Netinfo Security ›› 2025, Vol. 25 ›› Issue (9): 1465-1472.doi: 10.3969/j.issn.1671-1122.2025.09.014
Previous Articles Next Articles
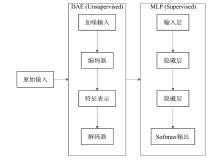
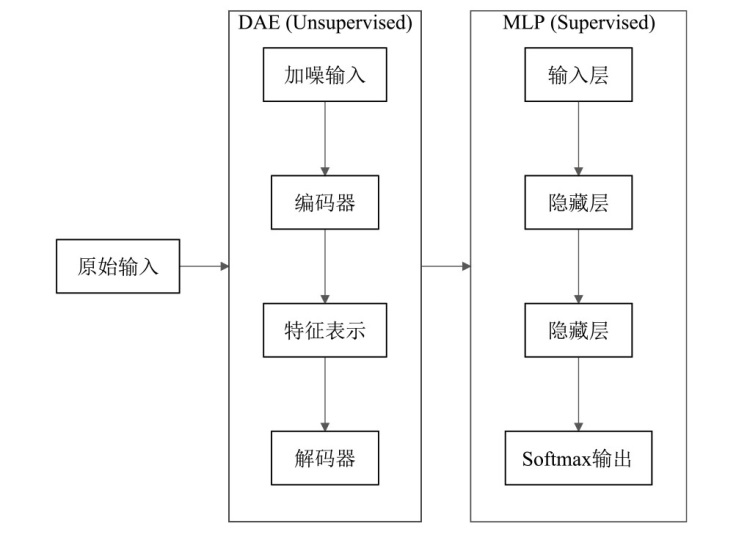
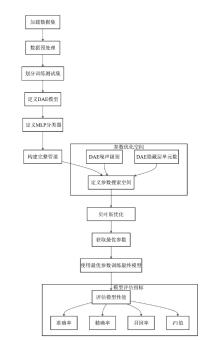
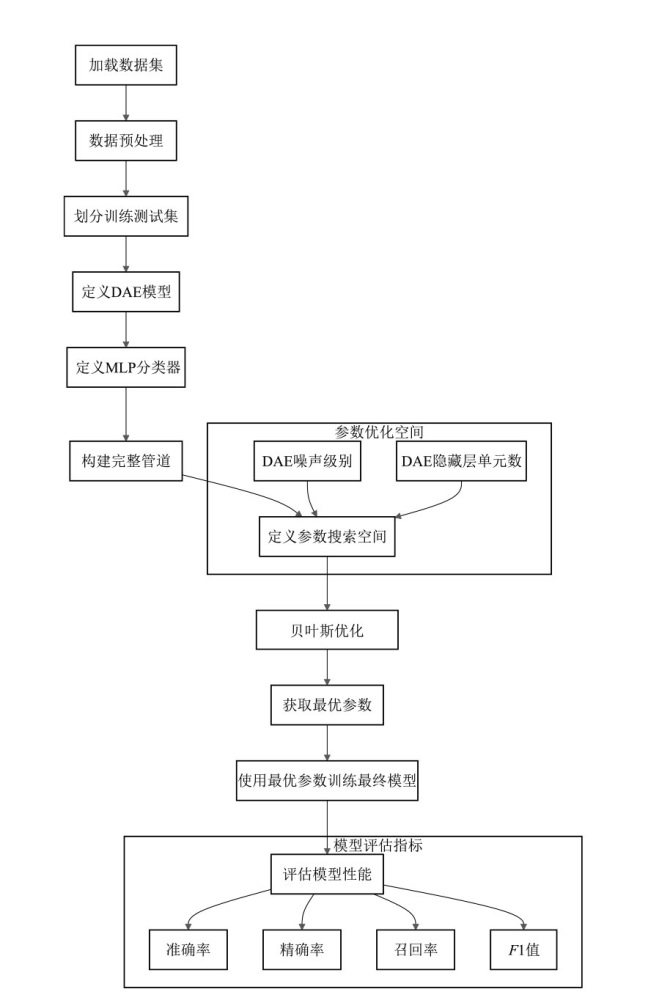
Bayesian Optimized DAE-MLP Malicious Traffic Identification Model
WANG Xinmeng1( ), CHEN Junbao1, YANG Yitao1, LI Wenjin2, GU Dujuan2
), CHEN Junbao1, YANG Yitao1, LI Wenjin2, GU Dujuan2
- 1. Department of Information Technology, Nanjing Police University, Nanjing 210023, China
2. NSFOCUS Technologies Group Co., Ltd., Beijing 100080, China
-
Received:2025-06-05Online:2025-09-10Published:2025-09-18
CLC Number:
Cite this article
WANG Xinmeng, CHEN Junbao, YANG Yitao, LI Wenjin, GU Dujuan. Bayesian Optimized DAE-MLP Malicious Traffic Identification Model[J]. Netinfo Security, 2025, 25(9): 1465-1472.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.09.014
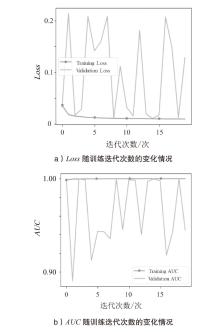
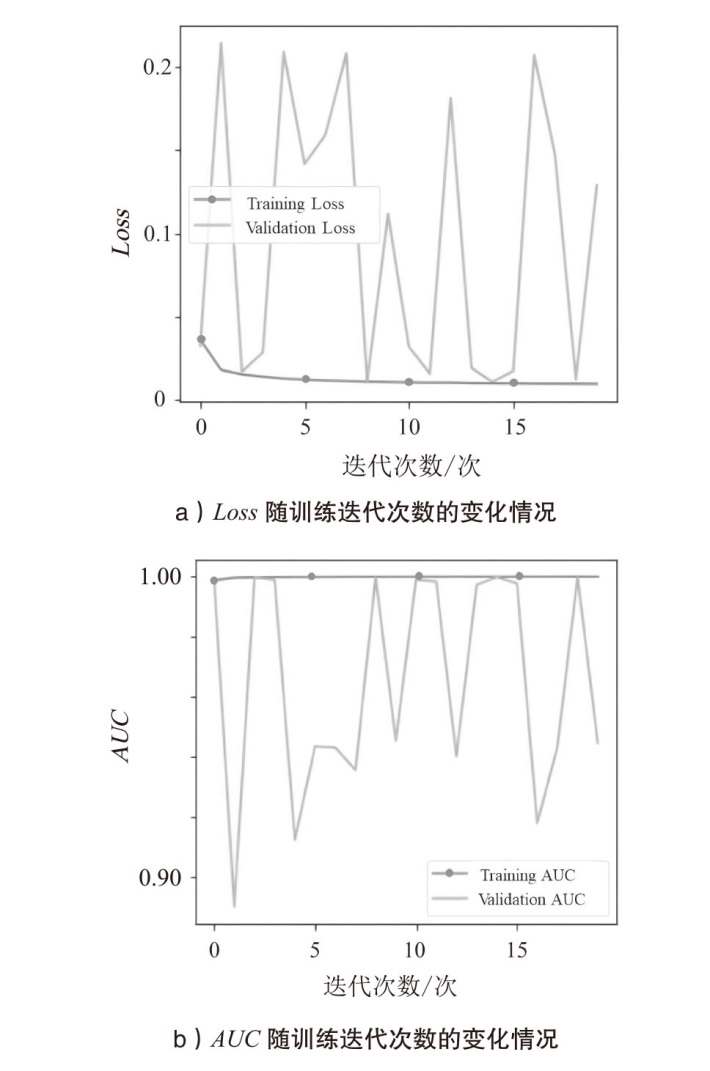
| 迭代次数/次 | Loss | action_AUC | val_loss | val_action_AUC |
|---|---|---|---|---|
| 0 | 0.036335 | 0.998471 | 0.032487 | 0.998998 |
| 1 | 0.018133 | 0.999324 | 0.214438 | 0.890129 |
| 2 | 0.015530 | 0.999441 | 0.017086 | 0.999524 |
| 3 | 0.014110 | 0.999501 | 0.028566 | 0.998675 |
| 4 | 0.013048 | 0.999553 | 0.209165 | 0.912300 |
| 5 | 0.012381 | 0.999555 | 0.141838 | 0.943375 |
| 6 | 0.011859 | 0.999591 | 0.159256 | 0.942962 |
| 7 | 0.011508 | 0.999633 | 0.208285 | 0.935487 |
| 8 | 0.011195 | 0.999619 | 0.010951 | 0.999571 |
| 9 | 0.011012 | 0.999638 | 0.111816 | 0.945271 |
| 10 | 0.010776 | 0.999645 | 0.031982 | 0.998757 |
| 11 | 0.010602 | 0.999651 | 0.015887 | 0.998084 |
| 12 | 0.010613 | 0.999663 | 0.181298 | 0.940058 |
| 13 | 0.010297 | 0.999673 | 0.019244 | 0.997025 |
