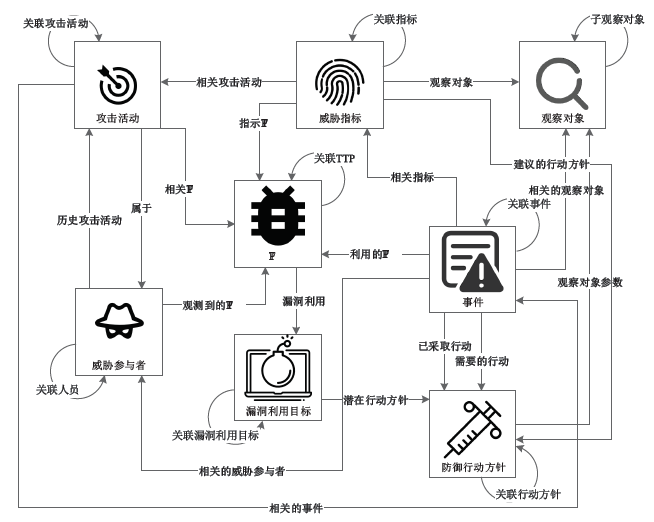
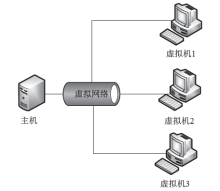
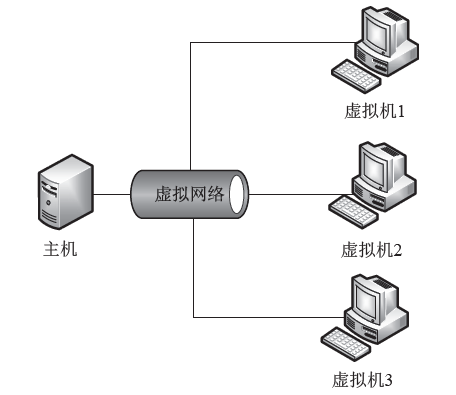
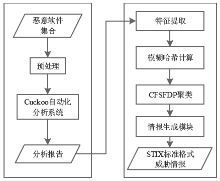
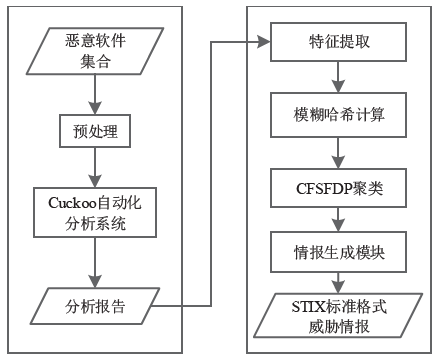
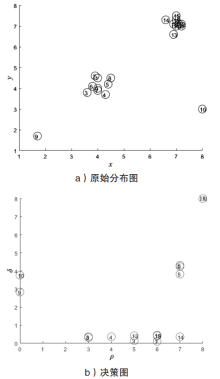
Netinfo Security ›› 2020, Vol. 20 ›› Issue (12): 83-90.doi: 10.3969/j.issn.1671-1122.2020.12.011
Previous Articles Next Articles
A Threat Intelligence Generation Method for Malware Family
WANG Changjie, LI Zhihua( ), ZHANG Ye
), ZHANG Ye
- School of Artificial Intelligence and Computer, Jiangnan University, Wuxi 214122, China
-
Received:2020-10-14Online:2020-12-10Published:2021-01-12 -
Contact:LI Zhihua E-mail:jswxzhli@aliyun.com
CLC Number:
Cite this article
WANG Changjie, LI Zhihua, ZHANG Ye. A Threat Intelligence Generation Method for Malware Family[J]. Netinfo Security, 2020, 20(12): 83-90.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.12.011
| 家族名 | 样本数量 |
|---|---|
| Win32:Agent-BARL | 78 |
| Win64:Vitro | 46 |
| Win32:Malware-gen | 49 |
| Win64:Trojan-gen | 30 |
| Patched-HO | 50 |
| Win32:Agent-KKQ | 39 |
| AutoRun-BPN | 34 |
| Win64:Evo-gen | 26 |
| Evo-gen | 16 |
| Kryptik-AZZ | 18 |
| Bluehero | 12 |
| Win64:Winnti | 9 |
| Win32:Patched-XF | 6 |
| Win32:Runouce-E | 3 |
| Win32:Patched-AKC | 3 |
| Win32:Flooder-GR | 2 |
| Win64:Adware-gen | 4 |
| Inject-AII | 3 |
| [1] | SYMANTEC. 2019 Symantec Symantec 2019 Internet Security Threat Report[EB/OL]. https://docs.broadcom.com/doc/istr-24-2019-en, 2020-09-28. |
| [2] | YANG Peian, WU Yang, SU Liya, et al. Overview of Threat Intelligence Sharing Technologies in Cyberspace[J]. Computer Science, 2018,45(6):9-18. |
| 杨沛安, 武杨, 苏莉娅, 等. 网络空间威胁情报共享技术综述[J]. 计算机科学, 2018,45(6):9-18. | |
| [3] | HAN Xiaoguang, QU Wu, YAO Xuanxia, et al. Research on Malicious Code Variants Detection Based on Texture Fingerprint[J]. Journal on Communications, 2014,35(8):125-136. |
| 韩晓光, 曲武, 姚宣霞, 等. 基于纹理指纹的恶意代码变种检测方法研究[J]. 通信学报, 2014,35(8):125-136. | |
| [4] | LIAO Xiaojing, YUAN Kan, WANG Xiaofeng, et al. Acing the IOC Game: Toward Automatic Discovery and Analysis of Open-source Cyber Threat Intelligence[C]// ACM. ACM SIGSAC Conference on Computer & Communications Security, October 24-28, 2016, Vienna, Austria. New York: ACM, 2016: 755-766. |
| [5] | SUN Bo, FUJINO A, MORI T, et al. Automatically Generating Malware Analysis Reports Using Sandbox Logs[J]. IEICE Transactions on Information and Systems, 2018,101(11):2622-2632. |
| [6] | ZHANG Yongsheng, WANG Zhi, WU Yijie, et al. Cyber Threat Intelligence Propagation Based on Conformal Prediction[J]. Netinfo Security, 2020,20(6):90-95. |
| [7] | WANG Qinxin, YANG Wang. Extraction of Threat Intelligence Entities Based on STIX[J]. Cyberspace Security, 2020,11(8):86-91. |
