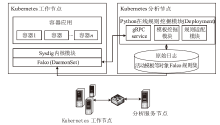
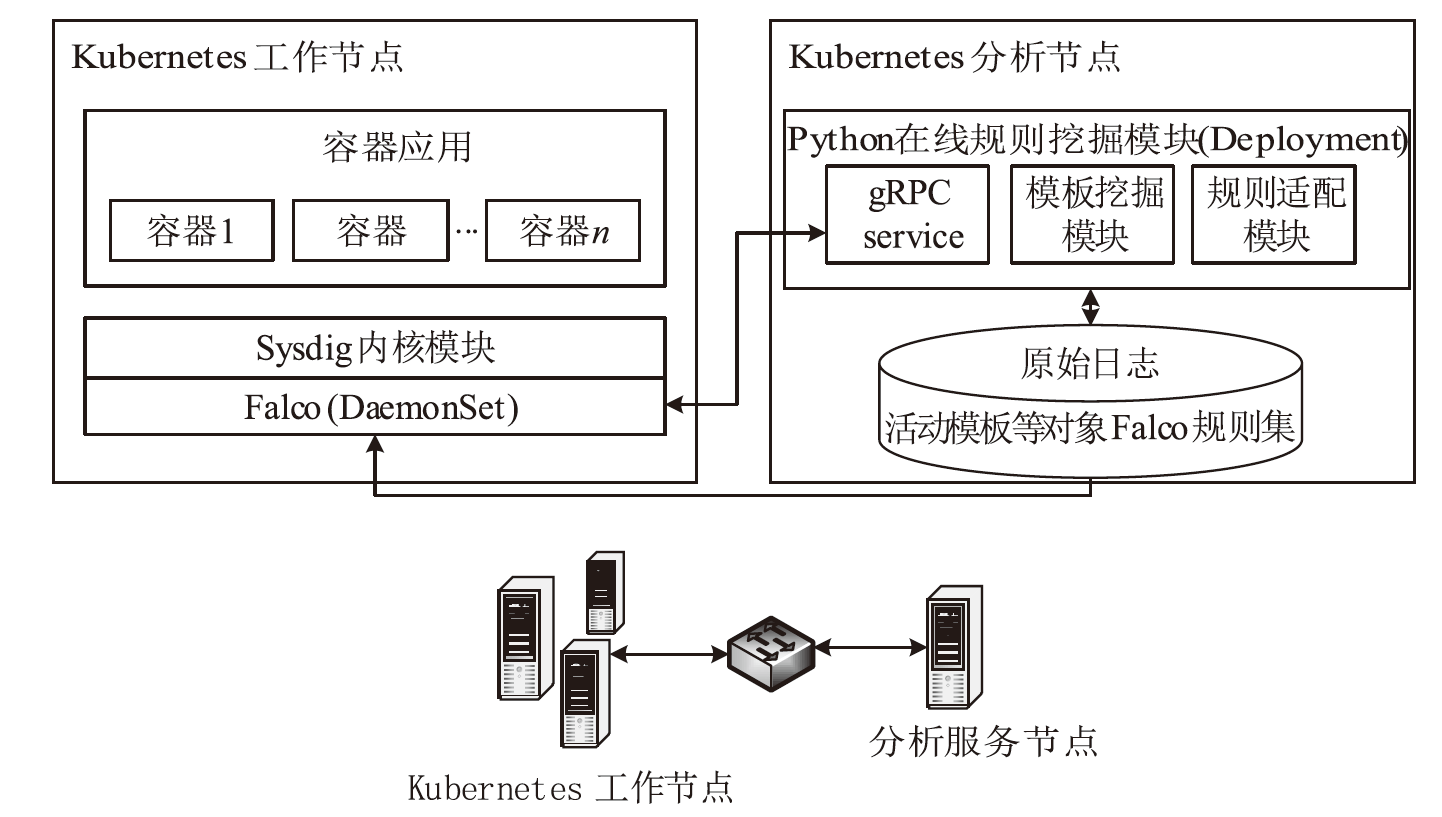
Netinfo Security ›› 2023, Vol. 23 ›› Issue (12): 91-102.doi: 10.3969/j.issn.1671-1122.2023.12.009
Previous Articles Next Articles
A Real-Time Anomaly Detection System for Container Clouds Based on Unsupervised System Call Rule Generation
WU Shenglin1, LIU Wanggen2, YAN Ming1( ), WU Jie1
), WU Jie1
- 1. School of Computer Science, Fudan University, Shanghai 200433, China
2. Transwarp Technology(Shanghai)Co.,Ltd., Shanghai 200233
-
Received:2023-04-11Online:2023-12-10Published:2023-12-13
CLC Number:
Cite this article
WU Shenglin, LIU Wanggen, YAN Ming, WU Jie. A Real-Time Anomaly Detection System for Container Clouds Based on Unsupervised System Call Rule Generation[J]. Netinfo Security, 2023, 23(12): 91-102.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.12.009
| 基本字段 | 描述 | |
|---|---|---|
| template_info | 模板自身基本信息,包括id、更新时间等 | |
| syscall_type | 系统调用类型信息,包括类型名称与方向(进入或返回),此字段为枚举值,不参与模板挖掘 | |
| image_info | 容器镜像相关信息,包括镜像名称和版本 | |
| process_info | 进程相关信息,包括进程名、进程路径、进程参数及父进程相应信息 | |
| event_action | action_type | 事件操作信息,包含操作类型(如tcp、file)、操作选项(如打开文件时只读、读写模式)、操作目标列表(如具体打开的文件路径、IP地址,采用列表面对rename等涉及多对象的操作),其中类型与选项为枚举值,不参与模板挖掘 |
| action_opt | ||
| action_subjects | ||
