Netinfo Security ›› 2025, Vol. 25 ›› Issue (9): 1397-1406.doi: 10.3969/j.issn.1671-1122.2025.09.008
Previous Articles Next Articles
Research and Implementation of Ransomware Detection Technology Based on Hardware Performance Counters
ZHAO Wenyu1, DANG Chenxi2,3, DU Zhenhua4, ZHANG Jian2,3( )
)
- 1. Tianjin Institute of Navigational Instruments, Tianjin 300131, China
2. College of Cryptology and Cyber Science, Nankai University, Tianjin 300350, China
3. Tianjin Key Laboratory of Network and Data Security Technology, Tianjin 300350, China
4. National Computer Virus Emergency Response Center, Tianjin 300392, China
-
Received:2025-06-15Online:2025-09-10Published:2025-09-18
CLC Number:
Cite this article
ZHAO Wenyu, DANG Chenxi, DU Zhenhua, ZHANG Jian. Research and Implementation of Ransomware Detection Technology Based on Hardware Performance Counters[J]. Netinfo Security, 2025, 25(9): 1397-1406.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.09.008
| 模型 | 独立训练 | Accuracy | Precision | Recall | F1 | MCC | FPR | FNR |
|---|---|---|---|---|---|---|---|---|
| EGB | 1 | 96.65% | 95.33% | 95.20% | 96.73% | 94.08% | 2.67% | 1.83% |
| 2 | 96.55% | 96.57% | 95.84% | 95.18% | 93.65% | 3.77% | 1.32% | |
| 3 | 95.12% | 96.74% | 95.90% | 95.80% | 94.09% | 2.98% | 2.11% | |
| 平均 | 96.10% | 96.21% | 95.64% | 95.90% | 93.94% | 3.14% | 1.75% | |
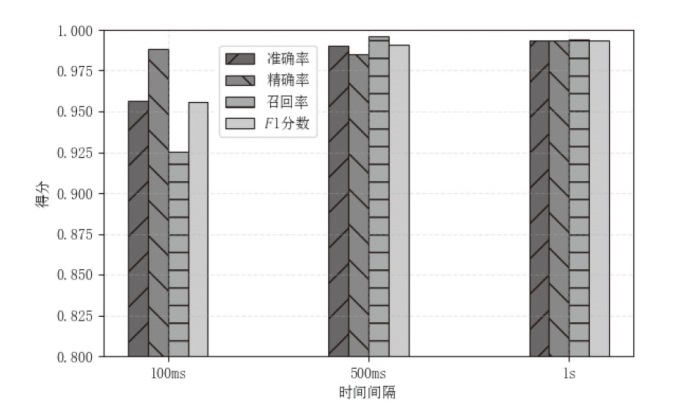
| 本文模型 | 1 | 99.28% | 99.21% | 99.37% | 99.41% | 99.11% | 0.84% | 0.35% |
| 2 | 99.17% | 99.45% | 99.45% | 99.49% | 98.29% | 1.02% | 0.78% | |
| 3 | 99.63% | 99.39% | 98.54% | 99.24% | 98.79% | 0.009% | 0.64% | |
| 平均 | 99.36% | 99.35% | 99.12% | 99.38% | 98.73% | 0.92% | 0.59% |
| [1] | 360 Digital Security Group. 2024 Ransomware Trends Report[EB/OL]. (2025-01-09)[2025-05-20]. https://360.cn/n/12648.html. |
| [2] | Cybersecurity Ventures. 2024 Cybersecurity Almanac: 100 Facts, Figures, Predictions And Statistics[EB/OL]. (2024-06-24)[2025-05-20]. https://cybersecurityventures.com/cybersecurity-almanac-2024/. |
| [3] | KHARAZ A, ARSHAD S, MULLINER C, et al. UNVEIL:A Large-Scale, Automated Approach to Detecting Ransomware[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley: USENIX Association, 2016: 757-772. |
| [4] | SCAIFE N, CARTER H, TRAYNOR P, et al. Cryptolock (and Drop It): Stopping Ransomware Attacks on User Data[C]// IEEE. 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2016: 303-312. |
| [5] | CHEN ZhiGuo, KANG H S, YIN Shangnan, et al. Automatic Ransomware Detection and Analysis Based on Dynamic API Calls Flow Graph[C]// ACM. The International Conference on Research in Adaptive and Convergent Systems. New York: ACM, 2017: 196-201. |
| [6] | LEE J, JEONG K, LEE H. Detecting Metamorphic Malwares Using Code Graphs[C]// ACM. The 2010 ACM Symposium on Applied Computing. New York: ACM, 2010: 1970-1977. |
| [7] | KOK S H, ABDULLAH A, JHANJHI N Z, et al. Prevention of Crypto-Ransomware Using a Pre-Encryption Detection Algorithm[J]. Computers, 2019, 8(4): 79-94. |
| [8] | ALHAWI O M K, BALDWIN J, DEHGHANTANHA A. Leveraging Machine Learning Techniques for Windows Ransomware Network Traffic Detection[J]. Cyber Threat Intelligence, 2018: 93-106. |
