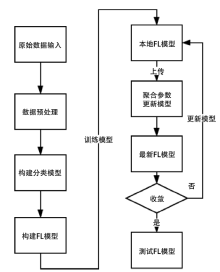
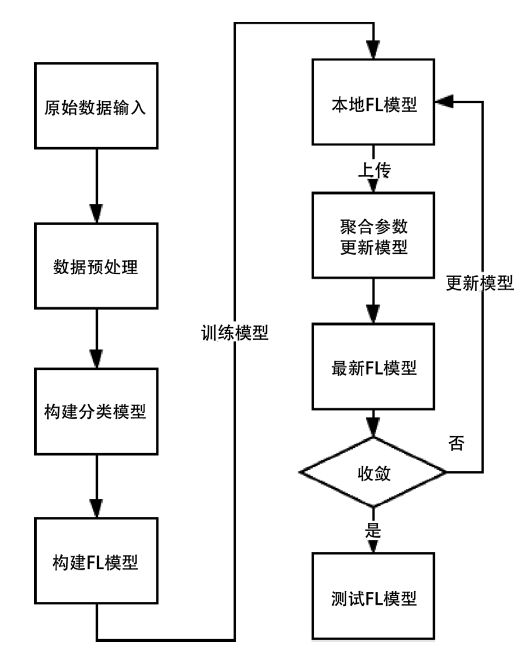
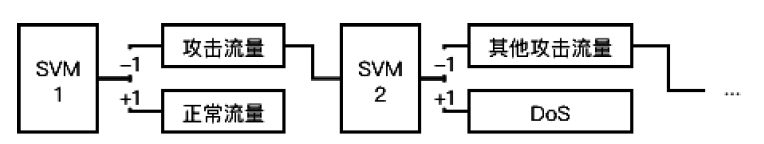
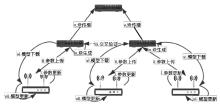
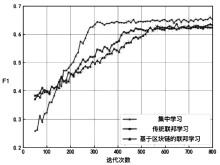
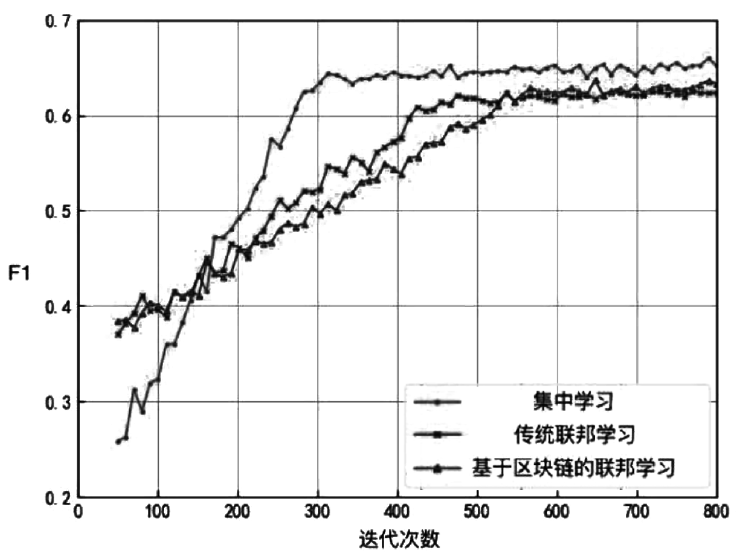
Netinfo Security ›› 2021, Vol. 21 ›› Issue (7): 27-34.doi: 10.3969/j.issn.1671-1122.2021.07.004
Previous Articles Next Articles
Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning
REN Tao1, JIN Ruochen1( ), LUO Yongmei2
), LUO Yongmei2
- 1. Software College, Northeastern University, Shenyang 110169, China
2. College of Inteligence and Computing, Tianjin University, Tianjin 300072, China
-
Received:2021-04-15Online:2021-07-10Published:2021-07-23 -
Contact:JIN Ruochen E-mail:20182747@stu.neu.edu.cn
CLC Number:
Cite this article
REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning[J]. Netinfo Security, 2021, 21(7): 27-34.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.07.004
| [1] | LI Hui, GUAN Xiaohong, ZAN Xin, et al. Network Intrusion Detection Based on Support Vector Machine[J]. Journal of Computer Research and Development, 2003, 40(6):799-807. |
| 李辉, 管晓宏, 昝鑫, 等. 基于支持向量机的网络入侵检测[J]. 计算机研究与发展, 2003, 40(6):799-807. | |
| [2] | IEEE 3652. 1-2020, IEEE Guide for Architectural Framework and Application of Federated Machine Learning[S]. USA: IEEE, 2021 |
| [3] | SHAO Qifeng, JIN Cheqing, ZHANG Zhao, et al. Blockchain: Architecture and Research Process[J]. Chinese Journal of Computer, 2018, 41(5):969-988. |
| 邵奇峰, 金澈清, 张召, 等. 区块链技术:架构及进展[J]. 计算机学报, 2018, 41(5):969-988. | |
| [4] | SONG Yong, HOU Bingnan, CAI Zhiping. Network Intrusion Detection Method Based on Deep Learning Feature Extraction[J]. Journal of Huazhong University of Science and Technology(Natural Science Edition), 2021, 49(2):115-120. |
| 宋勇, 侯冰楠, 蔡志平. 基于深度学习特征提取的网络入侵检测方法[J]. 华中科技大学学报(自然科学版), 2021, 49(2):115-120. | |
| [5] |
DEBARH, DACIERM. Andreas Wespi towards a Taxonomy of Intrusion-detection Systems[J]. Computer Networks, 1999, 31(8):805-822.
