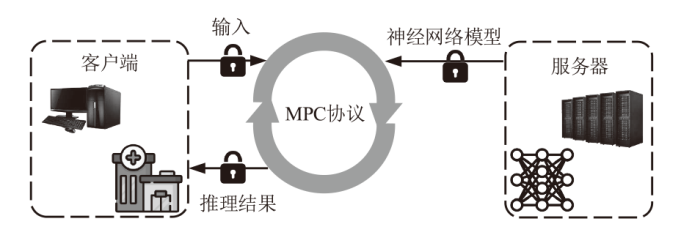
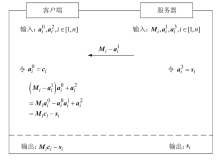
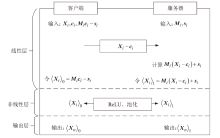
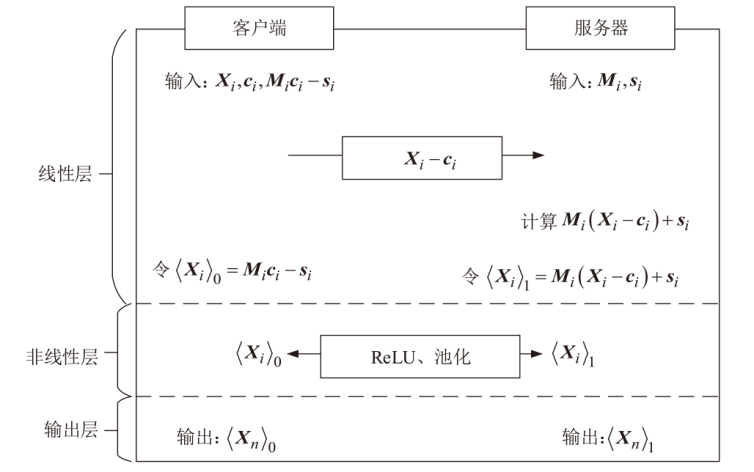
Netinfo Security ›› 2023, Vol. 23 ›› Issue (7): 22-30.doi: 10.3969/j.issn.1671-1122.2023.07.003
Previous Articles Next Articles
Efficient Neural Network Inference Protocol Based on Secure Two-Party Computation
XU Chungen1, XUE Shaokang2( ), XU Lei1, ZHANG Pan3
), XU Lei1, ZHANG Pan3
- 1. School of Mathematics and Statistics, Nanjing University of Science and Technology, Nanjing 210094, China
2. School of Computer Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
3. School of Cyber Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
-
Received:2023-02-20Online:2023-07-10Published:2023-07-14
CLC Number:
Cite this article
XU Chungen, XUE Shaokang, XU Lei, ZHANG Pan. Efficient Neural Network Inference Protocol Based on Secure Two-Party Computation[J]. Netinfo Security, 2023, 23(7): 22-30.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.07.003
| [1] | RATHOR K, PATIL K, TARUN M S, et al. A Novel and Efficient Method to Detect the Face Coverings to Ensure the Safety Using Comparison Analysis[C]// IEEE. The International Conference on Edge Computing and Applications. New York: IEEE, 2022: 1664-1667. |
| [2] |
BHANGALE K, KOTHANDARAMAN M. Speech Emotion Recognition Based on Multiple Acoustic Features and Deep Convolutional Neural Network[J]. Electronics, 2023, 12(4): 839-855.
doi: 10.3390/electronics12040839 URL |
| [3] | ZHANG Ge, ZHEN Peng, YAN Chaokun, et al. A Novel Liver Cancer Diagnosis Method Based on Patient Similarity Network and DenseGCN[EB/OL]. (2022-12-01) [2023-01-15]. https://www.nature.com/arti-cles/s41598-022-10441-3. |
| [4] |
ZIOVIRIS G, KOLOMVATSOS K, STAMOULIS G. Credit Card Fraud Detection Using a Deep Learning Multistage Model[J]. The Journal of Supercomputing, 2022, 78(12): 14571-14596.
