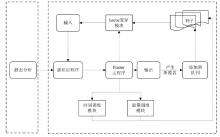
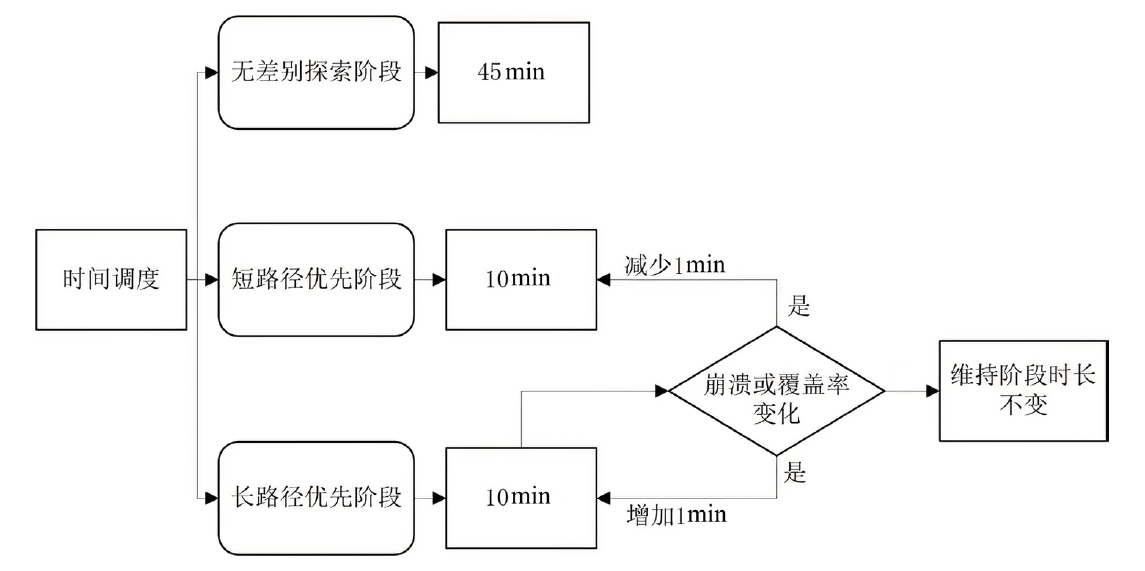
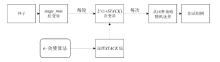
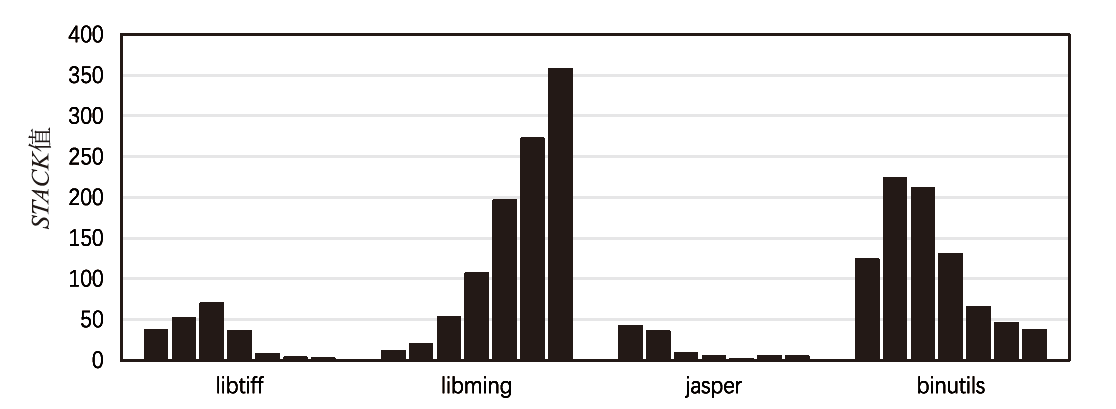
| [1] |
MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44.
doi: 10.1145/96267.96279
URL
|
| [2] |
CNCERT. 2020 China Internet Network Security Report[EB/OL]. (2021-07-21)[2022-10-06]. https://www.cert.org.cn/publish/man/upload/File/2020%20Annual%20Report.pdf.
|
|
国家互联网应急中心. 2020年中国互联网网络安全报告[EB/OL]. (2021-07-21)[2022-10-06]. https://www.cert.org.cn/publish/man/upload/File/2020%20Annual%20Report.pdf.
|
| [3] |
ZALEWSKI M. American Fuzzy Lop[EB/OL]. (2020-11-11)[2022-10-11]. https://lcamtuf.coredump.cx/afl/.
|
| [4] |
GODEFROID P. Random Testing for Security:Blackbox vs Whitebox Fuzzing[C]//IEEE. Proceedings of the 2nd International Workshop on Random Testing: Co-Located with the 22nd IEEE/ACM International Conference on Automated Software Engineering (ASE 2007). New York: IEEE, 2007: 1-12.
|
| [5] |
RAWAT S, JAIN V, KUMAR A, et al. VUzzer:Application-Aware Evolutionary Fuzzing[C]//ISOC. Network and Distributed System Security Symposium 2017. San Diego: ISOC, 2017: 1-14.
