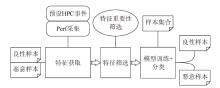
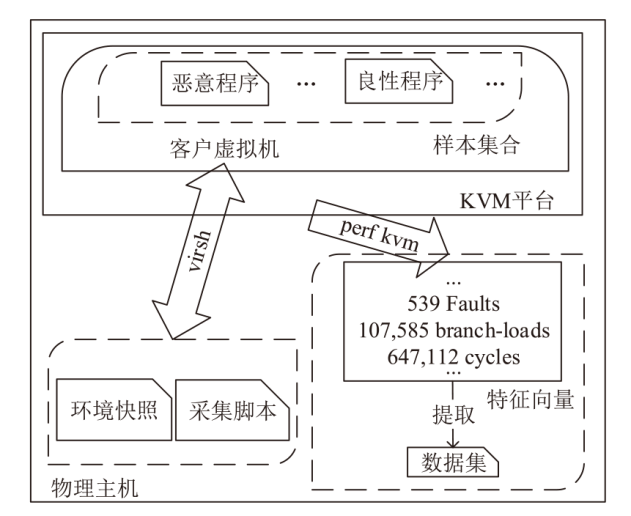
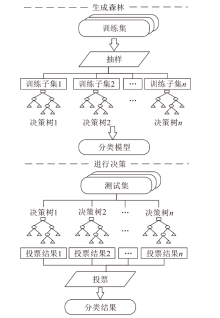
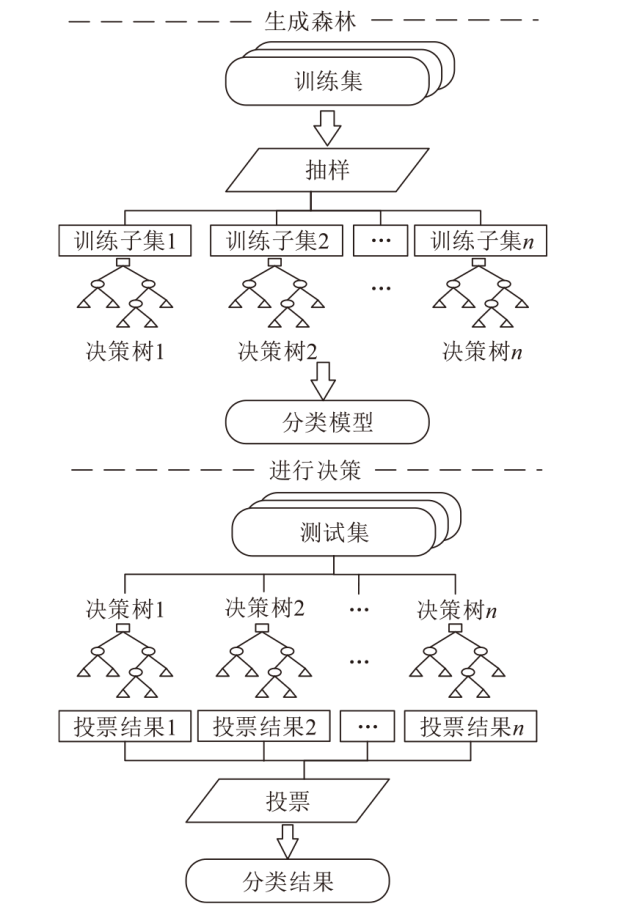
| [1] |
VMware. VMware Security Response Center(vSRC) Response to ‘ESXiArgs’ Ransomware Attacks[EB/OL]. (2023-02-06) [2023-04-20]. https://blogs.vmware.com/security/2023/02/83330.html.
|
| [2] |
Shenzhen Yunzhan Information Technology Co., Ltd. Ransomware Virus Targeting VMware ESXi Server Attacks are Spreading, Ransomware Defense, Emergency Rescue, Hardening Guide[EB/OL]. (2023-03-28) [2023-04-20]. https://www.sohu.com/a/660016097_121679003.
|
|
深圳云展信息技术有限公司. 勒索病毒针对VMware ESXi服务器攻击正在蔓延,勒索防御,紧急救援,加固指南[EB/OL]. (2023-03-28) [2023-04-20]. https://www.sohu.com/a/660016097_121679003.
|
| [3] |
UEKI K, KOURAI K. Fine-Grained Autoscaling with In-VM Containers and VM Introspection[C]// IEEE. 2020 IEEE/ACM 13th International Conference on Utility and Cloud Computing(UCC). New York: IEEE, 2020: 155-164.
|
| [4] |
SHARIF M, LEE W, CUI Weidong. Secure In-VM Monitoring Using Hardware Virtualization[C]// ACM. ACM Conference on Computer and Communications Security. New York: ACM, 2009: 477-488.
