Netinfo Security ›› 2024, Vol. 24 ›› Issue (9): 1375-1385.doi: 10.3969/j.issn.1671-1122.2024.09.006
Previous Articles Next Articles
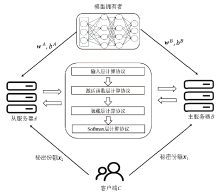
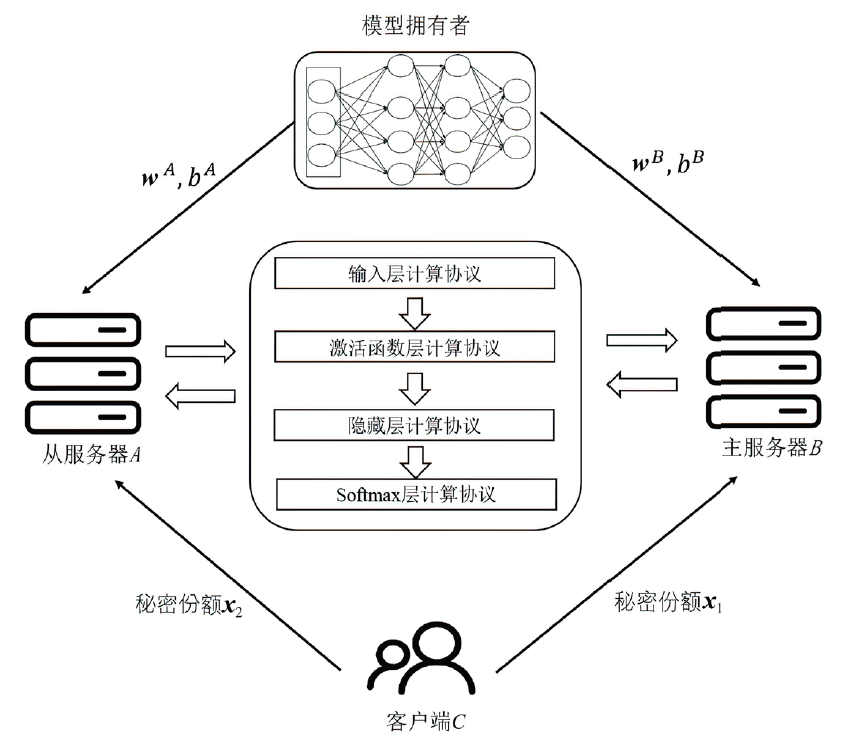
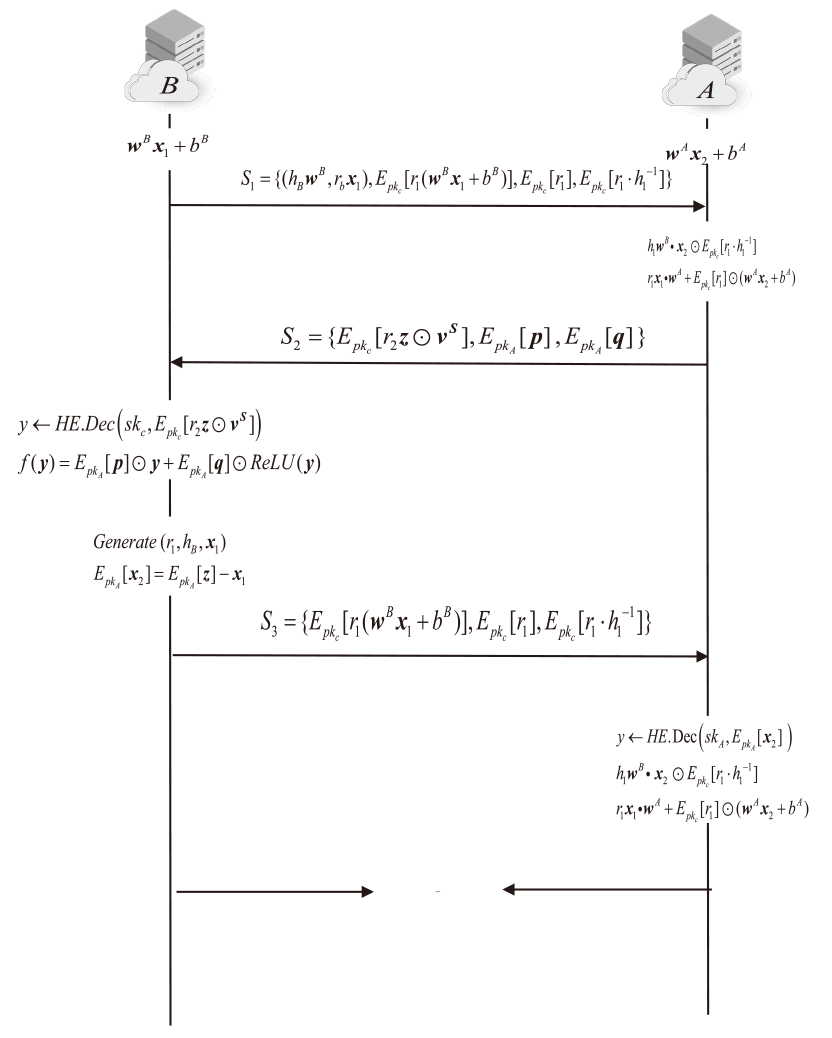
Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption
LIN Zhanhang, XIANG Guangli( ), LI Zhenpeng, XU Ziyi
), LI Zhenpeng, XU Ziyi
- School of Computer and Artificial Intelligence, Wuhan University of Technology, Wuhan 430070, China
-
Received:2024-05-29Online:2024-09-10Published:2024-09-27
CLC Number:
Cite this article
LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption[J]. Netinfo Security, 2024, 24(9): 1375-1385.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.09.006
| [1] | HAMDAN M A, MAKLOUF A M, MNIF H. Review of Authentication with Privacy-Preserving Schemes for 5G-Enabled Vehicular Networks[C]// IEEE. 2022 15th International Conference on Security of Information and Networks. New York: IEEE, 2022, 15(4): 1-6. |
| [2] | RANGARAJU S, NESS S, DHARMALINGAM R. Incorporating AI-Driven Strategies in DevSecOps for Robust Cloud Security[J]. International Journal of Innovative Science and Research Technology, 2023, 8(23): 2359-2365. |
| [3] | TANUWIDJAJA H C, CHOI R, BAEK S, et al. Privacy-Preserving Deep Learning on Machine Learning as a Service-a Comprehensive Survey[J]. IEEE Access, 2020, 8(2): 167425-167447. |
| [4] | YANG Wencheng, WANG Song, CUI Hui, et al. A Review of Homomorphic Encryption for Privacy-Preserving Biometrics[EB/OL].(2023-03-29)[2024-04-30]. https://doi.org/10.3390/s23073566. |
| [5] | WANG Jianhua, LI Lin, ZHAO Zhendong, et al. A Neural Network Prediction Scheme Based on Total Homomorphic Encryption Algorithm[J]. Artificial Intelligence, 2022, 3(4): 97-108. |
| 王建华, 黎琳, 赵镇东, 等. 一种基于全同态加密算法的神经网络预测方案[J]. 人工智能, 2022, 3(4):97-108. | |
| [6] | GILAD-BACHRACH R, DOWLIN N, LAINE K, et al. Cryptonets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2016, 48(2): 201-210. |
| [7] | HESAMIFARD E, TAKABI H, GHASEMI M. Cryptodl: Towards Deep Learning over Encrypted Data[C]// ACSAC. Annual Computer Security Applications Conference. New York: ACM, 2016, 6(3): 11-21. |