| 王沁心, 杨望. 基于STIX标准的威胁情报实体抽取研究[J]. 网络空间安全, 2020,11(8):86-91. | |
| [8] | GBADEBO A, SWARUP C, LATIFUR K, et al. Automated Threat Report Classification over Multi-source Data[C]// IEEE. 4th International Conference on Collaboration and Internet Computing, October 18-20, 2018, Philadelphia, PA, USA. New Jersey: IEEE, 2018: 236-245. |
| [9] | LYU Zongping, ZHONG Youbing, GU Zhaojun. Threat Intelligence Analysis Research Based on Kill Chain and Network Traffic Detection[J]. Application Research of Computers, 2017,34(6):1794-1797. |
| 吕宗平, 钟友兵, 顾兆军. 基于攻击链和网络流量检测的威胁情报分析研究[J]. 计算机应用研究, 2017,34(6):1794-1797. | |
| [10] | KIM E, KIM K, SHIN D, et al. CyTIME: Cyber Threat Intelligence ManagEment Framework for Automatically Generating Security Rules[C]// ACM. 13th International Conference on Future Internet Technologies, June 20-22, 2018, Seoul, Republic of Korea. New York: ACM, 2018: 1-5. |
| [11] | GASCON H, GROBAUER B, SCHRECK T, et al. Mining Attributed Graphs for Threat Intelligence[C]// ACM. The 7th ACM on Conference on Data and Application Security and Privacy, March 22-24, 2017, Scottsdale, Arizona, USA. New York: ACM, 2017: 15-22. |
| [12] | WAGNER C, DULAUNOY A, LKLODY A, et al. MISP-The Design and Implementation of a Collaborative Threat Intelligence Sharing Platform[C]// ACM. 2016 ACM on Workshop on Information Sharing and Collaborative Security, October 24, 2016, Vienna Austria. New York: ACM, 2016: 49-56. |
| [13] | VERMA M, KUMARGURU P, DEB S B, et al. Analysing Indicator of Compromises for Ransomware: Leveraging IOCs with Machine Learning Techniques[C]// IEEE. 2018 IEEE International Conference on Intelligence and Security Informatics, November 9-11, 2018, Miami, FL, USA. New Jersey: IEEE, 2018: 154-159. |
| [14] | RODRIGUEZ A, LAIO A. Clustering by Fast Search and Find of Density Peaks[EB/OL]. http://sites.psu.edu/mcnl/files/2017/03/9-2dhti48.pdf, 2014-06-14. |
| [15] | MITRE. Structured Threat Information eXpression[EB/OL]. https://stixproject.github.io/about/, 2020-09-28. |
| [16] | HUANG Yajuan. Research on Network Threat Intelligence in the United States[D]. Changsha: National University of Defense Technology, 2018. |
| 黄雅娟. 美国网络威胁情报工作研究[D]. 长沙:国防科技大学, 2018. | |
| [17] | CUCKOO Foundation. Automated Mailware Analysis: Cuckoo Sandbox[EB/OL]. https://cuckoo.sh/docs/, 2020-09-28. |
| [18] | KORNBLUM J. Identifying Almost Identical Files Using Context Triggered Piecewise Hashing[EB/OL]. https://www.sciencedirect.com/science/article/pii/S1742287606000764, 2020-09-28. |