|
| [5] |
BILL B. The Rootkit Arsenal Escape and Evasion in the Dark Corners of the System[M]. Sudbury: Wordware Publishing, 2012.
|
| [6] |
YAN Guanglu, LUO Senlin, LIU Wangtong, et al. Highly Reliable In-VM Hidden Process Adversarial Detection Method[J]. Transaction of Beijing Institute of Technology, 2018, 38(3): 305-312.
|
|
闫广禄, 罗森林, 刘望桐, 等. 高可靠In-VM隐藏进程对抗检测方法[J]. 北京理工大学学报, 2018, 38(3):305-312.
|
| [7] |
ENRICO B, PIETRO F, MARIUS M, et al. Branch History Injection: On the Effectiveness of Hardware Mitigations Against Cross-Privilege Spectre-v2 Attacks[C]// NDSS. 30th ISOC Network and Distributed System Security Symposium. San Diego: ISOC, 2023: 1-18.
|
| [8] |
ROBERT B, HANS N J, THILO K, et al. One Glitch to Rule Them All: Fault Injection Attacks Against AMD’s Secure Encrypted Virtualization[C]// ACM. The 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 971-988.
|
| [9] |
PATEL N, SASAN A, HOMAYOUN H. Analyzing Hardware Based Malware Detectors[C]// IEEE. The 54th Annual Design Automation Conference 2017. New York: IEEE, 2017: 1-6.
|
| [10] |
NIU Weina, ZHAO Chengyang, ZHANG Xiaosong, et al. ROPDetector: A Real-Time Detection Method for ROP Attacks Based on Hardware Performance Counters[J]. Chinese Journal of Computers, 2021, 44(4): 761-772.
|
|
牛伟纳, 赵成洋, 张小松, 等. ROPDetector:一种基于硬件性能计数器的ROP攻击实时检测方法[J]. 计算机学报, 2021, 44(4):761-772.
|
| [11] |
Shanghai Yucheng Information Technology Co., Ltd. Introduction and Use of System-Level Performance Analysis Tools PERF[EB/OL]. (2019-11-18) [2023-04-23]. https://www.cnblogs.com/xuanbjut/p/11884262.html.
|
|
上海语程信息科技有限公司. 系统级性能分析工具PERF的介绍与使用[EB/OL]. (2019-11-18) [2023-04-23]. https://www.cnblogs.com/xuanbjut/p/11884262.html.
|
| [12] |
REN Yongjie, CHENG Zhou. KVM in Action: Principles, Advanced and Performance Tuning[M]. Beijing: China Machine Press, 2019.
|
|
任永杰, 程舟. KVM实战:原理、进阶与性能调优[M]. 北京: 机械工业出版社, 2019.
|
| [13] |
RED Hat. Perf_events[EB/OL]. (2018-04-20) [2023-04-23]. https://www.linux-kvm.org/page/Perf_events.
|
| [14] |
XU Jiayun, LI Yingjiu, ROBERT H, et al. Differential Training: A Generic Framework to Reduce Label Noises for Android Malware Detection[C]// NDSS. The Network and Distributed System Security Symposium(NDSS) 2021. San Diego: ISOC, 2021: 1-14.
|
| [15] |
ZHOU Zhihua. Machine Learning[M]. Beijing: Tsinghua University Press, 2016.
|
|
周志华. 机器学习[M]. 北京: 清华大学出版社, 2016.
|
| [16] |
SINGH B, EVTYUSHKIN D, EWELL J, et al. On the Detection of Kernel-Level Rootkits Using Hardware Performance Counters[C]// ACM. Asia Conference on Computer and Communications Security(ASIACCS) 2017. New York: ACM, 2017: 483-493.
|
| [17] |
SAYADI H, SAI M, HOUMANSADR A, et al. Comprehensive Assessment of Run-Time Hardware-Supported Malware Detection Using General and Ensemble Learning[C]// ACM. International Conference on Computing Frontiers. New York: ACM, 2018: 212-215.
|
| [18] |
GAN Yuyou, MAO Yuhao, ZHANG Xuhong, et al. “Is Your Explanation Stable?”: A Robustness Evaluation Framework for Feature Attribution[C]// ACM. The 2022 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 1157-1171.
|
| [19] |
SAYADI H, PATEL N, MANOJ P, et al. Ensemble Learning for Effective Run-Time Hardware-Based Malware Detection: A Comprehensive Analysis and Classification[C]// ACM. ACM/IEEE Design Automation Conference. New York: ACM, 2018: 1-6.
|
 )
)