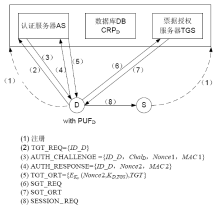
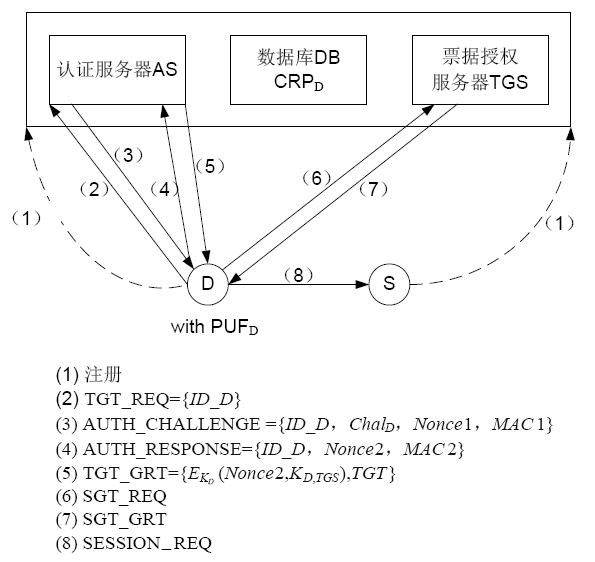
| [1] |
RFC 4120. The Kerberos Network Authentication Service(V5)FC 4120. The Kerberos Network Authentication Service(V5)[S]. USA: IETF, 2005.
|
| [2] |
NEEDHAM R M, SCHROEDER M D. Using Encryption for Authentication in Large Networks of Computers[J]. Communications of the ACM, 1978,21(12):993-999.
doi: 10.1145/359657.359659
URL
|
| [3] |
STEINER J G, NEUMAN B C, SCHILLER J I. Kerberos: An Authentication Service for Network System[EB/OL]. https://ieeexplore.ieee.org/document/312841/references#references, 2020-05-15.
|
| [4] |
RFC 6113. A Generalized Framework for Kerberos Pre-AuthenticationFC 6113. A Generalized Framework for Kerberos Pre-Authentication[S]. USA: IETF, 2011.
|
| [5] |
TUNG B, NEUMAN C, HUR M, Public Key Cryptography for Initial Authentication in Kerberos (PKINIT)[EB/OL]. https://www.researchgate.net/publication/243788044_Public_key_cryptography_for_initial_authentication_in_Kerberos, 2020-05-15.
|
| [6] |
RFC 4556. Public Key Cryptography for Initial Authentication in Kerberos(PKINIT)[S]. USA: IETF, 2006.
|
| [7] |
GAIKWAD P P, GABHANE J P, GOLAIT S S. 3-level Secure Kerberos Authentication for Smart Home Systems Using IoT[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=df202d88fa2d7afc656e4958b5d8c00b&site=xueshu_se, 2020-05-15.
|
| [8] |
RAO K, BHARADWAJ, RAM N, et al. Application of Time Synchronization Process to Kerberos[J]. Procedia Computer Science, 2016(85):249-254.
|
| [9] |
SUTRADHAR M R, SULTANA N, DEY H, et al. A New Version of Kerberos Authentication Protocol Using ECC and Threshold Cryptography for Cloud Security[EB/OL]. https://ieeexplore.ieee.org/document/8641010, 2020-05-15.
|
| [10] |
JENA S K, TRIPATHY B K, GUPTA P, et al. A Kerberos Based Secure Communication System in Smart (Internet of Things) Environment[J]. Journal of Computational and Theoretical Nanoscience, 2019,16(5):2381-2388.
doi: 10.1166/jctn.2019.7904
URL
|
| [11] |
DELVAUX J, PEETERS R, GU D, et al. A Survey on Lightweight Entity Authentication with Strong PUFs[J]. ACM Computing Surveys (CSUR), 2015,48(2):1-26.
|
| [12] |
ABUTALEB M, ALLAM A. FPGA-based Authenticated Key Exchange Scheme Utilizing PUF and CSI for Wireless Networks[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=86c0537a937e7aaf801639fd7786bbb2&site=xueshu_se, 2020-05-15.
|
| [13] |
LIU Dan, GUO Limin, YU Jun, et al. A Secure Mutual Authentication Protocol Based on SRAM PUF[J]. Journal of Cryptologic Research, 2017,4(4):58-69.
|
|
刘丹, 郭丽敏, 俞军, 等. 一种基于SRAM PUF的安全双向认证协议[J]. 密码学报, 2017,4(4):58-69.
|
| [14] |
WANG Jun, LIU Shubo, LIANG Cai, et al. Two-factor Wearable Device Authentication Protocol Based on PUF and IPI[J]. Journal on Communications, 2017,38(6):127-135.
|
|
王俊, 刘树波, 梁才, 等. 基于PUF和IPI的可穿戴设备双因子认证协议[J]. 通信学报, 2017,38(6):127-135.
|
| [15] |
CHATTERJEE U, CHAKRABORTY R S, MUKHOPADHYAY D. A PUF Based Secure Communication Protocol for IoT[J]. ACM Transactions on Embedded Computing Systems, 2017,16(3):1-25.
|
| [16] |
BRAEKEN A. PUF Based Authentication Protocol for IoT[J]. Symmetry, 2018,10(8):1-15.
doi: 10.3390/sym10010001
URL
|
| [17] |
USMANI M A, KESHAVARZ S, MATTHEWS E, et al. Efficient PUF-based Key Generation in FPGAs Using Per-device Configuration[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2019,27(2):364-375.
doi: 10.1109/TVLSI.2018.2877438
URL
|
 ), ZHA Daren1, LIU Yanan2, FANG Xuming2
), ZHA Daren1, LIU Yanan2, FANG Xuming2