: IEEE, 2010: 205-209. |
| [20] | XIA Yan, CAO Xudong, WEN Fang, et al. Learning Discriminative Reconstructions for Unsupervised Outlier Removal[C]// IEEE. The IEEE International Conference on Computer Vision. New York: IEEE, 2015: 1511-1519. |
| [21] | KIEU T, YANG Bin, JENSEN C S. Outlier Detection for Multidimensional Time Series Using Deep Neural Networks[C]// IEEE. 2018 19th IEEE International Conference on Mobile Data Management (MDM). New York: IEEE, 2018: 125-134. |
| [22] | MALHOTRA P, RAMAKRISHNAN A, ANAND G, et al. LSTM-Based Encoder-Decoder for Multi-Sensor Anomaly Detection[EB/OL]. (2016-07-11)[2023-05-26]. https://arxiv.org/abs/1607.00148. |
| [23] | CHEN Jinghui, SATHE S, AGGARWAL C, et al. Outlier Detection with Autoencoder Ensembles[C]// SIAM. The 2017 SIAM International Conference on Data Mining. Philadelphia: SIAM, 2017: 90-98. |
| [24] | KIEU T, YANG Bin, GUO Chenjuan, et al. Outlier Detection for Time Series with Recurrent Autoencoder Ensembles[C]// ACM. The 28th International Joint Conference on Artificial Intelligence (IJCAI’19). New York: ACM, 2019: 2725-2732. |
| [25] | MUNIR M, SIDDIQUI S A, DENGEL A, et al. DeepAnT: A Deep Learning Approach for Unsupervised Anomaly Detection in Time Series[J]. IEEE Access, 2018(7): 1991-2005. |
| [26] | PARK S H, PARK H J, CHOI Y J. RNN-Based Prediction for Network Intrusion Detection[C]// IEEE. 2020 International Conference on Artificial Intelligence in Information and Communication (ICAIIC). New York: IEEE, 2020: 572-574. |
| [27] | DU Min, LI Feifei, ZHENG Guineng, et al. Deeplog: Anomaly Detection and Diagnosis from System Logs through Deep Learning[C]// ACM. The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1285-1298. |
| [28] | LAPTEV N, AMIZADEH S, FLINT I. Generic and Scalable Framework for Automated Time-Series Anomaly Detection[C]// ACM. The 21th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2015: 1939-1947. |
| [29] | LAVIN A, AHMAD S. Evaluating Real-Time Anomaly Detection Algorithms-the Numenta Anomaly Benchmark[C]// IEEE. 2015 IEEE 14th International Conference on Machine Learning and Applications (ICMLA). New York: IEEE, 2015: 38-44. |
| [30] | AHMAD S, LAVIN A, PURDY S, et al. Unsupervised Real-Time Anomaly Detection for Streaming Data[J]. Neurocomputing, 2017(262): 134-147. |
| [31] | SCHLEGL T, SEEBÖCK P, WALDSTEIN S M, et al. Unsupervised Anomaly Detection with Generative Adversarial Networks to Guide Marker Discovery[C]// Springer. International Conference on Information Processing in Medical Imaging(IPMI). Heidelberg: Springer, 2017: 146-157. |
| [32] | LI Dan, CHEN Dacheng, JIN Baihong, et al. MAD-GAN: Multivariate Anomaly Detection for Time Series Data with Generative Adversarial Networks[C]// Springer. International Conference on Artificial Neural Networks. Heidelberg: Springer, 2019: 703-716. |
| [33] | BASHAR M A, NAYAK R. TAnoGAN: Time Series Anomaly Detection with Generative Adversarial Networks[C]// IEEE. 2020 IEEE Symposium Series on Computational Intelligence (SSCI). New York: IEEE, 2020: 1778-1785. |
| [34] | GEIGER A, LIU Dongyu, ALNEGHEIMISH S, et al. TadGAN: Time Series Anomaly Detection Using Generative Adversarial Networks[C]// IEEE. 2020 IEEE International Conference on Big Data (Big Data). New York: IEEE, 2020: 33-43. |
| [35] |
WU Nannan, CHEN Feng, LI Jianxin, et al. A Nonparametric Approach to Uncovering Connected Anomalies by Tree Shaped Priors[J]. IEEE Transactions on Knowledge and Data Engineering, 2018, 31(10): 1849-1862.