| event_results | 事件结果列表,包括返回值、数据大小等 | |
| event_data | 事件相关数据,例如,write调用所写内容 | |
| 场景 | 模板总数 | 总损失 | ||||
|---|---|---|---|---|---|---|
| 本算法 | Drain | SwissLog | 本算法 | Drain | SwissLog | |
| CVE-2017-7529 | 8 | 11 | 9 | 5.16 | 5.59 | 6.92 |
| CVE-2017-12635 | 10 | 12 | 7 | 6.06 | 9.11 | 6.01 |
| CVE-2018-3760 | 28 | 57 | 64 | 13.78 | 66.37 | 23.33 |
| CVE-2019-5418 | 26 | 38 | 45 | 13.19 | 28.41 | 30.68 |
| CVE-2020-9484 | 19 | 17 | 13 | 7.39 | 6.78 | 14.73 |
| CVE-2020-13942 | 77 | 93 | 63 | 13.06 | 12.28 | 40.39 |
| CVE-2020-23839 | 28 | 27 | 36 | 7.44 | 64.32 | 34.79 |
| EPS_CWE-434 | 398 | 77 | 245 | 24.97 | 45.1 | 74.71 |
| PHP_CWE-434 | 64 | 55 | 57 | 12.29 | 36.41 | 23.95 |
| 场景 | 平均日志处理速度(条/ms) | ||
|---|---|---|---|
| 本算法 | Drain | SwissLog | |
| CVE-2017-7529 | 16.67 | 25.00 | 7.69 |
| CVE-2017-12635 | 25.00 | 7.14 | 0.55 |
| CVE-2018-3760 | 3.70 | 20.00 | 4.55 |
| CVE-2019-5418 | 7.69 | 20.00 | 5.00 |
| CVE-2020-9484 | 14.29 | 5.56 | 0.52 |
| CVE-2020-13942 | 3.45 | 3.23 | 0.16 |
| CVE-2020-23839 | 9.09 | 25.00 | 12.50 |
| EPS_CWE-434 | 5.88 | 20.00 | 5.00 |
| PHP_CWE-434 | 16.67 | 14.29 | 1.79 |
| [1] |
BERNSTEIN D. Containers and Cloud: From LXC to Docker to Kubernetes[J]. IEEE Cloud Computing, 2014, 1(3): 81-84.