| [9] | ZHOU Boyou, GUPTA A, JAHANSHAHI R, et al. Hardware Performance Counters can Detect Malware: Myth or Fact?[C]// ACM. The 2018 on Asia Conference on Computer and Communications Security. New York: ACM, 2018: 457-468. |
| [10] | ZHOU Hongwei, WU Xin, SHI Wenchang, et al. HDROP: Detecting ROP Attacks Using Performance Monitoring Counters[C]// Springer. International Conference on Information Security Practice and Experience. Heidelberg: Springer, 2014: 172-186. |
| [11] | HERATH N, FOGH A. CPU Hardware Performance Counters for Security[EB/OL]. (2015-08-01)[2025-08-20]. https://www.blackhat.com/us-15/briefings.html. |
| [12] | CARVALHO DE MELO A. The New Linux Perf Tools[J]. Slides from Linux Kongress. 2010, 18(1): 1-42. |
| [13] | ALAM M, BHATTACHARYA S, DUTTA S, et al. RATAFIA: Ransomware Analysis Using Time and Frequency Informed Autoencoders[C]// IEEE. 2019 IEEE International Symposium on Hardware Oriented Security and Trust (HOST). New York: IEEE, 2019: 218-227. |
| [14] | WANG Xueyang, CHAI S, ISNARDI M, et al. Hardware Performance Counter-Based Malware Identification and Detection with Adaptive Compressive Sensing[J]. ACM Transactions on Architecture and Code Optimization (TACO), 2016, 13(1): 1-23. |
| [15] | DEMME J, MAYCOCK M, SCHMITZ J, et al. On the Feasibility of Online Malware Detection with Performance Counters[J]. ACM SIGARCH Computer Architecture News, 2013, 41(3): 559-570. |
| [16] | KAZDAGLI M, REDDI V J, TIWARI M. Quantifying and Improving the Efficiency of Hardware-Based Mobile Malware Detectors[C]// IEEE. 2016 49th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO). New York: IEEE, 2016: 1-13. |
| [17] | KRISHNAMURTHY P, RAMESH K, FAARSHAD K. Anomaly Detection in Real-Time Multi-Threaded Processes Using Hardware Performance Counters[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 666-680. |
| [18] | HE Zhangying, HOUMAN H, HOSSEIN S. Beyond Conventional Defenses: Proactive and Adversarial-Resilient Hardware Malware Detection Using Deep Reinforcement Learning[C]// ACM. The 61st ACM/IEEE Design Automation Conference. New York: ACM, 2024: 1-6. |
| [19] | LI Congmiao, GAUDIOT J L. Detecting Spectre Attacks Using Hardware Performance Counters[J]. IEEE Transactions on Computers, 2022, 71(6): 1320-1331. |
| [20] | GANFURE G O, WU Chunfeng, CHANG Yuanhao, et al. Deepware: Imaging Performance Counters with Deep Learning to Detect Ransomware[J]. IEEE Transactions on Computers, 2022, 72(3): 600-613. |
| [21] |
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
doi: 10.1162/neco.1997.9.8.1735 pmid: 9377276 |
| [22] | GRAVES A. Supervised Sequence Labelling with Recurrent Neural Networks[M]. Heidelberg: Springer, 2012. |
| [23] | VASWANI A, SHAZEER N, PARMAR N, et al. Attention is all you need[C]// Curran Associates Inc. Proceedings of the 31st International Conference on Neural Information Processing Systems. New York: Curran Associates Inc, 2017: 6000-6010. |