doi: 10.1109/TKDE.69 URL |
| [36] | WU Nannan, WANG Wenjun, CHEN Feng, et al. Uncovering Specific-Shape Graph Anomalies in Attributed Graphs[C]// ACM. The AAAI Conference on Artificial Intelligence (AAAI’19). New York: ACM, 2019, 33(1): 5433-5440. |
| [37] | AN Jinwong, CHO S. Variational Autoencoder Based Anomaly Detection Using Reconstruction Probability[J]. Special Lecture on IE, 2015, 2(1): 1-18. |
| [38] | YENTER A, VERMA A. Deep CNN-LSTM with Combined Kernels from Multiple Branches for IMDb Review Sentiment Analysis[C]// IEEE. 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON). New York: IEEE, 2017: 540-546. |
| [39] | SUTSKEVER I, VINYALS O, LE Q V. Sequence to Sequence Learning with Neural Networks[EB/OL]. (2014-12-08)[2023-05-26]. https://dl.acm.org/doi/10.5555/2969033.2969173. |
| [40] | GERS F A, ECK D, SCHMIDHUBER J. Applying LSTM to Time Series Predictable through Time-Window Approaches[C]// Springer. International Conference on Artificial Neural Networks. Heidelberg: Springer, 2001: 669-676. |
| [41] |
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
doi: 10.1162/neco.1997.9.8.1735 pmid: 9377276 |
| [42] | LONG Mingsheng, CAO Zhangjie, WANG Janmin, et al. Learning Multiple Tasks with Multilinear Relationship Networks[J]. (2015-06-06)[2023-05-26]. https://arxiv.org/abs/1506.02117. |
| [43] | CIRSTEA R G, MICU D V, MURESAN G M, et al. Correlated Time Series Forecasting Using Multi-Task Deep Neural Networks[C]// ACM. The 27th ACM International Conference on Information and Knowledge Management. New York: ACM, 2018: 1527-1530. |
| [44] | KIEU T, YANG Bin, GUO Chenjuan, et al. Distinguishing Trajectories from Different Drivers Using Incompletely Labeled Trajectories[C]// ACM. The 27th ACM International Conference on Information and Knowledge Management. New York: ACM, 2018: 863-872. |
| [45] | TAVALLAEE M, BAGHERI E, LU Wei, et al. A Detailed Analysis of the KDD CUP 99 Data Set[C]// IEEE. 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications. New York: IEEE, 2009: 1-6. |
| [46] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[EB/OL]. (2018-01-22)[2023-05-26]. https://www.scitepress.org/Papers/2018/66398/66398.pdf. |
| [47] | ZENATI H, FOO C S, LECOUAT B, et al. Efficient GAN-Based Anomaly Detection[EB/OL]. (2019-05-01)[2023-05-26]. https://arxiv.org/abs/1802.06222. |
| [48] | LI XuKui, CHEN Wei, ZHANG Qianru, et al. Building Auto-Encoder Intrusion Detection System Based on Random Forest Feature Selection[EB/OL]. (2020-08-01)[2023-05-26]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820301231. |
| [49] | LIANG Chao, SHANMUGAM B, AZAM S, et al. Intrusion Detection System for Internet of Things Based on a Machine Learning Approach[C]// IEEE. 2019 International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN). New York: IEEE, 2019: 1-6. |
| [50] | RAMYACHITRA D, MANIKANDAN P. Imbalanced Dataset Classification and Solutions: A Review[J]. International Journal of Computing and Business Research (IJCBR), 2014, 5(4): 1-29. |
| [1] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [2] | QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders [J]. Netinfo Security, 2023, 23(9): 1-11. |
| [3] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [4] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [5] | WU Shenglin, LIU Wanggen, YAN Ming, WU Jie. A Real-Time Anomaly Detection System for Container Clouds Based on Unsupervised System Call Rule Generation [J]. Netinfo Security, 2023, 23(12): 91-102. |
| [6] | LIAO Liyun, ZHANG Bolei, WU Lifa. IoT Anomaly Detection Model Based on Cost-Sensitive Learning [J]. Netinfo Security, 2023, 23(11): 94-103. |
| [7] | ZHANG Yuchen, LI Lianghui, MA Chenyang, ZHOU Hongwei. A Log Anomaly Detection Method with Variables [J]. Netinfo Security, 2023, 23(10): 16-20. |
| [8] | XING Lingkai, ZHANG Jian. Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC [J]. Netinfo Security, 2023, 23(10): 64-69. |
| [9] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [10] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| [11] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [12] | ZHOU Jingyi, LI Hongjiao. False Data Injection Attack Detection Method against PMU Measurements [J]. Netinfo Security, 2022, 22(5): 75-83. |
| [13] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [14] | XU Ruzhi, LYU Changran, LONG Yan, LIU Yuanbin. Defense Research of High-Hidden Data Attack in Industry Control System [J]. Netinfo Security, 2022, 22(12): 34-46. |
| [15] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||