| 14 | 0.010227 | 0.999669 | 0.011030 | 0.999523 |
| 15 | 0.010153 | 0.999669 | 0.017522 | 0.997513 |
| 16 | 0.010014 | 0.999681 | 0.207399 | 0.917826 |
| 17 | 0.009968 | 0.999688 | 0.147266 | 0.943102 |
| 18 | 0.009935 | 0.999694 | 0.012492 | 0.999692 |
| 19 | 0.009838 | 0.999678 | 0.128855 | 0.944568 |
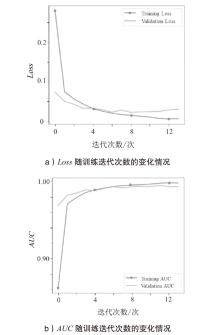
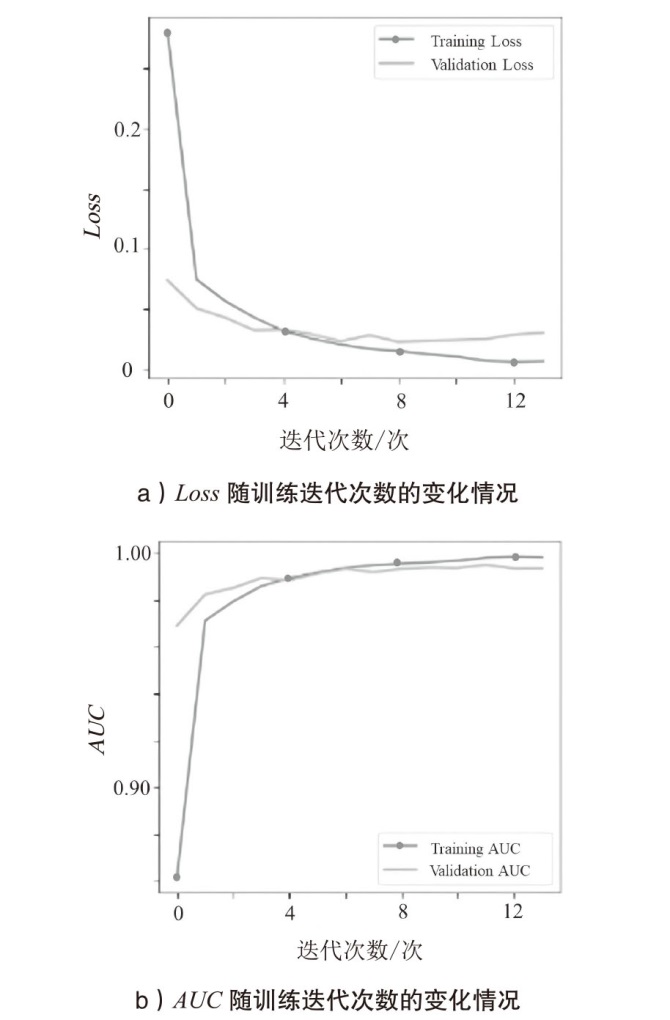
| 层(类型) | 输出形状 | 参数数量/个 |
|---|---|---|
| input_1 (InputLayer) | (None, 1000) | 0 |
| embedding (Embedding) | (None, 1000, 64) | 4800 |
| conv1d (Conv1D) | (None, 995, 64) | 24640 |
| max_pooling1d(MaxPooling1D) | (None, 248, 64) | 0 |
| conv1d_1 (Conv1D) | (None, 243, 128) | 49280 |
| max_pooling1d_1(MaxPooling1D) | (None, 60, 128) | 0 |
| flatten (Flatten) | (None, 384) | 0 |
| dense (Dense) | (None, 32) | 12320 |
| dropout (Dropout) | (None, 32) | 0 |
| 模型 | 时间复杂度 | 参数说明 |
|---|---|---|
| CNN | O(N×K2×C×H×W×L)+ O(K×H'×W'×L) | 输入数据的尺寸为H×W×C,卷积层数量为L,每个卷积层的卷积核数量为K,H'和W'是输出特征图的高度和宽度 |
| Transformer | O(N×(L2×d+L×d2)) | N表示序列数(样本数),L表示序列长度(特征数),d表示特征/ 嵌入维度 |
| RF | O(T×N×d)+O(T×d) | T表示树的数量,N表示数据集中样本数量,d表示树的平均深度 |
| 决策树 | O(N×M×log2N)+O(log2N) | N表示样本数,M表示特征数,log2N表示树的深度 |
| KNN | O(N×M)+O(Nlog2K) | N表示样本数,M表示特征数, K表示最近邻的数量 |
| DAE-MLP | O(N×D×H)+O(N× | N表示样本数,D表示特征数,H表示隐藏层神经元的数量,L表示MLP 的总层数, 第l、l+1 层的神经元数量 |
| [1] | MASEER Z K, YUSOF R, BAHAMAN N, et al. Benchmarking of Machine Learning for Anomaly Based Intrusion Detection Systems in the CICIDS2017 Dataset[J]. IEEE Access, 2021, 9: 22351-22370. |
| [2] | SANCHEZ O R, REPETTO M, CARREGA A, et al. Evaluating ML-Based DDoS Detection with Grid Search Hyperparameter Optimization[C]// IEEE. 2021 IEEE 7th International Conference on Network Softwarization. New York: IEEE, 2021: 402-408. |