|
| [6] |
CHEN Peng, CHEN Hao. Angora:Efficient Fuzzing by Principled Search[C]//IEEE. 2018 IEEE Symposium on Security and Privacy. New York: IEEE, 2018: 711-725.
|
| [7] |
ASCHERMANN C, SCHUMILO S, BLAZYTKO T, et al. REDQUEEN:Fuzzing with Input-to-State Correspondence[C]//ISOC. Network and Distributed System Security Symposium 2019. San Diego: ISOC, 2019: 1-15.
|
| [8] |
GAN Shuitao, ZHANG Chao, CHEN Peng, et al. GREYONE:Data Flow Sensitive Fuzzing[C]//ACM. 29th USENIX Security Symposium. New York: ACM, 2020: 2577-2594.
|
| [9] |
LYU Chenyang, JI Shouling, ZHANG Chao, et al. MOPT:Optimized Mutation Scheduling for Fuzzers[C]//ACM. 28th USENIX Security Symposium. New York: ACM, 2019: 1949-1966.
|
| [10] |
HU Zhicheng, SHI Jianqi, HUANG Yanhong, et al. GANFuzz:A GAN-Based Industrial Network Protocol Fuzzing Framework[C]//ACM. CF '18:Computing Frontiers Conference. NewYork: ACM, 2018: 138-145.
|
| [11] |
CUMMINS C, PETOUMENOS P, MURRAY A, et al. Compiler Fuzzing Through Deep Learning[C]//ACM. ISSTA'18:International Symposium on Software Testing and Analysis. NewYork: ACM, 2018: 95-105.
|
| [12] |
SHE Dongdong, PEI Kexin, EPSTEIN D, et al. Neuzz:Efficient Fuzzing with Neural Program Smoothing[C]//IEEE. 2019 IEEE Symposium on Security and Privacy. New York: IEEE, 2019: 803-817.
|
| [13] |
GODEFROID P, PELEG H, SINGH R. Learn&Fuzz:Machine Learning for Input Fuzzing[C]//IEEE. 2017 32nd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2017: 50-59.
|
| [14] |
BÖHME M, PHAM V T, NGUYEN M D, et al. Directed Greybox Fuzzing[C]//ACM. CCS'17: 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344.
|
| [15] |
CHEN Hongxu, XUE Yinxing, LI Yuekang, et al. Hawkeye:Towards a Desired Directed Grey-Box Fuzzer[C]//ACM. CCS '18: 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 2095-2108.
|
| [16] |
LIANG Hongliang, ZHANG Yini, YU Yue, et al. Sequence Coverage Directed Greybox Fuzzing[C]//IEEE. ICSE '19: 41st International Conference on Software Engineering. New York: IEEE, 2019: 249-259.
|
| [17] |
LEE G, SHIM W, LEE B. Constraint-Guided Directed Greybox Fuzzing[C]//ACM. 30th USENIX Security Symposium. New York: ACM, 2021: 3559-3576.
|
| [18] |
HUANG Heqing, GUO Yiyuan, SHI Qingkai, et al. BEACON:Directed Grey-Box Fuzzing with Provable Path Pruning[C]//IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 36-50.
|
| [19] |
ÖSTERLUND S, RAZAVI K, BOS H, et al. Parmesan:Sanitizer-Guided Greybox Fuzzing[C]//ACM. SEC'20: 29th USENIX Conference on Security Symposium. New York: ACM, 2020: 2289-2306.
|
| [20] |
ZHANG Chenhui, ZHOU Anmin, JIA Peng. A Time Slicing-Based Directed Fuzzing[J]. Modern Computer, 2022, 28(8):63-67.
|
|
张晨辉, 周安民, 贾鹏. 一种基于时间分片的定向模糊测试[J]. 现代计算机, 2022, 28(8):63-67.
|
| [21] |
JASON S. GNU Binutils[EB/OL]. (2001-06-19)[2022-11-04]. https://www.gnu.org/software/binutils/.
|
| [22] |
DMITRY F. MJS: Restricted JavaScript Engine[EB/OL]. (2018-02-09)[2022-11-04]. https://github.com/cesanta/mjs.
|
| [23] |
KAREEM E. DARPA Challenge Binaries on Linux, OS X, and Windows[EB-OL]. (2021-04-14)[2022-11-04]. https://github.com/trailofbits/cb-multios.
|
| [24] |
SANDRO S. Libming[EB/OL]. (2021-05-11)[2022-11-04]. http://www.libming.org/.
|
| [25] |
ALAN Y. Jasper[EB/OL]. (2021-09-28)[2022-11-04]. https://ece.engr.uvic.ca/frodo/jasper/doc.
|
| [26] |
NICK W. Libxml2[EB/OL]. (2022-08-25)[2022-11-04]. https://github.com/GNOME/libxml2.
|
| [27] |
VADIM Z. Libtiff[EB/OL]. (2017-11-29)[2022-11-04]. https://github.com/vadz/libtiff.
|
| [28] |
PETER J. Yasm[EB/OL]. (2022-09-15)[2022-11-04]. https://github.com/yasm/yasm.
|
 )
)