doi: 10.1109/MCC.2014.51 URL |
| [2] | LIN X, LEI L, WANG Y, et al. A Measurement Study on Linux Container Security: Attacks and Countermeasures[C]// ACM. Proceedings of the 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 418-429. |
| [3] | KERRISK M. Linux Manual Pages: Section 7[EB/OL]. [2023-08-10]. https://man7. org/linux/man-pages/dir_section_7. html. |
| [4] |
MARTIN A, RAPONI S, COMBE T, et al. Docker Ecosystem- Vulnerability Analysis[J]. Computer Communications, 2018, 122: 30-43.
doi: 10.1016/j.comcom.2018.03.011 URL |
| [5] | Tencent Cloud Computing(Beijing) Co., Ltd. Container Security Whitepaper of Tencent Cloud[EB/OL]. (2021-04-01)[2023-04-10]. https://cloud.tencent.com/developer/article/1639379?from=15425. |
| 腾讯云计算北京有限责任公司. 腾讯云容器安全白皮书[EB/OL]. (2021-04-01)[2023-04-10]. https://cloud.tencent.com/developer/article/1639379?from=15425. | |
| [6] | LIU M, XUE Z, XU X, et al. Host-Based Intrusion Detection System with System Calls: Review and Future Trends[J]. ACM Computing Surveys, 2019, 51(5): 1-36. |
| [7] | CASTANHEL G R, HEINRICH T, CESCHIN F, et al. Taking a Peek: An Evaluation of Anomaly Detection Using System Calls for Containers[C]// IEEE. 2021 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2021: 1-6. |
| [8] | MOORE P, SMALLEY S, PARIS E. Linux Security Module Usage[EB/OL]. [2023-08-11]. https://www.kernel.org/doc/html/v4.16/admin-guide/LSM/index.html. |
| [9] | HUANG C, WANG K, LI Y, et al. ASPGen-D: Automatically Generating Fine-Grained Apparmor Policies for Docker[C]// IEEE. 2022 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom). New York: IEEE, 2022: 822-829. |
| [10] | ZHU H, GEHRMANN C. Kub-Sec, An Automatic Kubernetes Cluster AppArmor Profile Generation Engine[C]// IEEE. 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS). New York: IEEE, 2022: 129-137. |
| [11] | IIGUNI T, KAMEI H, SAISHO K. Sprofiler: Automatic Generating System of Container-Native System Call Filtering Rules for Attack Surface Reduction[C]// IEEE. 2021 International Conference on Computational Science and Computational Intelligence (CSCI). New York: IEEE, 2021: 704-709. |
| [12] |
SULTAN S, AHMAD I, DIMITRIOU T. Container Security: Issues, Challenges, and the Road Ahead[J]. IEEE Access, 2019, 7: 52976-52996.
doi: 10.1109/Access.6287639 URL |
| [13] | GRIMMER M, RÖHLING M, KREUSEL D, et al. A Modern and Sophisticated Host Based Intrusion Detection Data Set[J]. IT-Sicherheit Als Voraussetzung Für Eine Erfolgreiche Digitalisierung, 2019: 135-145. |
| [14] | FALCOSECURITY. Falco[EB/OL]. (2023-04-06)[2023-04-10]. https://falco.org. |
| [15] | AQUASECURITY. Tracee[EB/OL]. (2023-04-01)[2023-04-10]. https://github.com/aquasecurity/tracee. |
| [16] | GHAVAMNIA S, PALIT T, BENAMEUR A. Confine: Automated System Call Policy Generation for Container Attack Surface Reduction[EB/OL]. (2020-10-03)[2023-04-10]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1s1f0js0wg1b0pm0k55v0p50c9316847&site=xueshu_se. |
| [17] | CANELLA C, WERNER M, GRUSS D, et al. Automating Seccomp Filter Generation for Linux Applications[C]// ACM. Proceedings of the 2021 on Cloud Computing Security Workshop. New York: ACM, 2021: 139-151. |
| [18] | MATTETTI M, SHULMAN-PELEG A, ALLOUCHE Y, et al. Securing the Infrastructure and the Workloads of Linux Containers[C]// IEEE. 2015 IEEE Conference on Communications and Network Security (CNS). New York: IEEE, 2015: 559-567. |
| [19] | LOUKIDIS-ANDREOU F, GIANNAKOPOULOS I, DOKA K, et al. Docker-Sec: A Fully Automated Container Security Enhancement Mechanism[C]// IEEE. 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2018: 1561-1564. |
| [20] |
ZHU H, GEHRMANN C. Lic-Sec: An Enhanced App Armor Docker Security Profile Generator[J]. Journal of Information Security and Applications, 2021, 61: 102924-102931.
