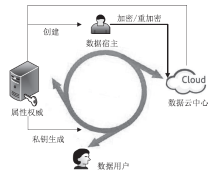
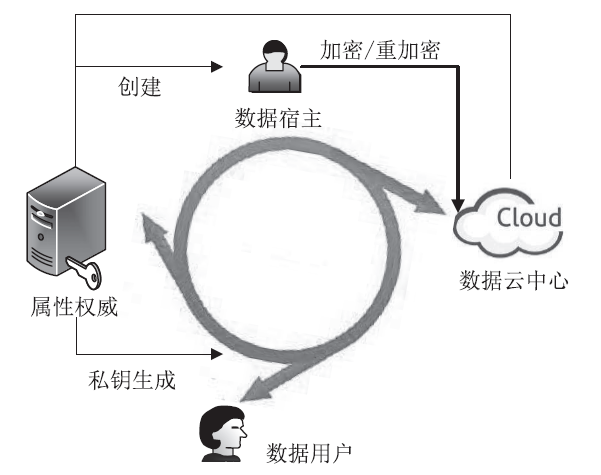
| [1] |
ZHANG Qian, WANG Jian. Cloud Shared Data Integrity Audit Scheme with Traceable User Identity[J]. Computer Science, 2020, 47(6):303-309.
|
|
张茜, 王箭. 用户身份可追踪的云共享数据完整性审计方案[J]. 计算机科学, 2020, 47(6):303-309.
|
| [2] |
JIANG Mingmin, WANG Yiyuan. Optimization Exploration and Characteristic Analysis of Cloud Shared Information from the Perspective of Information Foraging[J]. Information Science, 2020, 38(5):93-97.
|
|
蒋明敏, 王艺苑. 信息觅食视角下云共享信息的优化探索和特性分析[J]. 情报科学, 2020, 38(5):93-97.
|
| [3] |
YOO H, CHUNG K. PHR Based Diabetes Index Service Model Using Life Behavior Analysis[J]. Wireless Personal Communications, 2017, 93(1):161-174.
doi: 10.1007/s11277-016-3715-9
URL
|
| [4] |
LI Jiguo, ZHANG Yichen, NING Jianting, et al. Attribute Based Encryption with Privacy Protection and Accountability for CloudIoT[EB/OL]. https://ieeexplore.ieee.org/document/9003205, 2020-02-19.
|
| [5] |
SHEN Jian, ZHOU Tianqi, CAO Zhenfu. Protection Methods for Cloud Data Security[J]. Journal of Computer Research and Development, 2021, 58(10):2079-2098.
|
|
沈剑, 周天祺, 曹珍富. 云数据安全保护方法综述[J]. 计算机研究与发展, 2021, 58(10):2079-2098.
|
| [6] |
SAHAI A, WATERS B. Fuzzy Identity-based Encryption[C]// Springer. 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques(EUROCRYPT 2005), May 2-4, 2005, Aarhus, Denmark. Berlin: Springer, 2005: 457-473.
|
| [7] |
LIU Xueyan, LU Tingting, HE Xiaomei, et al. Verifiable Attribute-based Keyword Search over Encrypted Cloud Data Supporting Data Deduplication[J]. IEEE Access, 2020, 8(99):52062-52074.
doi: 10.1109/Access.6287639
URL
|
| [8] |
GUDEME J R, PASUPULETI S K, KANDUKURI R. Attribute-based Public Integrity Auditing for Shared Data with Efficient User Revocation in Cloud Storage[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 12(2):12652-12666.
|
| [9] |
EDEMACU K, JANG B, KIM J W. Collaborative eHealth Privacy and Security: An Access Control with Attribute Revocation Based on OBDD Access Structure[J]. IEEE Journal of Biomedical and Health Informatics, 2020, 24(10):2168-2194.
|
| [10] |
ALTAMIMI A, KAMOONA M A. Securing E-health Data using Ciphertext-policy Attribute-based Encryption with Dynamic User Revocation[J]. International Journal of Recent Technology and Engineering, 2019, 8(3):7244-7250.
|
| [11] |
WANG Shangping, GUO Keke, ZHANG Yaling. Ciphertext-policy Attribute-based Encryption Scheme with Attribute Level User Revocation for Cloud Storage[EB/OL]. https://www.researchgate.net/publication/327651817_Traceable_ciphertext-policy_attribute-based_encryption_scheme_with_attribute_level_user_revocation_for_cloud_storage, 2018-09-12.
|
| [12] |
CHEN Lu, XIANG Feng, SUN Zhixin. Research Progress of Blockchain Security Technology based on Attribute Cryptosystem[J]. Acta Electronica Sinica, 2021, 49(1):192-200.
doi: 10.12263/DZXB.20191375
|
|
陈璐, 相峰, 孙知信. 基于属性密码体制的区块链安全技术研究进展[J]. 电子学报, 2021, 49(1):192-200.
|
| [13] |
GOYAL V, PANDEY O, SAHAI A, et al. Attribute-based Encryption for Fine-grained Access Control of Encrypted Data[C]// ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security(CCS 2006), October 30-November 3, 2006, Alexandria, VA, USA. New York: ACM, 2006: 89-98.
|
| [14] |
WANG Ze, GAO Minghua, CHEN Lu, et al. An Access Control Scheme Based on Access Tree Structure Pruning for Cloud Computing[J]. International Journal of Network Security, 2021, 23(1):143-156.
|
| [15] |
HANAOKA G, KUROSAWA K. Between Hashed DH and Computational DH: Compact Encryption from Weaker Assumption[J]. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2010, 93(11):1994-2006.
|
| [16] |
XHAFA F, FENG Jianglang, ZHANG Yinghui, et al. Privacy-aware Attribute-based PHR Sharing with User Accountability in Cloud Computing[J]. Journal of Supercomputing, 2015, 71(5):1607-1619.
doi: 10.1007/s11227-014-1253-3
URL
|
| [17] |
HONG Hanshu, SUN Zhixin. High Efficient Key-insulated Attribute Based Encryption Scheme without Bilinear Pairing Operations[J]. Springer Plus, 2016, 5(1):131-142.
doi: 10.1186/s40064-016-1765-9
URL
|
| [18] |
LIN Guofeng, HONG Hanshu, SUN Zhixin. A Collaborative Key Management Protocol in Ciphertext Policy Attribute-based Encryption for Cloud Data Sharing[J]. IEEE Access, 2017, 23(5):9464-9475.
|
| [19] |
XUE Liang, YU Yong, LI Yannan, et al. Efficient Attribute-based Encryption with Attribute Revocation for Assured Data Deletion[J]. Information Sciences, 2019, 30(479):640-650.
|