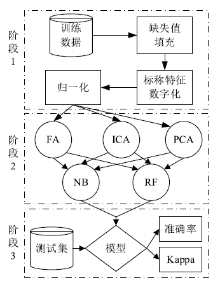
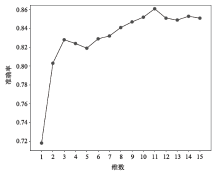
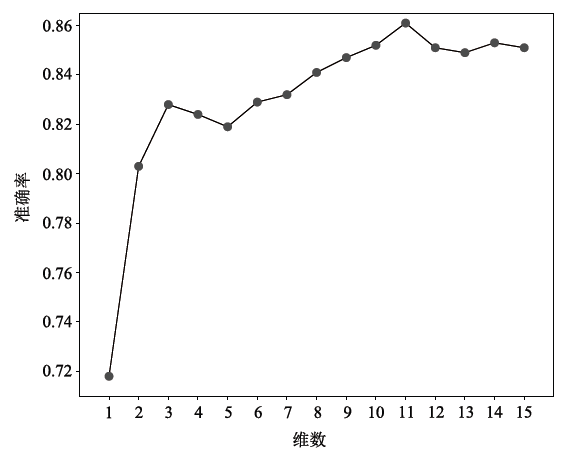
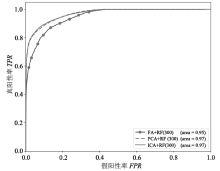
| [1] |
SHAHZAD A A, KIM Y G, ELGAMOUDI A.Secure IoT Platform for Industrial Control Systems[C]//IEEE. 2017 International Conference on Platform Technology and Service(PlatCon), February 13-15, 2017, Busan, South Korea. New York: IEEE, 2017: 1-6.
|
| [2] |
SHERASIYA T, UPADHYAY H, PATEL H B.A Survey: Intrusion Detection System for Internet of Things[J]. International Journal of Computer Science and Engineering, 2016, 5(2): 91-98.
|
| [3] |
HE Xiang, LIU Sheng, JIANG Jiguo.Comparative Study of Intrusion Detection Methods Based on Machine Learning[J]. Netinfo Security, 2018, 18(5): 1-11.
|
|
和湘,刘晟,姜吉国.基于机器学习的入侵检测方法对比研究[J].信息网络安全,2018,18(5):7-17.
|
| [4] |
MUNA A L H, MOUSTAFA N, SITNIKOVA E. Identification of Malicious Activities in Industrial Internet of Things Based on Deep Learning Models[EB/OL]. , 2019-1-22.
|
| [5] |
AMIRI F, YOUSEFI M M R, LUCAS C, et al. Mutual Information-based Feature Selection for Intrusion Detection Systems[J]. Journal of Network and Computer Applications, 2011, 34(4): 1184-1199.
|
| [6] |
MOUSTAFA N, SLAY J.A Hybrid Feature Selection for Network Intrusion Detection Systems: Central Points and Association Rules[C]//Joondalup Campus. 16th Australian Information Warfare Conference, November 30-December 2, 2015, Edith Cowan University, Perth, Western Australia. Western Australia: Edith Cowan University, 2015: 5-13.
|
| [7] |
BELOUCH M, EL HADAJ S, IDHAMMAD M.A Two-stage Classifier Approach Using Reptree Algorithm for Network Intrusion Detection[J]. International Journal of Advanced Computer Science and Applications, 2017, 8(6): 389-394.
|
| [8] |
ANWER H M, FAROUK M, ABDEL-HAMID A.A Framework for Efficient Network Anomaly Intrusion Detection with Features Selection[C]//IEEE. 9th International Conference on Information and Communication Systems, April 3-5, 2018, Irbid, Jordan. New York, IEEE, 2018: 157-162.
|
| [9] |
ELKHADIR Z, CHOUGDALI K, BENATTOU M.Intrusion Detection System Using PCA and Kernel PCA Methods[C]//Springer. The Mediterranean Conference on Information & Communication Technologies 2015, May 7-9, 2015, Saidia, Morocco. Heidelberg: Springer, 2016: 489-497.
|
| [10] |
LIN Weining, CHEN Mingzhi, ZHAN Yunqing, et al.Research on an Intrusion Detection Algorithm Based on PCA and Random-forest Classification[J]. Netinfo Security, 2017, 17(11): 50-54.
|
|
林伟宁,陈明志,詹云清,等.一种基于PCA和随机森林分类的入侵检测算法研究[J].信息网络安全,2017,17(11):50-54.
|
| [11] |
HYVARINEN A.Fast and Robust Fixed-point Algorithms for Independent Component Analysis[J]. IEEE Transactions on Neural Networks, 2002, 10(3): 626-634.
|
| [12] |
ZOU Su, LI Chuanri, XU Fei, et al.Correlation Factor Analysis of FEA Model Simplification Methods of Printed Circuit Board[C]//IEEE. 7th International Conference on Computational Intelligence and Security, December 3-4, 2011, Hainan, China. New York: IEEE, 2011: 1461-1465.
|
| [13] |
MOUSTAFA N, SLAY J.The Significant Features of the UNSW-NB15 and the KDD99 Data Sets for Network Intrusion Detection Systems[C]//IEEE. 4th International Workshop on Building Analysis Datasets and Gathering Experience Returns for Security, November 5, 2015, Kyoto, Japan. New York: IEEE, 2015: 25-31.
|