| [3] | ELSAYED M S, LE-KHAC N A, DEV S, et al. DDoSNet: A Deep-Learning Model for Detecting Network Attacks[C]// IEEE. IEEE 21st International Symposium on a World of Wireless, Mobile and Multimedia Networks. New York: IEEE, 2020: 391-396. |
| [4] | SADAF K, SULTANA J. Intrusion Detection Based on Autoencoder and Isolation Forest in Fog Computing[J]. IEEE Access, 2020, 8: 167059-167068. |
| [5] | AMIRI F, YOUSEFI M R, LUCAS C, et al. Mutual Information-Based Feature Selection for Intrusion Detection Systems[J]. Journal of Network and Computer Applications, 2011, 34(4): 1184-1199. |
| [6] | MUKHERJEE S, SHARMA N. Intrusion Detection Using Naive Bayes Classifier with Feature Reduction[J]. Procedia Technology, 2012, 4: 119-128. |
| [7] | RAO B B, SWATHI K. Fast KNN Classifiers for Network Intrusion Detection System[J]. Indian Journal of Science and Technology, 2017, 10(14): 1-10. |
| [8] | THASEEN I S, KUMAR C A. Intrusion Detection Model Using Fusion of PCA and Optimized SVM[C]// IEEE. 2014 International Conference on Contemporary Computing and Informatics. New York: IEEE, 2014: 879-884. |
| [9] | CAO Yangchen, ZHU Guosheng, QI Xiaoyun, et al. Research on Intrusion Detection Classification Based on Random Forest[J]. Computer Science, 2021, 48(S1): 459-463. |
| 曹扬晨, 朱国胜, 祁小云, 等. 基于随机森林的入侵检测分类研究[J]. 计算机科学, 2021, 48(S1): 459-463. | |
| [10] | FAN Yuchen. Research on Intrusion Detection Based on Deep Learning and Association Rules[D]. Beijing: China Academy of Railway Sciences Corporation Limited, 2022. |
| 范禹辰. 基于深度学习和关联规则的入侵检测研究[D]. 北京: 中国铁道科学研究院, 2022. | |
| [11] | HOU Yuluo. Research on Malicious HTTP Request Detection Based on Machine Learning[D]. Chengdu: University of Electronic Science and Technology of China, 2022. |
| 侯禹洛. 基于机器学习的恶意HTTP请求检测研究[D]. 成都: 电子科技大学, 2022. | |
| [12] | GONG Xinyu. Research on Deeplearning Based Web Attack Detection[D]. Shanghai: Shanghai Jiao Tong University, 2020. |