doi: 10.1016/j.jisa.2021.102924 URL |
| [21] | TUNDE-ONADELE O, HE J, DAI T, et al. A Study on Container Vulnerability Exploit Detection[C]// IEEE. 2019 IEEE International Conference on Cloud Engineering (IC2E). New York: IEEE, 2019: 121-127. |
| [22] | LI Xiaohan, ZHANG Xinyou. Docker Anomaly Detection Based on System Call[J]. Microelectronics & Computer, 2022, 39(12): 77-85. |
| 栗晓晗, 张新有. 基于系统调用的 Docker 容器异常检测[J]. 微电子学与计算机, 2022, 39(12): 77-85. | |
| [23] | TIEN C, HUANG T, TIEN C, et al. KubAnomaly: Anomaly Detection for the Docker Orchestration Platform with Neural Network Approaches[J]. Engineering Reports, 2019, 1(5): 80-92. |
| [24] | Github. Sysdig[EB/OL]. (2023-02-20)[2023-04-10]. https://github.com/draios/sysdig. |
| [25] | HE P, ZHU J, ZHENG Z, et al. Drain: An Online Log Parsing Approach with Fixed Depth Tree[C]// IEEE. 2017 IEEE International Conference on Web Services (ICWS). New York: IEEE, 2017: 33-40. |
| [26] | LI X, CHEN P, JING L, et al. SwissLog: Robust and Unified Deep Learning Based Log Anomaly Detection for Diverse Faults[C]// IEEE. 2020 IEEE 31st International Symposium on Software Reliability Engineering (ISSRE). New York: IEEE, 2020: 92-103. |
| [27] |
ZHU Yuqian, DENG Jiaying, PU Jiachen, et al. ML-Parser: An Efficient and Accurate Online Log Parser[J]. Journal of Computer Science and Technology, 2022, 37(6): 1412-1423.
doi: 10.1007/s11390-021-0730-4 |
| [28] | ZHU J, HE S, LIU J, et al. Tools and Benchmarks for Automated Log Parsing[C]// IEEE/ACM. 2019 IEEE/ACM 41st International Conference on Software Engineering:Software Engineering in Practice (ICSE-SEIP). New York: IEEE, 2019: 121-130. |
| [29] | LUPTON S, WASHIZAKI H, YOSHIOKA N, et al. Literature Review on Log Anomaly Detection Approaches Utilizing Online Parsing Methodology[C]// IEEE. 2021 28th Asia-Pacific Software Engineering Conference (APSEC). New York: IEEE, 2021: 559-563. |
| [30] |
WANG J, DONG Y. Measurement of Text Similarity: A Survey[J]. Information, 2020, 11(9): 421-438.
doi: 10.3390/info11090421 URL |
| [31] |
PRASETYA D, PRASETYA W, HIRASHIMA T. The Performance of Text Similarity Algorithms[J]. International Journal of Advances in Intelligent Informatics, 2018, 4(1): 63-71.