| [24] | AURANGZEB S, RAIS R N B, ALEEM M, et al. On the Classification of Microsoft-Windows Ransomware Using Hardware Profile[EB/OL]. (2021-02-02) [2025-08-20]. https://peerj.com/articles/cs-361/#intro. |
| [1] | ZHAN Dongyang, HUANG Zilong, TAN Kai, YU Zhaofeng, HE Zheng, ZHANG Hongli. Cross-Function Behavior Analysis and Constraint Technology for Serverless Applications [J]. Netinfo Security, 2025, 25(9): 1329-1337. |
| [2] | CAO Jun, XIANG Ga, REN Yawei, TAN Zicheng, YANG Qunsheng. Small-Sample APT Attack Event Extraction Method Based on Large Model [J]. Netinfo Security, 2025, 25(9): 1338-1347. |
| [3] | HU Yucui, GAO Haotian, ZHANG Jie, YU Hang, YANG Bin, FAN Xuejian. Automated Exploitation of Vulnerabilities in Vehicle Network Security [J]. Netinfo Security, 2025, 25(9): 1348-1356. |
| [4] | XUE Lei, ZHANG Jican, DU Pingxin. Intelligent Binary Analysis Method Based on Enhanced Semantic Program Dependency Graph [J]. Netinfo Security, 2025, 25(9): 1357-1366. |
| [5] | XU Ruzhi, WU Xiaoxin, LYU Changran. Research on Transformer-Based Super-Resolution Network Adversarial Sample Defense Method [J]. Netinfo Security, 2025, 25(9): 1367-1376. |
| [6] | LIU Hui, ZHU Zhengdao, WANG Songhe, WU Yongcheng, HUANG Linquan. Jailbreak Detection for Large Language Model Based on Deep Semantic Mining [J]. Netinfo Security, 2025, 25(9): 1377-1384. |
| [7] | WANG Lei, CHEN Jiongyi, WANG Jian, FENG Yuan. Intelligent Reverse Analysis Method of Firmware Program Interaction Relationships Based on Taint Analysis and Textual Semantics [J]. Netinfo Security, 2025, 25(9): 1385-1396. |
| [8] | YANG Yukun, XIAO Weien, LIANG Boxuan, HUANG Xin. Dynamic Three-Factor Authentication Key Agreement Protocol for IoT Scenarios [J]. Netinfo Security, 2025, 25(9): 1407-1417. |
| [9] | CHEN Xianyi, WANG Xuebo, CUI Qi, FU Zhangjie, WANG Qianqian, ZENG Yifu. Overview of Backdoor Attacks and Defenses in Personalized Federated Learning [J]. Netinfo Security, 2025, 25(9): 1418-1438. |
| [10] | SHI Yijuan, ZHOU Danping, FAN Lei, LIU Yin. Secure Multi-Party Computation Protocol Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(9): 1439-1446. |
| [11] | YANG Jianxin, WANG Xiaoding, LIN Hui. Improved Consensus Algorithm Based on HotStuff and Multi-Ary Trees [J]. Netinfo Security, 2025, 25(9): 1447-1455. |
| [12] | CHEN Yonghao, CAI Manchun, ZHANG Yiwen, PENG Shufan, YAO Lifeng, ZHU Yi. A Multi-Scale and Multi-Level Feature Fusion Approach for Deepfake Face Detection [J]. Netinfo Security, 2025, 25(9): 1456-1464. |
| [13] | WANG Xinmeng, CHEN Junbao, YANG Yitao, LI Wenjin, GU Dujuan. Bayesian Optimized DAE-MLP Malicious Traffic Identification Model [J]. Netinfo Security, 2025, 25(9): 1465-1472. |
| [14] | CAO Yue, FANG Boying, WEI Gaoda, LI Jinyu, YANG Yang, PENG Tao. Compatibility Evaluation and Optimization of CAN Bus Intrusion Detection Systems in In-Vehicle Ethernet Environment [J]. Netinfo Security, 2025, 25(8): 1175-1195. |
| [15] | LU Xinxi, GUO Jianwei, YUAN Lijuan, LIU Yan, XU Binbin, LIU Yang. Research on Container Security Framework Based on Namespace and Filesystem Proxy [J]. Netinfo Security, 2025, 25(8): 1196-1207. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||