| 龚昕宇. 基于深度学习的Web攻击检测研究[D]. 上海: 上海交通大学, 2020. | |
| [13] | VARTOUNI A M, KASHI S S, TESHNEHLAB M. An Anomaly Detection Method to Detect Web Attacks Using Stacked Auto-Encoder[C]// IEEE. 2018 6th Iranian Joint Congress on Fuzzy and Intelligent Systems. New York: IEEE, 2018: 131-134. |
| [14] | CHAKIR O, REHAIMI A, SADQI Y, et al. An Empirical Assessment of Ensemble Methods and Traditional Machine Learning Techniques for Web-Based Attack Detection in Industry 5.0[J]. Journal of King Saud University-Computer and Information Sciences, 2023, 35(3): 103-119. |
| [15] | KAMAL H, MASHALY M. Advanced Hybrid Transformer-CNN Deep Learning Model for Effective Intrusion Detection Systems with Class Imbalance Mitigation Using Resampling Techniques[EB/OL]. (2024-12-23)[2025-06-01]. https://doi.org/10.3390/fi16120481. |
| [1] | XU Ruzhi, WU Xiaoxin, LYU Changran. Research on Transformer-Based Super-Resolution Network Adversarial Sample Defense Method [J]. Netinfo Security, 2025, 25(9): 1367-1376. |
| [2] | ZHAO Wenyu, DANG Chenxi, DU Zhenhua, ZHANG Jian. Research and Implementation of Ransomware Detection Technology Based on Hardware Performance Counters [J]. Netinfo Security, 2025, 25(9): 1397-1406. |
| [3] | CHEN Yonghao, CAI Manchun, ZHANG Yiwen, PENG Shufan, YAO Lifeng, ZHU Yi. A Multi-Scale and Multi-Level Feature Fusion Approach for Deepfake Face Detection [J]. Netinfo Security, 2025, 25(9): 1456-1464. |
| [4] | CAO Yue, FANG Boying, WEI Gaoda, LI Jinyu, YANG Yang, PENG Tao. Compatibility Evaluation and Optimization of CAN Bus Intrusion Detection Systems in In-Vehicle Ethernet Environment [J]. Netinfo Security, 2025, 25(8): 1175-1195. |
| [5] | XIONG Ao, LIU Yuxiao, QIAN Xusheng, ZHANG Nan. Generative Steganography Method Based on Diffusion Model and Generative Adversarial Network [J]. Netinfo Security, 2025, 25(8): 1223-1230. |