doi: 10.1007/s11227-022-04465-9 |
| [5] | YAO A C. Protocols for Secure Computations[C]// IEEE. 23rd Annual Symposium on Foundations of Computer Science. New York: IEEE, 1982: 160-164. |
| [6] | BOGETOFT P, CHRISTENSEN D L, DAMGARD I, et al. Secure Multiparty Computation Goes Live[C]// Springer. 13th International Conference on Financial Cryptography and Data Security. Heidelberg: Springer, 2009: 325-343. |
| [7] | MA J P, CHOW S. Secure-Computation-Friendly Private Set Intersection from Oblivious Compact Graph Evaluation[C]// ACM. 2022 ACM on Asia Conference on Computer and Communications Security. New York: ACM, 2022: 1086-1097. |
| [8] | SPERLING L, RATHA N, ROSS A, et al. HEFT: Homomorphically Encrypted Fusion of Biometric Templates[C]// IEEE. 2022 IEEE International Joint Conference on Biometrics. New York: IEEE, 2022: 1-10. |
| [9] | MOHASSEL P, ZHANG Yupeng. Secureml: A System for Scalable Privacy-Preserving Machine Learning[C]// IEEE. 2017 IEEE Symposium on Security and Privacy. New York: IEEE, 2017: 19-38. |
| [10] | RIAZI M S, WEINERT C, TKACHENKO O, et al. Chameleon: A Hybrid Secure Computation Framework for Machine Learning Applications[C]// ACM. The 2018 on Asia Conference on Computer and Communications Security. New York: ACM, 2018: 707-721. |
| [11] | JUVEKAR C, VAIKUNTANATHAN V, CHANDRAKASAN A. Gazelle: A Low Latency Framework for Secure Neural Network Inference[C]// USENIX. 27th USENIX Security Symposium. Baltimore: USENIX Association, 2018: 1651-1669. |
| [12] | GARAY J A, SCHOENMAKERS B, VILLEGAS J. Practical and Secure Solutions for Integer Comparison[C]// Springer. 10th International Conference on Practice and Theory in Public-Key Cryptography. Heidelberg: Springer, 2007: 330-342. |
| [13] | RABIN M O. How to Exchange Secrets with Oblivious Transfer[EB/OL]. [2023-01-15]. https://e-print.iacr.org/2005/187.pdf. |
| [14] | ASHAROV G, LINDELL Y, SCHNEIDER T, et al. More Efficient Oblivious Transfer and Extensions for Faster Secure Computation[C]// ACM. 2013 ACM SIGSAC Conference on Computer & Communications Security. New York: ACM, 2013: 535-548. |
| [15] | SHAMIR A. How to Share a Secret[C]// ACM. Communications of the ACM. New York: ACM, 1979: 612-613. |
| [16] | BEAVER D. Precomputing Oblivious Transfer[C]// Springer. 15th Annual International Cryptology Conference. Heidelberg: Springer, 1995: 97-109. |
| [17] | DAMGARD I, PASTRO V, SMART N, et al. Multiparty Computation from Somewhat Homomorphic Encryption[C]// Springer. 32nd Annual Cryptology Conference. Heidelberg: Springer, 2012: 643-662. |
| [18] | YANG Kang, WENG Chenkai, LAN Xiao, et al. Ferret: Fast Extension for Correlated OT with Small Communication[C]// ACM. 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 1607-1626. |
| [19] | RATHEE D, RATHEE M, KUMAR N, et al. Cryptflow2: Practical 2--Party Secure Inference[C]// ACM. The 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 325-342. |
| [20] |
GOLDWASSER S, MICALI S. Probabilistic Encryption[J]. Journal of Computer and System Sciences, 1984, 28(2): 270-299.
doi: 10.1016/0022-0000(84)90070-9 URL |
| [21] | LIU Jian, JUUTI M, LU Yu, et al. Oblivious Neural Network Predictions via Minionn Transformations[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 619-631. |
| [22] | LIU Xiaoning, ZHENG Yifeng, YUAN Xingliang, et al. Medisc: Towards Secure and Lightweight Deep Learning as a Medical Diagnostic Service[C]// Springer. European Symposium on Research in Computer Security. Heidelberg: Springer, 2021: 519-541. |
| [23] | WAGH S, TOPLE S, BENHAMOUDA F, et al. Falcon: Honest-Majority Maliciously Secure Framework for Private Deep Learning[C]// Springer. Proceedings on Privacy Enhancing Technologies. Heidelberg: Springer, 2021: 188-208. |
| [24] | MISHRA M, LEHMKUHL R, SRINIVASAN A, et al. Delphi: A Cryptographic Inference Service for Neural Networks[C]// USENIX. 29th USENIX Security Symposium. California: USENIX Association, 2020: 2505-2522. |
| [1] | YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning [J]. Netinfo Security, 2023, 23(7): 53-63. |
| [2] | LI Chenwei, ZHANG Hengwei, GAO Wei, YANG Bo. Transferable Image Adversarial Attack Method with AdaN Adaptive Gradient Optimizer [J]. Netinfo Security, 2023, 23(7): 64-73. |
| [3] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [4] | CHEN Jing, PENG Changgen, TAN Weijie, XU Dequan. A Multi-Server Federation Learning Scheme Based on Differential Privacy and Secret Sharing [J]. Netinfo Security, 2023, 23(7): 98-110. |
| [5] | YANG Yuguang, LU Jiayu. A Dynamic and Hierarchical Quantum Secret Sharing Protocol Based on Starlike Cluster States [J]. Netinfo Security, 2023, 23(6): 34-42. |
| [6] | JIANG Zenghui, ZENG Weijun, CHEN Pu, WU Shitao. Review of Adversarial Samples for Modulation Recognition [J]. Netinfo Security, 2023, 23(6): 74-90. |
| [7] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [8] | QIN Baodong, CHEN Congzheng, HE Junjie, ZHENG Dong. Multi-Keyword Searchable Encryption Scheme Based on Verifiable Secret Sharing [J]. Netinfo Security, 2023, 23(5): 32-40. |
| [9] | CHEN Zitong, JIA Peng, LIU Jiayong. Identification Method of Malicious Software Hidden Function Based on Siamese Architecture [J]. Netinfo Security, 2023, 23(5): 62-75. |
| [10] | PEI Bei, ZHANG Shuihai, LYU Chunli. A Proactive Multi-Secret Sharing Scheme for Cloud Storage [J]. Netinfo Security, 2023, 23(5): 95-104. |
| [11] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [12] | MA Min, FU Yu, HUANG Kai. A Principal Component Analysis Scheme for Security Outsourcing in Cloud Environment Based on Secret Sharing [J]. Netinfo Security, 2023, 23(4): 61-71. |
| [13] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [14] | HU Zhijie, CHEN Xingshu, YUAN Daohua, ZHENG Tao. Static Detection Method of Android Adware Based on Improved Random Forest Algorithm [J]. Netinfo Security, 2023, 23(2): 85-95. |
| [15] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||