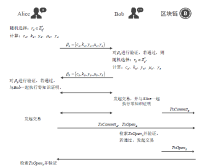
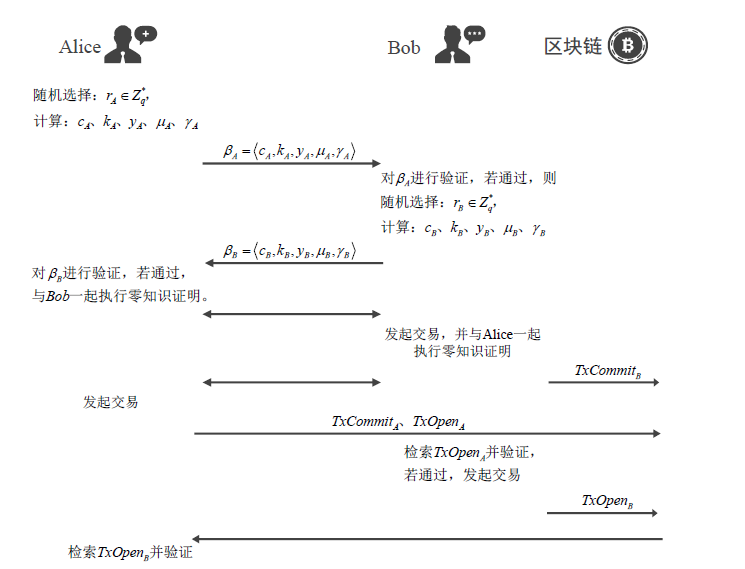
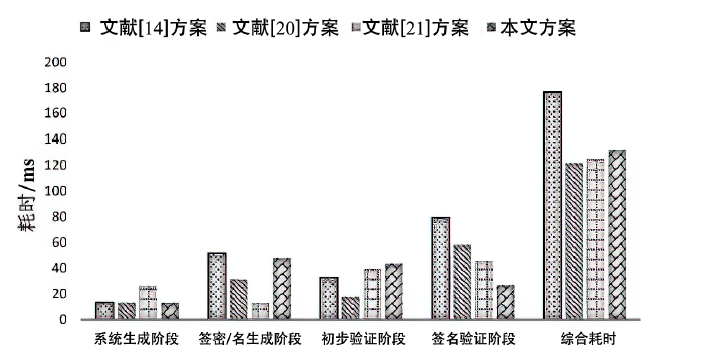
Netinfo Security ›› 2021, Vol. 21 ›› Issue (5): 19-30.doi: 10.3969/j.issn.1671-1122.2021.05.003
Previous Articles Next Articles
Blockchain-based Fair Exchange Scheme
ZHOU Yousheng1,2( ), ZHONG Tianqi1
), ZHONG Tianqi1
- 1. College of Computer Science and Technology, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
2. College of Cyber Security and Information Law, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2021-01-20Online:2021-05-10Published:2021-06-22 -
Contact:ZHOU Yousheng E-mail:zhouys@cqupt.edu.cn
CLC Number:
Cite this article
ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme[J]. Netinfo Security, 2021, 21(5): 19-30.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.05.003
| [1] | ASOKAN N. Fairness in Electronic Commerce[D]. Waterloo: University of Waterloo, 1998. |
| [2] |
EVEN S, GOLDREICH O, LEMPEL A. A Randomized Protocol for Signing Contracts[J]. Communications of the ACM, 1985,28(6):637-647.
doi: 10.1145/3812.3818 URL |
| [3] | OKAMOTO T, OHTA K. How to Simultaneously Exchange Secrets by General Assumptions[C]// ACM. 2nd ACM Conference on Computer & Communications Security. November 2-4, 1994, Fairfax, Virginia, USA. New York: ACM, 1994: 184-192. |
| [4] | BLUM M. How to Exchange(secret) Keys[J]. ACM Transactions on Computer Systems(Tocs), 1983,1(2):175-193. |
| [5] |
BEN-OR M, GOLDREICH O, MICALI S, et al. A Fair Protocol for Signing Contracts[J]. IEEE Transactions on Information Theory, 1990,36(1):40-46.
doi: 10.1109/18.50372 URL |
| [6] |
RABIN M O. Transaction Protection by Beacons[J]. Journal of Computer and System Sciences, 1983,27(2):256-267.
doi: 10.1016/0022-0000(83)90042-9 URL |
| [7] | BAHREMAN A, TYGAR J D. Certified Electronic Mail[EB/OL]. https://people.eecs.berkeley.edu/~tygar/papers/Certified_Electronic_Mail/Certified_electronic_mail.pdf, 2012-01-02. |
| [8] |
DENG R H, GONG L, LAZAR A A, et al. Practical Protocols for Certified Electronic Mail[J]. Journal of Network and Systems Management, 1996,4(3):279-297.