| [6] | JIN Zhigang, LI Zimeng, CHEN Xuyang, LIU Zepei. Review of Network Intrusion Detection System for Unbalanced Data [J]. Netinfo Security, 2025, 25(8): 1240-1253. |
| [7] | SUN Nan, QIN Zhongyuan, HU Aiqun, LI Tao. Immune-Based Intrusion Detection Methods for Programmable Data Plane [J]. Netinfo Security, 2025, 25(8): 1263-1275. |
| [8] | WANG Gang, GAO Yunpeng, YANG Songru, SUN Litao, LIU Naiwei. A Survey on Deep Learning-Based Encrypted Malicious Traffic Detection Methods [J]. Netinfo Security, 2025, 25(8): 1276-1301. |
| [9] | XUN Yijie, CUI Jiarong, MAO Bomin, QIN Junman. Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning [J]. Netinfo Security, 2025, 25(6): 872-888. |
| [10] | ZHANG Xinglan, TAO Kejin. Universal Perturbations Generation Method Based on High-Level Features and Important Channels [J]. Netinfo Security, 2025, 25(5): 767-777. |
| [11] | LI Yuancheng, SUN Heyang, ZHANG Tong, ZHANG Hefang, YANG Liqun. DACDiff-Based Defense against FDIAs in Distributed Generation Dispatch and Control System [J]. Netinfo Security, 2025, 25(4): 578-586. |
| [12] | JIN Zengwang, JIANG Lingyang, DING Junyi, ZHANG Huixiang, ZHAO Bo, FANG Pengfei. A Review of Research on Industrial Control System Security [J]. Netinfo Security, 2025, 25(3): 341-363. |
| [13] | CHEN Hongsong, LIU Xinrui, TAO Zimei, WANG Zhiheng. A Survey of Anomaly Detection Model for Time Series Data Based on Deep Learning [J]. Netinfo Security, 2025, 25(3): 364-391. |
| [14] | LIU Chenfei, WAN Liang. CAN Bus Intrusion Detection Method Based on Spatio-Temporal Graph Neural Networks [J]. Netinfo Security, 2025, 25(3): 478-493. |
| [15] | LI Hailong, CUI Zhian, SHEN Xieyang. Overview of Anomaly Analysis and Detection Methods for Network Traffic [J]. Netinfo Security, 2025, 25(2): 194-214. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||