| [8] | MOHASSEL P, ZHANG Yupeng. SecureML: A System for Scalable Privacy-Preserving Machine Learning[C]// IEEE. 2017 IEEE Symposium on Security and Privacy. New York: IEEE, 2017, 36(2): 19-38. |
| [9] | LIU Jian, JUUTI M, LU Yao, et al. Oblivious Neural Network Predictions via Minionn Transformations[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017, 14(6): 619-631. |
| [10] | MOHASSEL P, RINDAL P. ABY3: A Mixed Protocol Framework for Machine Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018, 21(3): 35-52. |
| [11] | JUVEKAR C, VAIKUNTANATHAN V, CHANDRAKASAN A. Gazelle: A Low Latency Framework for Secure Neural Network Inference[C]// USENIX. 27th USENIX Security Symposium. Berkeley: USENIX, 2018, 23(2): 1651-1669. |
| [12] | WAGH S, GUPTA D, CHANDRAN N. SecureNN: 3-Party Secure Computation for Neural Network Training[J]. Proceedings on Privacy Enhancing Technologies, 2019, 2019(3): 26-49. |
| [13] | LI Jinguo, YAN Yan, ZHANG Kai, et al. FPCNN: A Fast Privacy-Preserving Outsourced Convolutional Neural Network with Low-Bandwidth[EB/OL]. (2023-11-01)[2024-04-30]. https://api.semanticscholar.org/CorpusID:265169136. |
| [14] | REN Yanli, YU Lingzan, HE Gang, et al. A Scheme of Privacy-Preserving Convolutional Neural Network Prediction[J]. Chinese Journal of Computers, 2023, 46(8): 1606-1619. |
| 任艳丽, 余凌赞, 何港, 等. 一种隐私保护的卷积神经网络预测方案[J]. 计算机学报, 2023, 46(8):1606-1619. | |
| [15] | NARESH V S, THAMARAI M. Privacy-Preserving Data Mining and Machine Learning in Healthcare: Applications, Challenges, and Solutions[J]. (2023-01-24)[2024-04-30]. https://wires.onlinelibrary.wiley.com/doi/abs/10.1002/widm.1490. |
| [16] | ZHAO Xia, WANG Limin, ZHANG Yufei, et al. A Review of Convolutional Neural Networks in Computer Vision[J]. Artificial Intelligence Review, 2024, 57(4): 1-43. |
| [17] | DONG Aoxiang, STARR A, ZHAO Yifan. Neural Network-Based Parametric System Identification: A Review[J]. International Journal of Systems Science, 2023, 54(13): 2676-2688. |
| [18] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate Numbers[C]// Springer. Advances in Cryptology-ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security. Heidelberg: Springer, 2017, 1(23): 409-437. |
| [19] | CHATTOPADHYAY A K, SAHA S, NAG A, et al. Secret Sharing: A Comprehensive Survey, Taxonomy and Applications[EB/OL]. (2024-02-01)[2024-04-30]. https://doi.org/10.1016/j.cosrev.2023.100608. |
