Netinfo Security ›› 2022, Vol. 22 ›› Issue (10): 98-107.doi: 10.3969/j.issn.1671-1122.2022.10.014
Previous Articles Next Articles
Research on Security and Privacy Threats of Smart Wearable Devices
NI Xueli1,2( ), WANG Qun1,2, LIANG Guangjun1,2
), WANG Qun1,2, LIANG Guangjun1,2
- 1. Department of Computer Information and Cyber Security, Jiangsu Police Institute, Nanjing 210031, China
2. Jiangsu Electronic Data Forensics and Analysis Engineering Research Center, Nanjing 210031, China
-
Received:2022-08-11Online:2022-10-10Published:2022-11-15 -
Contact:NI Xueli E-mail:nixueli@jspi.edu.cn
CLC Number:
Cite this article
NI Xueli, WANG Qun, LIANG Guangjun. Research on Security and Privacy Threats of Smart Wearable Devices[J]. Netinfo Security, 2022, 22(10): 98-107.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.10.014
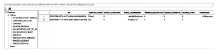
| 通信方式 | 安全威胁 |
|---|---|
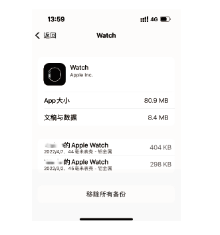
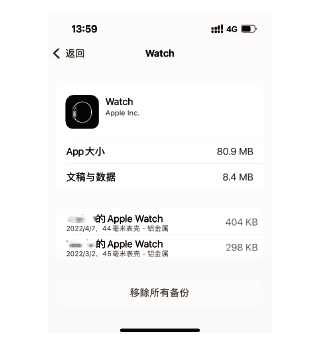
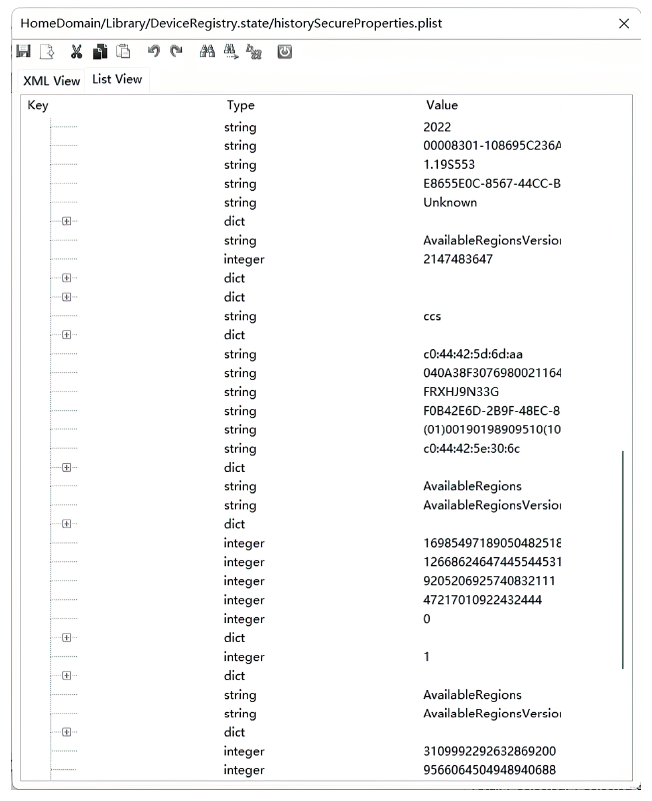
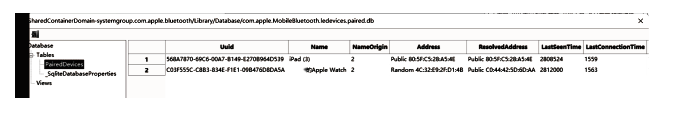
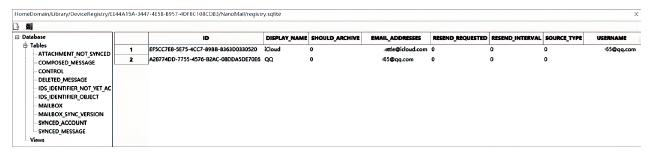
| USB连接 | 若攻击者感染了穿戴设备所连接的设备(如手机、PC等)或拥有该设备的物理访问权限,则有可能通过USB连接获得穿戴设备上的所有数据 |
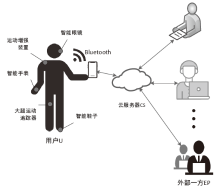
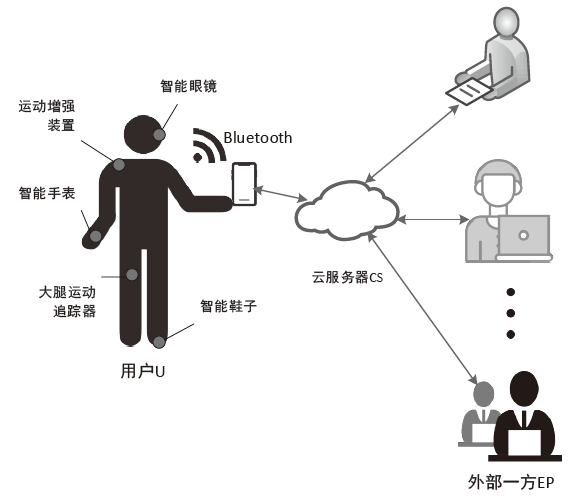
| 蓝牙 | 蓝牙低能耗(Bluetooth Low Energy, BLE)技术因其超低能耗、高数据传输速度、易于开发等特点,已成为物联网和智能穿戴设备的实际通信协议。由于该协议设计简单,所以存在大量的安全和隐私漏洞[ |
| NFC | 最新的穿戴设备可以通过近场通信(Near Field Communication,NFC)技术进行通信。攻击者在近距离内会尝试以窃听、篡改、伪造身份[ |
| WiFi | 较新的穿戴设备能够直接连接WiFi网络,在针对WiFi环境的网络攻击行为持续演化和升级的态势下[ |
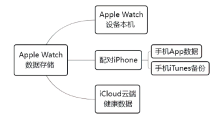
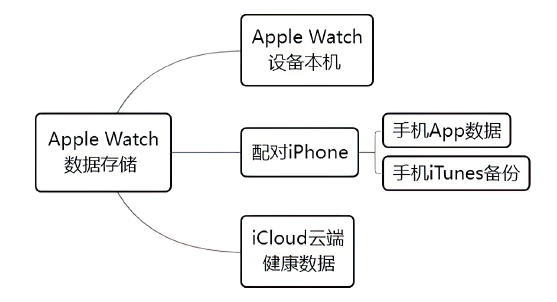
| 蜂窝移动 网络 | 部分功能较强大的穿戴设备具备蜂窝移动网络功能(如Apple Watch),针对无线空口的各类攻击与漏洞不断出现并被公开披露[ |
| [1] | SUN Wen, LIU Jiajia, ZHANG Haibin. When Smart Wearables Meet Intelligent Vehicles: Challenges and Future Directions[J]. IEEE Wireless Communications, 2017, 24(3): 58-65. |
| [2] | WALTER C, HALE M L, GAMBLE R F. Imposing Security Awareness on Wearables[C]// IEEE. 2016 IEEE/ACM 2nd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS). Austin: IEEE, 2016: 29-35. |
| [3] | QIU Yue. Security Analysis for the Information of Wearable Devices[J]. Netinfo Security, 2016, 16(9): 79-83. |
| 裘玥. 智能可穿戴设备信息安全分析[J]. 信息网络安全, 2016, 16(9): 79-83. | |
| [4] | MICHAEL K, MICHAEL M G. Apple Watch Temptation: Just Visit the App Store[J]. IEEE Consumer Electronics Magazine, 2015, 4(4): 120-122. |
| [5] | HATHALIYA J J, TANWAR S. An Exhaustive Survey on Security and Privacy Issues in Healthcare 4.0[J]. Computer Communications, 2020, 153: 311-335. |