doi: 10.1007/BF02139147 URL |
| [9] | ZHOU J, GOLLMAN D. A Fair Non-repudiation Protocol[C]// IEEE. 1996 IEEE Symposium on Security and Privacy, May 6-8 1996, Oakland, CA, USA. New York: IEEE, 1996: 55-61. |
| [10] | ASOKAN N, SHOUP V, WAIDNER M. Asynchronous Protocols for Optimistic Fair Exchange[C]// IEEE. 1998 IEEE Symposium on Security and Privacy, May 6, 1998, Oakland, CA, USA. New York: IEEE, 1998: 86-99. |
| [11] | DODIS Y, REYZIN L. Breaking and Repairing Optimistic Fair Exchange from PODC 2003[C]// ACM. 10th ACM Conference on Computer and Communications Security. October 27, 2003. Washington, DC, USA. New York: ACM, 2003: 47-54. |
| [12] | PARK J M, CHONG E K P, SIEGEL H J. Constructing Fair-exchange Protocols for E-commerce via Distributed Computation of RSA Signatures[C]// ACM. Twenty-Second Annual ACM Symposium on Principles of Distributed Computing, July 13-16, 2003, Boston, Massachusetts, USA. New York: ACM, 2003: 172-181. |
| [13] | CHEN L, KUDLA C, PATERSON K G. Concurrent Signatures[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques, May 2-6, 2004, Interlaken, Switzerland. Berlin: Springer, 2004: 287-305. |
| [14] | LUO Ming, ZOU Chunhua, HU Jun, et al. Signcryption-based Fair Exchange Protocol[J]. Journal on Communications, 2010,31(S1):87-93. |
| 罗铭, 邹春华, 胡军, 等. 基于签密的公平交易协议[J]. 通信学报, 2010,31(S1):87-93. | |
| [15] | EVEN S, YACOBI Y. Relations among Public Key Signature Systems[R]. Computer Science Department, Technion. No. CS Technion report CS0175, 1980. |
| [16] |
ZHANG Yinghui, DENG R H, LIU Ximeng, et al. Blockchain Based Efficient and Robust Fair Payment for Outsourcing Services in Cloud Computing[J]. Information Sciences, 2018,462(9):262-277.
doi: 10.1016/j.ins.2018.06.018 URL |
| [17] | HUANG Hui, LI Kuan-ching, CHEN Xiaofeng. Blockchain-based Fair Three-party Contract Signing Protocol for Fog Computing[EB/OL]. https://www.researchgate.net/publication/324577631_Blockchain-based_fair_three-party_contract_signing_protocol_for_fog_computing, 2021-01-02. |
| [18] | CAMPANELLI M, GENNARO R, GOLDFEDER S, et al. Zero-knowledge Contingent Payments Revisited: Attacks and Payments for Services[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security, October 30-November 3, 2017, Dallas, Texas, USA. New York: ACM, 2017: 229-243. |
| [19] | LIU Jian, LI Wenting, KARAME G O, et al. Toward Fairness of Cryptocurrency Payments[J]. IEEE Security & Privacy, 2018,16(3):81-89. |
| [20] | TIAN Haibo, HE Jiejie, FU Liqing. A Privacy Preserving Fair Contract Signing Protocol Based on Public Blcokchains[J]. Journal of Cryptologic Research, 2017,4(2):187-198. |
| 田海博, 何杰杰, 付利青. 基于公开区块链的隐私保护公平合同签署协议[J]. 密码学报, 2017,4(2):187-198. | |
| [21] |
ZHANG Liang, ZHANG Hanlin, YU Jia, et al. Blockchain-based Two-party Fair Contract Signing Scheme[J]. Information Sciences, 2020,535(10):142-155.
doi: 10.1016/j.ins.2020.05.054 URL |
| [22] | NAKAMOTO S, BITCOIN A. A Peer-to-peer Electronic Cash System[EB/OL]. https://bitcoin.org/bitcoin.pdf, 2021-01-02. |
| [23] | ZHENG Yuliang. Digital Signcryption or How to Achieve Cost(Signature & Encryption)《 Cost(Signature)+ Cost(Encryption)[C]// Springer. 17th Annual International Cryptology Conference, August 17-21, 1997, Santa Barbara, California, USA. Berlin: Springer, 1997: 165-179. |
| [24] | ANTONOPOULOS A M. Mastering Bitcoin: Programming the Open Blockchain[M]. Sebastopol CA: O'Reilly Media, Inc. , 2017. |
| [25] |
SCHNORR C P. Efficient Signature Generation by Smart Cards[J]. Journal of Cryptology, 1991,4(3):161-174.
doi: 10.1007/BF00196725 URL |
| [26] | FRANKLIN M K, REITER M K. Verifiable Signature Sharing[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques, May 21-25, 1995, Saint-Malo, France. Berlin: Springer, 1995: 50-63. |
| [27] | CARO D A, IOVINO V. jPBC: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications(ISCC), June 28-July 1, 2011, Kerkyra, Greece. New York: IEEE, 2011: 850-855. |
| [1] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [2] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [3] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [4] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| [5] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [6] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [7] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [8] | SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology [J]. Netinfo Security, 2020, 20(8): 1-8. |
| [9] | LI Li, ZENG Qingxian, WEN Yihong, WANG Shicheng. Data Sharing Scheme Based on the Blockchain and the Proxy Re-encryption [J]. Netinfo Security, 2020, 20(8): 16-24. |
| [10] | BIAN Lingyu, ZHANG Linlin, ZHAO Kai, SHI Fei. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [11] | MAO Zhilai, LIU Yanan, SUN Huiping, CHEN Zhong. Research on Blockchain Performance Scalability and Security [J]. Netinfo Security, 2020, 20(3): 56-64. |
| [12] | LANG Weimin, ZHANG Han, ZHAO Yifeng, YAO Jinfang. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [13] | JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract [J]. Netinfo Security, 2020, 20(11): 22-31. |
| [14] | LIU Kaifang, FU Shaojing, SU Jinshu, ZHANG Fucheng. An Optimizing Scheme on Multi-domain Collaborative IOTA Blockchain Technology for the Internet of Things [J]. Netinfo Security, 2020, 20(10): 41-48. |
| [15] | PENG Ruyue, MA Zhaofeng, LUO Shoushan. Research and Implementation of Digital Content Service and Security Supervision Technology Based on Blockchain [J]. Netinfo Security, 2020, 20(10): 49-56. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||