| [19] | MITRE. A Python Library for Parsing, Manipulating, and Generating Structured Threat Information eXpression(STIX™) v1.2.0 Content[EB/OL]. https://github.com/STIXProject/python-stix, 2020-09-28. |
| [20] |
SERKETZIS N, KATOS V, LLIOUDIS C, et al. Actionable Threat Intelligence for Digital Forensics Readiness[J]. Information and Computer Security, 2019,27(2):273-291.
doi: 10.1108/ICS-09-2018-0110 URL |
| [1] | ZHENG Dong, ZHAO Yue. Android Malware Detection Based on SM3 and Multi-feature [J]. Netinfo Security, 2020, 20(6): 17-25. |
| [2] | ZHANG Yongsheng, WANG Zhi, WU Yijie, DU Zhenhua. Cyber Threat Intelligence Propagation Based on Conformal Prediction [J]. Netinfo Security, 2020, 20(6): 90-95. |
| [3] | XU Guotian, SHEN Yaotong. A Malware Detection Method Based on XGBoost and LightGBM Two-layer Model [J]. Netinfo Security, 2020, 20(12): 54-63. |
| [4] | TAN Yang, LIU Jiayong, ZHANG Lei. Malware Familial Classification of Deep Auto-encoder Based on Mixed Features [J]. Netinfo Security, 2020, 20(12): 72-82. |
| [5] | HUANG Baohua, CHENG Qi, YUAN Hong, HUANG Pirong. K-means Clustering Algorithm Based on Differential Privacy with Distance and Sum of Square Error [J]. Netinfo Security, 2020, 20(10): 34-40. |
| [6] | HOU Liuyang, LUO Senlin, PAN Limin, ZHANG Ji. Multi-feature Android Malware Detection Method [J]. Netinfo Security, 2020, 20(1): 67-74. |
| [7] | Xin SONG, Kai ZHAO, Linlin ZHANG, Wenbo FANG. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [8] | Yanchen QIAO, Qingshan JIANG, Liang GU, Xiaoming WU. Malware Classification Method Based on Word Vector of Assembly Instruction and CNN [J]. Netinfo Security, 2019, 19(4): 20-28. |
| [9] | Yanming FU, Zhenduo LI. Research on k-means++ Clustering Algorithm Based on Laplace Mechanism for Differential Privacy Protection [J]. Netinfo Security, 2019, 19(2): 43-52. |
| [10] | Xuruirui FENG, Jiayong LIU, Pengsen CHENG. Analyzing Malware Behavior and Capability Related Text Based on Feature Extraction [J]. Netinfo Security, 2019, 19(12): 72-78. |
| [11] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [12] | Xie LU, Shoushan LUO, Yumei ZHANG. Research on Hadoop-based Massive Security Log Clustering Algorithm [J]. Netinfo Security, 2018, 18(8): 56-63. |
| [13] | Yunchun LI, Wentao LU, Wei LI. Malware Detection Method Based on Shapelet [J]. Netinfo Security, 2018, 18(3): 70-77. |
| [14] | Wei ZHAO, Na ZHAO, Yixing ZHANG. Spectral Clustering Bipartite Graph Segmentation Method Based on Color Invariant Features [J]. Netinfo Security, 2018, 18(12): 8-14. |
| [15] | Li HE, Yuanhui YAO. Detection and Recognition Strategy for Anomaly of Cloud Virtual Machine Based on Context Clustering [J]. Netinfo Security, 2018, 18(12): 54-65. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||