| [6] | DO Q, MARTINI B, CHOO K. Is the Data on Your Wearable Device Secure? An Android Wear Smartwatch Case Study[J]. Software: Practice and Experience, 2017, 47(3): 391-403. |
| [7] | ZHANG Chi, SHAHRIAR H, RIAD A. Security and Privacy Analysis of Wearable Health Device[C]// IEEE. 2016 IEEE/ACM 2nd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS). Madrid: IEEE, 2020: 1767-1772. |
| [8] | BARUA A, ALAMIN A A, HOSSAIN S, et al. Security and Privacy Threats for Bluetooth Low Energy in IoT and Wearable Devices: A Comprehensive Survey[J]. IEEE Open Journal of the Communications Society, 2022, 3: 251-281. |
| [9] | YANG Minghui, GUO Junqi, ZHAO Ziyun, et al. Teenager Health Oriented Data Security and Privacy Protection Research for Smart Wearable Device[J]. Procedia Computer Science, 2020, 174: 333-339. |
| [10] | DAS A K, WAZID M, KUMAR N, et al. Design of Secure and Lightweight Authentication Protocol for Wearable Devices Environment[J]. IEEE Journal of Biomedical and Health Informatics, 2018, 22(4): 1310-1322. |
| [11] | SIBONI S, SHABTAI A, TIPPENHAUER N O, et al. Advanced Security Testbed Framework for Wearable IoT Devices[J]. ACM Transactions on Internet Technology, 2016, 16(4): 1-26. |
| [12] | AHMAD M, ALQARNI M A, KHAN A, et al. Smartwatch-Based Legitimate User Identification for Cloud-Based Secure Services[EB/OL]. (2018-08-14)[2022-05-03]. https://www.hindawi.com/journals/misy/2018/5107024/. |
| [13] | LEE J, PARK S, KIM Y G, et al. Advanced Authentication Method by Geometric Data Analysis Based on User Behavior and Biometrics for IoT Device with Touchscreen[J]. Electronics, 2021, 10(21): 1-13. |
| [14] | LIU Wei, LIU Hong, WAN Yueliang, et al. The Yoking-Proof-Based Authentication Protocol for Cloud-Assisted Wearable Devices[J]. Personal & Ubiquitous Computing, 2016, 20(3): 469-479. |
| [15] | LIU Sha, HU Shun, WENG Jian, et al. A Novel Asymmetric Three-party Based Authentication Scheme in Wearable Devices Environment[J]. Journal of Network & Computer Applications, 2016, 60: 144-154. |
| [16] | DEY S, ROY N, XU W, et al. AccelPrint: Imperfections of Accelerometers Make Smartphones Trackable[C]// ISOC. 2014 Network and Distributed System Security Symposium. San Diego: ISOC, 2014: 1-16. |
| [17] | MICHALEVSKY Y, BONEH D, NAKIBLY G. Gyrophone: Recognizing Speech From Gyroscope Signals[C]// USENIX Association. 23rd USENIX Security Symposium. San Diego: USENIX, 2014: 1053-1067. |
