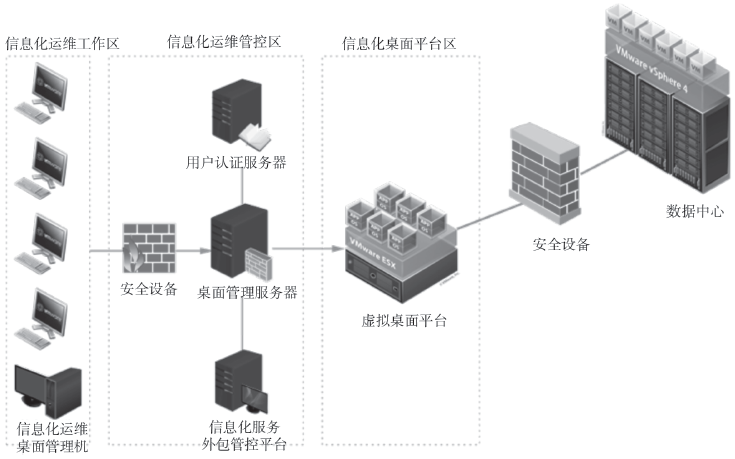
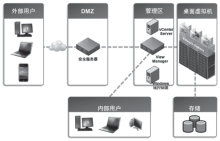
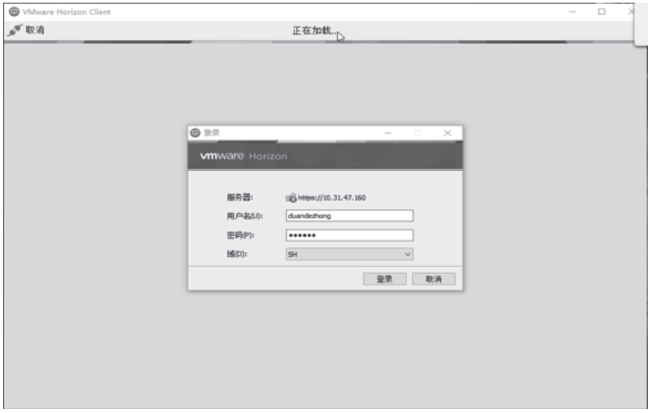
| [1] |
ZHANG Wenkai.Customs Informatization: Risk Management of Information Technology Outsourcing in Operation and Maintenance[J]. China Management Informationization,2014(1):63-65.
|
|
张文凯. 海关信息化:信息化运维外包的风险管理[J].中国管理信息化,2014(1):63-65.
|
| [2] |
ZHANG Hui,WANG Wei,GUO Dong.A Framework for Building Microservices-based Desktop Cloud[J]. Netinfo Security,2017(2):35-42.
|
|
张辉,王伟,郭栋.一种基于微服务范式的桌面云构建框架[J].信息网络安全,2017(2):35-42.
|
| [3] |
Cloud Technology Community.DevOps Fire Best Practices from Senior Operation Engineers[M].Beijing:China Machine Press,2017: 316-326.
|
|
云技术社区.运维前线一线运维专家的运维方法、技巧与实践[M].北京:机械工业出版社,2017:316-326.
|
| [4] |
ZHOU Liang.Research on Outsourcing Management Mode of Public Service Informatization Construction[D]. Beijing: Graduate School of Chinese Academy of Social Sciences,2012.
|
|
周梁. 公共服务信息化建设外包管理模式研究[D].北京:中国社会科学院研究生院,2012.
|
| [5] |
LI Hui.Knowing Yourself before Knowing Others——Probing into the Informatization Outsourcing Service in Government[J]. Shanghai Informatization,2007(1):23-25.
|
|
李慧. 先知已后知彼——政府信息化服务外包探秘[J].上海信息化,2007(1):23-25.
|
| [6] |
XIANG Linbo,LIU Chuanyi.Key Technology Research and Implement on Insider Threat for Controlled Cloud Computing[J].Netinfo Security,2016(3):53-58.
|
|
向林波,刘川意.针对内部威胁的可控云计算关键技术研究与实现[J].信息网络安全,2016(3):53-58.
|
| [7] |
LI Bei,TIAN Yangguang,LI Qian.Discussion on Outsourcing Management of Operation and Maintenance for Government Departments in E-government Construction[J]. Heilongjiang Science and Technology Information,2014(13):137.
|
|
李蓓,田阳光,李谦.浅议政府部门在电子政务建设中的运维外包管理[J].黑龙江科技信息,2014(13):137.
|
| [8] |
LIN Zefu,CHEN Dequan,WEN Ke.Risk Management Strategy in Information Technology Outsourcing[J]. Science of Science and Management of S.&.T.,2004,25(2):133-135.
|
|
林则夫,陈德泉,温珂.试论信息技术外包中的风险管理策略[J].科学学与科学技术管理,2004,25(2):133-135.
|
| [9] |
HONG Bing,XIA Hui,LIU Hong.Strategy Analysis of IT Outsourcing for Enterprises[J]. Journal of Industrial Engineering and Engineering Management, 2002,16(2):38-41.
|
|
红兵,夏晖,刘洪.企业信息技术外包的策略分析[J].管理工程学报,2002,16(2):38-41.
|
| [10] |
WEN Weiping,GUO Ronghua,MENG Zheng, et al.Research and Implementation on Information Security Risk Assessment Key Technology[J]. Netinfo Security,2015(2):7-14.
|
|
文伟平,郭荣华,孟正,等.信息安全风险评估关键技术研究与实现[J].信息网络安全,2015(2):7-14.
|
 ), Wei JIANG1, Jiahua JI1, Dezhong DUAN2
), Wei JIANG1, Jiahua JI1, Dezhong DUAN2