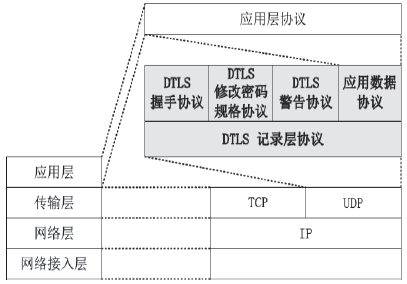
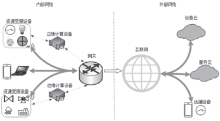
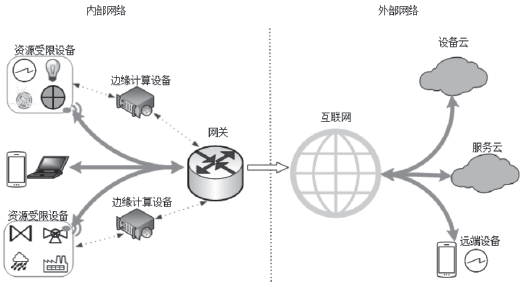
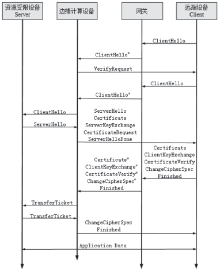
| [1] |
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
| [2] |
LEHONG H.Hype Cycle for the Internet of Things [R]. Stamford: Gartner Inc,G00234864, 2012.
|
| [3] |
张晓惠,林柏钢. 基于平衡二叉决策树SVM算法的物联网安全研究[J]. 信息网络安全,2015(8):20-25.
|
| [4] |
Luk M, Mezzour G, Perrig A, et al.MiniSec: A Secure Sensor Network Communication Architecture[C]// IEEE. International Symposium on Information Processing in Sensor Networks, April 25-27 2007, Cambridge, MA, USA. New York: IEEE, 2007:479-488.
|
| [5] |
高君丰,崔玉华,罗森林,等. 信息系统可控性评价研究[J]. 信息网络安全,2015(8):67-75.
|
| [6] |
YU H, HE J, ZHANG T, XIAO P, et al.Enabling end-to-end Secure Communication Between Wireless Sensor Networks and the Internet[J]. World Wide Web, 2013, 16( 4):515-540.
|
| [7] |
BRACHMANN M, KEOH S L, MORCHON O G, et al.End-to-End Transport Security in the IP-Based Internet of Things[C]// IEEE. International Conference on Computer Communications and Networks, July 30-August 2, 2012, Munich, Germany. New York: IEEE, 2012:1-5.
|
| [8] |
GRANJAL J, MONTEIRO E, SILVA J S.End-to-end Transport-layer Security for Internet-integrated Sensing Applications with Mutual and Delegated ECC Public-key Authentication[C]// IEEE. Ifip NETWORKING Conference, May 22-24,2013, Brooklyn, NY, USA. New York: IEEE, 2013:1-9.
|
| [9] |
KOTHMAYR T, SCHMITT C, HU W, et al.DTLS based Security and Two-way Authentication for the Internet of Things[J]. Ad Hoc Networks, 2013, 11(8):2710-2723.
|
| [10] |
TAN C C, WANG H, ZHONG S, et al.IBE-Lite: a Lightweight Identity-based Cryptography for Body Sensor Networks.[J]. EEE Transactions on Information Technology in Biomedicine A Publication of the IEEE Engineering in Medicine & Biology Society,2009, 13(6):926-932.
|
| [11] |
BORMANN C, ERESUE M, KERANEN A.RFC7228: Terminology for Constrained Node Networks[EB/OL].
|
| [12] |
DAWSON-HAGGERTY S, TAVAKOLI A, CULLER D.Hydro: A Hybrid Routing Protocol for Low-Power and Lossy Networks[C]// IEEE. First IEEE International Conference on Smart Grid Communications, October 4-6, 2010, Gaithersburg, MD, USA. New York: IEEE, 2010:268-273.
|
| [13] |
SHI W, CAO J, ZHANG Q, et al.Edge Computing: Vision and Challenges[J]. IEEE Internet of Things Journal, 2016, 3(5):637-646.
|
| [14] |
GREENBERG A, HAMILTON J, MALTZ D A, et al.The Cost of a Cloud: Research Problems in Data Center Networks[J]. Acm Sigcomm Computer Communication Review, 2008, 39(1):68-73.
|
| [15] |
JARARWEN Y, TAWALBEH L, ABABNEH F, et al.Resource Efficient Mobile Computing Using Cloudlet Infrastructure[C]// IEEE. International Conference on Mobile Ad-Hoc and Sensor Networks, December 11-13, 2013, Dalian, China . New York: IEEE, 2013:373-377.
|
| [16] |
BONOMI F, MILITO R, ZHU J, et al.Fog Computing and its Role in the Internet of Things[C]// ACM. Edition of the Mcc Workshop on Mobile Cloud Computing, August 17, 2012, Helsinki, Finland.New York: ACM, 2012:13-16.
|
 ), Lei BAI2, Qingqi PEI2, Xiangjun LI1
), Lei BAI2, Qingqi PEI2, Xiangjun LI1