| [18] | ZHANG Chen. NFC Lightweight Security Authentication Method in Internet of Things[D]. Xi’an: Xidian University, 2019. |
| 张晨. 物联网下NFC轻量级安全认证方法研究[D]. 西安: 西安电子科技大学, 2019. | |
| [19] | WANG Ting, WANG Na, CUI Yunpeng, et al. The Optimization Method of Wireless Network Attacks Detection Based on Semi-Supervised Learning[J]. Journal of Computer Research and Development, 2020, 57(4): 791-802. |
| 王婷, 王娜, 崔运鹏, 等. 基于半监督学习的无线网络攻击行为检测优化方法[J]. 计算机研究与发展, 2020, 57(4): 791-802. | |
| [20] | ZHAO Haoming. Research on Security Flaws and Attack Verification of Mobile Communication[D]. Chongqing: Chongqing University of Posts and Telecommunications, 2021. |
| 赵昊明. 移动通信网络安全缺陷研究与攻击验证[D]. 重庆: 重庆邮电大学, 2021. |
| [1] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [2] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [3] | LIU Qin, ZHANG Biao, TU Hang. Certificateless Blind Signature Scheme Based on twisted Edwards Curve [J]. Netinfo Security, 2022, 22(8): 19-25. |
| [4] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [5] | YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment [J]. Netinfo Security, 2022, 22(7): 55-63. |
| [6] | QIN Baodong, YU Peihang, ZHENG Dong. Decision Tree Classification Model Based on Double Trapdoor Homomorphic Encryption [J]. Netinfo Security, 2022, 22(7): 9-17. |
| [7] | HONG Sheng, LI Lei, YUAN Yidong, GAO Xinyan. Research on Cooperative Security Technology of Side Channel in Processor Microarchitecture Storage System [J]. Netinfo Security, 2022, 22(6): 26-37. |
| [8] | ZHAO Hong, LI Shan, ZUO Peiliang, WEI Zhanzhen. Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning [J]. Netinfo Security, 2022, 22(6): 44-52. |
| [9] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [10] | WANG Juan, WANG Yunru, WENG Bin, GONG Jiaxin. Survey on Application of Machine Learning in Disassembly on x86 Binaries [J]. Netinfo Security, 2022, 22(6): 9-25. |
| [11] | SUN Pengyu, TAN Jinglei, LI Chenwei, ZHANG Hengwei. Network Security Defense Decision-Making Method Based on Time Differential Game [J]. Netinfo Security, 2022, 22(5): 64-74. |
| [12] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [13] | LI Guoqi, HONG Sheng, LAN Xueting, ZHANG Hong. The Security Reference Model of the Multi-rotor UAV System [J]. Netinfo Security, 2022, 23(3): 10-19. |
| [14] | LI Li, LI Zequn, LI Xuemei, SHI Guozhen. FPGA Realization of Physical Unclonable Function Based on Cross-coupling Circuit [J]. Netinfo Security, 2022, 23(3): 53-61. |
| [15] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||