| [20] | XIA Zhihua, GU Qi, XIONG Lizhi, et al. Privacy-Preserving Image Retrieval Based on Additive Secret Sharing[J]. International Journal of Autonomous and Adaptive Communications Systems, 2024, 17(2): 99-126. |
| [1] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [2] | GUO Qian, ZHAO Jin, GUO Yi. Hierarchical Clustering Federated Learning Framework for Personalized Privacy-Preserving [J]. Netinfo Security, 2024, 24(8): 1196-1209. |
| [3] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| [4] | HU Chengcong, HU Honggang. Lattice-Based Round-Optimal Password Authenticated Secret Sharing Protocol [J]. Netinfo Security, 2024, 24(6): 937-947. |
| [5] | WEN Weiping, ZHANG Shichen, WANG Han, SHI Lin. Linux Malicious Application Detection Scheme Based on Virtual Machine Introspection [J]. Netinfo Security, 2024, 24(5): 657-666. |
| [6] | GUO Jiansheng, GUAN Feiting, LI Zhihui. A Dynamic (t,n) Threshold Quantum Secret Sharing Scheme with Cheating Identification [J]. Netinfo Security, 2024, 24(5): 745-755. |
| [7] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| [8] | SUN Junfeng, LI Chenghai, SONG Yafei. ACCQPSO: An Improved Quantum Particle Swarm Optimization Algorithm and Its Applications [J]. Netinfo Security, 2024, 24(4): 574-586. |
| [9] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [10] | ZHANG Xinyou, SUN Feng, FENG Li, XING Huanlai. Multi-View Representations for Fake News Detection [J]. Netinfo Security, 2024, 24(3): 438-448. |
| [11] | FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection [J]. Netinfo Security, 2024, 24(3): 449-461. |
| [12] | ZHANG Qiang, HE Junjiang, LI Wenshan, LI Tao. Anomaly Traffic Detection Based on Deep Metric Learning [J]. Netinfo Security, 2024, 24(3): 462-472. |
| [13] | YU Shangrong, XIAO Jingbo, YIN Qilin, LU Wei. A Social Heterophily Focused Framework for Social Bot Detection [J]. Netinfo Security, 2024, 24(2): 319-327. |
| [14] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [15] | SA Qirui, YOU Weijing, ZHANG Yifei, QIU Weiyang, MA Cunqing. A Survey of Ownership Protection Schemes for Federated Learning Models [J]. Netinfo Security, 2024, 24(10): 1553-1561. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||