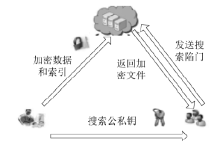
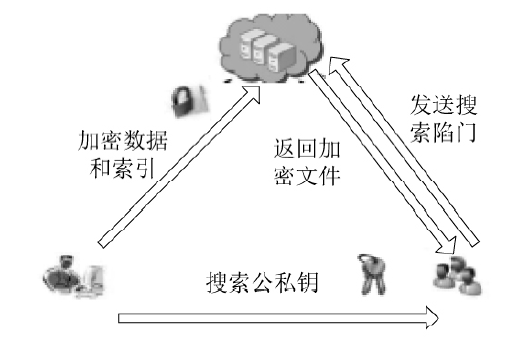
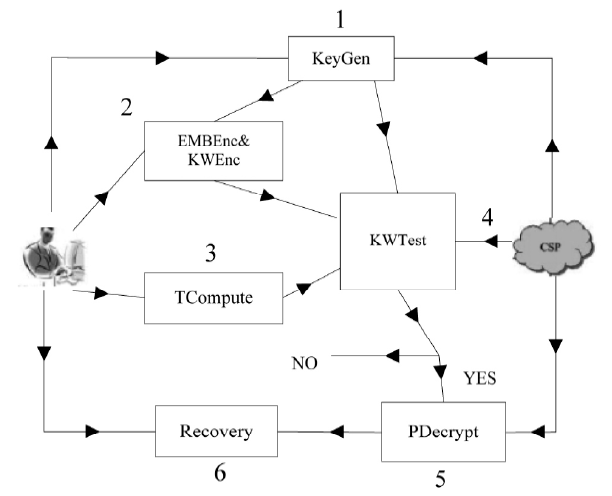
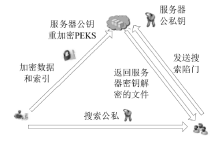
| [1] |
BONEH D, DI CRESCENZO G, OSTROVSKY R, et al.Public Key Encryption with Keyword Search[C]//Advances in Cryptology-Eurocrypt 2004. Springer Berlin Heidelberg, 2004: 506-522.
|
| [2] |
SONG D X, WAGNER D, PERRIG A.Practical Techniques for Searches on Encrypted Data[C]//Security and Privacy, 2000, S&P 2000. Proceedings. 2000 IEEE Symposium on, IEEE, 2000: 44-55.
|
| [3] |
CHANG Y C, MITZENMACHER M.Privacy preserving keyword searches on remote encrypted data[C]//Third International Conference, ACNS, New York, 2005: 442-455.
|
| [4] |
CURTMOLA R, GARAY J, KAMARA S, et al.Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[C]//ACM Conference on Computer and Communica-tions Security 2006, New York, 2006: 79-88.
|
| [5] |
BAEK J, SAFAVI-NAINI R, SUSILO W.Public Key Encryption with Keyword Search Revisited[C]//Computational Science and Its Applications-ICCSA 2008, Perugia, Italy, 2008: 1249-1259.
|
| [6] |
RHEE H S, PARK J H, SUSILO W, et al.Trapdoor Security in a Searchable Public-key Encryption Scheme with a designated Tester[J]. Journal of Systems and Software, 2010, 83(5): 763-771.
|
| [7] |
LI J, WANG Q, WANG C, et al.Fuzzy Keyword Search over Encrypted Data in Cloud Computing[J]. Computer Science & Information Systems, 2013, (2): 1-5.
|
| [8] |
LIU Q, WANG G, WU J.Secure and Privacy Preserving Keyword Searching for Cloud Storage Services[J]. Journal of network and computer applications, 2012, 35(3): 927-933.
|
| [9] |
BONEH D, FRANKLIN M.Identity-based Encryption from the Weil Pairing[J]. Siam Journal on Computing, 2001, 32(3): 213-229.
|
| [10] |
LEVENSTEIN V.Binary Codes Capable of Correcting Spurious Insertions and Deletions Of Ones[J]. Problems of Information Transmission, 1965, 1(1): 8-17.
|
| [11] |
秦志光,吴世坤,熊虎. 云存储服务中数据完整性审计方案综述[J]. 信息网络安全,2014,(7):1-6.
|
| [12] |
Menezes A J, Okamoto T, Vanstone S A.Reducing Elliptic Curve Logarithms to a Finite Field[J]. IEEE Tran on Info Theory, 1993, 39(5): 1639-1646.
|
| [13] |
黄婕. 基于弹性云计算的移动式数据终端的密集型算法[J]. 计算机应用与软件,2013,30(11):210-213.
|
| [14] |
洪澄,张敏,冯登国. 面向云存储的高效动态密文访问控制方法[J]. 通信学报,2011,32(7):125-132.
|
| [15] |
LIU Q, WANG G, WU J.An Efficient Privacy Preserving Keyword Search Scheme in Cloud Computing[C]//2009 International Conference on Computational Science and Engineering, Vancouver, 2009: 715-720pp.
|
| [16] |
乔宏明,姚文胜. 基于策略提升公共云存储信息安全水平的方案研究[J]. 移动通信,2013,(21):53-57.
|
| [17] |
RHEE H S, SUSILO W, KIM H J.Secure searchable public key encryption scheme against keyword guessing attacks[J]. IEICE Electronics Express, 2009, 6(5): 237-243.
|
| [18] |
LI M, YU S, CAO N, et al. Authorized private keyword search over encrypted data in cloud computing[EB/OL]. , 2015-03-11.
|
| [19] |
吕从东,韩臻,马威. 云存储服务端数据存储加密机制的设计和实现[J]. 信息网络安全,2014,(6):1-5.
|
| [20] |
张婷,杨庚,滕玮,等. 云计算中基于属性和定长密文的访问控制方法[J]. 计算机技术与发展,2013,23(11):128-132.
|
| [21] |
LI C, LU J, LU Y.Efficient merging and filtering algorithms for approximate string searches[C]//IEEE International Conference on Data Engineering. IEEE, 2008: 257-266.
|
| [22] |
王威,吴羽翔,金鑫,等. 基于可信第三方的公有云平台的数据安全存储方案[J]. 信息网络安全,2014,(2):68-74.
|
| [23] |
沈志荣,薛巍,舒继武. 可搜索加密机制研究与进展[J]. 软件学报,2014,25(4):880-895.
|
| [24] |
ABU-LIBDEH H, PRINCEHOUSE L, WEATHERSPOON H.RACS: a case for cloud storage diversity[C]//Proceedings of the 1st ACM symposium on Cloud computing. ACM, 2010: 229-240.
|
| [25] |
李双,徐茂智. 基于属性的可搜索加密方案[J]. 计算机学报,2014,37(5):1017-1024.
|
| [26] |
DENG J, HU J, LIU A C M, et al. Research and Application of Cloud Storage[C]//Intelligent Systems and Applications (ISA), 2010 2nd International Workshop on. IEEE, 2010: 1-5.
|
| [27] |
王映康,罗文俊. 云存储环境下多用户可搜索加密方案[J]. 电信科学,2012,(11):103-107.
|
 ), ZHAO Yang, XIONG Hu
), ZHAO Yang, XIONG Hu