doi: 10.1016/S1389-1286(98)00017-6 URL |
| [6] | SMAHA S. E. Haystack: an Intrusion Detection System[C]// IEEE. Proceeding of the 4th Aerospace Computer Security Applications Conference, September 12-16, 1988,Orlando, FL, USA. New York: IEEE Computer Society Press, 1988: 37-44. |
| [7] | LUNT TF, JAGANNATHAN R, EDWARDS DL, et al. IDES:The Enhanced Prototype a Real Time Intrusion-detection Expert System[C]// IEEE. Proceeding of the 4th Aerospace Computer Security Applications Conference, September 12-16, 1988, Orlando, FL, USA. New York: IEEE Computer Society Press, 1988: 59-66. |
| [8] | The Center of UC Santa Barbara Engineering. NetSTAT: A Network-based Intrusion Detection Approach[EB/OL]. https://sites.cs.ucsb.edu/~vigna/publications/1998_vigna_kemmerer_acsac98.pdf, 2021-04-14. |
| [9] | SHENG Xiaoyan. Research on Intrusion Detection System Based on Immune Mechanism[D]. Nanjing: Nanjing University of Aeronautics and Astronautics, 2008. |
| 盛晓艳. 基于免疫机制的入侵检测系统的研究[D]. 南京:南京航空航天大学, 2008. | |
| [10] | The Center for Education and Research in Information Assurance and Security (CERIAS). Autonomous Agents for Intrusion Detection[EB/OL]. https://www.cerias.purdue.edu/site/about/history/coast/projects/aafid.php, 2021-04-14. |
| [11] | JIA Fan, KONG Lingzhi. Intrusion Detection Algorithm Based on Convolutional Neural Network[J]. Transactions of Beijing Institute of Technology, 2017, 37(12):1271-1275. |
| 贾凡, 孔令智. 基于卷积神经网络的入侵检测算法[J]. 北京理工大学学报, 2017, 37(12):1271-1275. | |
| [12] |
YIN Chuanlong, ZHU Yuefei, FEI Jinlong, et al. A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks[J]. IEEE Access, 2017, 5(1):21954-21961.
doi: 10.1109/ACCESS.2017.2762418 URL |
| [13] | SHONE N, NGOC T N, PHAI V D, et al. A Deep Learning Approach to Network Intrusion Detection[J]. IEEE Trans Emerg Top Computlntell, 2018, 2(2):41-50. |
| [14] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4):47-54. |
| 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4):47-54. | |
| [15] | SATOSHI Nakamoto. Consensus mechanism[EB/OL]. https://docs.ont.io/ontology-elements/consensus-mechanism, 2020-06-14. |
| [16] | DING Hongwei, WAN Liang, LONG Tingyan. Research on the Application of Deep Auto-encoder Network in Intrusion Detection[J]. Journal of Harbin Institute of Technology, 2019, 51(5):185-194. |
| 丁红卫, 万良, 龙廷艳. 深度自编码网络在入侵检测中的应用研究[J]. 哈尔滨工业大学学报, 2019, 51(5):185-194. | |
| [17] | LI Xuegui, GUO Yuantao, LI Panchi, et al. Classification Model of Support Vector Machine Based on Modified Vortex Search Algorithm[J]. Journal of Jilin University(Information Science Edition), 2020, 38(3):312-318. |
| 李学贵, 郭远涛, 李盼池, 等. 基于改进涡流搜索算法的支持向量机分类模型[J]. 吉林大学学报(信息科学版), 2020, 38(3):312-318. | |
| [18] | WANG Shengsheng, CHEN Jingyu, LU Yi'nan. COVID-19 Chest CT Image Segmentation Based on Federated Learning and Blockchain[EB/OL]. https://doi.org/10.13229/j.cnki.jdxbgxb20200674, 2021-03-05. |
| 王生生, 陈境宇, 卢奕南. 基于联邦学习和区块链的COVID-19胸部CT图像分割[EB/OL]. https://doi.org/10.13229/j.cnki.jdxbgxb20200674, 2021-03-05. | |
| [19] | TAVALLAEE ME, BAGHERI W, Lu , et al. A Detailed Analysis of the KDD CUP 99 Data Set[C]// IEEE. Second IEEE Symposium on Computational Intelligence for Security and Defense Applications (CISDA), July 8-10, 2009, Ottawa, ON, Canada. New York: IEEE, 2009: 1-6. |
| [20] | WEI Yuxin. Research on Key Technologies of Network Intrusion Detection System[D]. Beijing: Beijing University of Posts and Telecommunications, 2008. |
| 魏宇欣. 网络入侵检测系统关键技术研究[D]. 北京:北京邮电大学, 2008. |
| [1] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| [2] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [3] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [4] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [5] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [6] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [7] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| [8] | LIU Yi, LI Jianhua, ZHANG Yitao, MENG Tao. Network Abnormal Flow Detection Method Based on Feature Attribute Information Entropy [J]. Netinfo Security, 2021, 21(2): 78-86. |
| [9] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [10] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [11] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [12] | SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology [J]. Netinfo Security, 2020, 20(8): 1-8. |
| [13] | LI Li, ZENG Qingxian, WEN Yihong, WANG Shicheng. Data Sharing Scheme Based on the Blockchain and the Proxy Re-encryption [J]. Netinfo Security, 2020, 20(8): 16-24. |
| [14] | JIANG Nan, CUI Yaohui, WANG Jian, WU Jinchao. Context-based Attack Scenario Reconstruction Model for IDS Alarms [J]. Netinfo Security, 2020, 20(7): 1-10. |
| [15] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||