doi: 10.26555/ijain.v4i1.152 URL |
| [32] | NORA RAJU T, RAHANA P A, MONCY R, et al. Sentence Similarity-A State of Art Approaches[C]// IEEE. 2022 International Conference on Computing, Communication, Security and Intelligent Systems (IC3SIS). New York: IEEE, 2022: 1-6. |
| [33] | PRADHAN N, GYANCHANDANI M, WADHVANI R. A Review on Text Similarity Technique Used in IR and Its Application[J]. International Journal of Computer Applications, 2015, 120(9): 29-34. |
| [34] | CHRISTEN P. A Comparison of Personal Name Matching: Techniques and Practical Issues[C]// IEEE. Sixth IEEE International Conference on Data Mining-Workshops (ICDMW’06). New York: IEEE, 2006: 290-294. |
| [35] | DU M, LI F, ZHENG G, et al. DeepLog: Anomaly Detection and Diagnosis from System Logs through Deep Learning[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1285-1298. |
| [36] | GANTIKOW H, REICH C, KNAHL M, et al. Rule-Based Security Monitoring of Containerized Environments[J]. Cloud Computing and Services Science, 2020, 1218(8): 66-86. |
| [37] | GUO R, ZENG J. Phantom Attack: Evading System Call Monitoring[EB/OL]. [2023-04-10]. https://connect.ed-diamond.com/misc/misc-130/introduction-a-tetragon-observabilite-et-securite-temps-reel-basees-sur-ebpf. |
| [38] | Massachusetts Institute of Technology Lincoln Laboratory. DARPA Intrusion Detection Evaluation Data Set[EB/OL]. (1999-05-12)[2023-05-10]. https://www.ll.mit.edu/ideval/data/1999data.html. |
| [39] | University of New Mexico Computer Science Department Farris Engineering Center. Computer Immune Systems-Data Sets and Software[EB/OL]. [2023-03-10]. https://www.cs.unm.edu/-immsec/systemcalls.htm. |
| [40] | CREECH G, HU J. Generation of a New IDS Test Dataset: Time to Retire the KDD Collection[C]// IEEE. 2013 IEEE Wireless Communications and Networking Conference (WCNC). New York: IEEE, 2013: 4487-4492. |
| [41] |
HAIDER W, HU J, SLAY J, et al. Generating Realistic Intrusion Detection System Dataset Based on Fuzzy Qualitative Modeling[J]. Journal of Network and Computer Applications, 2017, 87: 185-192.
doi: 10.1016/j.jnca.2017.03.018 URL |
| [42] | GRIMMER M. LID-DS[EB/OL]. (2021-04-05)[2023-03-10]. https://github.com/LID-DS/LID-DS. |
| [43] | WU S. Dataset Recaptured from the Scenarios in LID-DS[EB/OL]. (2023-02-01)[2023-03-10]. https://github.com/wsl-fd/dataset_RADSCCBUSCRG. |
| [1] | QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders [J]. Netinfo Security, 2023, 23(9): 1-11. |
| [2] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [3] | XIA Yihang, ZHANG Zhilong, WANG Muzi, CHEN Libo. Dependency-Based Vulnerability Detection Method in Container Supply Chain [J]. Netinfo Security, 2023, 23(2): 76-84. |
| [4] | LIAO Liyun, ZHANG Bolei, WU Lifa. IoT Anomaly Detection Model Based on Cost-Sensitive Learning [J]. Netinfo Security, 2023, 23(11): 94-103. |
| [5] | ZHANG Yuchen, LI Lianghui, MA Chenyang, ZHOU Hongwei. A Log Anomaly Detection Method with Variables [J]. Netinfo Security, 2023, 23(10): 16-20. |
| [6] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| [7] | ZHOU Jingyi, LI Hongjiao. False Data Injection Attack Detection Method against PMU Measurements [J]. Netinfo Security, 2022, 22(5): 75-83. |
| [8] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [9] | XU Ruzhi, LYU Changran, LONG Yan, LIU Yuanbin. Defense Research of High-Hidden Data Attack in Industry Control System [J]. Netinfo Security, 2022, 22(12): 34-46. |
| [10] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [11] | NIU Yinuo, ZHANG Yifei, GAO Neng, MA Cunqing. Design of Log-Based Anomaly Detection System Based on Temporal and Logical Relationship [J]. Netinfo Security, 2022, 22(11): 1-6. |
| [12] | HUANG Zilong, ZHAN Dongyang, YE Lin, ZHANG Hongli. A Secure Container Management Approach Based on Virtual Machine Introspection [J]. Netinfo Security, 2022, 22(11): 55-61. |
| [13] | QIN Zhongyuan, HU Ning, FANG Lanting. Network Anomaly Detection Method Based on Immune Bionic Mechanism and Graph Neural Network [J]. Netinfo Security, 2021, 21(8): 10-16. |
| [14] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [15] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||